Erik K
@lcbuilt12
Cybersecurity. InfoSec. Threat modeling. Security Architecture. IAM. #InformationSecurity #AZ900 #CC
You might like
Join me on TradingView, this place is awesome. If you eventually grab a paid plan, we each get up to $15 as a bonus! Use this link to sign up: tradingview.com/black-friday/?…
🎉 New Year, New Skills! 🚀 We're excited to kick off our #NewYearGiveaway! Get the chance to level up your #CloudSecurity expertise with hands-on #cloudsecurity training courses! 📚✨ To Enter: 👍 Like, 🔁 Share this tweet 💬 Comment below Check out our Training Courses &…

In the fourth report of our ongoing Cyberattack series, a credential phishing and smishing cyberattack was used to target a privileged user with social engineering. Learn how we detected the incident and responded to it: msft.it/6013iPjLl #IncidentResponse
Microsoft just released their updated Microsoft Cybersecurity Reference Architectures (MCRA). A slide deck full of high-level guidance on securing one's organisation. Very handy for orgs starting out or already on the way. learn.microsoft.com/en-us/security…

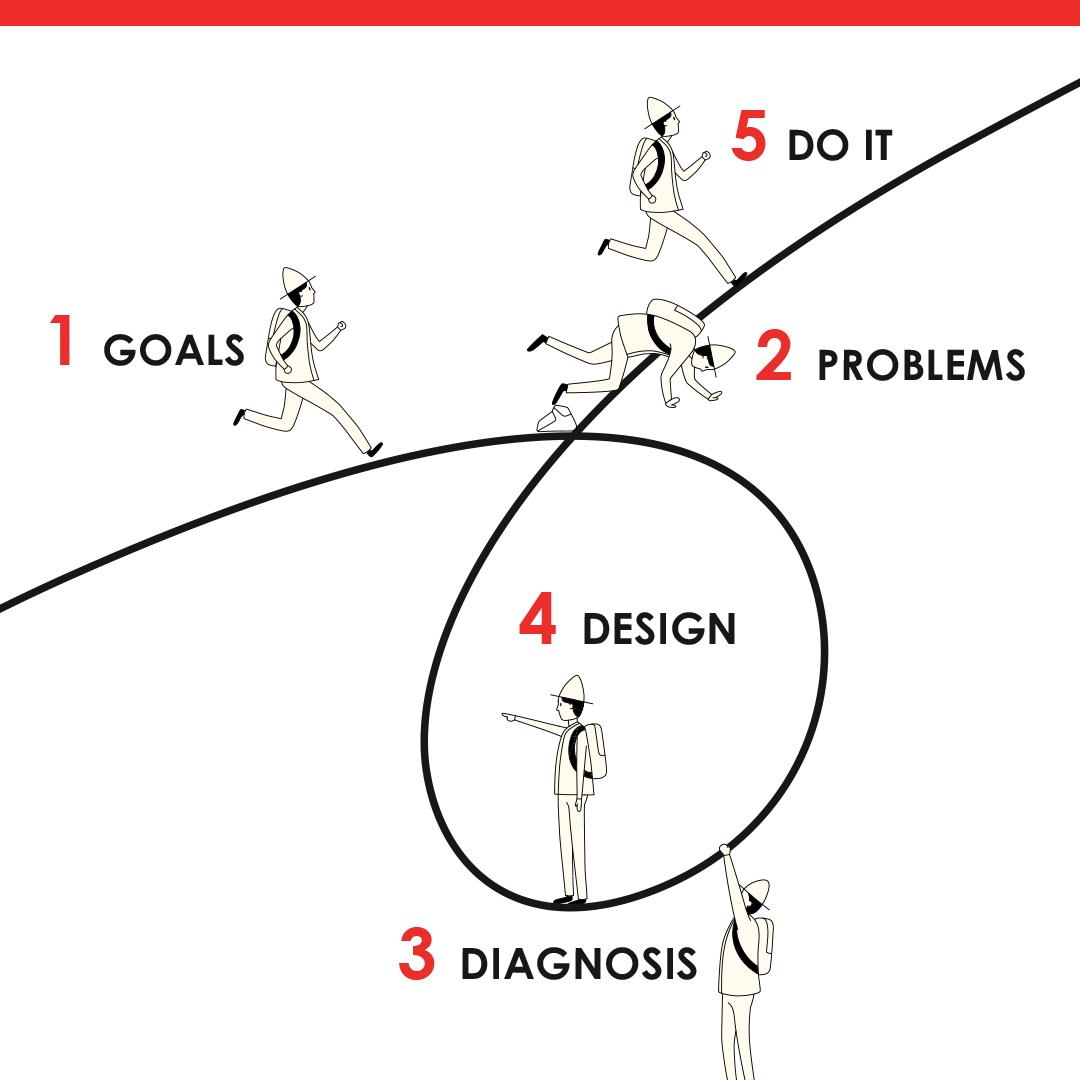
It seems to me that the personal evolutionary process takes place in five distinct steps. If you can do those five things well, you will almost certainly be successful. Together, these five steps make up a loop, like the one here. #principleoftheday

How generative AI is defining the future of identity access management venturebeat.com/security/how-g… via @VentureBeat
Called the help desk for the first time ever and they replaced my laptop. I lost all my stickers 👀😭
Official launch is October 18, 2023! #cyber #teacher #girlsincyber #girlsthatcode #cyberchallenge #mentoring #students #cybersecurity #share #STEM #girlsinstem #careersincyber #stemcareers #stemeducation

Microsoft has been published a #TokenTheft playbook which includes investigation checklist, hunting queries, response/recovery task list but also accompanying decision tree. A must read for every #AzureAD, #Entra, #SecOps admin and architect. learn.microsoft.com/en-us/security…
United States Trends
- 1. #DWTS 88.8K posts
- 2. Luka 41.2K posts
- 3. Robert 126K posts
- 4. Lakers 29.2K posts
- 5. Clippers 10.9K posts
- 6. Alix 14.5K posts
- 7. Elaine 44.9K posts
- 8. Jordan 117K posts
- 9. Dylan 34.9K posts
- 10. #LakeShow 2,214 posts
- 11. Collar 36.3K posts
- 12. Kawhi 3,836 posts
- 13. NORMANI 5,623 posts
- 14. Zubac 1,719 posts
- 15. #DancingWithTheStars 2,240 posts
- 16. Colorado State 2,111 posts
- 17. Godzilla 35.2K posts
- 18. Carrie Ann 4,204 posts
- 19. Daniella 3,927 posts
- 20. Kobe Brown N/A
Something went wrong.
Something went wrong.