#softwaresecurity search results
Cyber Security from Zero to Expert A Complete Paid Course Free for 24 Hours⏰ This will help you crack your dream role Only for the First 500 People🫣 Retweet & Reply "NEED" to get it for free. [MUST FOLLOW] @Shipon_40AI so that I can DM you.
![Shipon_40AI's tweet image. Cyber Security from Zero to Expert
A Complete Paid Course Free for 24 Hours⏰
This will help you crack your dream role
Only for the First 500 People🫣
Retweet & Reply "NEED" to get it for free.
[MUST FOLLOW] @Shipon_40AI so that I can DM you.](https://pbs.twimg.com/media/G5AFU6QasAApfxA.png)
[CVE-2025-64492: HIGH] SuiteCRM versions 8.9.0 and below have a time-based blind SQL Injection vulnerability, allowing attackers to access sensitive data. Ensure to update to version 8.9.1 for the fix.#cve,CVE-2025-64492,#cybersecurity cvefind.com/CVE-2025-64492
![CveFindCom's tweet image. [CVE-2025-64492: HIGH] SuiteCRM versions 8.9.0 and below have a time-based blind SQL Injection vulnerability, allowing attackers to access sensitive data. Ensure to update to version 8.9.1 for the fix.#cve,CVE-2025-64492,#cybersecurity cvefind.com/CVE-2025-64492](https://pbs.twimg.com/media/G5MyQ9SXEAAVD-N.jpg)
Este repositorio es una joya. Te da todos los pasos e instrucciones para proteger y asegurar tu servidor Linux. Perfecto por si tienes un servidor propio o VPS: github.com/imthenachoman/…

☁️ A Compilation of Cloud Security Resources Github: github.com/senaykt/cloud-… author: @sena_yakutt #infosec


XBOW raised $117M to build AI hacking agents. Now someone just open-sourced it for FREE. Strix deploys autonomous AI agents that act like real hackers - they run your code dynamically, find vulnerabilities, and validate them through actual proof-of-concepts. Why it matters:…
[CVE-2025-64495: HIGH] Cybersecurity alert: Open WebUI versions 0.6.34 and below are vulnerable to DOM XSS. Update to version 0.6.35 to fix this issue and enhance your online security.#cve,CVE-2025-64495,#cybersecurity cvefind.com/CVE-2025-64495
![CveFindCom's tweet image. [CVE-2025-64495: HIGH] Cybersecurity alert: Open WebUI versions 0.6.34 and below are vulnerable to DOM XSS. Update to version 0.6.35 to fix this issue and enhance your online security.#cve,CVE-2025-64495,#cybersecurity cvefind.com/CVE-2025-64495](https://pbs.twimg.com/media/G5MyOemWIAADS_c.jpg)
[CVE-2025-10230: CRITICAL] Critical flaw in Samba's WINS hook handling allows remote command execution by passing unsanitized data from registration packets to a shell. Vulnerable to network attackers.#cve,CVE-2025-10230,#cybersecurity cvefind.com/CVE-2025-10230
![CveFindCom's tweet image. [CVE-2025-10230: CRITICAL] Critical flaw in Samba's WINS hook handling allows remote command execution by passing unsanitized data from registration packets to a shell. Vulnerable to network attackers.#cve,CVE-2025-10230,#cybersecurity cvefind.com/CVE-2025-10230](https://pbs.twimg.com/media/G5Mybl7X0AAX5F_.jpg)
Software verification is a MUST. If you value your privacy & security and don't know how to verify software, you're NGMI. "And what's so dangerous about it?" > lost crypto funds > stolen credentials > worst case - control over your whole operating system

Very cool book teaching security hardening for compilers, linkers, JITs and assemblers Low-Level Software Security for Compiler Developers: llsoftsec.github.io/llsoftsecbook/ #cybersecurity
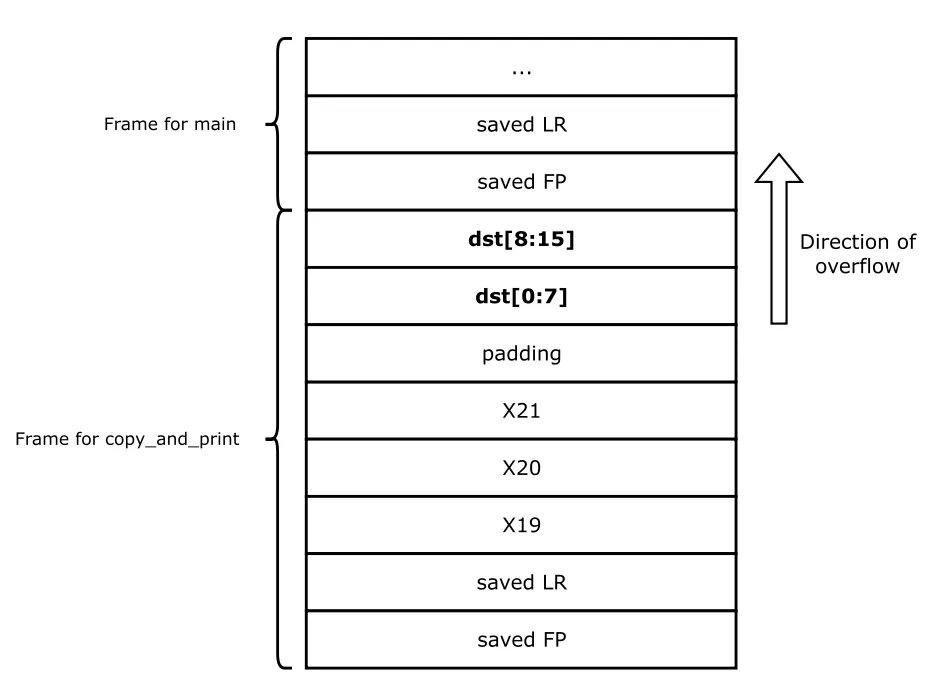

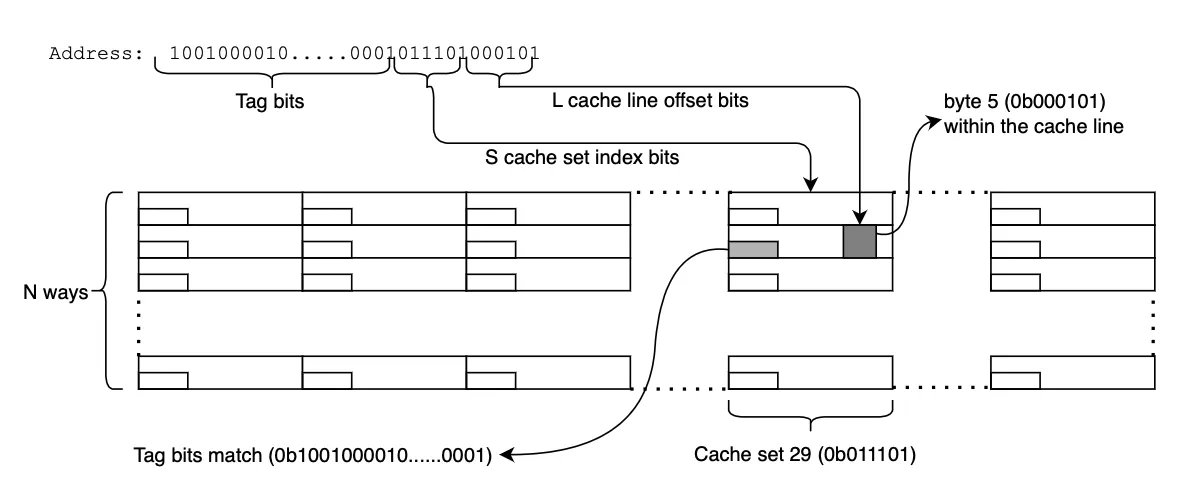
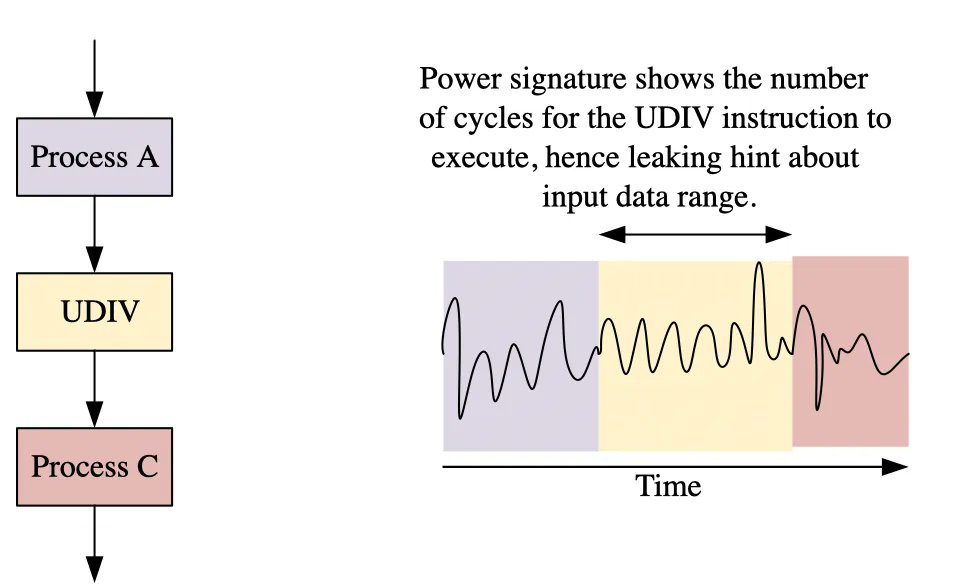
building apps is easy; securing them is the hard part. > this is the field guide for devs who want to defend against real-world attacks. > a must-read if you ship code to the web

Day 52: Going through an old repository github.com/solana-foundat… to understand common exploits
The field of Cybersecurity is growing - and no wonder with the ever-present threat of attacks these days. So if you want to show potential employers you know your stuff, there are some certifications you should consider. Here, Manish shares his top cert picks and why they're…

Excellent free book teaching security hardening for compilers, linkers, JITs and assemblers Low-Level Software Security for Compiler Developers: llsoftsec.github.io/llsoftsecbook/ #cybersecurity #compilers


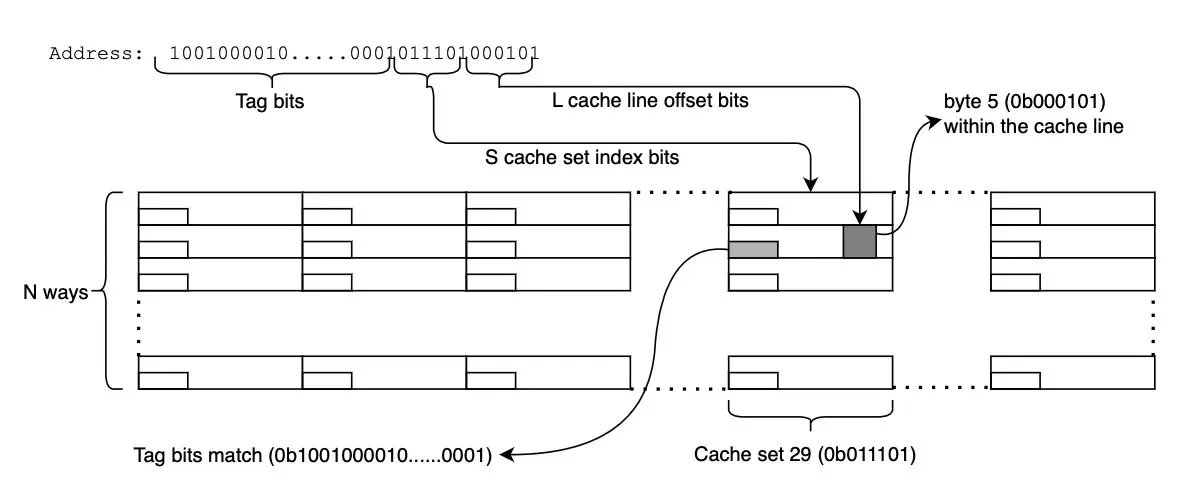
We’re excited to welcome Aleksandr Kolchanov, Independent Researcher, as he explores how attackers compromise web installers to inject malicious code and evade controls. #CyberSecurity #SoftwareSecurity #Infosec #Malware #ThreatIntel

Ransomware doesn’t just disrupt your operations—it can halt them altogether by locking you out of critical systems. Discover how to strengthen your #Security with smart strategies from trusted partners. dy.si/P8N4G

When you need to understand what's in your embedded software, a file-based SBOM that doesn't require a package manager is the way to go. runsafe.ly/3KnUUxD #SBOM #SoftwareSecurity #EmbeddedSoftware #AppSec

At Glog.AI, we prioritize Software Security. Our AI-powered platform ensures seamless code protection by automatically detecting and resolving vulnerabilities throughout the development phase. With our solution, your team can accelerate product innovation while…
Application Security Cheat Sheet: A list of cheat sheets for application security 0xn3va.gitbook.io/cheat-sheets/ #cybersecurity #bughunting #hacking #malware #exploit

⚡AI is quickly changing how software is built, but speed without security is risky. In @TechStrongTV, our CEO @PieterDanhieux shares why empowering developers & embedding security everywhere is essential: ow.ly/gHAy50XoJgk #AIDevelopment #SoftwareSecurity #DevOps
⏰ Deadlines slowly approaching and we are looking forward to your submissions! The 4th edition of MSR4P&S will be once more co-located with @SANERconf 2026 in Limassol, Cyprus 🇨🇾 🌎 More information in our website: msr4ps.github.io #softwaresecurity #ai #genai #cfp

🛡️ 𝐆𝐞𝐭 𝐓𝐡𝐞 𝐃𝐨𝐃 𝐂𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐏𝐨𝐥𝐢𝐜𝐲 𝐂𝐡𝐚𝐫𝐭 𝐓𝐨𝐝𝐚𝐲! The chart features over 200+ polices and is updated regularly to bring you the most current information. Click here: buff.ly/3LOEyMa. #cybersecurity #softwaresecurity #datasecurity
Embracing the idea that we can share evidence (a key fragment was used) without ever having to share the key fragment. Digging into ineffable crypto chat with Mike Loewy from TideCloak #DevSecOps #SecureCoding #SoftwareSecurity #AppSec
🔒 Secure Software Coding: Best Practices for Protecting Your Applications Enroll now! tinyurl.com/2s3d93p Click to Join WhatsApp shorturl.at/Uqswx 🎞️ Subscribe YouTube bit.ly/31R9zZt #SecureCoding #SoftwareSecurity #Cybersecurity #Omni_academy

Turn your indie projects into trusted software. Sign your code, show your identity, and make every download safe and professional. Product Link - tinyurl.com/comodo-individ… #CodeSigning #comodo #SoftwareSecurity #indiedevs #indiedeveloper

The GlassWorm campaign targeting Open VSX infected VS Code extensions with malware stealing data and crypto. Malicious extensions removed, tokens revoked, and automated scans enhanced security. #GlassWorm #OpenVSX #SoftwareSecurity ift.tt/ljcLFKA
Catch up on Emproof insights on YouTube 🎥 Webinars, recaps & the latest in code protection and embedded security. 👉 youtube.com/channel/UC8zEy… #CyberSecurity #SoftwareSecurity #ReverseEngineering #AppSec #EmbeddedSecurit
We’re excited to welcome Aleksandr Kolchanov, Independent Researcher, as he explores how attackers compromise web installers to inject malicious code and evade controls. #CyberSecurity #SoftwareSecurity #Infosec #Malware #ThreatIntel

🚀 The Fuzzing Educational Course is now publicly available! This comprehensive course covers techniques and tools for fuzzing in various languages such as Python, Go, Rust, Java, and Web. github.com/raminfp/the-ar… #Fuzzing #SoftwareSecurity #Education

Reet Kaur, author of 97 Things Every Application Security Professional Should Know, will be presenting. It is a great chance to get insights & a signed copy! Grab the book 👉 ow.ly/wIYB50WTl78 Register 👉 ow.ly/xnBm50WTl79 #AppSec #CyberSecurity #SoftwareSecurity

⏰ Deadlines slowly approaching and we are looking forward to your submissions! The 4th edition of MSR4P&S will be once more co-located with @SANERconf 2026 in Limassol, Cyprus 🇨🇾 🌎 More information in our website: msr4ps.github.io #softwaresecurity #ai #genai #cfp

Amazing discussion around #opensourcesecurity #softwaresecurity between @mehimansu @juliangordonhk8 at @openssf meet @CRED_club @snyksec

Stay updated! Enable automatic software updates to protect against cyber threats. Keep your devices secure. 🛡️#SoftwareSecurity #CyberSafetyTips #DigitalIndia

Navigate your training path, conquer certification, and propel your #SoftwareSecurity career with #CSSLP and ISC2! Download The Ultimate Guide for insights and success strategies: ow.ly/zYqY50UzRUC #CybersecurityCertification

Market forces have sidelined #softwaresecurity, leaving software vulnerable. Industry needs to develop a standard for creating software that is secure by design, says a paper from @AFCEA International and coauthored by the SEI’s Greg Touhill - insights.sei.cmu.edu/news/new-paper…

Updates are critical to keeping your software secure. Never ignore update notifications - they protect you from new threats. #SoftwareSecurity #UpdateNow #StaySafe #doitcraj

Why prioritize software security? The average cost of a data breach jumped to $4.88 million globally in 2024. Don’t be a statistic. Learn more: ow.ly/lkba50UYLjk #Cybersecurity #CSSLP #SoftwareSecurity

Introducing JFrog AppTrust. Security, governance, and visibility in every release. Trusted applications start here → bit.ly/42Qqb2e #SoftwareSecurity #DevSecOps

Mayhem takes the hard work out of building, maintaining, and optimizing your testing algorithms. This means your team can focus on developing great software while Mayhem ensures its quality: hubs.la/Q02YwyHM0 appsec #softwaresecurity #cybersecurity #MayhemSecurity

92% of UK IT leaders are deeply worried about email security, especially phishing attacks. 🔒 Our research shows that security credentials are crucial for brand trust in the software industry. 🌐 👉 bit.ly/3Fwu54w #ITLeaders #SoftwareSecurity

Just in 📩 92% of UK IT leaders are deeply worried about email security, especially phishing attacks. 🔒 Our research shows that security credentials are crucial for brand trust in the software industry. 🌐 👉 bit.ly/3Fwu54w #ITLeaders #SoftwareSecurity

#EclipseFdn head of security @mikbarbero discusses the findings from our new survey report software supply chain security practices in his new blog: hubs.la/Q01H3t4L0 #SoftwareSecurity #SLSA #opensource #softwaresupplychain

Stay updated! Enable automatic software updates to protect against cyber threats. Keep your devices secure. 🛡️#SoftwareSecurity #CyberSafetyTips #DigitalIndia

This recent blog post of ours delves into the principles of DevSecOps and the importance of shifting security left and making it an integral part of the entire development process: blog.codacy.com/what-is-devsec… #devsecops #softwaresecurity #codesecurity #shiftleft

Our CEO @jaimefjorge is participating in a great virtual event hosted by @TheLeadDev on February 14: "Balancing innovation and security in software development." Register today so you don't miss it! tinyurl.com/3c6xbdfu #softwaredevelopment #softwaresecurity #codequality

Looking for insights into software supply chain security practices? Our new whitepaper, co-authored with @Chainguard_dev, @TheOpenSSF, and @rust_foundation, has you covered. Read it here: hubs.la/Q01H8gqd0 #softwaresecurity #supplychainmanagement

It's official! AgileConnection is now StickyMinds! Follow @StickyMinds for the latest on #agile #DevOps #softwaresecurity #softwaretesting and much more!

Something went wrong.
Something went wrong.
United States Trends
- 1. #SmackDown 29.2K posts
- 2. Caleb Wilson 3,541 posts
- 3. Giulia 10.1K posts
- 4. Lash Legend 3,260 posts
- 5. #TheLastDriveIn 1,246 posts
- 6. #OPLive N/A
- 7. Chelsea Green 4,197 posts
- 8. Kansas 23.5K posts
- 9. Darryn Peterson 1,950 posts
- 10. Reed Sheppard N/A
- 11. Nia Jax 2,395 posts
- 12. #MutantFam N/A
- 13. #Dateline N/A
- 14. Rockets 17.5K posts
- 15. Tiller 4,152 posts
- 16. Georgetown 3,176 posts
- 17. End of 3rd 1,364 posts
- 18. Dizzy 12.5K posts
- 19. Vesia 6,506 posts
- 20. Tar Heels 1,016 posts












































