Detectify
@detectify
Advanced application security testing for evolving attack surface coverage. Fuelled by elite ethical hackers. Go hack yourself.
你可能會喜歡
🚨Security Update on CVE-2025-64446 - FortiWeb authentication bypass that leads to complete WAF control. Learn how the impersonation flaw works and what steps to take now. blog.detectify.com/industry-insig…
We're now integrating real-world threat data into our AI Researcher Alfred to prioritize and generate protection against the most active CVEs, boosting security speed and relevance for all Detectify customers: blog.detectify.com/product-update…
450 automated, validated security tests created in 6 months, targeting critical threats (avg. CVSS 8.5). 70% of tests needed no manual fix. Write-up with our prompts, lessons, & build process in @detectify labs! ⤵️ labs.detectify.com/writeups/ai-ag…
With the new API Scanner, customers gain access to dynamic payloads that make every scan different. Instead of relying on static methods, the scanner uses ML to randomize and rotate payloads for each run, ensuring fresh attack simulations every time:
Methods and tools (from DNS records and IP addresses to HTTP analysis and HTML content) that practitioners can use to classify every web app and asset in their attack surface. blog.detectify.com/best-practices…
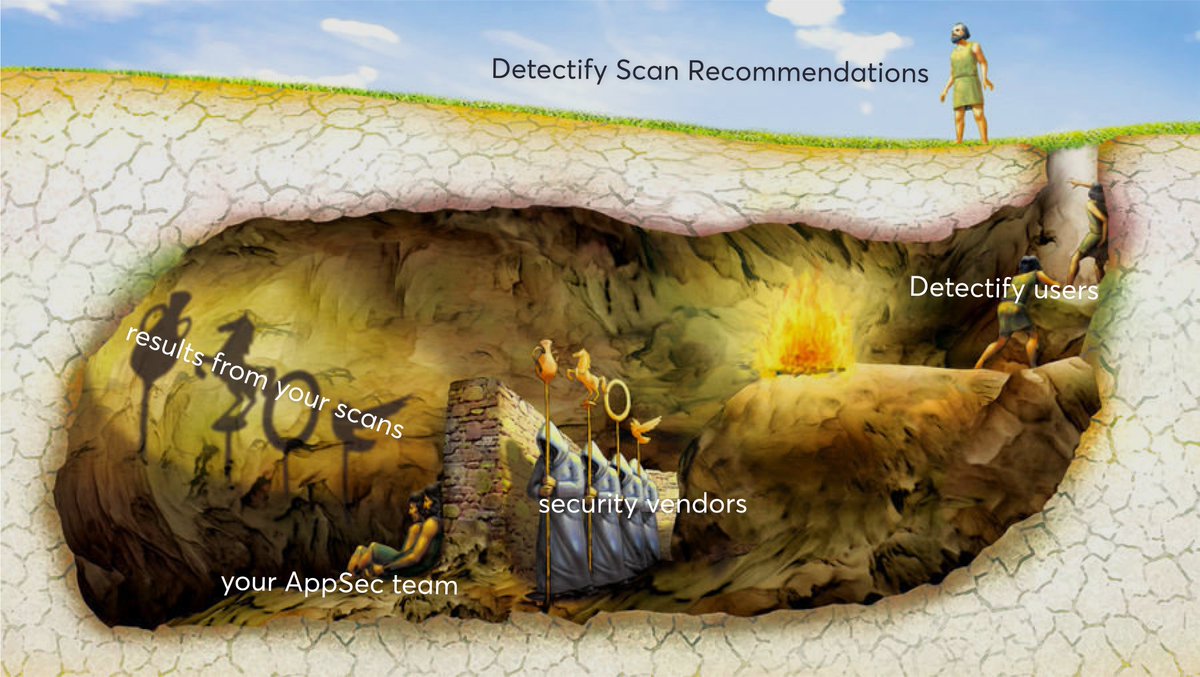
We know it is hard to ensure all essential web apps are covered with deep DAST. Which of your dozens or hundreds of web apps actually need deep testing? Which are processing user data or even have many components that attackers would target? blog.detectify.com/product-update…
Attending #RSAC? It's finally your chance to snag some of our famous Go Hack Yourself swag. More info: detectify.com/rsac
Detectify Surface Monitoring customers can test whether they have exposed ingress NGINX admission, which enables the exploit chain for IngressNightmare (CVE-2025-1097, CVE-2025-1098, CVE-2025-24514, CVE-2025-1974) blog.detectify.com/product-update…
DNS is a critical attack surface very often overlooked. Security risks exist at every level (Root, TLDs, Registrars, Providers, Zones, Software Queries). Are you protecting all levels? blog.detectify.com/best-practices…
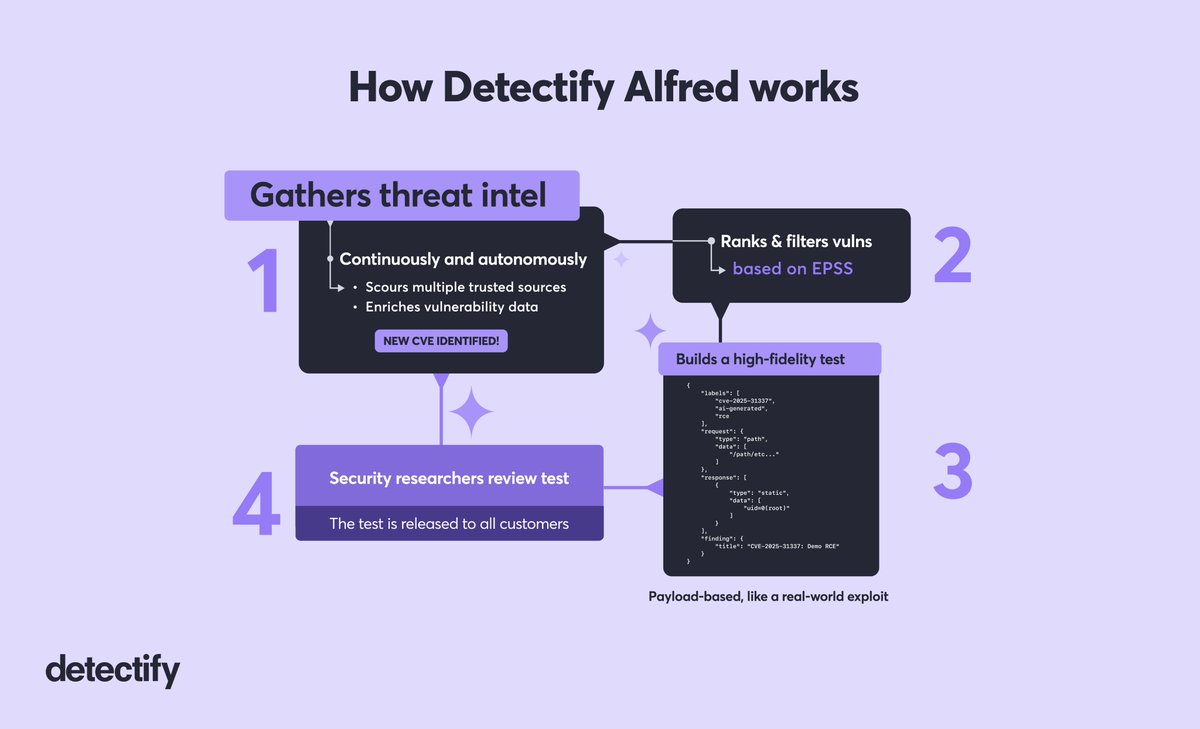
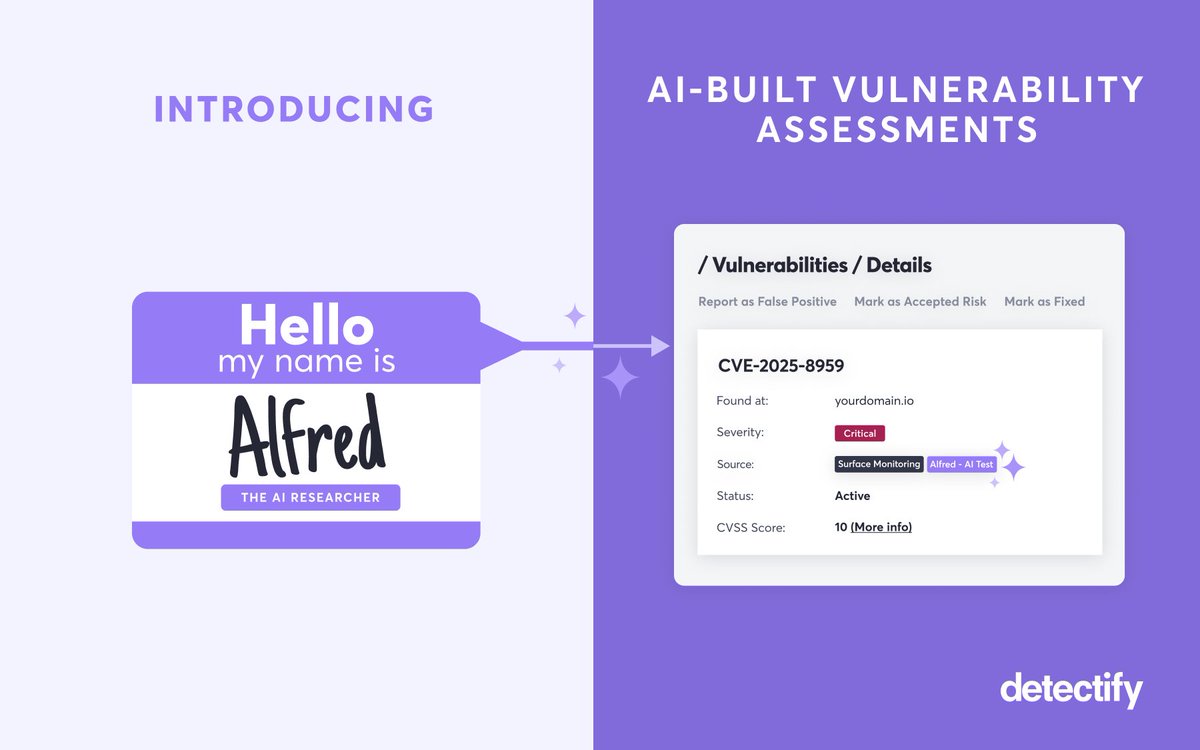
Find out how Detectify Alfred (AI-Built vuln assessments) is working around the clock to continuously bring you the latest security research: blog.detectify.com/product-update…
Thanks @helpnetsecurity for featuring Detectify Alfred as one of the releases of the week 🎉
New infosec products of the week: March 14, 2025 - helpnetsecurity.com/2025/03/14/new… - @usealloy @detectify @pondurance @SimSpaceCorp - #CyberSecurity #netsec #security #InfoSecurity #CISO #ITsecurity #CyberSecurityNews #SecurityNews
Detectify launches Alfred to automate CVE security testing with AI ift.tt/5vPsWGn
✨ Say hi to Alfred, a revolutionary system that uses AI to completely autonomously collect and prioritize threat intelligence and generate high-fidelity payload-based security tests for likely exploitable vulnerabilities. blog.detectify.com/product-update…
echo “Hello, World!” | wall We have been busy lately. Keep an eye out for some funky news coming shortly. ༼▃ Ĺ̯ ▃༽
🏆 Meet the incredibly talented winners of our Crowdsource Awards 2024: @DhiyaneshDK @yougina @popc0rn94 labs.detectify.com/crowdsource-co…
To help our customers secure their complex attack surface we need to send a very large amount of requests to their systems. Our engineering team has put a lot of work into preventing overwhelming their systems while ensuring maximum value. Check out how: blog.detectify.com/industry-insig…
United States 趨勢
- 1. Tulane 11K posts
- 2. #SmackDown 32.2K posts
- 3. Gunther 20.5K posts
- 4. North Texas 6,962 posts
- 5. #ROHFinalBattle 15.8K posts
- 6. Anthony Davis 1,793 posts
- 7. #OPLive 2,591 posts
- 8. LA Knight 10.3K posts
- 9. Cocona 35.4K posts
- 10. #TNAFinalResolution 6,276 posts
- 11. Boise State 2,778 posts
- 12. Athena 9,673 posts
- 13. Kennesaw State 3,610 posts
- 14. UNLV 3,772 posts
- 15. Mark Pope 3,151 posts
- 16. Persephone 2,685 posts
- 17. #OPNation 1,054 posts
- 18. Trouba N/A
- 19. Jimmy Rogers 2,461 posts
- 20. Wes Miller N/A
你可能會喜歡
-
 Frans Rosén
Frans Rosén
@fransrosen -
 publiclyDisclosed
publiclyDisclosed
@disclosedh1 -
 Nicolas Grégoire
Nicolas Grégoire
@Agarri_FR -
 André Baptista
André Baptista
@0xacb -
 Tanner
Tanner
@itscachemoney -
 Somdev Sangwan
Somdev Sangwan
@s0md3v -
 Gareth Heyes \u2028
Gareth Heyes \u2028
@garethheyes -
 Geekboy
Geekboy
@emgeekboy -
 Joel Margolis (teknogeek)
Joel Margolis (teknogeek)
@0xteknogeek -
 Yassine Aboukir 🐐
Yassine Aboukir 🐐
@Yassineaboukir -
 Julien | MrTuxracer 🇪🇺
Julien | MrTuxracer 🇪🇺
@MrTuxracer -
 Patrik Fehrenbach
Patrik Fehrenbach
@ITSecurityguard -
 Jasmin Landry
Jasmin Landry
@JR0ch17 -
 spaceraccoon | Eugene Lim
spaceraccoon | Eugene Lim
@spaceraccoonsec -
 Michael Skelton
Michael Skelton
@codingo_
Something went wrong.
Something went wrong.