你可能會喜歡
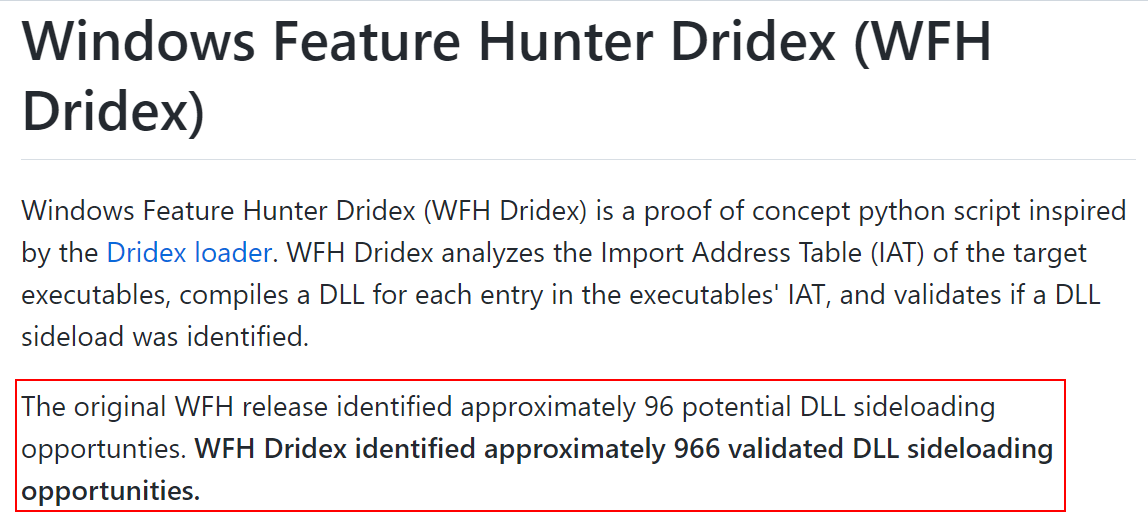
Today I'm releasing WFH Dridex, another approach to automatically identify and validate DLL sideloading opportunities inspired by the Dridex loader. I also submitted a pull request to @Wietze's HijackLibs project with 507 entries from C:\Windows\System32. github.com/ConsciousHacke…
🔥Fire research by the team! Great talk on compromising cloud AI providers via a GPU kernel 0day by Valentina Palmiotti (@chompie1337) & Samuel Lovejoy (@_dinolover38) youtube.com/watch?v=Lvz2_Z…
youtube.com
YouTube
HEXACON 2025 - CUDA de Grâce by Valentina Palmiotti & Samuel Lovejoy
Wish I could RT this 100x. There is no such thing as messing up with this stuff 👏🏼 Just delete the VM and start over with more knowledge than you did before
I am happy that you like my writeup! You should definitely try this challenge, you gonna learn a lot. And if you mess up, what is the harm? You can start over again. Just be patient with it and with yourself. The next #FlareOn13 is going to be next autumn
#MDE custom collection is finally in public preview! It's a centrally managed solution to improve visibility and detection opportunities. We're releasing a management tool and rule repository in YAML format to share new rules with the community. medium.com/falconforce/mi…

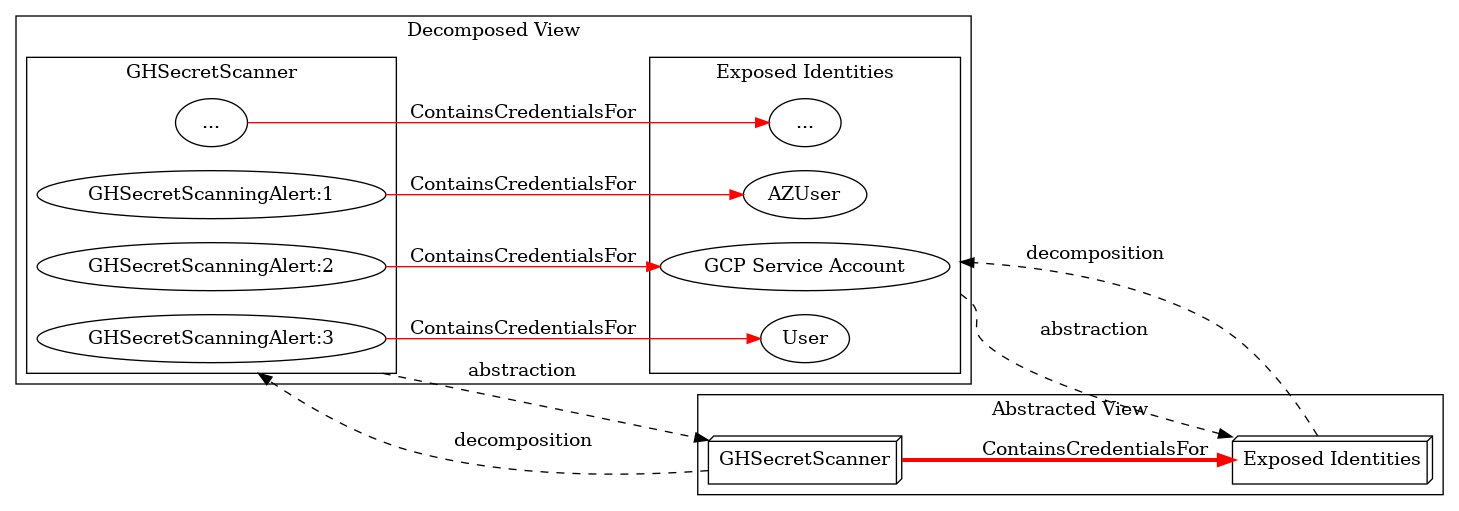
SCCM’s AdminService uses Entra tokens without confirming the UPN exists in AD. A crafted synced UPN can let an attacker impersonate the site server. Microsoft now requires on-prem SID matching (CVE-2025-59501). Great deep dive by @unsigned_sh0rt! ghst.ly/43wTzLx

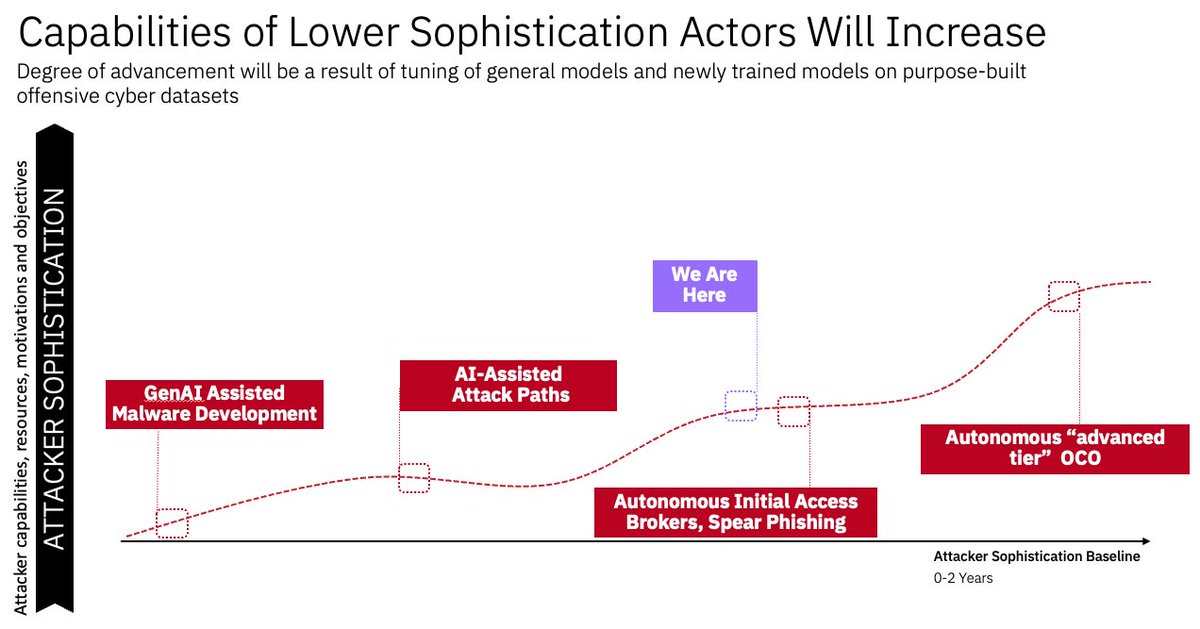
Seeing a lot of bad takes on Anthropic's incident report. A lot of people are missing the point; offensive cyber capabilities in current models are a side-effect of being trained on coding datasets. As frontier model labs and private groups start to shift to tuning current models…
Released my first blog post today: specterops.io/blog/2025/11/1… And released SecretHound, a BloodHound OpenGraph extension for secrets: github.com/C0KERNEL/Secre…
Don't even bother reading the "full report" from Anthropic. Word salad.
If you're into serious red teaming with a crazy skilled team we've got a US based opening! ibmglobal.avature.net/en_US/careers/…
SANS has made it a PITA, but results from local model(s) solve rate so far. We'll see how far we can go.
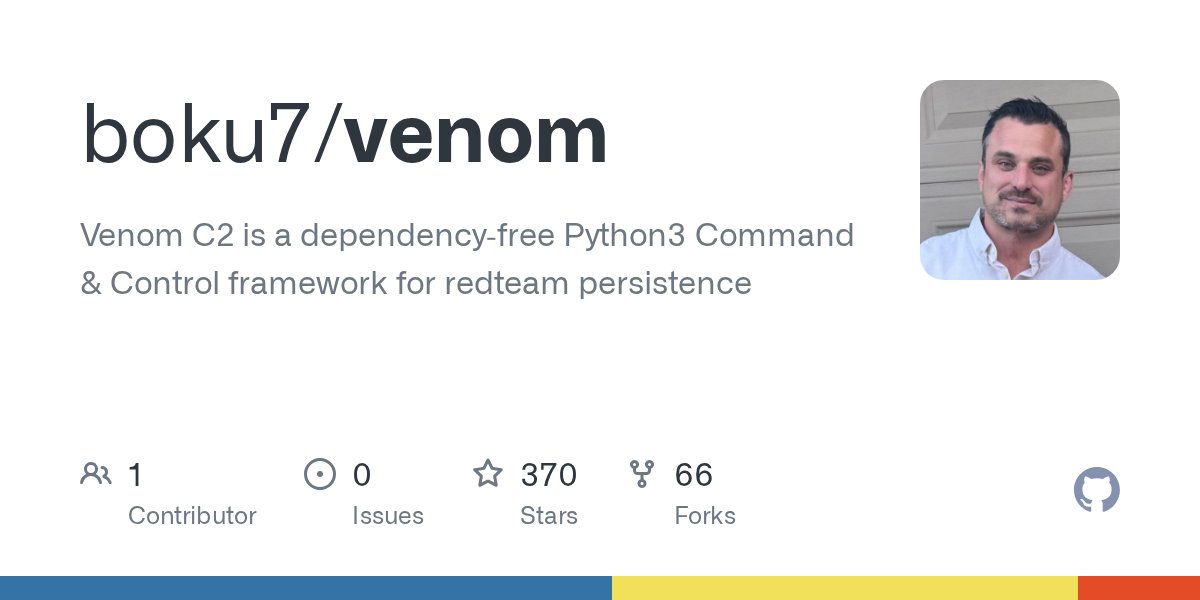
Venom C2 tool drop! 🐍 During a recent red team engagement we needed a simple python agent that needs no dependencies to setup persistence on some exotic boxes we landed on. Some had EDR so we didn't want anything off-the-shelf. The server, agent, and client were made…

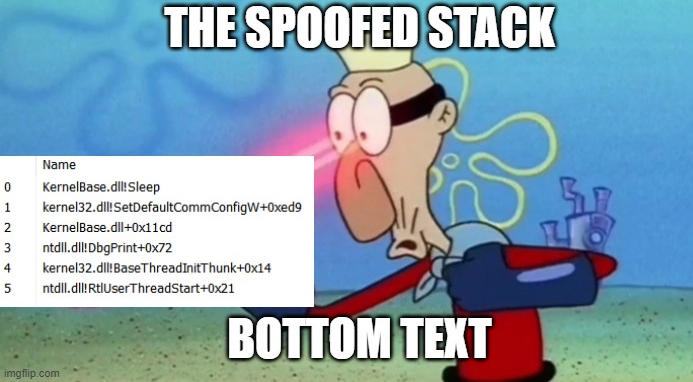
I bypassed user approvals and achieved RCE in VS Code Copilot by flipping 4 bits. Find out how: jro.sg/CVEs/copilot/ Thanks to @msftsecresponse for rapidly triaging and patching this vulnerability.
''Decrypting credentials from SCCM site servers configured for high availability | IBM'' #infosec #pentest #redteam #blueteam ibm.com/think/x-force/…
Any Canadian friends with strong red team backgrounds looking for an AdvSim spot? ibmglobal.avature.net/en_US/careers/…
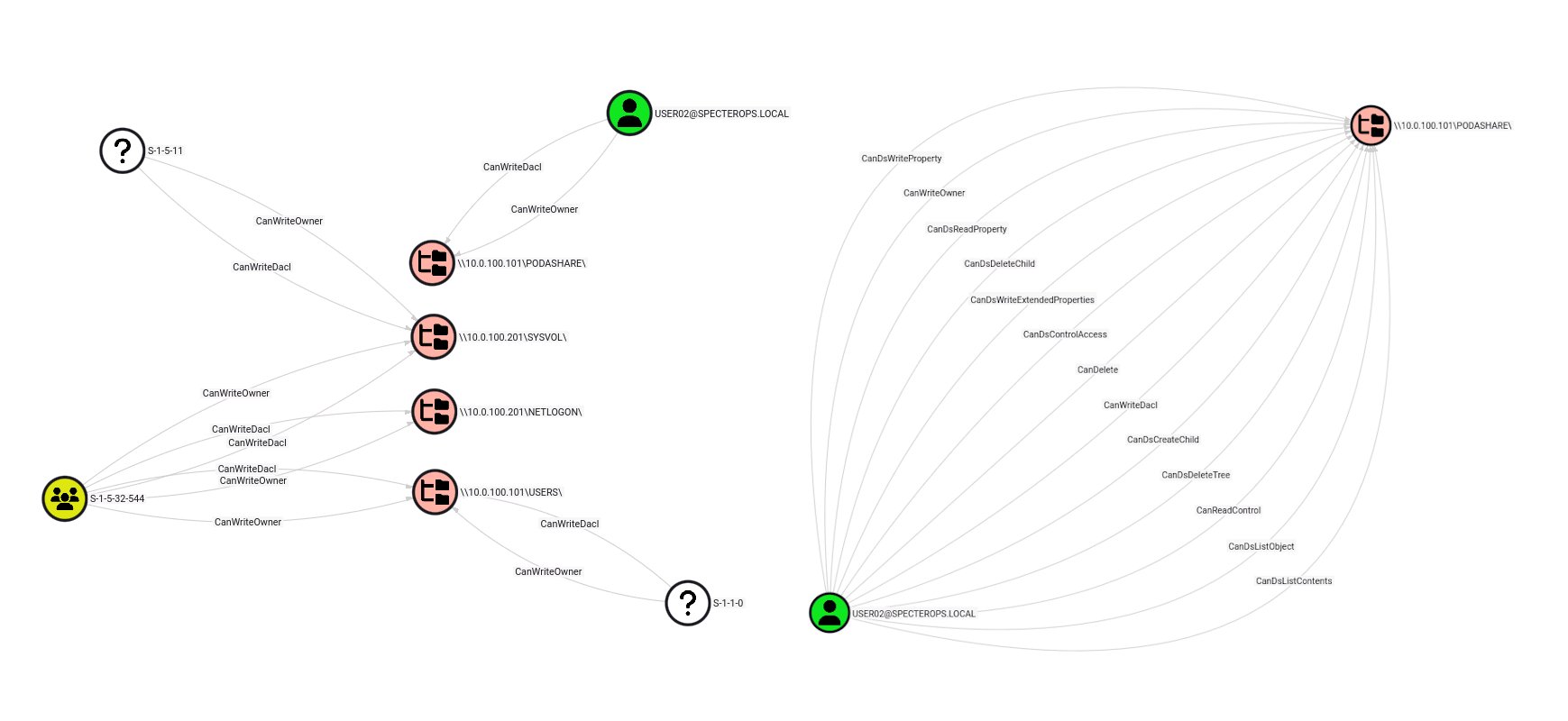
I have released an OpenGraph collector for network shares and my first blogpost at @SpecterOps on the subject! You can now visualize attack paths to network shares in BloodHound 👀 specterops.io/blog/2025/10/3…
New blog - Offsec Evals: Growing Up In The Dark Forest Caught up in the fervor of greenfield research at @OffensiveAIcon , we all agreed we were going to put out evals and benchmarks and push the field forward. On day two of the con, I got a question I've been thinking about…

United States 趨勢
- 1. Black Friday 343K posts
- 2. #SkylineSweeps N/A
- 3. #FanCashDropPromotion N/A
- 4. Good Friday 57.1K posts
- 5. #releafcannabis N/A
- 6. Mainz Biomed N.V. N/A
- 7. WHO DEY 13K posts
- 8. #AVenezuelaNoLaTocaNadie 1,892 posts
- 9. #FridayVibes 3,875 posts
- 10. CONGRATULATIONS JIN 52.7K posts
- 11. Clark Lea N/A
- 12. CONGRATULATIONS J-HOPE 44.2K posts
- 13. GreetEat Corp. N/A
- 14. Mr. President 21.7K posts
- 15. $SMX 8,435 posts
- 16. TODAY ONLY 65.1K posts
- 17. Third World Countries 52.2K posts
- 18. Victory Friday N/A
- 19. Cyber Monday 5,810 posts
- 20. Black Cats 2,892 posts
你可能會喜歡
-
 Matt Hand
Matt Hand
@matterpreter -
 Lee Chagolla-Christensen
Lee Chagolla-Christensen
@tifkin_ -
 Beau Bullock
Beau Bullock
@dafthack -
 Ryan Cobb
Ryan Cobb
@cobbr_io -
 Marcello
Marcello
@byt3bl33d3r -
 Mr.Un1k0d3r
Mr.Un1k0d3r
@MrUn1k0d3r -
 Matt Nelson
Matt Nelson
@enigma0x3 -
 Jason Lang
Jason Lang
@curi0usJack -
 Chris Thompson
Chris Thompson
@retBandit -
 bohops
bohops
@bohops -
 @[email protected]
@[email protected]
@christruncer -
 Steven
Steven
@0xthirteen -
 b33f | 🇺🇦✊
b33f | 🇺🇦✊
@FuzzySec -
 Dwight Hohnstein
Dwight Hohnstein
@djhohnstein -
 Dominic Chell 👻
Dominic Chell 👻
@domchell
Something went wrong.
Something went wrong.