You might like
New blog post and tooling: Introducing Striker and the Payload Automation Libraries. blog.redxorblue.com/2021/06/introd… A set of Python libraries to interact with Cobalt Strike to help script and automate custom payload generation.
I've been researching the Microsoft cloud for almost 7 years now. A few months ago that research resulted in the most impactful vulnerability I will probably ever find: a token validation flaw allowing me to get Global Admin in any Entra ID tenant. Blog: dirkjanm.io/obtaining-glob…
The wait is over…Choose your side!! Barely Human Official Video is live now!!! #LYLVC #judgeandjury #howardbenson #neilsanderson #altmetal #metalcore #raprock #rapmetal #posthardcore #activerock #rockmusic #rock #numetal #hardrock
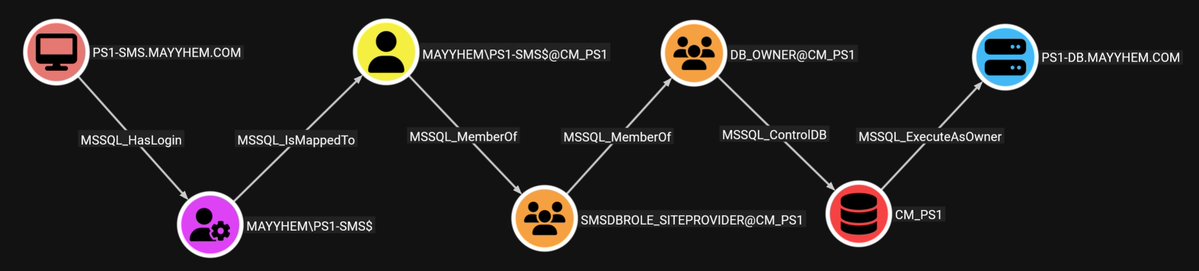
I'm SO hyped to finally make MSSQLHound public! It's a new BloodHound collector that adds 37 new edges and 7 new nodes for MSSQL attack paths using the new OpenGraph feature for 8.0!. Let me know what you find with it! - github.com/SpecterOps/MSS… - specterops.io/blog/2025/07/2…
Hiring a junior/mid role on my team for a Red Team operator, feel free to DM me with any questions or anything nvidia.wd5.myworkdayjobs.com/NVIDIAExternal…
Azure Arc is Microsoft's solution for managing on-premises systems in hybrid environments. My new blog covers how it can it be identified in an enterprise and misconfigurations that could allow it to be used for out-of-band execution and persistence. ibm.com/think/x-force/…
You can find my slide deck for @TheOffensiveX on GitHub. I also included a minimalist extension that you can build on and will load in any of the VSCode forks on any platform 👨💻⚔️

I'm happy to announce that my BOF Development and Tradecraft course on Zero Point Security is now part of their Purcharsing Parity Program (PPP). This means you can purchase the course at a potentially reduced price based on the country that you live in! zeropointsecurity.co.uk/course/bof-dev
🚨 New blog post alert! @_xpn_ drops knowledge on LLM security w/ his latest post showing how attackers can by pass LLM WAFs by confusing the tokenization process to smuggle tokens to back-end LLMs. ghst.ly/4koUJiz
Okay so this is HUGE - our amazing AI red team have open sourced their AI red team labs so you can set up your own training! aka.ms/AIRTlabs @ram_ssk
Back in 2023, the assessment of the pre-authentication vulnerability in SSH was that it wasn't exploitable on Linux. For my OffensiveCon 2025 keynote, I wrote enough of an exploit to show, with the right heap groom and stabilization, it's likely exploitable. Then I tried to have…
If someone get a working OpenSSH exploit from this bug, I'm switching my main desktop to Windows 98 😂 (this bug was discovered by a Windows 98 user who noticed sshd was crashing when trying to login to a Linux server!)
Me and the homies are dropping browser exploits on the red team engagement 😎. Find out how to bypass WDAC + execute native shellcode using this one weird trick -- exploiting the V8 engine of a vulnerable trusted application. ibm.com/think/x-force/…
Well I've sent my two emails for the day, time to put all my passwords in SharePoint and take a four hour lunch break
As promised... this is Loki Command & Control! 🧙♂️🔮🪄 Thanks to @d_tranman for his work done on the project and everyone else on the team for making this release happen! github.com/boku7/Loki
Many people wanted my slides from the Windows Client Privilege Escalation webinar yesterday. Here are links to the slides and the recording of the webinar. slideshare.net/slideshow/wind… youtu.be/EG2Mbw2DVnU?si…

youtube.com
YouTube
Webinar - Windows Client Privilege Escalation
I am excited to announce the first conference dedicated to the offensive use of AI in security! Request an invite at offensiveaicon.com. Co-organized by RemoteThreat, Dreadnode, & DEVSEC. The Call for Papers opens Tuesday, March 25, 2025, and will remain open until Friday,…

Today I'm releasing Xenon, a custom Mythic agent for Windows targets written in C. Notable features include: 📁 Modular command/code inclusion 🦠 Malleable C2 Profile support 🪨 Compatible with Cobalt Strike BOFs github.com/MythicAgents/X… Blog series - c0rnbread.com/creating-mythi…
My intern research from IBM @XForce Red last summer just got released! Introducing SoaPy - a completely custom engineered way to use Active Directory Web Services (ADWS) from Linux hosts for stealthy Active Directory interaction! Read about it here! securityintelligence.com/x-force/stealt…
Going forward I'll only be publishing new tooling one line of code per week, and all new blogs will be meandering sports analogies. If you think this is silly then you're arming ATPs
I see we're doing the quarterly open source tools/research debate again. I'll just say this: Phishing got much harder when @mrgretzky released evilnginx AD got more secure after @SpecterOps released Certified Pre-Owned AD got more secure when @TimMedin showed us kerberoasting
Loki C2 is coming.. Cross-platform Stage 1 C2, battle-tested in ops for 8 months against the world’s leading EDRs and MSSPs, undetectable, bypasses Application Control/WDAC.. Shoutouts to @d_tranman for helping build the project, and @chompie1337 & @knavesec for inspiration!

United States Trends
- 1. #KonamiWorldSeriesSweepstakes N/A
- 2. #2025MAMAVOTE 1.52M posts
- 3. Mitch McConnell 12.6K posts
- 4. Tyla 22.3K posts
- 5. Term 190K posts
- 6. Budapest 9,759 posts
- 7. No Kings 153K posts
- 8. Somalia 31.5K posts
- 9. Yung Miami 1,678 posts
- 10. Caresha 1,362 posts
- 11. Deport Harry Sisson 29.4K posts
- 12. #TrumpShutdownBadForUS 1,597 posts
- 13. Miguel Vick N/A
- 14. Chanel 25.9K posts
- 15. Spencer Dinwiddie N/A
- 16. ErgoChair X N/A
- 17. Brian Cashman N/A
- 18. President Putin 21.4K posts
- 19. #SpiritDay 2,088 posts
- 20. Andrade 7,428 posts
You might like
-
 Lee Chagolla-Christensen
Lee Chagolla-Christensen
@tifkin_ -
 Matt Hand
Matt Hand
@matterpreter -
 drm
drm
@lowercase_drm -
 Shawn
Shawn
@anthemtotheego -
 Dwight Hohnstein
Dwight Hohnstein
@djhohnstein -
 sinusoid
sinusoid
@the_bit_diddler -
 Justin Bui
Justin Bui
@slyd0g -
 Dave Cossa
Dave Cossa
@G0ldenGunSec -
 Chris Thompson
Chris Thompson
@retBandit -
 sn🥶vvcr💥sh
sn🥶vvcr💥sh
@snovvcrash -
 Harley Lebeau
Harley Lebeau
@r3dQu1nn -
 Bobby Cooke
Bobby Cooke
@0xBoku -
 checkymander
checkymander
@checkymander -
 Andrew Oliveau
Andrew Oliveau
@AndrewOliveau -
 freefirex
freefirex
@freefirex2
Something went wrong.
Something went wrong.