Aspasht
@aspasht
Before I wanted to know how it works but now I want to change the way it works.🇳🇵
You might like
Excellent blog post on bypassing Ubuntu’s Unprivileged Namespace Restriction by @u1f383 u1f383.github.io/linux/2025/06/… #infosec

"LLMs Solving a DEF CON CTF Finals Challenge" wilgibbs.com/blog/defcon-fi… Credits @cl4sm #infosec

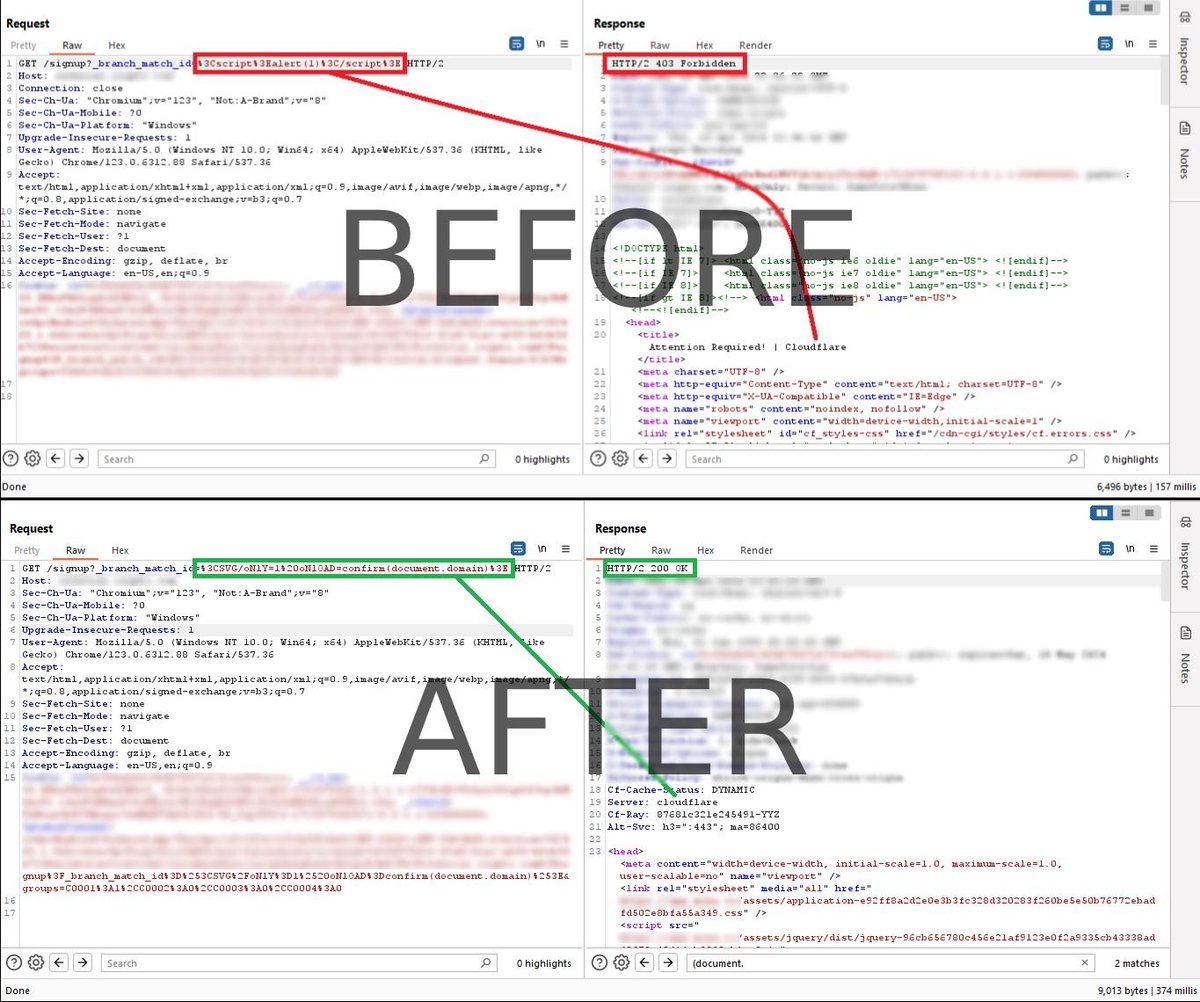
New XSS Bypass Cloudflare WAF 🧱 Payload : %3CSVG/oNlY=1%20ONlOAD=confirm(document.domain)%3E #BugBounty #XSS #Cybersecurity
Check out this awesome project on GitHub: Frida Gadget. A powerful tool that automates APK patching to integrate Frida Gadget by downloading the library and injecting code into the main activity🛠️ #Frida #ReverseEngineering github.com/ksg97031/frida…

IDA Free Step-by-Step Reverse Engineering Part 1 of our 12 part Patreon series unlocked❤️
नाति पुस्तालाई गोली हान्न आदेश दिने … सबैप्रति धिक्कार छ 😢 🙏🏼
This should be our demand!

When a SSRF is enough: Full Docker Escape on Windows Docker Desktop (CVE-2025-9074) blog.qwertysecurity.com/Articles/blog3… "How was it found It was by mistake actually, I did not know much about container separations and its implication"
🎉 Big news! 🚨 Next Nepal Cloud Meetup is happening on Aug 30! 🕓 2:00 PM – 4:00 PM NPT (UTC+5:45) | 🖥️ Online via Microsoft Teams.🔗 RSVP: meetup.com/nepalcloudpro/… #NepalCloudPro #MakuraCreations #Azure #GenAI #Networking #CloudSecurity 🚀 Don’t miss out!

🚀 Call for Speakers – Nepal Cloud Professionals Passionate about #AI, #DevOps, #Cloud, or #Cybersecurity? Speak at our upcoming meetups & inspire the community! 🗣️ ~30 min talk via MS Teams 📝 Apply: forms.office.com/r/cywefzeBAV #NepalCloudPro #Azure

Day 144 - Bug Bounty - Went today deep in authentication flows - Learned a lot about different edge cases using different encoding/null bytes - Found this repo, which constantly updates the best ATO H1 reports: github.com/reddelexc/hack… Total earned so far: $5425
HAPPENING TODAY! 📣 Nepal Cloud Meetup- July 2025! 🚀Are you excited?😍 🕓 Time: 2:00 PM – 4:00 PM NPT 📍 Venue: Microsoft Teams Let’s connect, learn, and grow together in the cloud community! 🌥️ #NepalCloudPro #MicrosoftCloud #Azure #PowerPlatform meetup.com/nepalcloudpro/…

Blog for ToolShell Disclaimer: The content of this blog is provided for educational and informational purposes only. blog.viettelcybersecurity.com/sharepoint-too… #SharePoint #ToolShell

I hope everyone got some rest after @DownUnderCTF this weekend. My colleague @hash_kitten wrote up a blog post on a novel technique for SQL Injection in PDO's prepared statements, required to exploit the “legendary” challenge, which only got one solve: slcyber.io/assetnote-secu…
slcyber.io
Novel SQL Injection Technique in PDO Prepared Statements
Searchlight Cyber's Security Research team details a Novel Technique for SQL Injection in PDO's Prepared Statements.
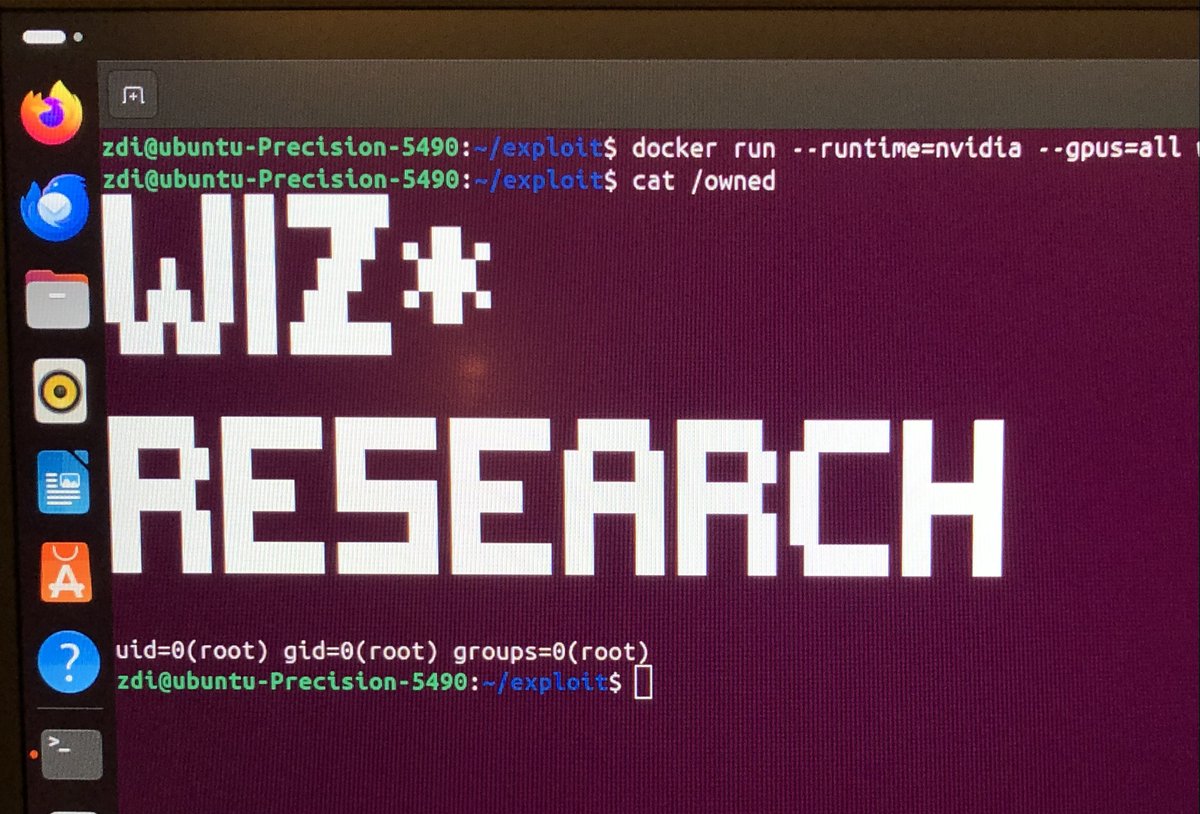
We found a new container escape affecting all container runtimes using @NVIDIA GPUs. The crazy part? The exploit is just three lines long 🤯 This is the story of #NVIDIAScape 🧵👇
XSS Tip: If you find <textarea> maybe for description or any other feature. Try the below payload. </textarea><img src=x onerror=alert()> This may trigger the XSS simple payload like this <img src=x onerror=alert()> will not work in this context. #bugbountytips
United States Trends
- 1. Thanksgiving 358K posts
- 2. Fani Willis 7,364 posts
- 3. Trumplican 2,241 posts
- 4. Golesh 1,346 posts
- 5. Hong Kong 71.3K posts
- 6. Elijah Moore N/A
- 7. Ruth 13.5K posts
- 8. #Wednesdayvibe 3,306 posts
- 9. #wednesdaymotivation 6,274 posts
- 10. Stranger Things 151K posts
- 11. Karoline Leavitt 26.9K posts
- 12. Nuns 9,756 posts
- 13. Mora 22.2K posts
- 14. Gretzky N/A
- 15. Khabib 5,175 posts
- 16. Good Wednesday 35K posts
- 17. Ribs 11.2K posts
- 18. #WednesdayWisdom 1,079 posts
- 19. Fulton County 1,950 posts
- 20. #BurnoutSyndromeSeriesEP1 265K posts
Something went wrong.
Something went wrong.