#cloudsecurity نتائج البحث
A tool for unauthenticated enumeration of AWS, Azure, and GCP Principals github.com/righteousgambi… By @WesLadd #cybersecurity #infosec #cloudsecurity

Life Lately, I’ve been playing around a lot with Google Cloud Platform (security~wise) as to becoming an expert security engineer. Not for work but for personal development and I have another guide put together. I’ll share with y’all soon. #CloudSecurity

If your Azure Local instance fails or you have a data center outage, you can fail over workloads to Azure. Azure Local is secure by default with many security features. #Azure #CloudSecurity #AzureLocal
🔐 Microsoft 365 Security & Compliance Specialist needed! Remote, full-time, cloud security + DLP + Azure AD. 👉 tohoza.com/ad/microsoft-3… #InfoSec #CloudSecurity #RemoteWork
Cloud Pentesting — Executive Summary ☁️🔍 Cloud penetration testing is the authorised, methodical evaluation of cloud environments (IaaS/PaaS/SaaS) to identify misconfigurations, weak identities, exposed data, and risky deployment practices. #CloudSecurity #Pentesting #CSPM
Hammer Distribution’s new Sensra service offers 24×7 monitoring and response from its UK SOC, using Seceon’s aiSIEM + aiXDR to safeguard hybrid and multi-cloud environments. businesspartnermagazine.com/hammer-distrib… #aiXDR #CloudSecurity
Most companies misunderstand cloud inventory. It's not just server names—it's hardware, software licenses, and, critically, knowing where your data lives, jurisdiction by jurisdiction. This feeds your security strategy. #CloudSecurity #DataGovernance
Litigation against cloud providers is rare and risky. Courts often view liability as a shared responsibility between the provider and the enterprise. Risk assessment & mitigation plans are essential. #CloudSecurity #RiskManagement
Why can't enterprises get a handle on the #cloud misconfiguration problem? buff.ly/X3PHhVN @CSOonline @MariaKorolov #tech #cloudsecurity #digital #innovation #business #leadership #CIO #CTO #CDO #CEO #CISO #cybersecurity #digitaltransformation #cloudproviders #IT

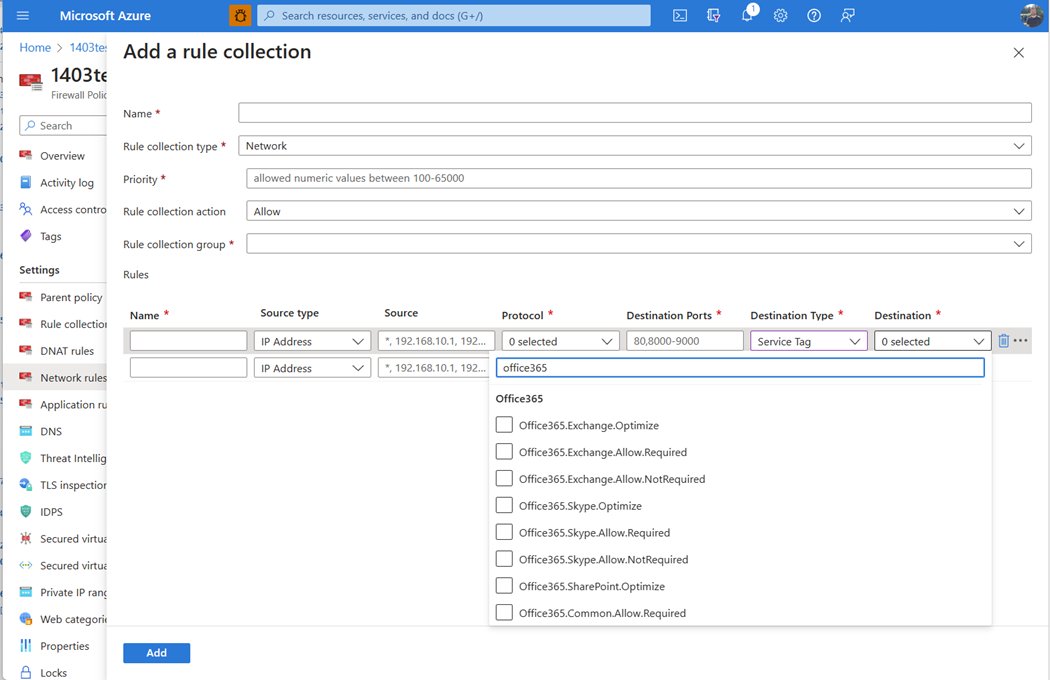
🛡️ Secure Microsoft 365 traffic with #Azure Firewall! ✅ Use built-in Service & FQDN tags 🔍 Allow outbound access to required endpoints 🚀 Simplify rule management & enhance protection Learn more 👉 msft.it/6018trW1I #CloudSecurity #Networking #M365
Fundamentals of Cloud and Cloud Security-TO READ amazon.com/Fundamentals-C… #CloudSecurity #cloudsecurityebook #cloudsecuritysolution #cybersecurityebook #CybersecurityCareer #CybersecurityTraining #applicationsecurityebook




80% of data breaches involve cloud data stores. Over-permissioned identities, misconfigurations & orphaned accounts are major risks. That’s why CIEM is now essential in cloud security. tycoonstory.com/how-to-impleme… #cloudsecurity #ciem #cnapp #cybersecurity #iam #dataprotection

🤖 Automate Threat Response with AI at the Cloud’s Edge ☁️ Cyberattacks are getting faster, more complex, and harder to stop — but with eScan’s AI-powered edge security, you can stay one step ahead. bit.ly/3vgw3Rn #eScan #AI #CloudSecurity #EdgeComputing #CyberSecurity

In today’s digital-first world, businesses rely on SaaS applications and cloud platforms to accelerate growth, collaboration, and innovation. bit.ly/3vgw3Rn #eScan #CloudSecurity #SaaSProtection #Cybersecurity #SecureEveryWorkflow #EmpowerEveryMove

🔍 How often should an organization conduct cloud security audits to ensure compliance and data protection? A) Monthly B) Annually C) Every 3 years D) As needed #CloudSecurity #CyberAwareness #DataProtection
Cloud ATOs are getting smarter. 🕵️♀️ At #BSidesLisbon, Permiso’s Enisa Hoxhaxhiku & Dredhza Braina will break down how password sprays + suspicious user-agents expose attackers before the breach. 📅 Nov 13 | “Anatomy of a Cloud ATO” | #CloudSecurity #ThreatResearch

Azure Local's security features are built-in by default. Microsoft Defender for Cloud gives an overview with recommendations for physical machines, VMs, and Kubernetes clusters. An end-to-end solution! #Azure #CloudSecurity #AzureLocal #AzureArc
Cloud threats are evolving fast. Is your org keeping up? Join us live on December 3rd for a virtual summit sponsored by @rubrikInc, and learn about the best practices top-performing teams are currently implementing. Register today: virtualizationreview.com/webcasts/2025/… #CloudSecurity

Critical vulnerabilities unveiled: Apache Syncope’s CVE-2025-65998 risks stored passwords; Fluent Bit RCE flaws enable cloud attacks; Oracle KEV exploits affect Canon; major breaches hit Dartmouth, SitusAMC, Almaviva, and more. #DataBreach #CloudSecurity ift.tt/u7mRinL
🔐 Microsoft 365 Security & Compliance Specialist needed! Remote, full-time, cloud security + DLP + Azure AD. 👉 tohoza.com/ad/microsoft-3… #InfoSec #CloudSecurity #RemoteWork
The more I explore cloud security, the clearer it becomes: breaches rarely happen because someone ‘hacked’ everything. Most incidents start with one small overlook. • an unused IAM role • a test bucket left public • logging turned off temporarily #CloudSecurity #CyberSecurity
In parallel, there have been critical vulnerabilities disclosed in Fluent Bit, a popular log processor used in cloud environments. #FluentBit #CloudSecurity
Geografisch verteilte Clouds für MSPs und Reseller in der DACH-Region mit Cubbit und WIIT => innovative-trends.de/2024/12/06/geo… <= #Recht #Security #CloudSecurity #Frankfurt #Düsseldorf #StartUp #ITSicherheit #ITManagement #DigitaleTransformation #Backup #Digitalisierung #NIS2 #Cubbit
Hammer Distribution’s new Sensra service offers 24×7 monitoring and response from its UK SOC, using Seceon’s aiSIEM + aiXDR to safeguard hybrid and multi-cloud environments. businesspartnermagazine.com/hammer-distrib… #aiXDR #CloudSecurity
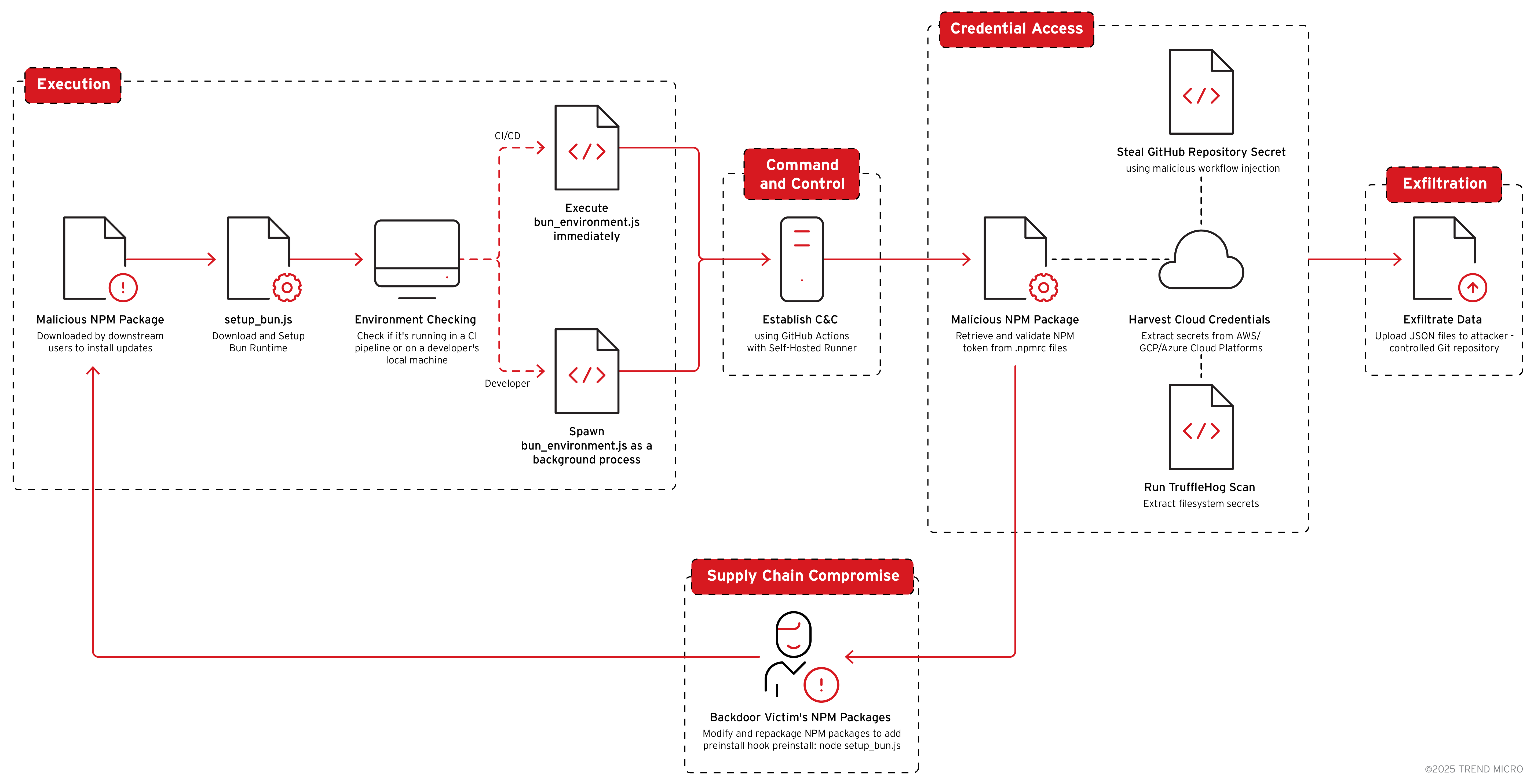
Shai-hulud 2.0 malware targets AWS, GCP, Azure, GitHub, and NPM by stealing credentials and injecting backdoors into repos and packages, enabling worm-like supply chain attacks with malicious preinstall hooks. #CloudSecurity #DevOpsRisk #ShaiHulud ift.tt/hUB24Sq
🛡️ El SASE (Secure Access Service Edge) es ideal para empresas distribuidas: protege usuarios sin importar dónde estén. La arquitectura del futuro ya está aquí. 📲Contáctanos y agenda una revisión de tu ciberseguridad. #SASE #ZeroTrust #CloudSecurity #Cibercorp

Cloud threats are evolving fast. Is your org keeping up? Join us live on December 3rd for a virtual summit sponsored by @rubrikInc, and learn about the best practices top-performing teams are currently implementing. Register today: virtualizationreview.com/webcasts/2025/… #CloudSecurity

Cloud breaches usually come from one cause: misconfigurations. Secure it. Monitor it. Review it. #cloudsecurity #azure #yyc #cybersecurity

Thankful today for the businesses that trust Cloud77 to power and protect their tech. 🎁 As a small thank you, we’re opening early access to our December MSP growth session. Reply THANKFUL for the invite. Happy Thanksgiving! #MSP #ITFirm #CloudSecurity #ITSolutions

The new Gartner® Market Guide for CNAPP shows what teams want: fewer tools and more unified visibility. Uptycs delivers that with one platform that connects code, cloud, and runtime. hubs.ly/Q03VL-MT0 #CNAPP #CloudSecurity
Join DataSunrise at AWS re:Invent 2025! Discover cutting-edge database security solutions, network with industry experts, and explore innovations in data protection and compliance for cloud environments. bit.ly/42XBtSF #AWSreInvent #DataSecurity #CloudSecurity

A tool for unauthenticated enumeration of AWS, Azure, and GCP Principals github.com/righteousgambi… By @WesLadd #cybersecurity #infosec #cloudsecurity

Life Lately, I’ve been playing around a lot with Google Cloud Platform (security~wise) as to becoming an expert security engineer. Not for work but for personal development and I have another guide put together. I’ll share with y’all soon. #CloudSecurity

☁️ Cloud Security Tools — Essential Toolkit for Modern Teams 🛡️🚀 #CloudSecurity #InfoSec #DevSecOps #CyberSecurity #CSPM #CWPP #IAM #SIEM #ContainerSecurity #Compliance #SecurityTools #CloudComputing ☁️🛡️




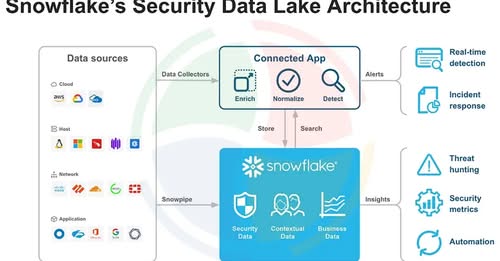
Your data deserves fortress-level protection. 🛡️ Learn how Snowflake’s multi-layered security, encryption, and IAM framework keep your cloud data safe. 👉 bit.ly/47tH71r #Snowflake #CloudSecurity #DataProtection
🔐 Nearly 80% of breaches in 2025 involve stolen credentials. We reviewed the 8 best enterprise password managers for 2025, comparing features, pricing, and ideal use cases. 👉 See the full list: techrepublic.com/article/enterp… #Cybersecurity #CloudSecurity #PasswordManager #Infosec…

🤖 Automate Threat Response with AI at the Cloud’s Edge ☁️ Cyberattacks are getting faster, more complex, and harder to stop — but with eScan’s AI-powered edge security, you can stay one step ahead. bit.ly/3vgw3Rn #eScan #AI #CloudSecurity #EdgeComputing #CyberSecurity

Crea tu propio SO en la nube con Puter. ☁️ Un entorno open-source y auto-alojable para máximo control y privacidad, ideal para aislar tus proyectos y datos de forma segura. Link: github.com/heyPuter/puter/ 🔒 [#Puter #SelfHosted #CloudSecurity #Privacy]
![EsGeeks's tweet image. Crea tu propio SO en la nube con Puter. ☁️ Un entorno open-source y auto-alojable para máximo control y privacidad, ideal para aislar tus proyectos y datos de forma segura.
Link: github.com/heyPuter/puter/
🔒 [#Puter #SelfHosted #CloudSecurity #Privacy]](https://pbs.twimg.com/media/G5BBQRgXkAAY_ZU.jpg)
The Latio 2025 Cloud Security Market Report confirms what we’ve long believed: the future of #cloudsecurity lies in Continuous Threat Exposure Management (CTEM). At Tenable, we’re leading this evolution - empowering organizations with a unified view of... ow.ly/Azn1106p0bh

A tool for unauthenticated enumeration of AWS, Azure, and GCP Principals github.com/righteousgambi… By @WesLadd #cybersecurity #infosec #cloudsecurity

In today’s digital-first world, businesses rely on SaaS applications and cloud platforms to accelerate growth, collaboration, and innovation. bit.ly/3vgw3Rn #eScan #CloudSecurity #SaaSProtection #Cybersecurity #SecureEveryWorkflow #EmpowerEveryMove

From compliance to containers—secure your AWS stack with: ✅ NIST, PCI DSS, GDPR ✅ Serverless & IoT protection ✅ Multi-cloud & hybrid strategies Built for cloud pros & security enthusiasts. 🛡️ #CloudSecurity #AWS #DevSecOps #CyberResilience 🔗 ow.ly/VQ7H50X6qT6

🤯 Only 6% of organizations feel “very capable” of withstanding cyberattacks. 🤔 Yet 60% call it a top priority. Big gap. Big opportunity. Here’s how leaders can close it, and why AI is leading the way: hubs.la/Q03T2Rw20 #CyberResilience #AI #CloudSecurity

#IFITechsolutions helped L&T's achieve proactive, Microsoft-powered security. Learn more: bit.ly/3KhVg9d #CyberSecurity #CloudSecurity #ManagedSecurity #MicrosoftDefender #MicrosoftPartner #ThreatProtection #MicrosoftSecurity #AzureSecurity

📌Big data. Bigger risks. Your cloud needs strong security to stay safe from leaks and breaches. Join @innovationhubug on the professional talk for insights on must secure areas in cloud protectioin. #DataProtection #Innovationhubug #CloudSecurity

The future of cloud security gets defined at re:Invent. See CyberArk at Booth #359 — securing human, machine + AI agent identities across AWS. Book strategy time with our team: spr.ly/60137r4I5 #IdentitySecurity #CloudSecurity #Cybersecurity #AWSreInvent

Why can't enterprises get a handle on the #cloud misconfiguration problem? buff.ly/X3PHhVN @CSOonline @MariaKorolov #tech #cloudsecurity #digital #innovation #business #leadership #CIO #CTO #CDO #CEO #CISO #cybersecurity #digitaltransformation #cloudproviders #IT

Ready to level up your #cloudsecurity game? 🔒 Master Azure's robust security features & prep for AZ-500. Become the security champion your IT needs: bit.ly/3JkHtyd #azure #microsoft #training #certification #learningpath

Fundamentals of Cloud and Cloud Security-TO READ amazon.com/Fundamentals-C… #CloudSecurity #cloudsecurityebook #cloudsecuritysolution #cybersecurityebook #CybersecurityCareer #CybersecurityTraining #applicationsecurityebook




Tata Motors Fixes Security Flaws That Exposed Sensitive Customer and Dealer Data cysecurity.news/2025/11/tata-m… #CloudSecurity #Criticalsecurityflaw #CustomerData

Your data stays safe, your team stays productive—Atlantic.net has you covered #CloudSecurity #DataProtection #CyberSecurity #SecureCloud #HackProof

John Grancarich shares why 2026 is the year of DSPM, tackling data sprawl across cloud, SaaS, and AI with visibility that powers stronger risk decisions. Part of the @vmblog 2026 Predictions Series: hubs.la/Q03TbN5N0 #DSPM #DataSecurity #CloudSecurity

Something went wrong.
Something went wrong.
United States Trends
- 1. Ravens 47.2K posts
- 2. Ravens 47.2K posts
- 3. Lamar 38.2K posts
- 4. Joe Burrow 14.4K posts
- 5. Zay Flowers 3,426 posts
- 6. Chiefs 102K posts
- 7. Cowboys 86.3K posts
- 8. Derrick Henry 4,034 posts
- 9. #WhoDey 2,636 posts
- 10. Zac Taylor 2,390 posts
- 11. Perine 1,414 posts
- 12. #CINvsBAL 2,379 posts
- 13. Mahomes 32.1K posts
- 14. Cam Boozer 1,839 posts
- 15. Tanner Hudson 1,173 posts
- 16. Sarah Beckstrom 182K posts
- 17. Tinsley 1,545 posts
- 18. AFC North 1,762 posts
- 19. Jason Garrett N/A
- 20. Myles Murphy N/A