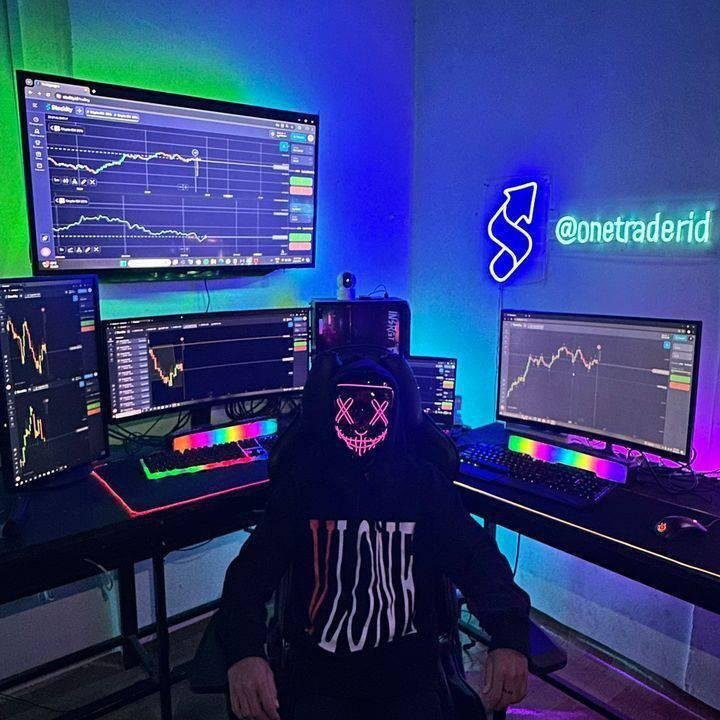
🚀 Seriously building a 5-person founding team. We're killing a daily pain point for millions. The Problem: A repetitive, high-friction task that wastes hours for knowledge workers. The Solution: A beautiful, minimal B2C SaaS with a clear path to revenue.
Test every URL parameter from 5 years ago.That old debug=true or api_version=1 parameter might still be supported and disable modern security controls.
Turn verbose errors into a blind data extraction tool. Time-based SQLi is for amateurs. Use the error message itself as your oracle for faster data exfiltration. #SQLInjection
The client-side validation you see is a suggestion. The server-side validation is the law. But sometimes the police are on vacation. Always replay modified requests. #LogicFlaw
New features inherit old permissions. That 'secure' new API endpoint might be using the permission model from 2018. Progress creates backdoors. #API #Authorization
Patience pays. Monitor for subdomain takeovers LONG after a service is discontinued. Devs forget DNS entries, leaving cloud instances ripe for claiming months later. #OSINT #InfoSec
Test business logic at 3 AM. Payment systems and fraud checks often have different rules during off-hours. Race conditions and logic flaws love the quiet of the night. #RedTeam
Master cache poisoning via unkeyed headers. It's a scalpel, not a hammer. Poison a single request and your payload gets served to thousands of users from the CDN. #WebAppHacking
Stop just fuzzing for endpoints. Read the client side JavaScript. SPAs are full of deprecated, forgotten, but still active API routes with minimal auth. The low hanging fruit is in the source. #JavaScript #API
Elevate your SSRF game. It's not just about reading internal ports. The crown jewel is hitting cloud metadata services to steal IAM roles and access keys. #CloudSecurity #AWS
Listen to the clock. Timing attacks on login systems are still wildly effective. A 50ms difference between a valid and invalid user is a gaping hole in 'secure' auth. #Vulnerability
JWT 'alg:none' is beginner stuff. The real flaws are in 'kid' header injection, 'jku' claim spoofing, and weak secret brute-forcing. Dive deeper than the scanner. #Hacking #ZeroDay
For Brokers: Liquidity isn't just depth; it's predictability. Use actuarial science to model user behavior under extreme volatility... The leading brokers are no longer just gateways; they are risk management engines. #ActuarialTrading #FinTech #RiskManagement
For Traders: Forget chasing pumps. The edge is in derivatives and liquidity provisioning . The math for sustainable yield is in Automated Market Makers (AMMs) and Options Finance (OpFi). Your strategy shouldn't be a guess; it should be a continuously validated algorithm. #DEFİ
United States 트렌드
- 1. Godzilla 25.3K posts
- 2. Shabbat 3,013 posts
- 3. Trench 7,630 posts
- 4. $DUOL 2,673 posts
- 5. Brujas 27.9K posts
- 6. Barca 99.7K posts
- 7. Lamine 66.6K posts
- 8. Brugge 49.3K posts
- 9. Barcelona 155K posts
- 10. #dispatch 40.8K posts
- 11. Richardson 3,474 posts
- 12. Flick 38.7K posts
- 13. Sharia 121K posts
- 14. Foden 22.2K posts
- 15. Captain Kangaroo N/A
- 16. Jared Golden 2,133 posts
- 17. Alastor 87.2K posts
- 18. Frey 29K posts
- 19. SCOTUS 37.3K posts
- 20. Anthony Taylor 1,871 posts
Something went wrong.
Something went wrong.