You might like
As a seasoned Go developer our CTO, Mikhail Swift, recently explored the transformative impact of the much-awaited generics feature in Go 1.18 through a compelling use case within our Witness project. See what he learned in the full blog post: buff.ly/3S5BvmM

Make sure to head over and star it today to ensure you stay updated with project updates and information. We have room for more "relationships". 😉 Join the #witness community - buff.ly/3JFu7tG #supplychain #cybersecurity #repo #github

At TestifySec, we're passionate about #softwaresecurity and #supplychainsecurity. But we're also passionate about our families. As the holiday season approaches, remember to prioritize the people who matter most. #familytime

Great blog post by @colek42c published on @testifysec website about comparing #intoto and @projectsigstore; you will find very niche details about them; don't forget to read it 👇 testifysec.com/blog/sigstore-…
Introducing Archivista, a server-side app that helps businesses securely manage their software supply chain data. Protect your supply chain and make confident, informed decisions. Visit our website or contact us to schedule a demo. testifysec.com/blog/secure-su…

In the land of TestifySec, Our products do protect, Witness and Archivista, Together a perfect pair, To help secure your software, From source to production fair, And Judge to enforce the rules, With policies that we can share, So come and try our tools, And join us in our quest
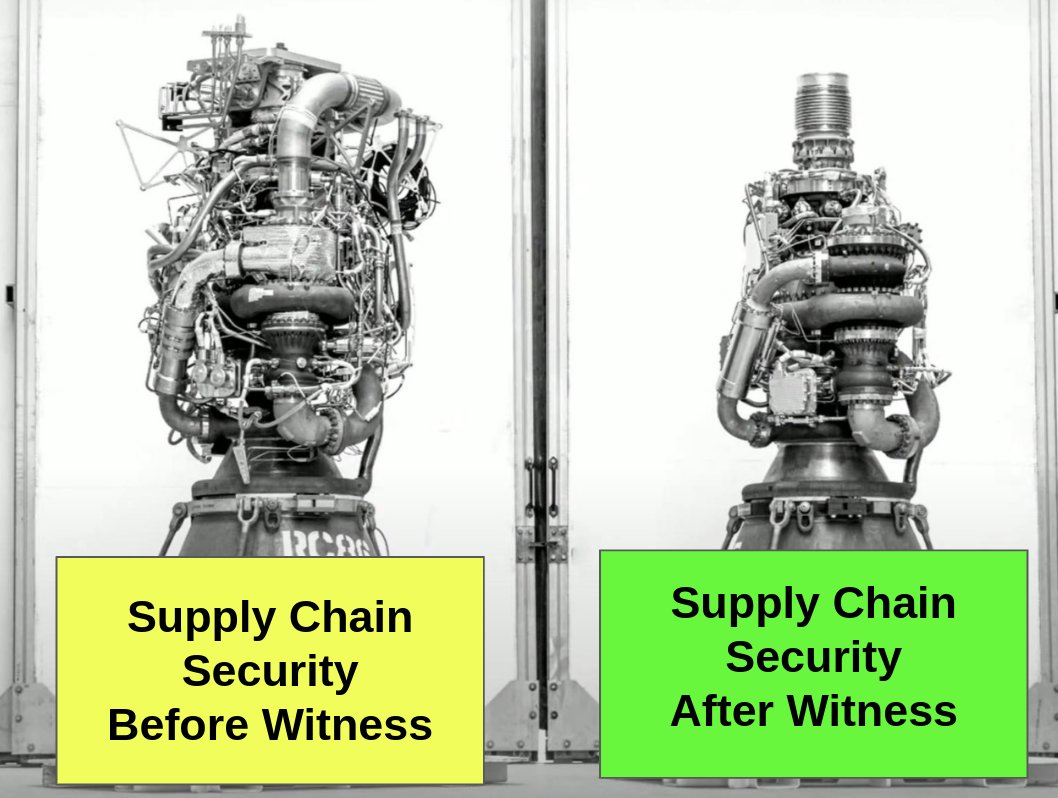
At @TestifySec we know that getting compromised can seriously affect organizations. That's why we're dedicated to securing the software supply chain and ensuring the integrity of the software being developed. Don't let your software become a vulnerability - trust TestifySec.

There needs to be more clarity in the Software Supply Chain Security space In our latest blog article, We talk about the differences between in-toto and @projectsigstore, and when it is appropriate to use each. testifysec.com/blog/sigstore-…
In-toto vs. sigstore: what are they and how do they differ? 🧵 👇 @projectsigstore @torresariass #intoto
You can now generate in-toto metadata via a GitHub action, thanks to @colek42c's work at @KubeCon_'s in-toto + TUF + @projectsigstore ContribFest! github.com/marketplace/ac…
Petition to start calling these GUESSBOMs! 💣💣💣
One under-appreciated problem with software bill-of-materials (SBOM) is that SBOMs that are recreated after build time - e.g. by software composition analysis [SCA] tools - are typically incomplete and have to make a best guess of the 'ingredients' of the software artifacts.
We just landed initial @witness_dev support for @github. This uses a preview build of Witness with #Archivist support. A GitHub attestor, and Keyless signing should drop before Kubecon. Let me know if you give it a whirl. github.com/testifysec/wit…
Have you ever wondered how to inventory all the dependencies in a software build? In this talk, I will showcase how end users can create and use #BPF traces to minimize #CVE false positives and negatives with @witness_dev and @ciliumproject #tetragon sched.co/1AOie

We are working on making supply chain security and compliance easy. Learn more at witness.dev @witness_dev
preview of our backend for @witness_dev. Amazing work by @mikhailswift/@ffkiv
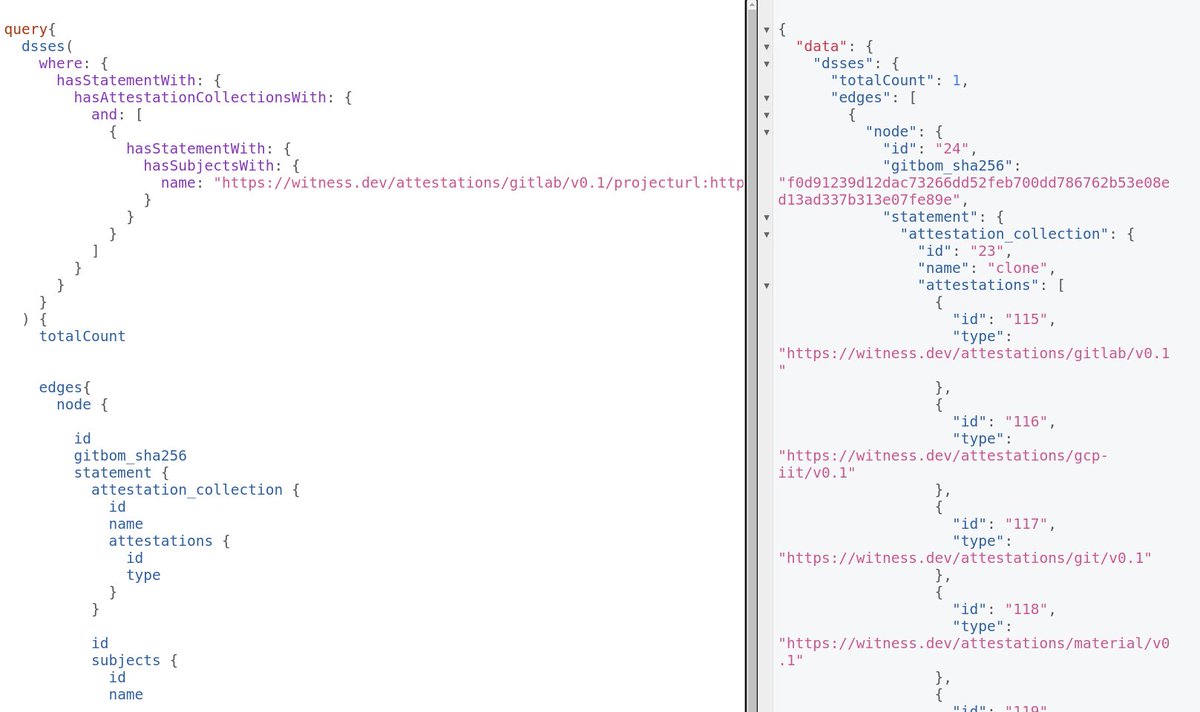
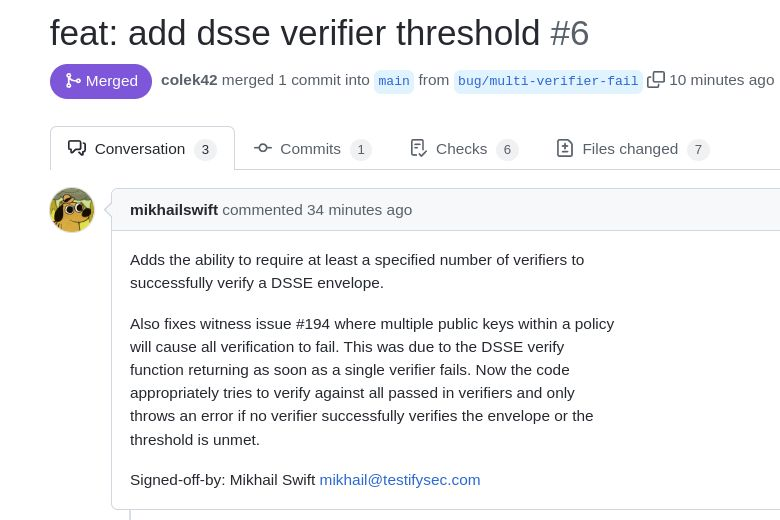
We had a user post an issue that hit an edge case we didn't test for. Our team fixed the issue the next business day, along with unit and integration tests. I couldn't be more proud of our engineering team led by @mikhailswift
I started adding support for the SPIRE delegated identity API to @witness_dev today. This lets us sign attestations based on the shasum of the CI command being run. Great work on this powerful API @SPIFFEio team!
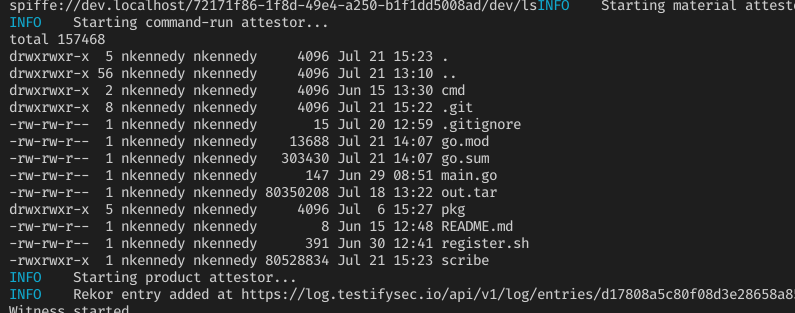
We use @SPIFFEio as a way to distribute trust, using remote attestation in our Judge platform. However, we don't expect our users to understand Spire, and spire registrations. We are making great progress on federating SPIRE and making registration easy. asciinema.org/a/ieVRO9nQ3AZx…
asciinema.org
untitled
Recorded by testifysec
United States Trends
- 1. Texas A&M 8,343 posts
- 2. South Carolina 9,758 posts
- 3. Jeremiyah Love 2,912 posts
- 4. Malachi Fields 1,028 posts
- 5. Marcel Reed N/A
- 6. Aggies 2,689 posts
- 7. Dylan Stewart N/A
- 8. #GoIrish 2,772 posts
- 9. Elko 1,686 posts
- 10. Randy Bond N/A
- 11. College Station 1,334 posts
- 12. Sellers 9,883 posts
- 13. Massie 106K posts
- 14. Mike Shula N/A
- 15. #NotreDame N/A
- 16. #GoBlue 2,079 posts
- 17. Underwood 1,890 posts
- 18. Northwestern 4,022 posts
- 19. Navy 28.4K posts
- 20. Zvada N/A
Something went wrong.
Something went wrong.