TechNadu
@TechNadu
Cutting through tech noise, covering #Cybersecurity, #VPNs | Real insights. Expert reviews. Daily threats decoded. #InfoSec #Privacy
You might like
🌍 @OpenAI says a @mixpanel breach exposed limited API-user data (names, emails, coarse location, device info). No chats, API keys, or payment data were involved. Researchers note that sending identifiable info to analytics tools isn’t considered best practice. What should…

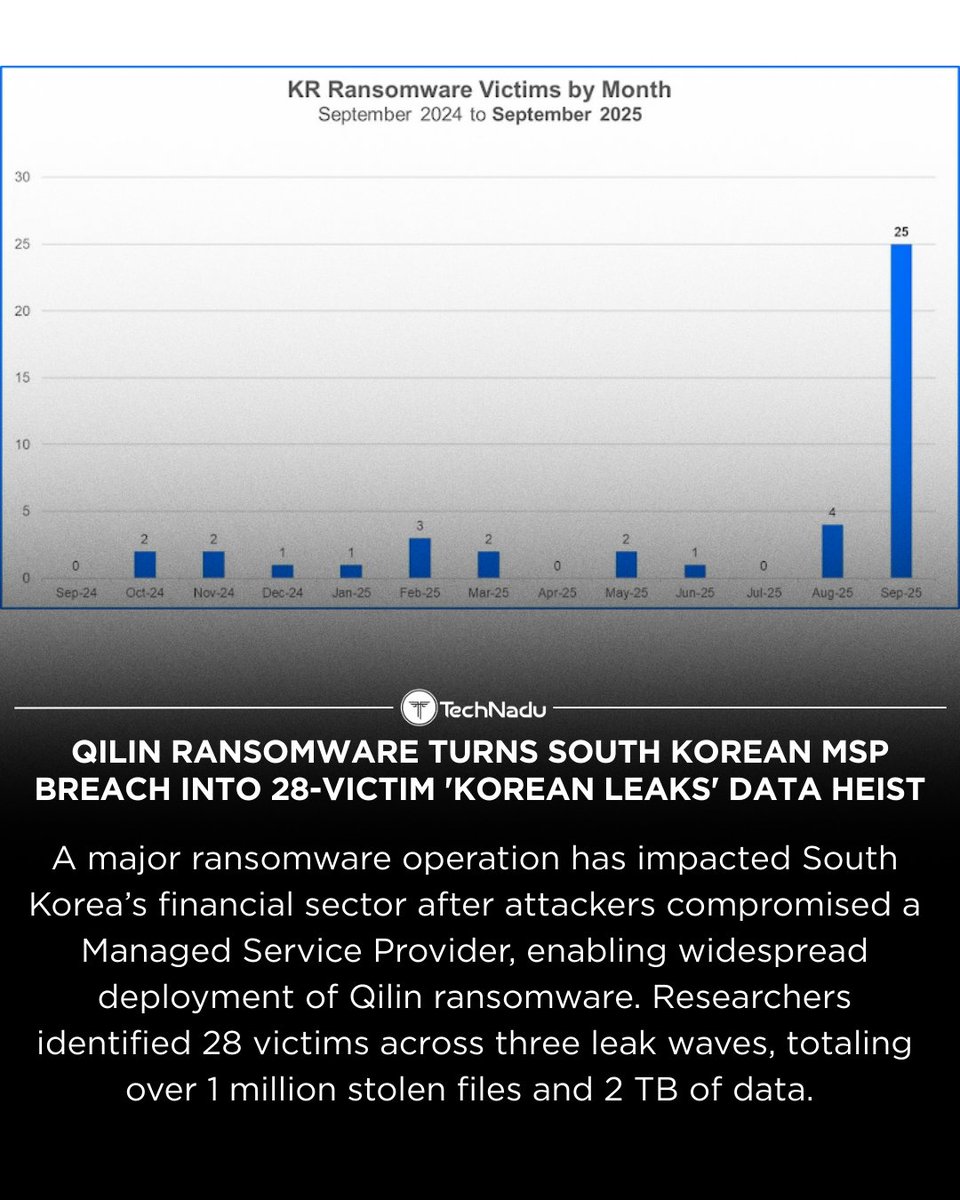
The “Korean Leaks” ransomware campaign hit 28 victims after a South Korean MSP breach, leading to over 1M files and 2TB of data stolen. Qilin ransomware - now among the most active RaaS groups - is linked to the incident. What can MSPs do to better secure access pathways? Share…
Kensington & Chelsea and Westminster City Council are responding to a cybersecurity issue affecting shared IT systems, with support from the NCSC. Hammersmith & Fulham is taking precautionary steps. Officials say it’s too early to determine the cause, and continuity plans are…

Neutral & concise, avoiding explicit detail. The DOJ alleges that an NSA contractor misused his work computer for harmful online activity involving minors. Monitoring systems reportedly triggered the investigation, and the contractor’s employment ended after his arrest. He…

Dartmouth College confirms a data breach after the Clop extortion group leaked files allegedly taken via an Oracle E-Business Suite zero-day. At least 1,494 individuals are directly affected, with more potentially impacted. 💬 What’s the bigger risk for universities - legacy…

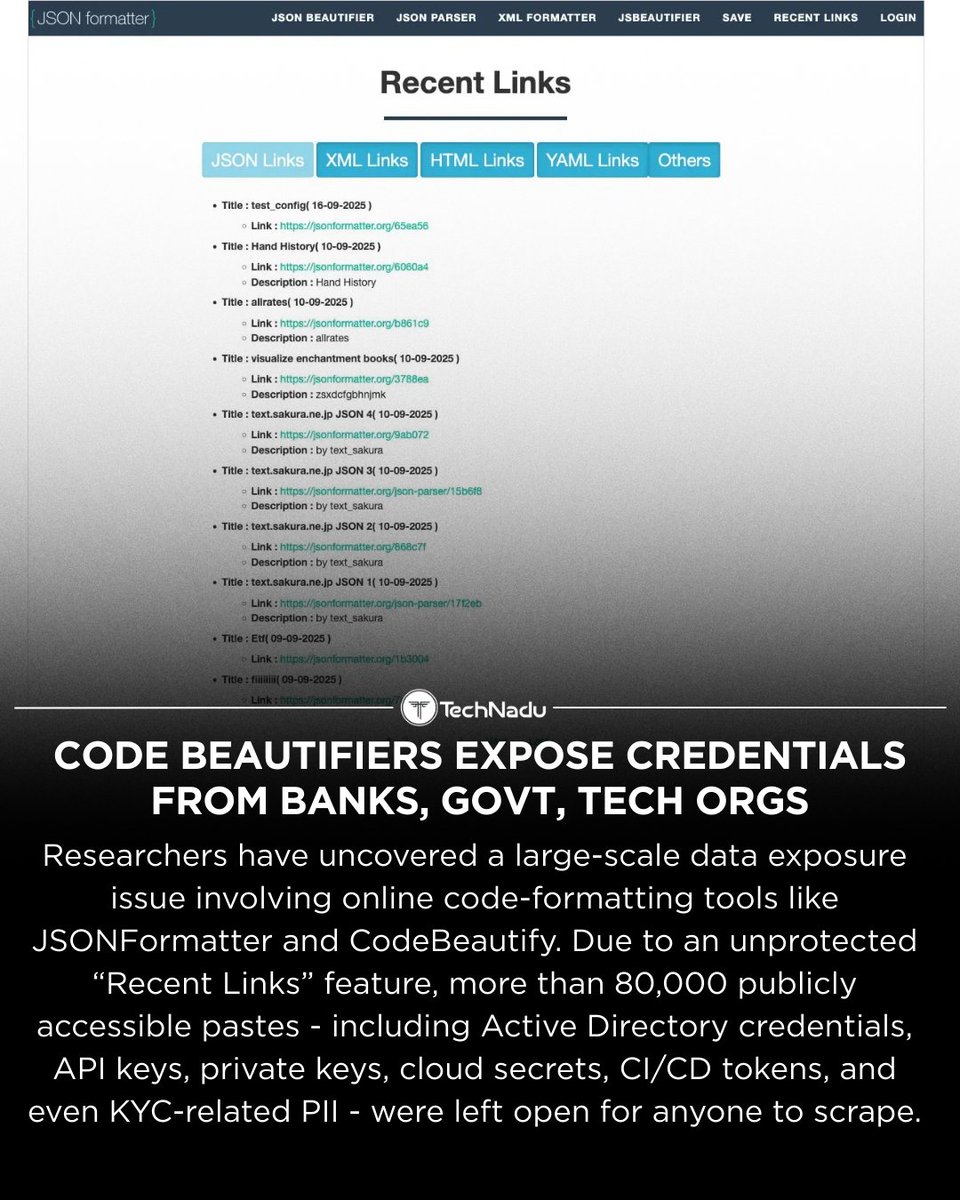
Researchers found that code-beautifier tools like JSONFormatter & CodeBeautify exposed 80k+ public pastes containing credentials, API keys, private keys, PII & more - due to an unprotected “Recent Links” feature. Even expired links were accessed by automated scanners. Follow…
United States Trends
- 1. Thanksgiving 1.4M posts
- 2. Thankful 252K posts
- 3. Turkey Day 33.1K posts
- 4. Busta Rhymes 1,056 posts
- 5. Lil Jon N/A
- 6. #ProBowlVote 13.9K posts
- 7. Toys R Us N/A
- 8. Afghanistan 240K posts
- 9. Gobble Gobble 21K posts
- 10. Mr. Fantasy N/A
- 11. #Grateful 4,290 posts
- 12. #Gratitude 7,079 posts
- 13. Turn Down for What N/A
- 14. Sarah Beckstrom 12.9K posts
- 15. Debbie Gibson N/A
- 16. Shaggy 3,107 posts
- 17. Andrew Wolfe 29.2K posts
- 18. Go Lions 1,711 posts
- 19. Liar Liar 74.1K posts
- 20. Feliz Día de Acción de Gracias 2,520 posts
You might like
-
 Neha Dwivedi
Neha Dwivedi
@nehadw -
 軍聞社 Military News Agency, ROC(Taiwan)🇹🇼
軍聞社 Military News Agency, ROC(Taiwan)🇹🇼
@mna_roc -
 Recycle India
Recycle India
@recycleindia -
 Sundeep Kishan
Sundeep Kishan
@sundeepkishan -
 OpenVPN Inc.
OpenVPN Inc.
@OpenVPN -
 RJ Balaji
RJ Balaji
@RJ_Balaji -
 CARS24 India
CARS24 India
@cars24india -
 XR Today
XR Today
@Xrtoday -
 Kiran Mazumdar-Shaw
Kiran Mazumdar-Shaw
@kiranshaw -
 FEG (Feed Every Gorilla)
FEG (Feed Every Gorilla)
@FEGtoken -
 Blockchain Daily News
Blockchain Daily News
@blckchaindaily -
 Google Cloud India
Google Cloud India
@GoogleCloud_IN -
 theapache64
theapache64
@theapache64 -
 AR Insider
AR Insider
@ArInsider -
 Simulation
Simulation
@simulationshow
Something went wrong.
Something went wrong.