내가 좋아할 만한 콘텐츠
Pump it !
Ascend
just 1 day after the announcement of Project Ascend, we've already seen: - $2,402,294 in creator fee claims - thousands of new streams - over 200,000 daily stream viewers this is just one small step towards MASSIVELY disrupting the global creator economy Ascend.
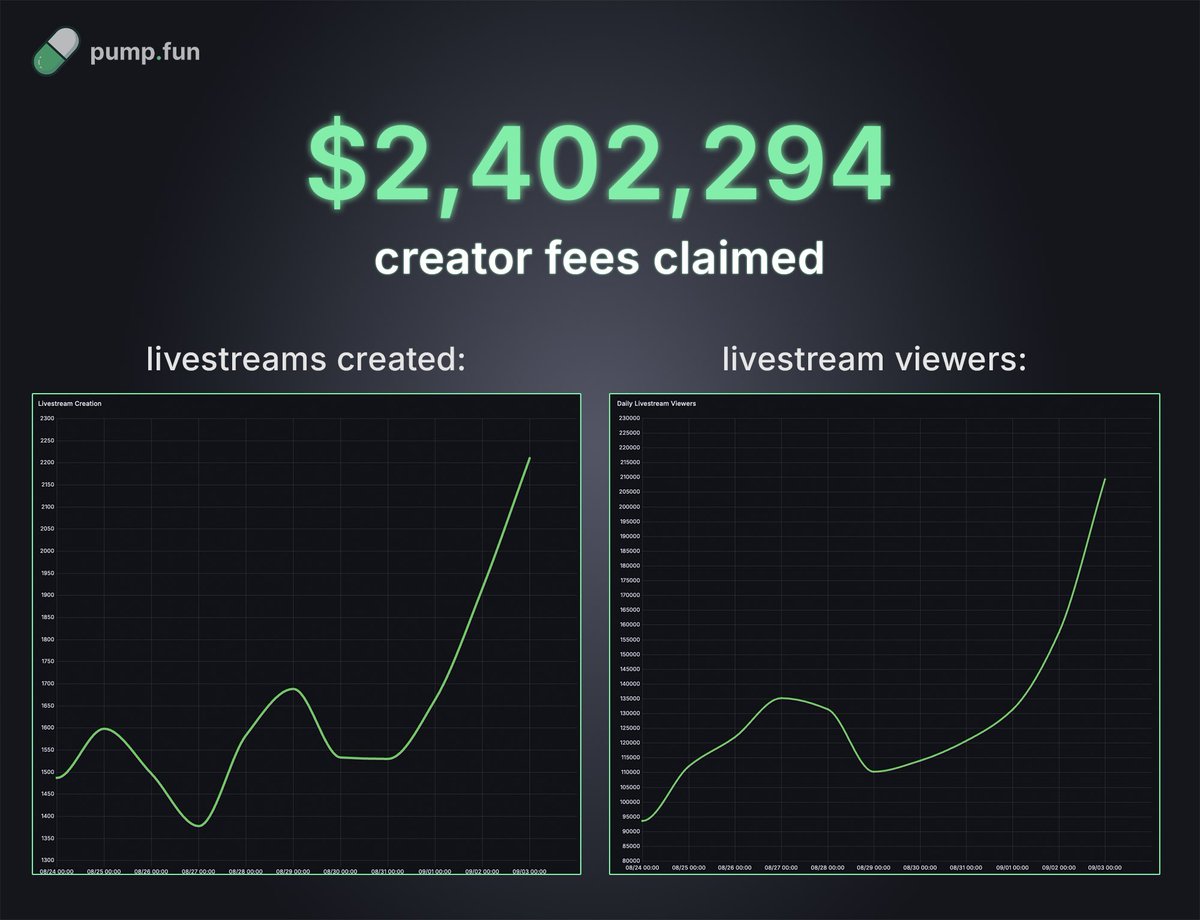
introducing Project Ascend, a series of updates that will 100x the pump fun ecosystem by making coins more sustainable & aligned with their communities to start: - 10x more creator earnings via Dynamic Fees - 10x faster processing of CTO Creator Fee applications learn more 👇
After 3 amazing years with one of the best teams I’ve worked with @phantom 👻, it’s time for a new chapter. Thrilled to be joining @pumpdotfun to help secure the Web3 ecosystem, and secure some memes along the way. Let’s build 🛡️💻
SMS-based MFA is consistently unreliable for security
What would you do if you could spy on SMS messages? @theredguild and @opsek_io have identified SLOVENLY COMET, a threat actor which has been intercepting OTP codes and other credentials sent over SMS to certain regions since as early as February 7, 2025 More info below 🔗

This isn’t just a glitch—it’s a blueprint for future CI/CD attacks. thehackernews.com/2025/03/github… Why does it matter now? Thousands of developers still rely on infected actions. The exploit may have been removed, but the attack method remains.
🚨 Security Alert: A new RAT (StilachiRAT) is targeting crypto wallets by stealing private keys and credentials via clipboard monitoring. 🔒 To protect yourself: ✅ Install and update antivirus software ✅ Avoid running unknown software ✅ Use a hardware wallet for better…
Microsoft Incident Response researchers uncovered a novel remote access trojan (RAT) that demonstrates sophisticated techniques to evade detection, persist in the target environment, and exfiltrate sensitive data. msft.it/6013qVXAl
Say goodbye to sneaky extensions! Google Chrome’s upcoming version 117 is set to introduce an innovative security feature. This feature will promptly alert users and automatically remove any installed extensions that turn malicious. androidpolice.com/hrome-117-deve….
Glad to share with you my recently discovered CVE-2020-25728 cve.mitre.org/cgi-bin/cvenam… A full write-up can be found here : amriunix.com/post/alfresco-… #CVE #cybersecurity #Alfresco
Distributed Remote Code Execution 😂😂😂 youtube.com/watch?v=EAzdGo… Thanks @ayoul3__ , you made my day!
youtube.com
YouTube
DEF CON Safe Mode - ayoul3 - Only Takes a Spark Popping a Shell on...
padding-oracle-attacker : CLI tool and library to execute padding oracle attacks easily (with support for concurrent network requests) : github.com/KishanBagaria/… cc @KishanBagaria
Corona or no corona, staying away from people is always a good idea 😂👌
Due to Corona virus all the TCP application will be transformed to UDP to avoid handshakes 🤔🤔🤔
My Advanced Cyber Threat Intelligence course is now available on @cybraryIT --> app.cybrary.it/browse/course/…
Why do i need a shell? when i can steal token! amriunix.com/post/windows-k… #exploitDev #shellcode #Windows10

XSS Challenge ended Solution: <?><svg onload=alert()> (see reply for explanation)
"from read@GLIBC to RCE in X86_64" I write a new post showing new technique of binary exploitation. amriunix.com/post/from-read…
CVE-2019-18276 - Suidbash - Walkthrough amriunix.com/post/cve-2019-… big thanks to @LiveOverflow
United States 트렌드
- 1. Cowboys 73.8K posts
- 2. #heatedrivalry 25.8K posts
- 3. LeBron 108K posts
- 4. Gibbs 20.4K posts
- 5. Pickens 14.6K posts
- 6. Lions 91.8K posts
- 7. scott hunter 5,474 posts
- 8. fnaf 2 26.5K posts
- 9. Paramount 20.4K posts
- 10. Warner Bros 22.1K posts
- 11. Shang Tsung 30.6K posts
- 12. #OnePride 10.6K posts
- 13. Brandon Aubrey 7,418 posts
- 14. Ferguson 11K posts
- 15. #PowerForce N/A
- 16. Eberflus 2,686 posts
- 17. CeeDee 10.6K posts
- 18. #criticalrolespoilers 2,105 posts
- 19. Cary 40.1K posts
- 20. Goff 8,752 posts
Something went wrong.
Something went wrong.