TechNadu
@TechNadu
Cutting through tech noise, covering #Cybersecurity, #VPNs | Real insights. Expert reviews. Daily threats decoded. #InfoSec #Privacy
قد يعجبك
👉 @grafana patched a CVSS 10.0 SCIM flaw (CVE-2025-41115) that could enable impersonation or privilege escalation when SCIM + user sync are enabled. Issue: numeric externalId values could override internal user IDs. Patched in latest enterprise builds. 💬 Thoughts? Follow…

🌍 @CISACyber added CVE-2025-61757 - a critical Oracle Identity Manager flaw - to its KEV list after signs of active exploitation. Attackers can bypass auth by appending ?WSDL or ;.wadl, hitting protected endpoints + achieving pre-auth RCE. Researchers say it may have been…

If an “agent” tells you to stay off the internet or not talk to anyone… that’s a major scam red flag. Scammers use fear + urgency to isolate you. ✔ Claim your name is tied to crimes ✔ Pressure you to act fast ✔ Tell you not to verify anything ✔ Ask you to “protect” your…

The @FCC voted 2–1 to reverse a telecom security rulemaking tied to the Salt Typhoon intrusions. Supporters say the earlier rule overextended authority; critics warn it could weaken protections for lawful intercept systems. 💬 Thoughts on balancing regulation & telecom security?…

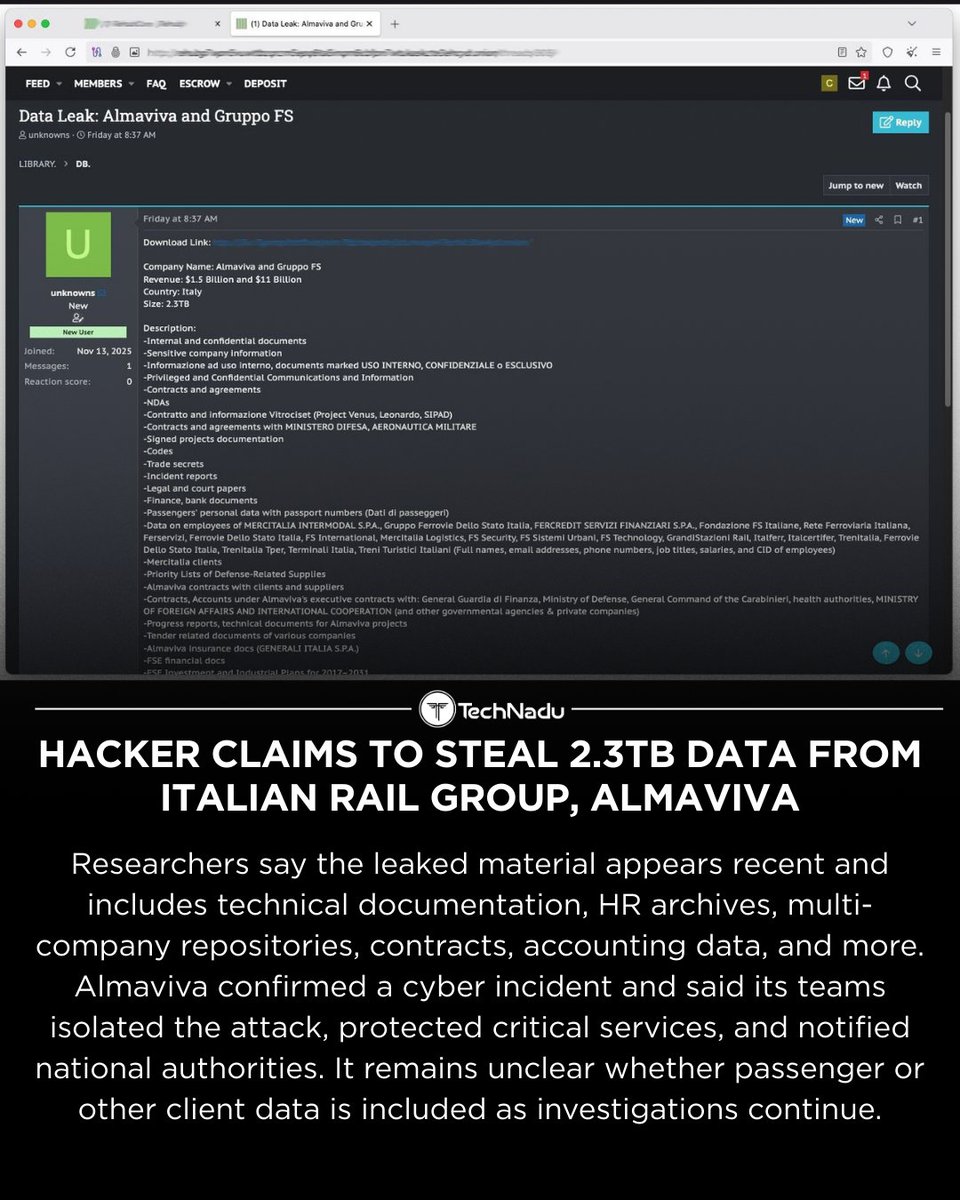
A hacker claims to have stolen 2.3TB of data from Italian rail IT provider Almaviva - impacting FS Italiane Group. Analysts say the files look recent and include internal shares, HR archives & technical docs. Almaviva confirmed a cyber incident but says critical services stayed…
The PCLOB has clarified that the @FBI does not buy real-time location data for counterterrorism cases - but does use historical data from brokers like Babel Street. The report frames open-source info as a “least intrusive” investigative method, raising questions about privacy +…

The SEC has dropped its lawsuit against @solarwinds and its CISO - a case that fueled big discussions about cybersecurity disclosures and regulatory expectations. SolarWinds says the outcome supports its position and may ease industry concerns. How should cyber risks be…

Two teenagers accused in relation to the TfL cyberattack have pleaded not guilty in court. The NCA says investigations also extend to possible links with attacks on U.S. healthcare organizations. Legal restrictions apply - meaning no speculation about guilt. Thoughts on how…

Fairplay is urging parents to be cautious with AI-powered toys this holiday season. Concerns include: privacy risks, sensitive data collection, inappropriate chatbot replies, and young children forming false “friendships” with AI. Some toys - like FoloToy's Kumma bear - were…

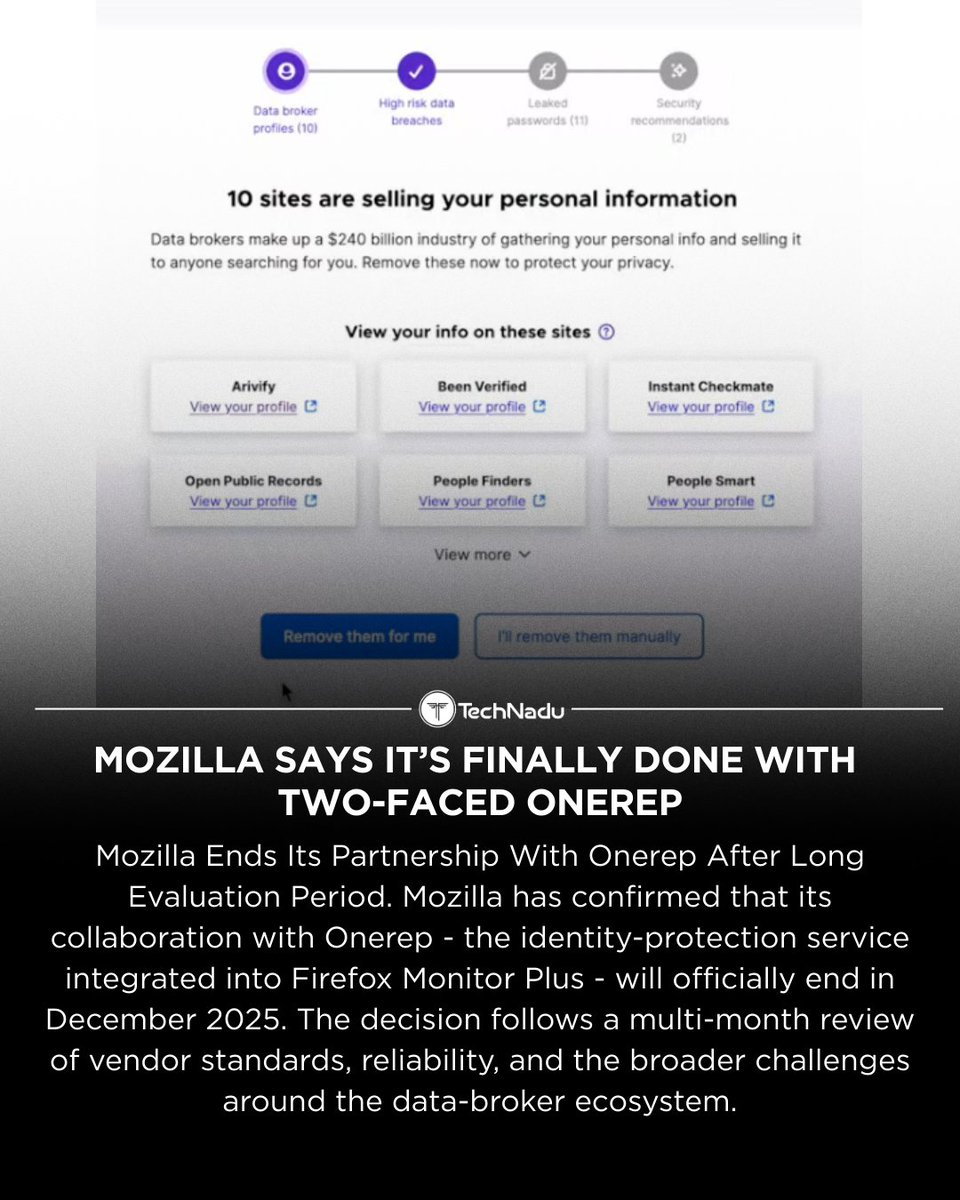
Mozilla says its partnership with Onerep is ending in Dec 2025, following a long review of vendor standards and the challenges of the data-broker ecosystem. Highlights ⬇️ • Monitor Plus will be discontinued • Breach alerts in Firefox will continue • Subscribers get prorated…
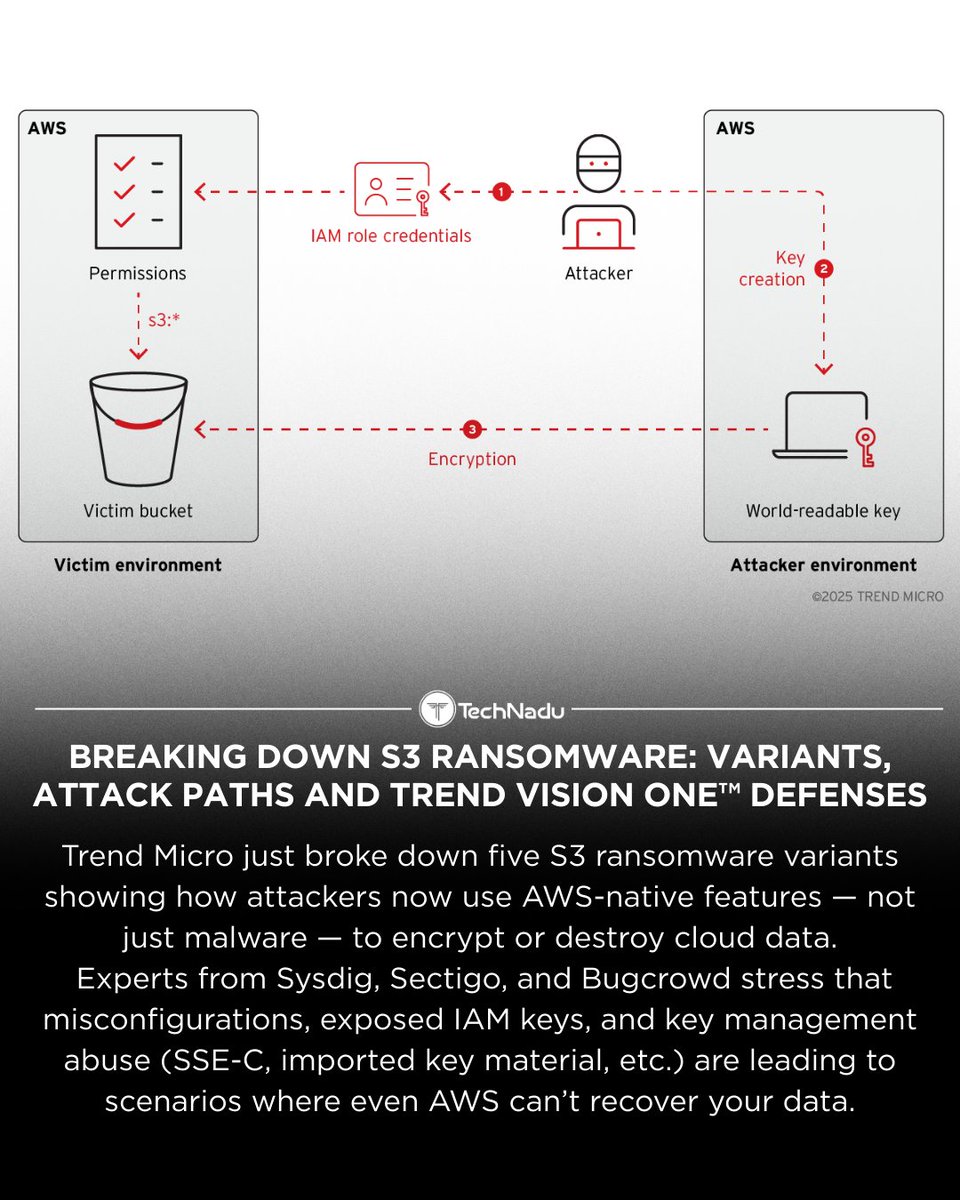
Cloud ransomware is evolving - and experts warn that S3, KMS, SSE-C, and imported key material abuses are becoming real-world attack paths. Key shifts ⬇️ • Attackers treat AWS as the ransomware mechanism • Misconfigs + exposed IAM keys remain common entry points • New S3…
United States الاتجاهات
- 1. Syracuse 5,558 posts
- 2. #UFCQatar 68K posts
- 3. Harden 25.7K posts
- 4. Arman 20.5K posts
- 5. Belal 9,905 posts
- 6. Ian Garry 8,215 posts
- 7. Mercer 2,856 posts
- 8. Fran Brown N/A
- 9. Mizzou 5,991 posts
- 10. Dan Hooker 5,988 posts
- 11. Makai Lemon 1,019 posts
- 12. Deuce Knight 1,817 posts
- 13. Malik Benson N/A
- 14. #GoIrish 3,750 posts
- 15. Mike Washington N/A
- 16. Stoops N/A
- 17. Oklahoma 23.1K posts
- 18. Andrew Marsh N/A
- 19. Arbuckle 1,838 posts
- 20. Mateer 2,718 posts
قد يعجبك
-
 Neha Dwivedi
Neha Dwivedi
@nehadw -
 軍聞社 Military News Agency, ROC(Taiwan)🇹🇼
軍聞社 Military News Agency, ROC(Taiwan)🇹🇼
@mna_roc -
 Recycle India
Recycle India
@recycleindia -
 Sundeep Kishan
Sundeep Kishan
@sundeepkishan -
 OpenVPN Inc.
OpenVPN Inc.
@OpenVPN -
 RJ Balaji
RJ Balaji
@RJ_Balaji -
 CARS24 India
CARS24 India
@cars24india -
 XR Today
XR Today
@Xrtoday -
 Kiran Mazumdar-Shaw
Kiran Mazumdar-Shaw
@kiranshaw -
 FEG (Feed Every Gorilla)
FEG (Feed Every Gorilla)
@FEGtoken -
 Blockchain Daily News
Blockchain Daily News
@blckchaindaily -
 Google Cloud India
Google Cloud India
@GoogleCloud_IN -
 theapache64
theapache64
@theapache64 -
 AR Insider
AR Insider
@ArInsider -
 Simulation
Simulation
@simulationshow
Something went wrong.
Something went wrong.