你可能會喜歡
We came, we stormed, we CONQUERED.🙌

#MiamiHerbert earned its highest placements to date in @usnews's 2026 rankings! Read more: news.miami.edu/miamiherbert/s…

App-Bound Encryption isn't stopping hungry attackers from getting into the cookie jar. 🍪 Join Andrew Gomez & Antero Guy at #BSidesDenver Sept 12 to learn how threat actors are still stealing browser secrets, plus a sweet EntraID cloud pivot bonus. ➡️ ghst.ly/45Bguqx

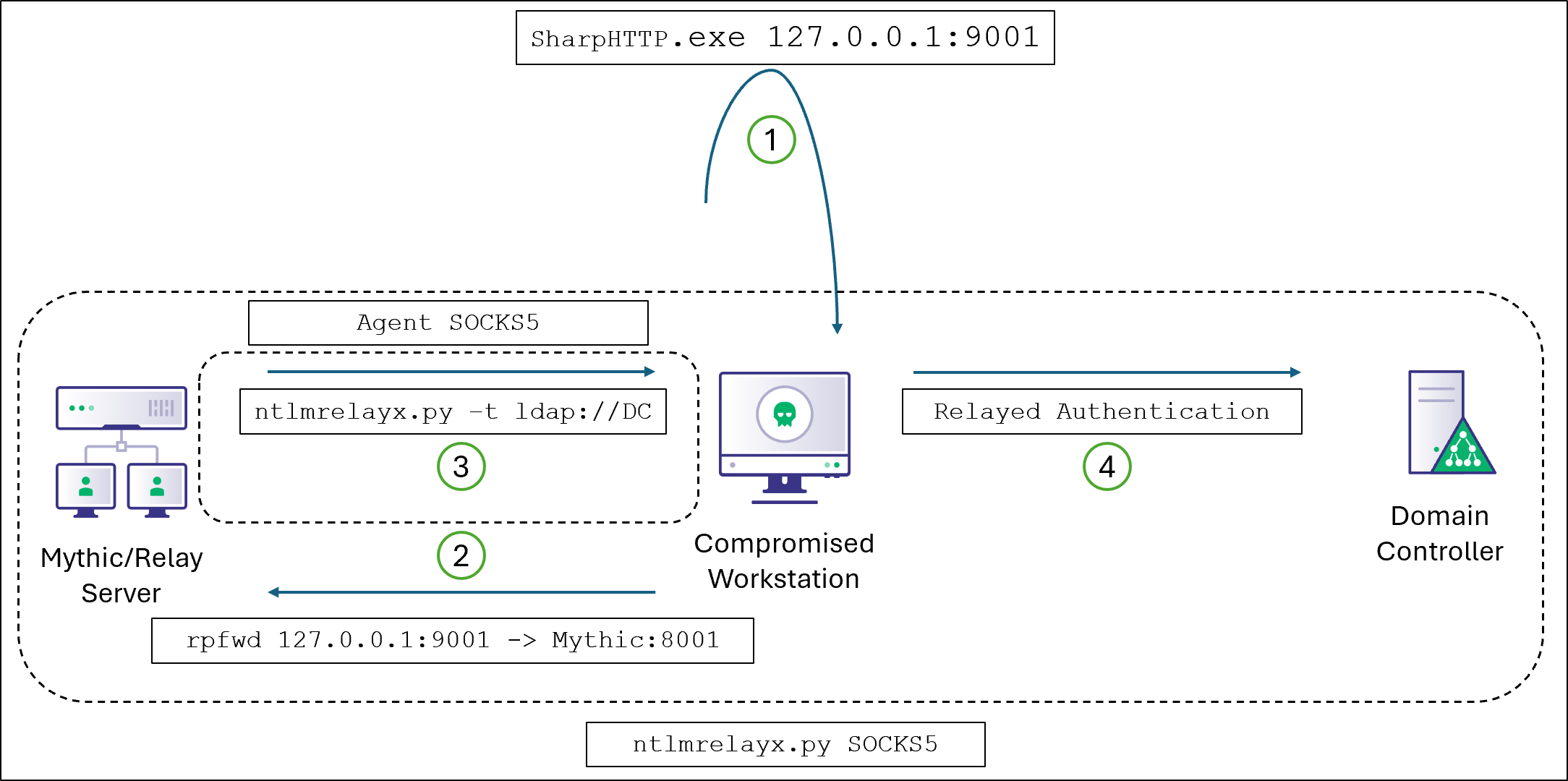
I Just documented a cool way to authenticate proxied tooling to LDAP in an AD environment using C2 payload auth context, without stealing any tickets or hashes! Keep tooling execution off-host and away from EDR on your Red Team assessments! specterops.io/blog/2025/08/2…
Trying to fly under EDR's radar? @_logangoins explains how to use HTTP-to-LDAP relay attacks to execute tooling completely off-host through the C2 payload context. Perfect for when you need LDAP access but want to avoid being caught stealing creds. ghst.ly/41mjMv7
New blog post just dropped! West Shepherd breaks down extending the Mythic Poseidon agent for ARM64 Dylib injection on Apple Silicon. Details include: ✅ Shellcode construction ✅ Memory allocation ✅ Runtime patching ✅ Thread creation Read more ⤵️ ghst.ly/41Nu4ED
Manual recon commands eating up your time? 🕐 @atomiczsec breaks down how Mythic Eventing automates those repetitive reconnaissance tasks during RTOs, complete with starter YAML scripts you can customize. ghst.ly/45jwYDr
🐺 It's time to unleash the hounds! @HugovdToorn & @joeydreijer are bringing BloodHound wizardry to Red Team Village at #DEFCON33. No shells to pop, no buffers to overflow; just a full-blown digital treasure hunt. Learn more: redteamvillage.io/defcon-33

⏰ 1 HOUR TO GO 🚨 Next Code Drop hits today at 4PM EDT! Don’t miss your chance to grab a ticket to the Red Team Village party at AREA15. Make sure you're following @redteamvillage_ — tickets go quick.
MSSQLHound leverages BloodHound's OpenGraph to visualize MSSQL attack paths with 7 new nodes & 37 new edges, all without touching the SharpHound & BloodHound codebases. @_Mayyhem unpacks this new feature in his blog post. 👇 ghst.ly/4leRFFn
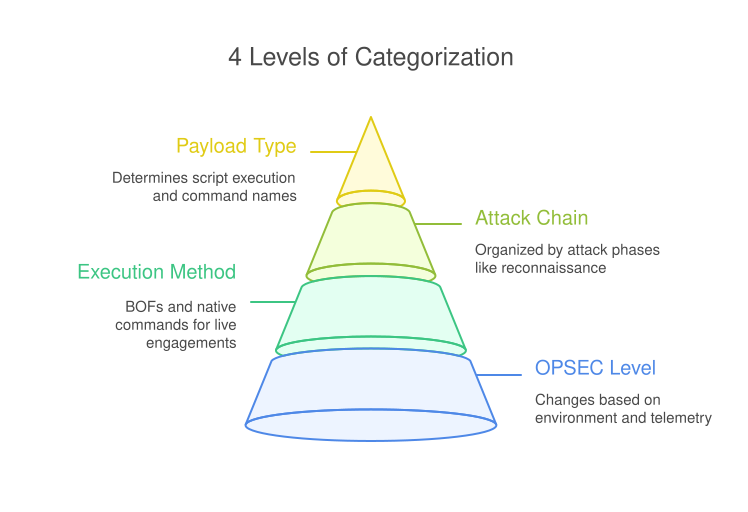
In this blog post I explain the fundamental building blocks, vocabulary, and principles of attack graph design for BloodHound: specterops.io/blog/2025/08/0…
🎯 Mythic, Ghostwriter, Nemesis, and Tying the Room Together – @th3d00rman shows how these tools streamline red team ops, automate data analysis, and make reporting less painful. Modern workflows that really “tie the room together” at @redteamvillage_ during @defcon 33! 🎳

Entra Connect sync accounts can be exploited to hijack device userCertificate properties, enabling device impersonation and conditional access bypass. @hotnops explores cross-domain compromise tradecraft within the same tenant. Read more ⤵️ ghst.ly/3ISMGN9
BloodHound v8.0 is here! 🎉 This update introduces BloodHound OpenGraph, revolutionizing Identity Attack Path Management by exposing attack paths throughout your entire tech stack, not just AD/Entra ID. Read more from @JustinKohler10: ghst.ly/bloodhoundv8 🧵: 1/7
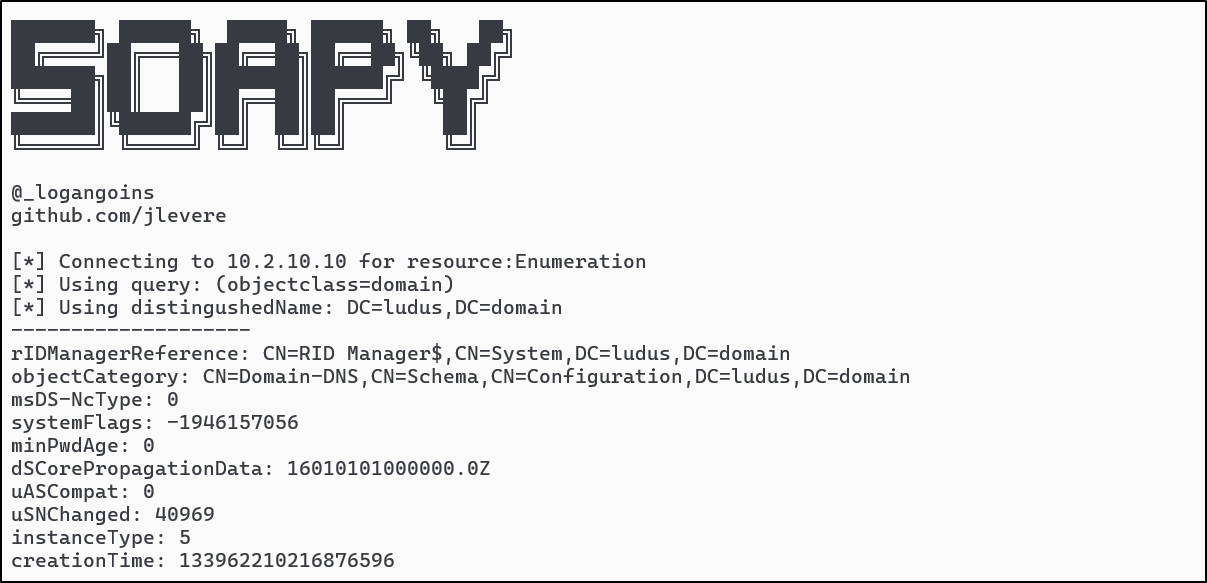
.@_logangoins is dropping knowledge on ADWS exploitation. 🧠 Learn how attackers use the SOAP protocol for LDAP collection on Domain Controllers & dive into maximizing OPSEC-considerate collection workflows while exploring detection methods. ghst.ly/4lPodH4
Thanks to our #DC33 sponsors! @Amazon @FlareSystems @KindoAI @WKL_cyber @AlteredSecurity #HTX @specterops @corelight_inc @hackinghub_io @HakaiOffsec @SynackRedTeam @threatsims @RedSeerSecurity @risk3sixty @CYQUEST_io @Optiv @JustHackingHQ @MaltekInfoSec @TheSecOpsGroup @Packtpub
Tried to write a short post on on MCP servers, how they can be vulnerable and some offensive cool MCP servers out there. medium.com/p/1ac7ffe82fb6 @RedSeerSecurity
🔴 Red and blue teams, this one's for you. 🔵 LudusHound bridges BloodHound Attack Paths with lab automation by creating a functional Active Directory replica testing environment. Read @bagelByt3s blog post for more. ghst.ly/40Ippn1
United States 趨勢
- 1. Jets 96.7K posts
- 2. Jets 96.7K posts
- 3. Justin Fields 17.3K posts
- 4. Aaron Glenn 7,175 posts
- 5. London 203K posts
- 6. Sean Payton 3,389 posts
- 7. Garrett Wilson 4,341 posts
- 8. Bo Nix 4,330 posts
- 9. #Pandu N/A
- 10. #HardRockBet 3,564 posts
- 11. Tyrod 2,447 posts
- 12. #DENvsNYJ 2,532 posts
- 13. HAPPY BIRTHDAY JIMIN 184K posts
- 14. #JetUp 2,501 posts
- 15. #OurMuseJimin 226K posts
- 16. Tyler Warren N/A
- 17. Breece Hall 2,390 posts
- 18. Waddle 1,783 posts
- 19. Bam Knight N/A
- 20. Folk 16.1K posts
Something went wrong.
Something went wrong.