clibm079
@clibm079
Independent Malware Analyst & Researcher,Notes (Philosophy & Poetry) — The Path of Clarity & Poems of Malware Analysis. Blog: http://malwareanalysisspace.blogspot.com
你可能會喜歡
"To truly understand an adversary, you must rise to — or beyond — their depth.Because only depth reveals intent." #CyberSecurity #MalwareAnalysis #APT #NationalLevelAPT #ThreatIntel #ReverseEngineering
💙PE-bear: The Art of Intuitive Malware Analysis How Visual Design Turns the ‘First View’ into Actionable Insights for Reverse Engineering malwareanalysisspace.blogspot.com/2025/11/pe-bea…
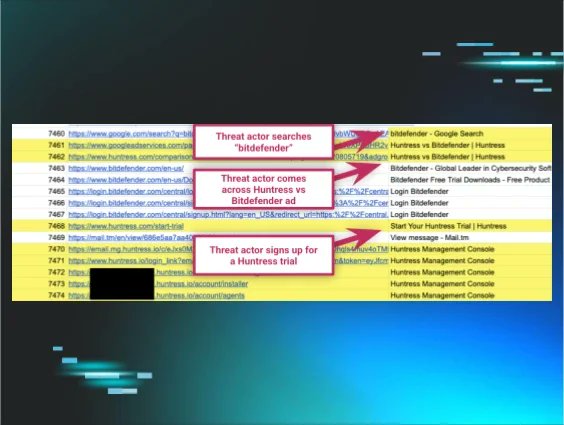
So this was a fun one to investigate! We had a threat actor install our agent, and it gave us some insight into what they do for a "living." 👇 huntress.com/blog/rare-look…
Long overdue, but here’s my writeup for #FlareOn12 Task 9: hshrzd.wordpress.com/2025/11/20/fla…
💽 Digital Forensics: Repairing a Damaged Hard Drive and Extracting the Data Blog: hackers-arise.com/digital-forens… Author: @three_cube
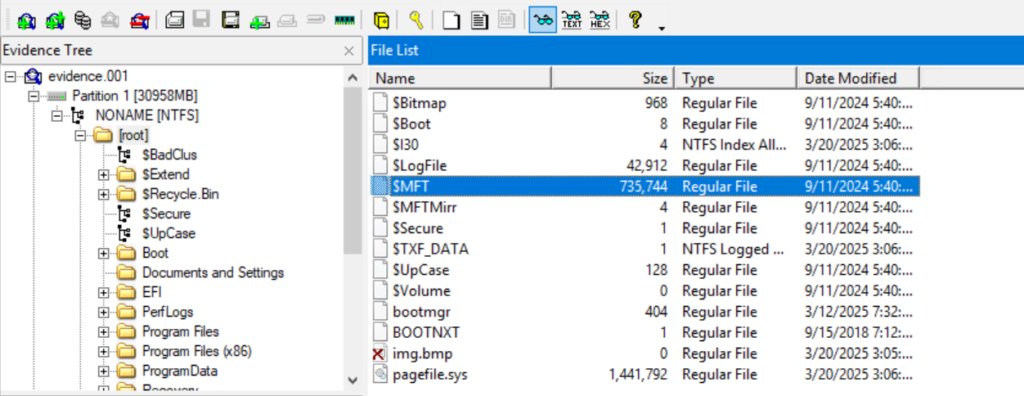
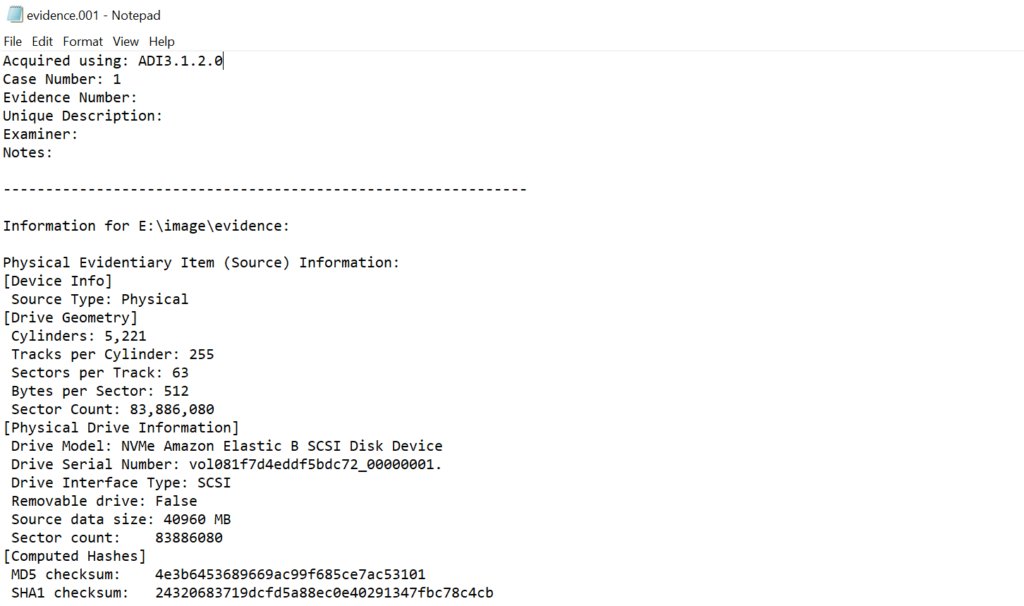

Been waiting for this for so long... now we have Plugin Manager and officially built BinDiff/BinExport for 9.2 My suffering has ended.
⌨️ Introducing HCLI: The Modern Command-Line Interface for IDA. Automate workflows, simplify plugin development across platforms, manage licenses and more. hex-rays.com/blog/introduci…
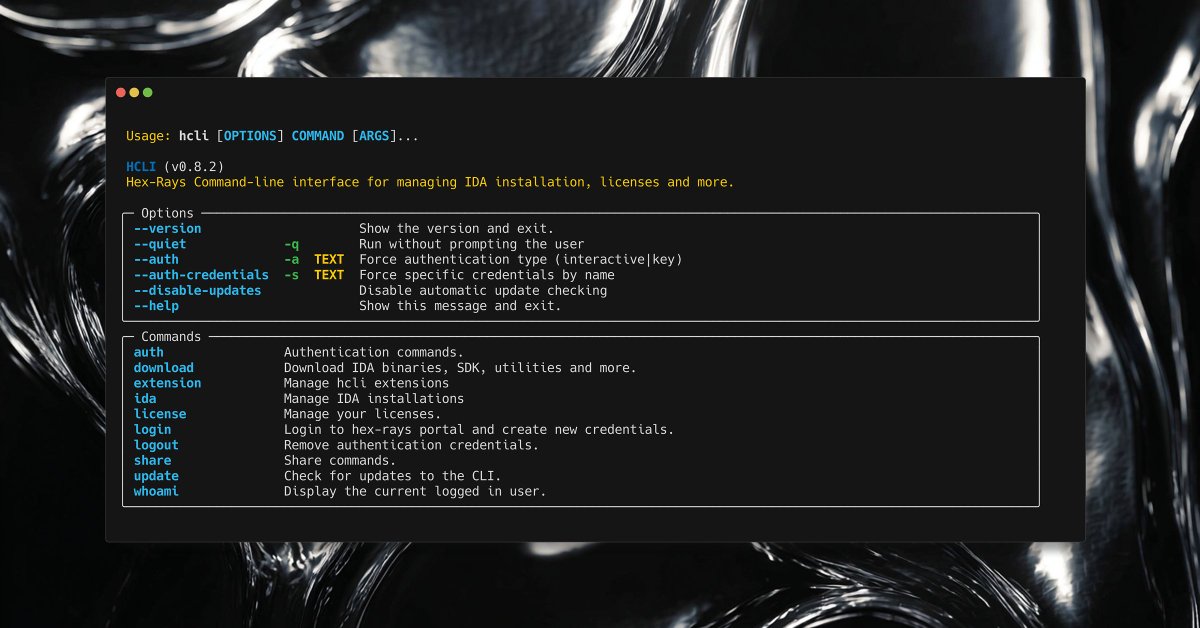
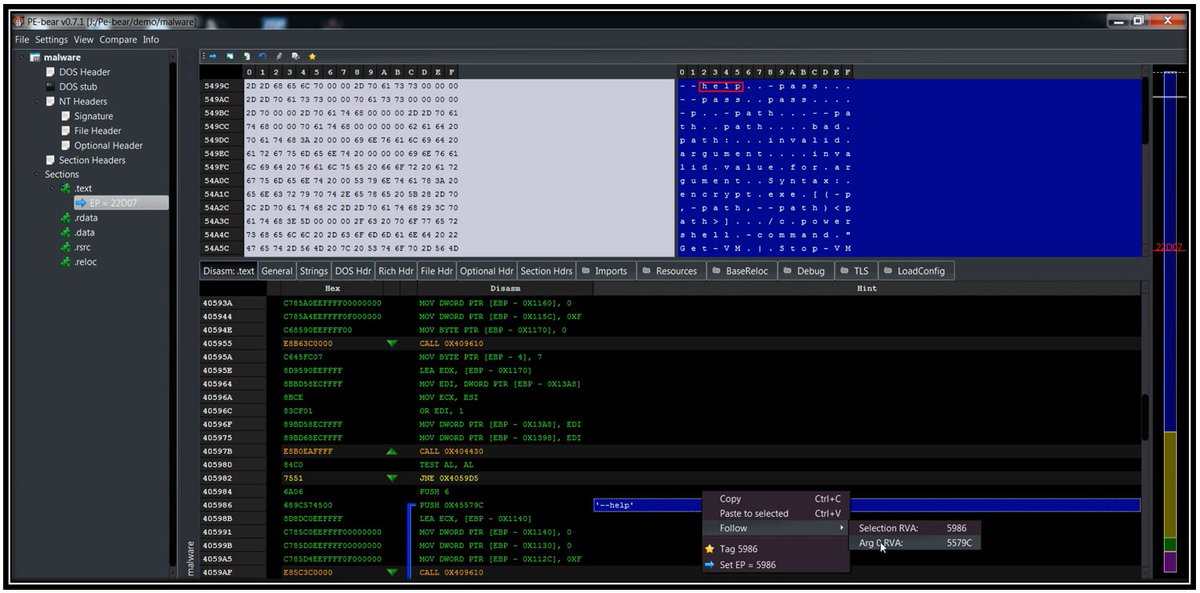
In PE-Bear’s Disasm view, “Follow arg 0 RVA” shows the RVA (Relative Virtual Address) of the first argument passed to a function. This makes it much easier to identify pointers to strings, structures, static configuration blocks, and other referenced data.💙
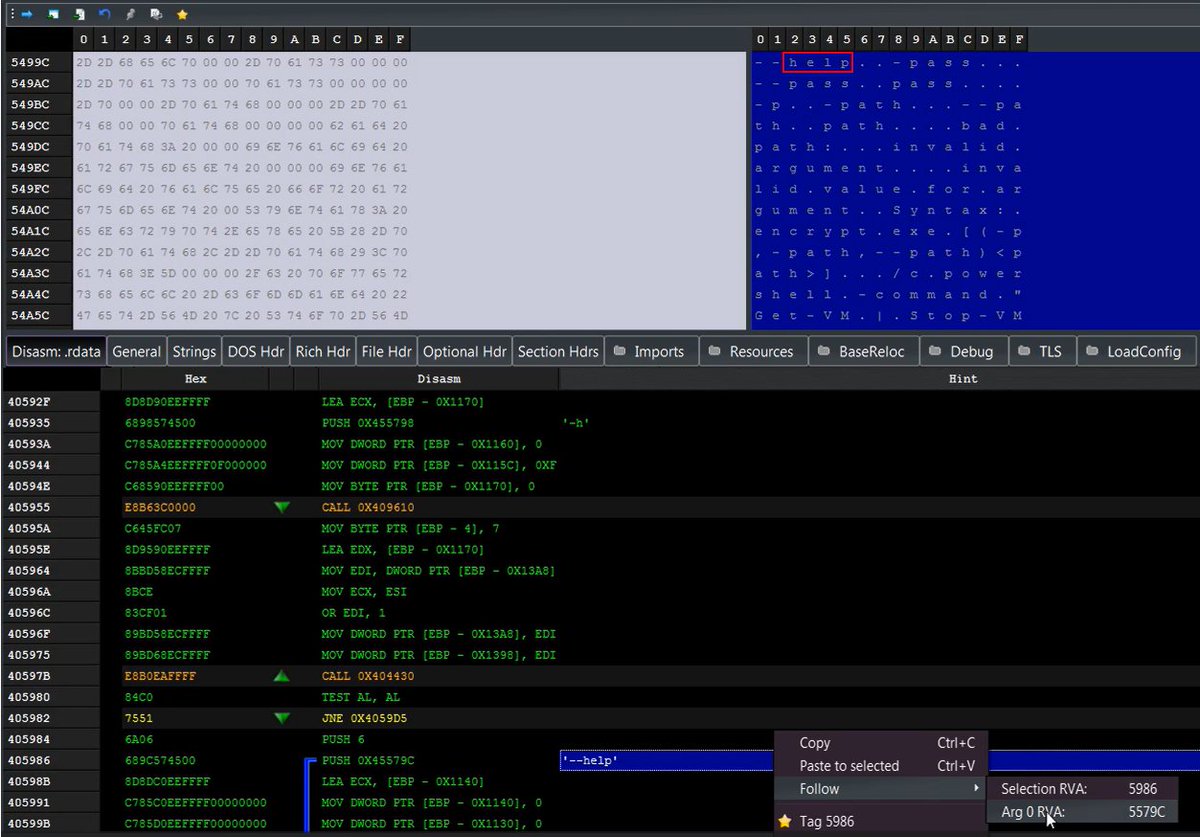
Example: PE-bear + IDA: How a beginner can quickly navigate to the main function using PE-bear’s Disasm Let IDA guide you efficiently and help you start a new journey.
Example: In the PE-Bear section map, visually contrast readable and obfuscated strings. Builds your “kung-fu” intuition for spotting packed vs. unpacked samples—no entropy needed. Flexible for mental triage and picking the right next step.
Example: Bridging PE-Bear and IDA: A Rapid Workflow from String Clue to Deep Static Analysis. PE-Bear finds the VA — IDA chases the logic.💙
Example: PE-Bear’s string scan + “Follow Raw” flow feels natural. That loop — scan → follow → scroll → inspect → spot → scan — keeps both panels in a single view: fast, focused, fluid. An amazing interactive, fast-feedback workflow that drives real analysis forward.💙
Malware is using AI to dynamically generate malicious scripts, obfuscate their own code to evade detection, and leverage AI models to create malicious functions on demand, rather than hard-coding them into the malware



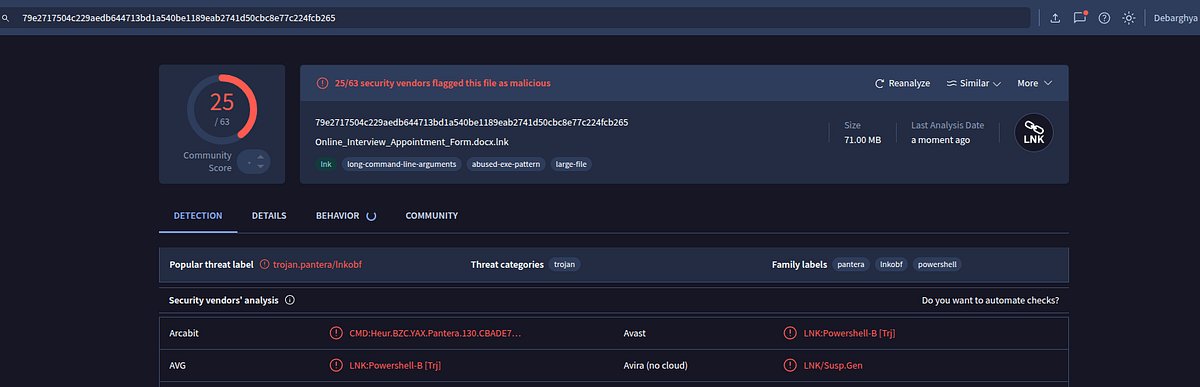
When a LNK is not a shortcut via recruiter lure that led to Pantera-like PowerShell stage -- medium.com/@debarghya4444…
So far, I have spent sleepless months writing custom libs and loaders for my red teaming assessments and its still going on =) After going through all this, I have decided to write a blog about some mistakes I made and why you shouldn't make them. Finally, I would like to…
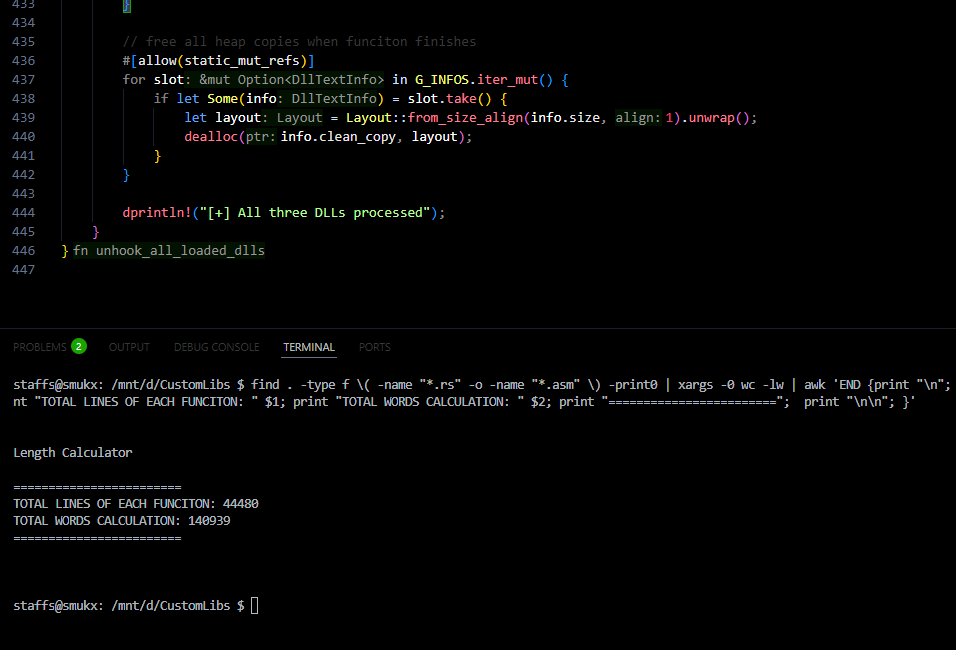
Couldn’t resist taking another look — PE-Bear’s string hover preview is pure design insight from real analysis work.💙
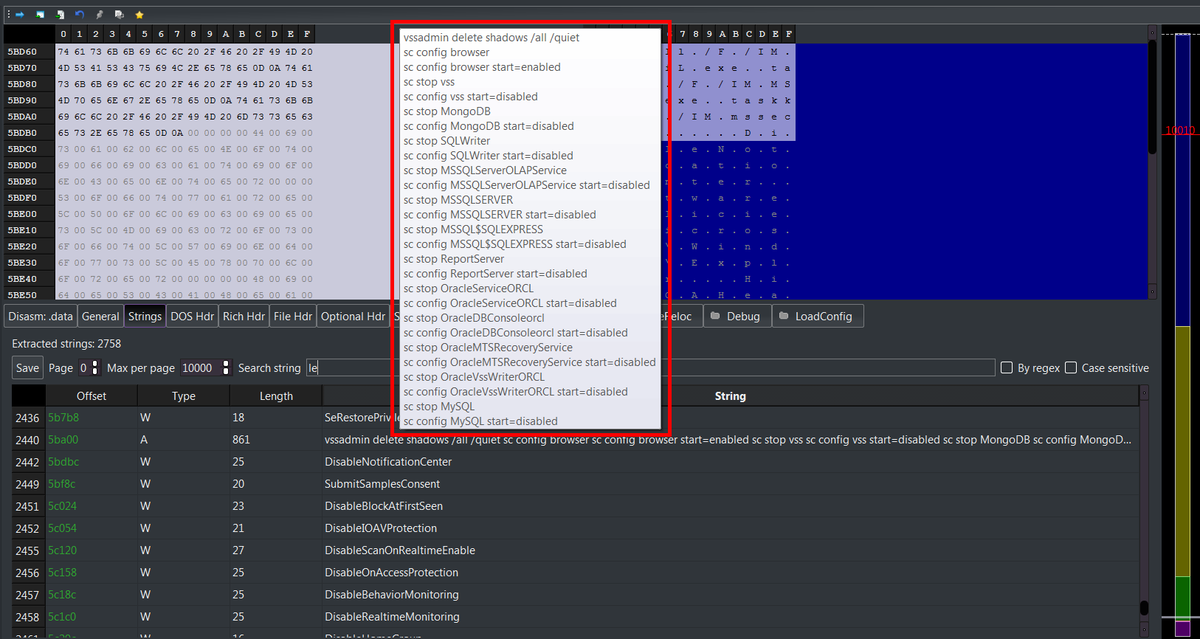
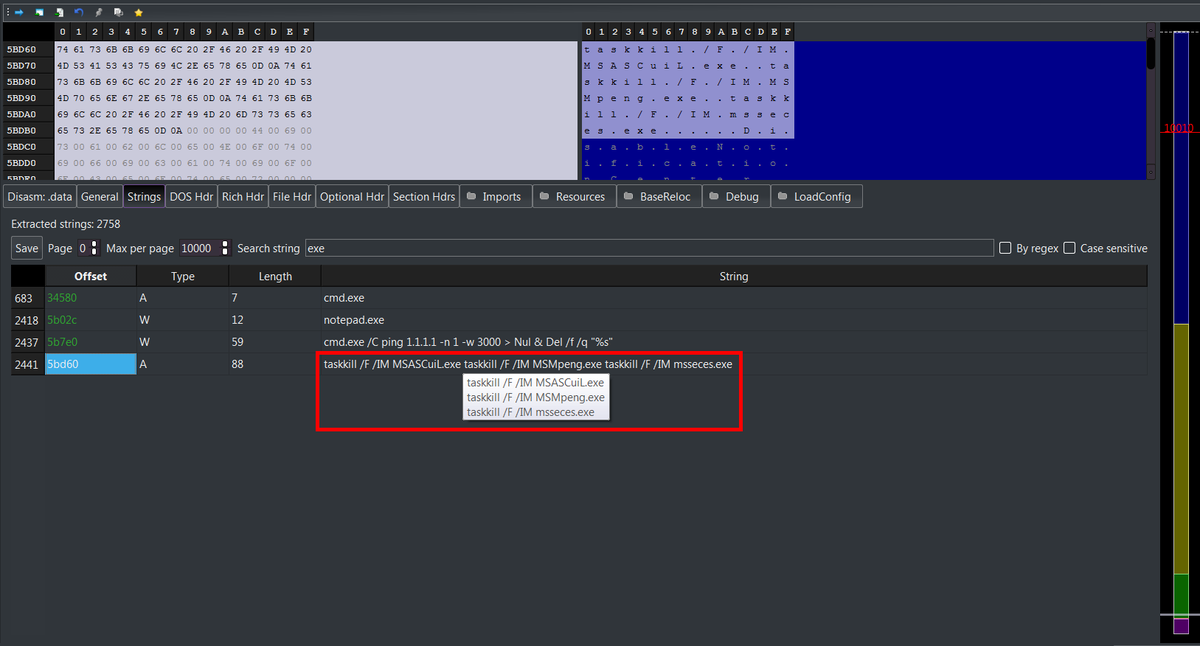
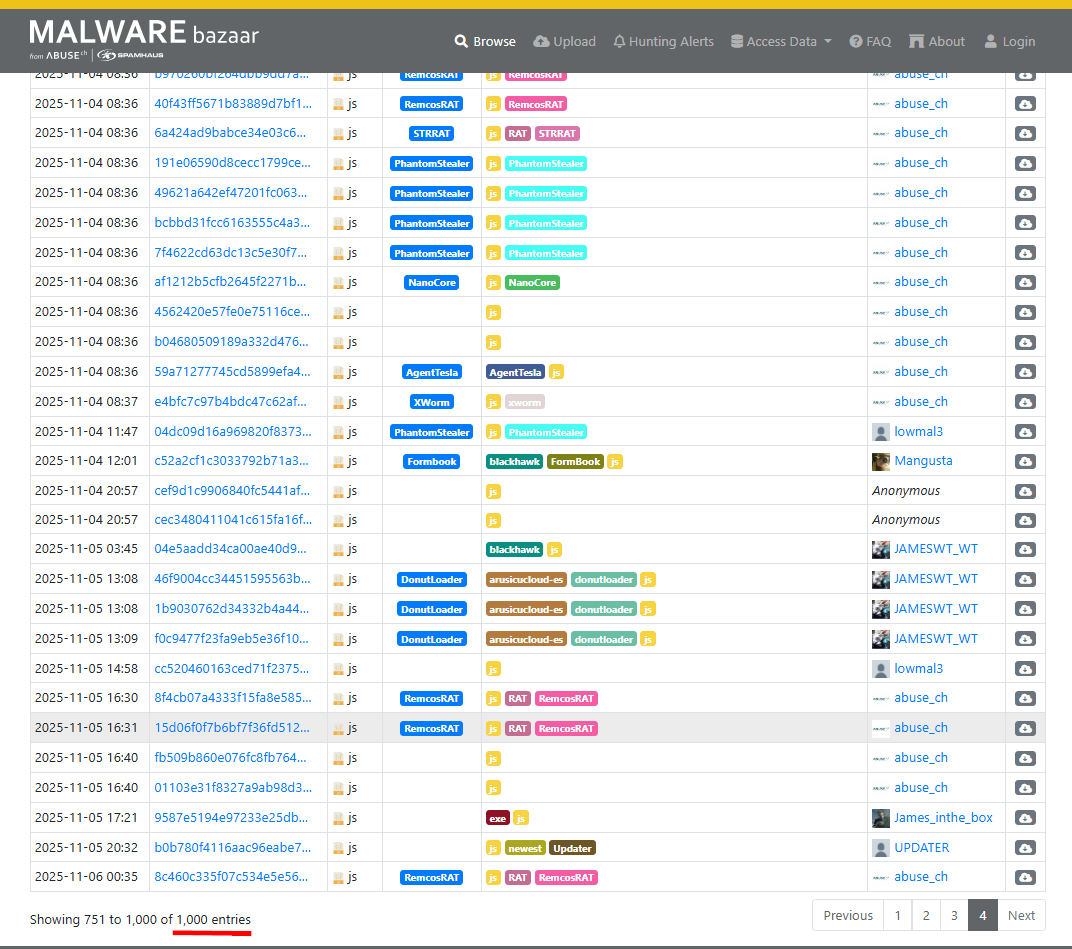
⚠️ I searched tag=JS on Bazaar and found about 1k malicious entries (2025-10-15 → 2025-11-06). The use of JavaScript for malware delivery seems to be quietly growing.
Guess who's back? 🎶 Gootloader's back. Again. New evasion tricks. New persistence chain. Same legal-themed lures. Big props to @RussianPanda9xx & @HuntressLabs for catching this one early. Details: gootloader.wordpress.com/2025/11/05/goo… #gootloader #malware #JavaScript #powershell
Example: IDA + DIE — Decode XOR data directly in DIE’s data convertor. A fast workflow for efficient malware analysis. #MalwareAnalysis #XOR #ReverseEngineering #DIE #IDA
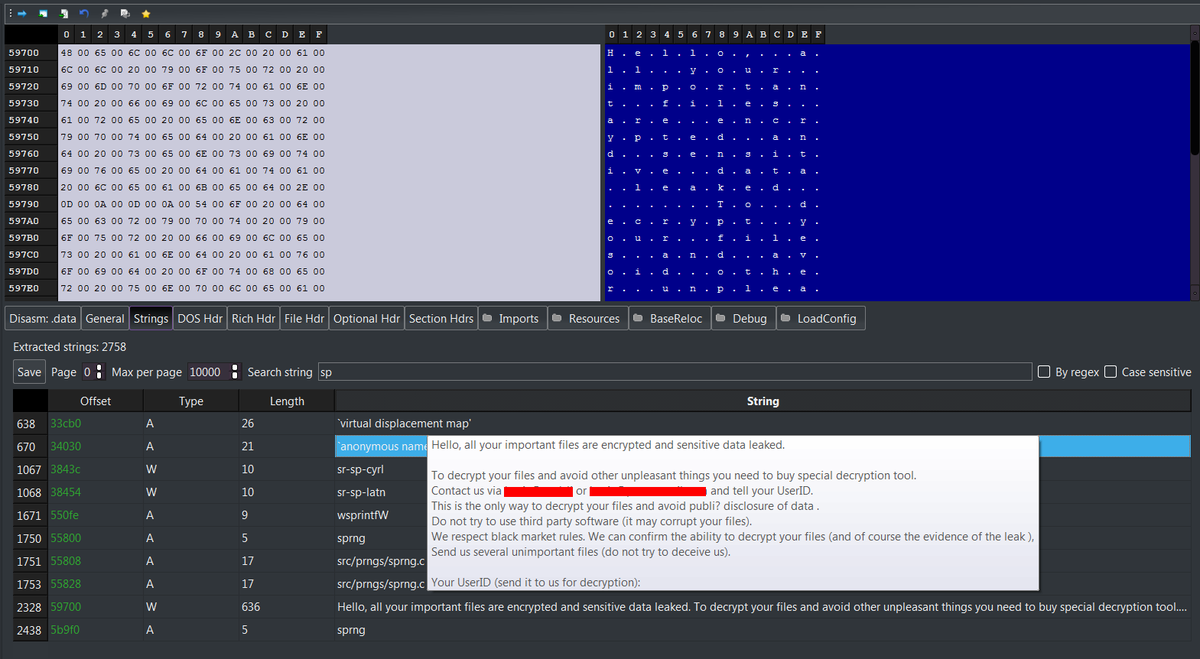
PE-Bear reveals the embedded RansomNote via its string hover preview — a practical highlight that makes it perfect for quick visual triaging. 💙
Example: PE-Bear: Using New Instances for Multiple Incident Response and Analysis Tasks A new instance isn’t just another window — it’s a separate task. Switch between analyses seamlessly and resume work instantly, staying focused and building efficient habits.
A new approach to static analysis with AI that turns days of research into hours. No MCP or live IDA required. Using GPT-5, we completely cracked XLoader v8, one of the most challenging malware families to analyze. #XLoader #MalwareAnalysis #AI research.checkpoint.com/2025/generativ…
United States 趨勢
- 1. Caleb 52.9K posts
- 2. Bears 75.9K posts
- 3. Packers 62.8K posts
- 4. #GoPackGo 11.1K posts
- 5. Jeff Kent 4,253 posts
- 6. Ben Johnson 6,178 posts
- 7. Notre Dame 164K posts
- 8. Nixon 13.6K posts
- 9. DJ Moore 2,845 posts
- 10. Raiders 33.7K posts
- 11. Browns 78.2K posts
- 12. Shedeur 108K posts
- 13. ESPN 119K posts
- 14. Kmet 1,425 posts
- 15. Parsons 6,422 posts
- 16. Ravens 50.4K posts
- 17. Stefanski 31.8K posts
- 18. Josh Jacobs 4,285 posts
- 19. Mattingly 2,781 posts
- 20. Jordan Love 12.7K posts
Something went wrong.
Something went wrong.