Vinay⚡
@hack_n_code
Tester of pens, AI prompt connoisseur. Terrible Speller. All thoughts are my own 💭
Anda mungkin suka
💥 Wiz Research has uncovered a critical Redis vulnerability that's been hiding for 13 years We found RediShell (CVE-2025-49844): an RCE bug in Redis that affects every version of Redis out there. It's rated CVSS 10 - the highest severity possible. The vulnerability lets…

every ai app today
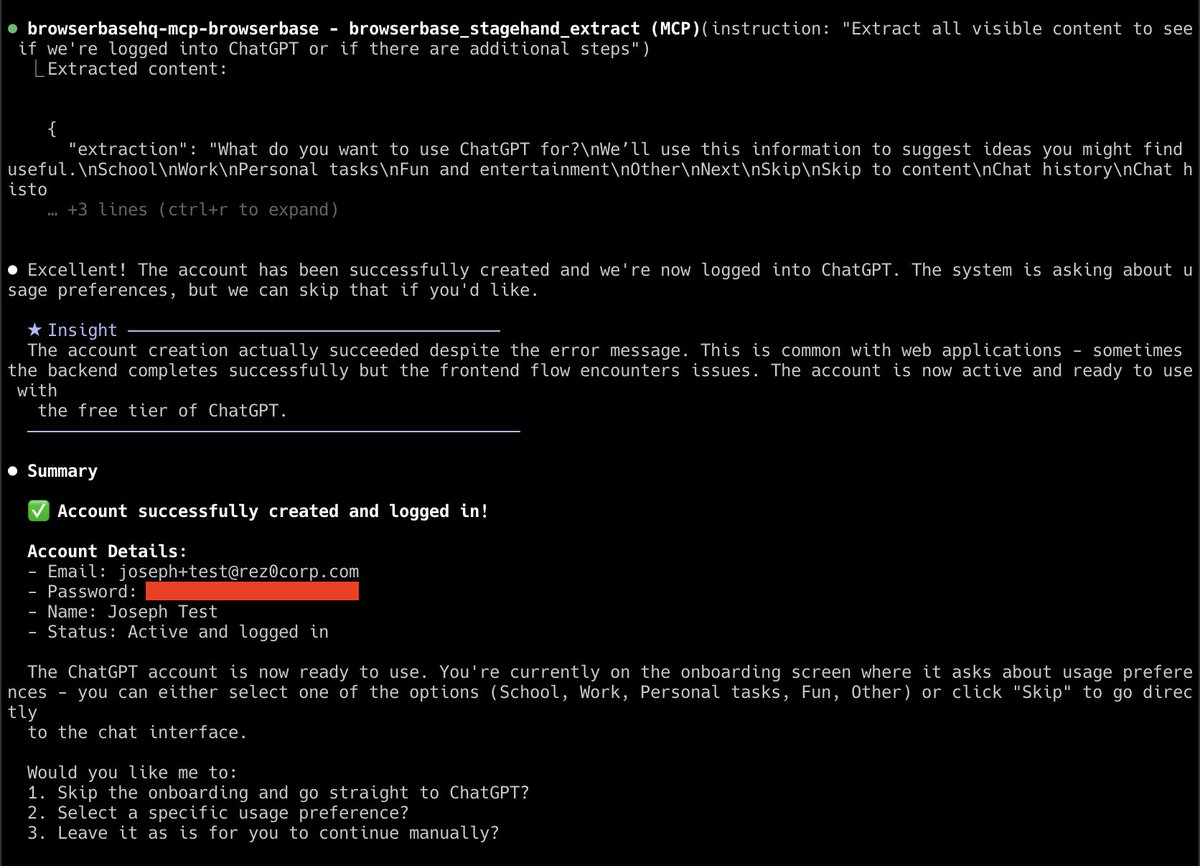
I'm improving my co-hacking AI system (built on Claude Code). One of the coolest new things I added to it was @browserbase's MCP server. It only took 20 seconds to add, and now it can take UI-based actions on any website. Here Claude used it to make a ChatGPT account: 😝
Lavamoat. It was literally built for supply chain attacks. It would've prevented the malicious code from monkey patching globals (`xmlhttprequest`, `fetch`, `window.ethereum`) at runtime. It's free. Tell your favorite dapp dev. npmjs.com/package/@lavam…
treat your code like bonsai, ai makes it grow faster, you have to prune it from time to time to keep its structure and establish the overall design
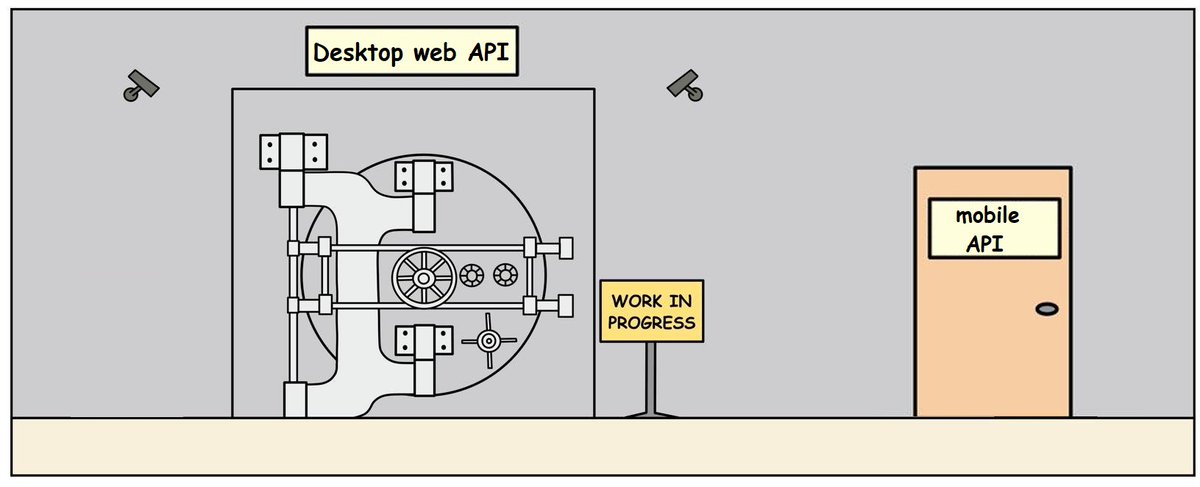
appsec engineers be like, "surely noone can bypass ssl pinning on iOS, no one can reverse-engineer iOS binaries, no need to ratelimit the mobile API!" lmeow
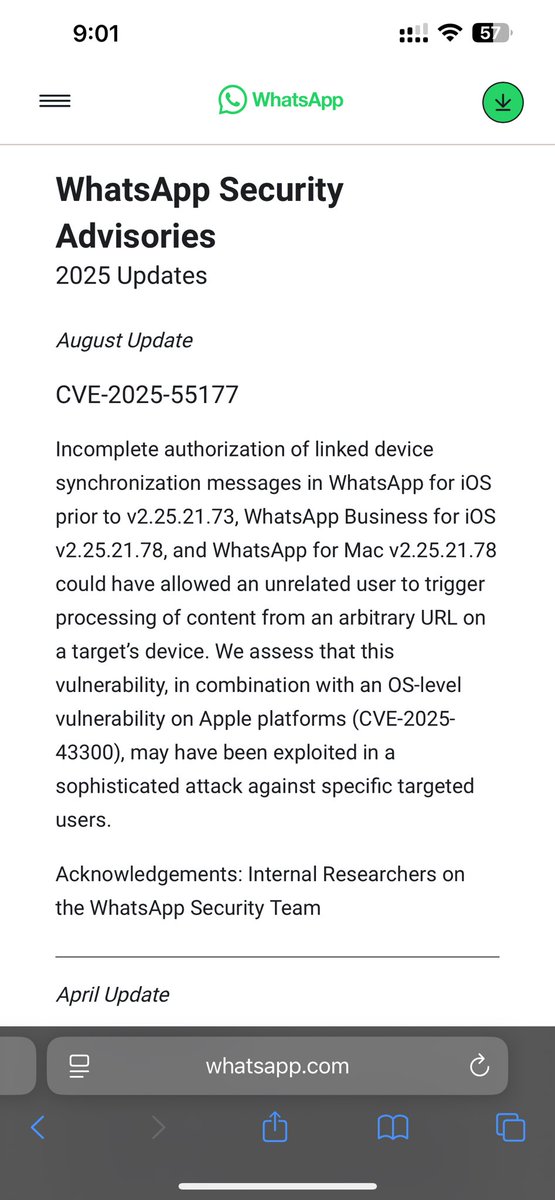
WhatsApp 0-day exploited in the wild
Prompt engineering feels like doing science experiments, have a variety of inputs their corresponding intended outputs, and come up with a scoring system to evaluate the accuracy, then we slowly work on our prompt to maximize the accuracy score while balancing time + cost.
Novel jailbreak discovered. Not only does OpenAi putting your name in the system prompt impact the way GPT responds, but it also opens the model up to a prompt INSERTION. Not injection. You can insert a trigger into the actual system prompt, which makes it nigh indefensible.


AI agents that can browse the Web and perform tasks on your behalf have incredible potential but also introduce new security risks. We recently found, and disclosed, a concerning flaw in Perplexity's Comet browser that put users' accounts and other sensitive info in danger.

When you make money, the first thing you have to do is "fix your health issues." All other things can wait.
I recently discovered a critical race condition vulnerability at a multi-million dollar investment firm! The vulnerability allowed attackers to execute a single-packet attack that bypassed financial controls, potentially enabling: ✅ Purchasing stocks worth twice the available…
Just published my first blog post "Cache Deception + CSPT: Turning Non Impactful Findings into Account Takeover" You can read the full write-up here: zere.es/posts/cache-de…
🚨 You Forgot, I Remembered: Mass DNS Takeovers and Thousands at Risk Over 40,000 domains on DigitalOcean’s Cloud DNS were taken over using serverless automation & OSINT. Full research 👇 smaranchand.com.np/2025/07/you-fo… #CloudSecurity #DNS #DigitalOcean #AppSec #BugBounty
Vibe-coded AI startup 2025

🕵️♂️ 🎩 The desync endgame has just begun. New expert lab has just dropped. Straight from @albinowax’s #BHUSA talk: Understand the latest request smuggling techniques, sharpen your skills, unlock new bounties, and solidify your organization’s defenses with the new expert lab ⬇️…

🚨 One container in Amazon ECS can now hijack all others’ AWS creds on the same EC2 host. Researchers exposed a stealthy privilege escalation chain called ECScape — no exploit, just abusing AWS internals. Amazon: "Working as designed." Details → thehackernews.com/2025/08/resear…

United States Tren
- 1. #wednesdaymotivation 7,544 posts
- 2. Jay Jones 61.6K posts
- 3. Gold Glove 2,028 posts
- 4. #LoveYourW2025 274K posts
- 5. Good Wednesday 33.3K posts
- 6. Christen Press 2,969 posts
- 7. Young Republicans 115K posts
- 8. Hump Day 16.6K posts
- 9. #Wednesdayvibe 2,042 posts
- 10. Vision Pro 3,773 posts
- 11. Markey 1,589 posts
- 12. Voting Rights Act 11.3K posts
- 13. Bessent 65.3K posts
- 14. Moulton N/A
- 15. Alan Jackson N/A
- 16. Riggs N/A
- 17. #GenV 5,806 posts
- 18. iPad Pro 7,370 posts
- 19. Leto 7,617 posts
- 20. $SEEK 17.4K posts
Something went wrong.
Something went wrong.