
F5 DevCentral Community
@devcentral
A community of @F5 experts collaborating to solve challenges, share ideas, and discuss industry trends. Join the community here: https://devcentral.f5.com
Talvez você curta
Discover how to effectively monitor login attempts on your BIG-IP system. my.f5.com/manage/s/artic…
How do #AI agents challenge traditional #IAM? Disposable workers that spin up for seconds don’t fit within today’s identity systems. From ephemeral credentials to zero trust, learn the next steps for securing agent-driven systems. Watch now! 🎥 go.f5.net/t9z6q4fj

Integrating Falcon sensors with BIG-IP systems enhances visibility and defense by detecting and blocking malicious activity across these critical components. community.f5.com/kb/TechnicalAr…
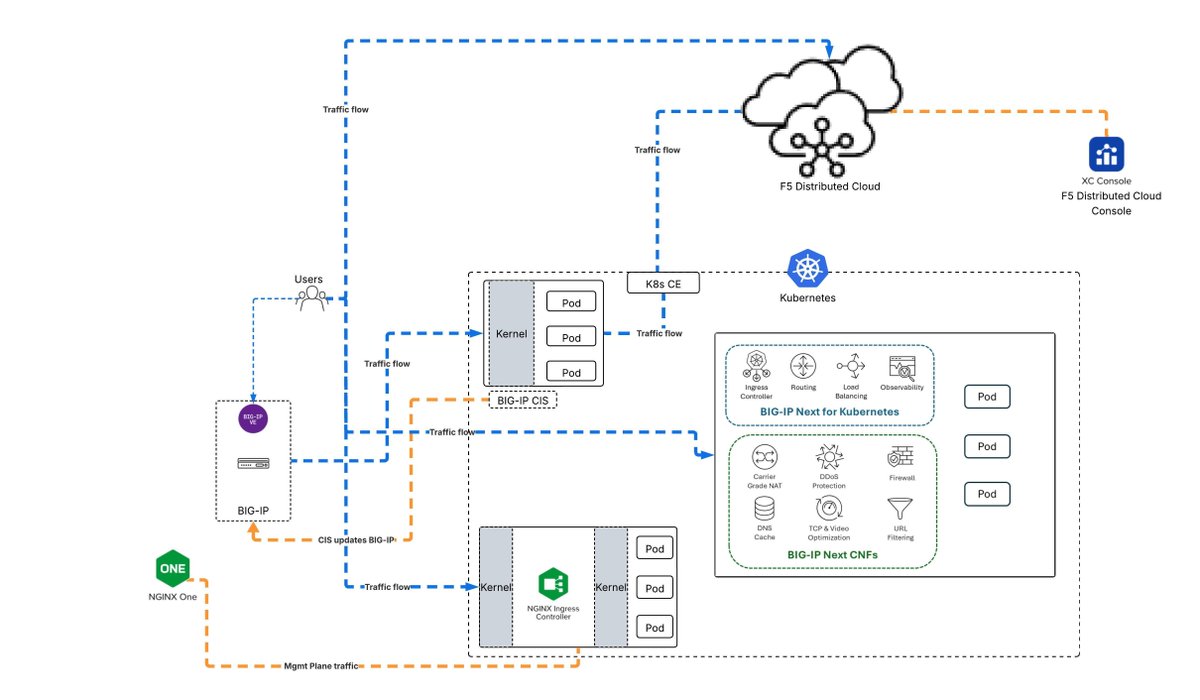
Check out Mohamed Mahdy's guide to ingress solutions and newly updated Kubernetes integration cheat sheet: community.f5.com/kb/technicalar…
APIs power your apps, but are you leaving the back door open? Broken Object Level Authorization (BOLA) is today’s top API vulnerability—and it's growing. Learn how to secure against BOLA with this expert discussion. go.f5.net/jw4nh0fh #CyberSecurity #APIVulnerabilities

Manual updates on F5 BIG-IP can introduce risk and slow down operations. This article by Matt Mabis explores how Ansible automation streamlines the process, ensuring consistency and reliability across your infrastructure. 🔗 go.f5.net/bzfz4pay
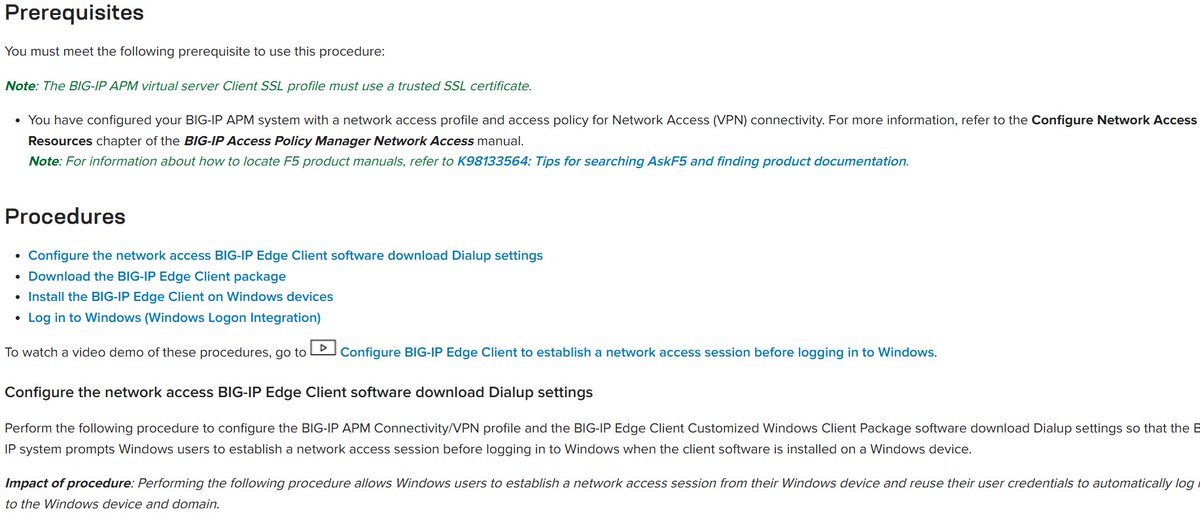
Need to configure your BIG-IP Edge Client for Network Access Sessions? Learn to set up the #BIGIP Edge Client to establish a network access session before logging in to Windows. go.f5.net/kr10tpcv
Is Your Certificate Authority Quantum-Ready? This GitHub lab guide walks you through building a Post-Quantum CA using OpenSSL 3.2+ and OQS libraries—fully aligned with NSA’s CNSA 2.0 requirements to safeguard against “harvest now, decrypt later” threats. community.f5.com/kb/TechnicalAr…
Explore how to seamlessly integrate OpenShift Service Mesh (OSSM) with F5 BIG-IP to enhance ingress traffic management, health monitoring, and security using Layer 4 and Layer 7 configurations. community.f5.com/kb/TechnicalAr…
Need to configure an SSL profile with a custom chain certificate on the #BIGIP system? Learn exactly how to import chain certificates to your BIG-IP system and configure SSL profiles to use them, step-by-step, in this AskF5 video: go.f5.net/txrqi5wy
This new guide shows how to implement a global Layer 3 Virtual Network—connecting private data centers and AWS VPCs, enabling secure segmentation, and simplifying routing with BGP peering. community.f5.com/kb/TechnicalAr…
Editor Koichi from the #F5 Security Incident Response Team highlights key security incidents you need to be aware of. community.f5.com/kb/security-in…
The quantum challenge is no longer distant—it’s here. Organizations must begin transitioning to post-quantum cryptography (PQC) now to protect sensitive data and modernize PKI practices. community.f5.com/kb/TechnicalAr…

#F5 BIG-IP enables enterprises to streamline workload distribution, enhance security protocols, and ensure high availability regardless of the deployment model. community.f5.com/kb/TechnicalAr…
The recently discovered #BlackLock ransomware, formerly known as El Dorado, poses a critical risk to organizations globally. Leveraging a Ransomware-as-a-Service (RaaS) model, it targets Windows, Linux, and VMware ESXi systems. community.f5.com/kb/security-in…
#Smartphones have become essential tools that serve as personal assistants, health trackers, and gateways to corporate networks. As we look to the future, #mobilesecurity will be at the forefront of protecting our digital lives. community.f5.com/kb/security-in…
Dive deep into Service Extensions with #SSLOrchestrator, focusing on the innovative User Coaching Service Extension. This guide is a must-read for IT professionals. community.f5.com/kb/TechnicalAr…
#F5 Security News Update for the week of Sept 7–13. 1️⃣ Apple's Memory Integrity Enforcement 2️⃣ Fake Chrome Extensions 3️⃣ Google's Pixel 10 Trusted Photography with C2PA Content Credentials 4️⃣ CISA Alert on Dassault's DELMIA Apriso RCE community.f5.com/kb/security-in…
A secure extranet that spans multiple clouds and partners is no small feat. Organizations grapple with technology fragmentation, endpoint proliferation, configuration drift, and more. #F5 and #Equinix have teamed up to simplify this complex landscape. community.f5.com/kb/TechnicalAr…
F5 #BIGIP is an industry-leading ADC solution optimizes S3 flows directed at #cloudstorage solutions like StorageGRID. #S3 is set to redefine what’s possible in data management. community.f5.com/kb/TechnicalAr…
United States Tendências
- 1. #SpotifyWrapped 52.1K posts
- 2. Chris Paul 17.6K posts
- 3. Clippers 27.1K posts
- 4. #NSD26 8,961 posts
- 5. Good Wednesday 30.8K posts
- 6. #WednesdayMotivation 3,584 posts
- 7. Hump Day 11.2K posts
- 8. National Signing Day 3,782 posts
- 9. Happy Hump 7,437 posts
- 10. Nashville 32.3K posts
- 11. #Wednesdayvibe 1,982 posts
- 12. #PutThatInYourPipe N/A
- 13. Wonderful Wednesday 6,161 posts
- 14. TOP CALL 10.8K posts
- 15. Welcome Home 15.1K posts
- 16. The BIGGЕST 309K posts
- 17. Wordle 1,628 X N/A
- 18. FELIX LV VISIONARY SEOUL 28.9K posts
- 19. Elden Campbell 1,106 posts
- 20. Fisherman 11.2K posts
Something went wrong.
Something went wrong.






























































































































![michvictor's profile picture. @USMC Veteran ~ Fortune Ones to Watch: Tech ∆* ~ #LiveVictoriously ~ Johns Hopkins Grad School Alumna, Doing Innovative Digital @boozallen [Tweets are my own😊]](https://pbs.twimg.com/profile_images/1751018220012621824/mG9tvGJk.jpg)






