
boot2generic
@boot2generic
Generic by Nature | Security Researcher | Opinions here are my own
You might like
ShmooCon was fun, recommend checking out LetItGo, and ProcAid if you haven't.
Highly Recommend Adversary Tactics: Vulnerability Research for Operators training @SpecterOps, one of the best training formats I have seen. A lot of information to cover and they do a great job presenting it.
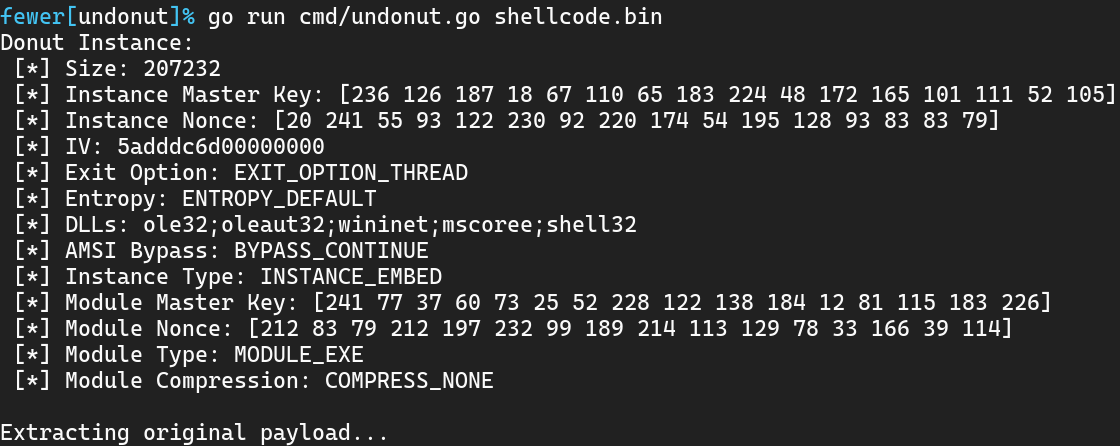
Weekend project - unpacking #donut payloads. @TheRealWover Et Al. have made something really groundbreaking, worth a look - github.com/TheWover/donut
New by me: 0DayAllDay Hackers Go Godzilla On Guardzilla To Reveal A Real Video Nasty via @forbes forbes.com/sites/daveywin… #IoT #cybersecurity #Rapid7 #0DayAllDay
Check out 0DayAllDay's latest blog. Where @kulinacs and @CharlesDardaman got their first CVE (CVE-2018-5560). Vulnerability is still present as the vendor never responded. 0dayallday.org/guardzilla-vid…
Just updated the spraying toolkit to support a custom OWA URL as the target. Also bugfixes! github.com/byt3bl33d3r/Sp…
*mind blown* F7 in cmd pops up an inline list of all the previous commands you've executed. Omg, I've used cmd for *decades* and never knew that!
Some sketchy firmware
Thanks to @kulinacs you can download firmware for both the TPLink and the Guardzilla that he ripped this morning at the #0DAYALLDAY event: github.com/kulinacs/0daya…
⛈️⛈️⛈️⛈️⛈️⛈️⛈️⛈️⛈️⛈️⛈️⛈️⛈️⛈️⛈️⛈️⛈️⛈️⛈️⛈️ securify.nl/advisory/SFY20… ⛈️⛈️⛈️⛈️⛈️⛈️⛈️⛈️⛈️⛈️⛈️⛈️⛈️⛈️⛈️⛈️⛈️⛈️⛈️⛈️
United States Trends
- 1. Alcaraz N/A
- 2. Shakur N/A
- 3. Djokovic N/A
- 4. Happy Black History Month N/A
- 5. #AustralianOpen2026 N/A
- 6. Good Sunday N/A
- 7. Career Grand Slam N/A
- 8. Muhammad Qasim N/A
- 9. #AO26 N/A
- 10. #AusOpen N/A
- 11. #LingOrmTaipeiFanmeeting N/A
- 12. LINGORM TP FANMEET N/A
- 13. And Mary N/A
- 14. Career Slam N/A
- 15. Carlitos N/A
- 16. #LENAMIUBorn2Shine N/A
- 17. Tank N/A
- 18. LENAMIU 1ST FAN MEETING N/A
- 19. Happy New Month N/A
- 20. Taylor Rehmet N/A
Something went wrong.
Something went wrong.



































































