내가 좋아할 만한 콘텐츠
Awesome team! Can recommend to check it out!
Goooood morning everyone! Our team is looking for another Senior Technical Threat Researcher! So, check out our blog! Tell your friends and ping us if you awesome and interested! Check it out: dcso.de/job/senior-tec…
#ProgressUpdate The project now uses a staging system🥳. This prevents me from debugging in production and can be considered an invest into stability! The cat likes it! #ioc_one #cti

The recent #XZBackdoor caused a lot of agitation in the Open Source Community. Today we publish a #ComprehensiveOverview what happened and how to check your system for affection. Read more at medium.com/@DCSO_CyTec/fb… #DCSO #DRIF #Cyber
I converted the new threat actor naming taxonomy from Microsoft (@MsftSecIntel) to json in case someone else needs the data in a machine readable format. gist.github.com/botlabsDev/e23… #threatintel #research #apt
We are announcing a new taxonomy that better reflects the complex tapestry of the threat ecosystem. Name mapping list and industry aka's:➡️ learn.microsoft.com/en-us/microsof… Read more: ⬇️⬇️⬇️

Working with @jaydinbas on our next #ShortAndMalicious post was a lot of fun as always 😁 Check it out below! #PikaBot #iPikaBot #DCSO #CyTec
For our first blog post 2023, we continue the #ShortAndMalicious series with fresh malware: A brief analysis of the #PikaBot #iPikaBot #malware t.ly/_Cly
Ok. Let's call it a day. The "new future" wants me to take a break.

Check out our new blog post! This time we analyse and follow HZ Rat. A previously undocumented malware delivered through malicious documents and self extracting archives. We tracked the campaign and identified a lot of C2 servers. medium.com/@DCSO_CyTec/50… #HZRat #DCSO #CyTec
We took a quick look at a new stealer utilizing polyglot files. Check it out. #CyTec #ShortAndMalicious #StrelaStealer ➡️ medium.com/@DCSO_CyTec/sh…
medium.com
#ShortAndMalicious: StrelaStealer aims for mail credentials
Quick look at a new stealer utilizing polyglot files
Back to full talks with Axel Wauer @botlabsDev who presents HZ Rat Goes China: Following The Tail Of An Unknown Backdoor #CTI-Summit

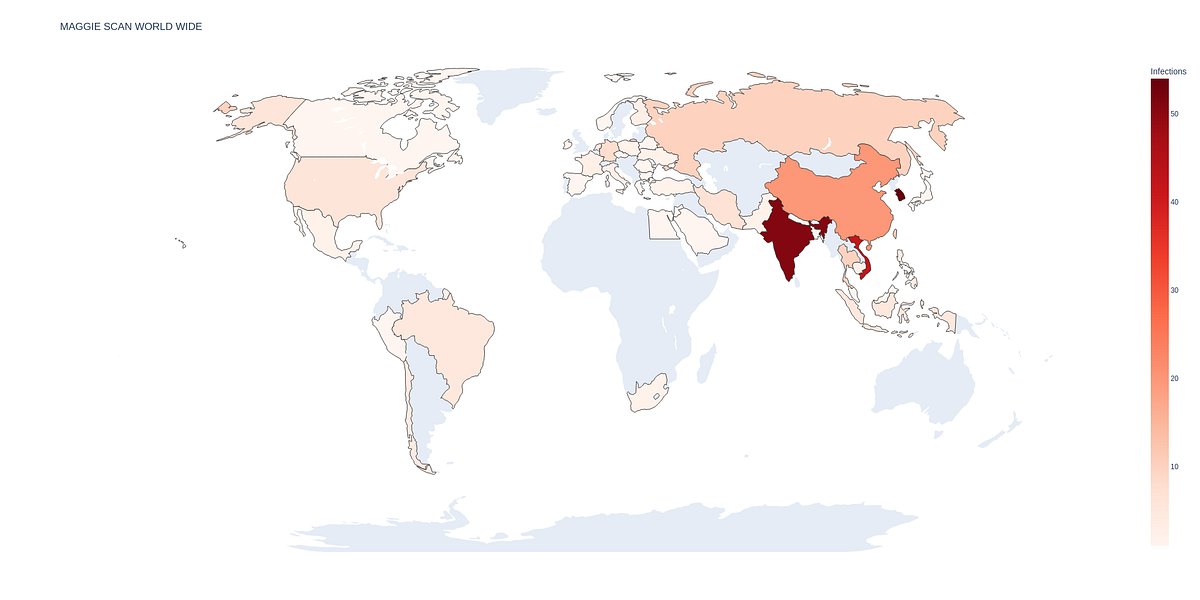
Part 2: Tracking down Maggie @DCSO_de's Incident Response Team (DIRT) provides insights on how to detect the novel MSSQL malware “Maggie” in your environment. #DFIR #threat_hunting #sigma #yara #mssql medium.com/@DCSO_CyTec/tr…
MSSQL, meet Maggie! In our latest blog post, we analyze 'Maggie', a novel backdoor for MSSQL servers, implemented as an Extended Stored Procedure and only controlled using SQL queries. medium.com/@DCSO_CyTec/89…
Thanks again @brucon for this awesome conference. I really enjoyed every single talk ❤️ #BruCon #BruCON0x0E 🍻

Historical IP to ASN Mapper. The script is slow and more a PoC. I just put it here if someone else needs it. #threathunting #ASN gist.github.com/botlabsDev/60b…
Today we published “404 — File still found”, where we can confirm #SideWinder attribution and established even more relations between samples. medium.com/@DCSO_CyTec/40…
Verifying myself: I am botlabsdev on Keybase.io. IHwuz4seAZ8yC1MeuCySRCFVRYexDIT_F06W / keybase.io/botlabsdev/sig…
United States 트렌드
- 1. #AEWDynamite 12.4K posts
- 2. #Survivor49 2,380 posts
- 3. JUNGWOO 13.3K posts
- 4. Blake Snell 5,216 posts
- 5. Donovan Mitchell 4,162 posts
- 6. doyoung 18.1K posts
- 7. Cavs 7,290 posts
- 8. Yesavage 5,454 posts
- 9. Kacie N/A
- 10. #SistasOnBET N/A
- 11. #AbbottElementary 1,390 posts
- 12. Mobley 1,725 posts
- 13. #loveisblindreunion N/A
- 14. Okada 4,008 posts
- 15. Jaylen Brown 6,773 posts
- 16. Davis Schneider 5,011 posts
- 17. Trae Young 2,228 posts
- 18. Game 5 57.2K posts
- 19. Blood and Guts N/A
- 20. Josh Minott N/A
Something went wrong.
Something went wrong.