你可能會喜歡
سعدت بالحصول على مكافأة مالية بقيمة 21 الف ريال من منصة اكتشاف الثغرات @BugBountySA #BugBounty
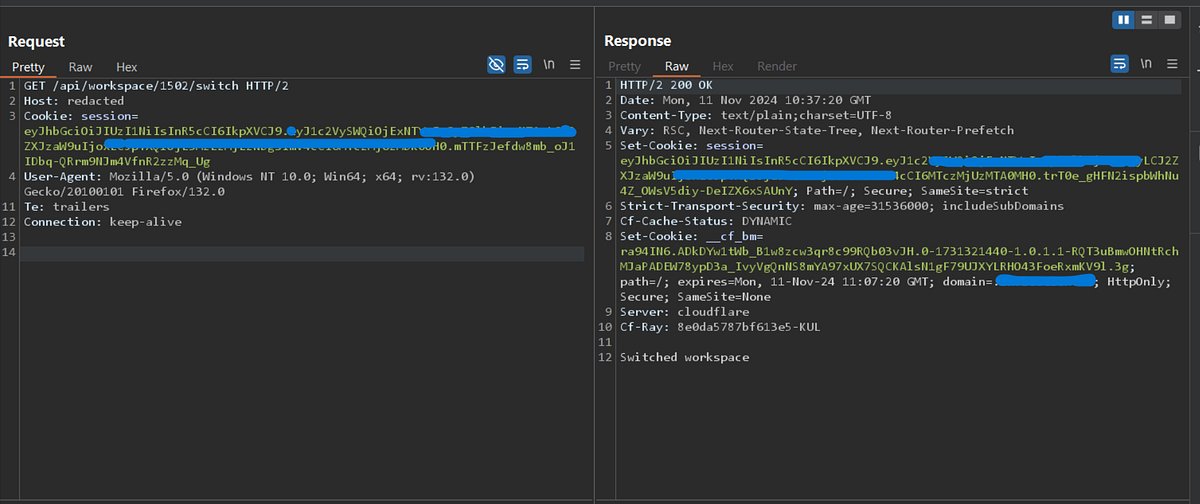
One of the biggest mistakes you probably make when trying to find an API token or sensitive information in JS files is relying only on automated tools like JSRecon without checking the files manually. I found an access token that let me into a company's internal website where i…
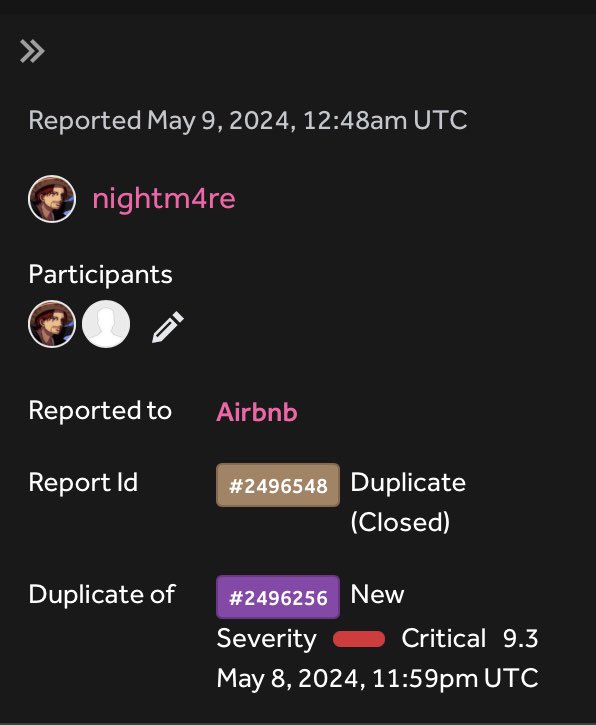
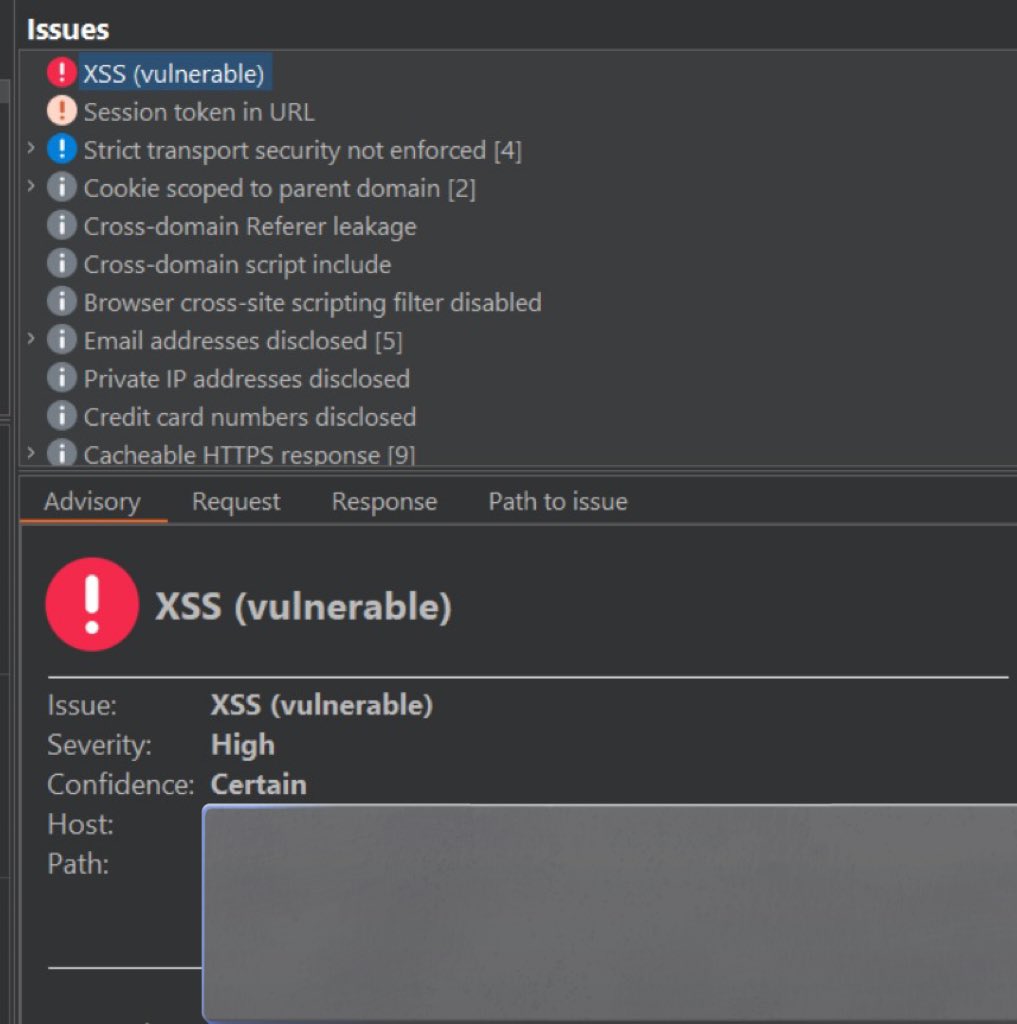
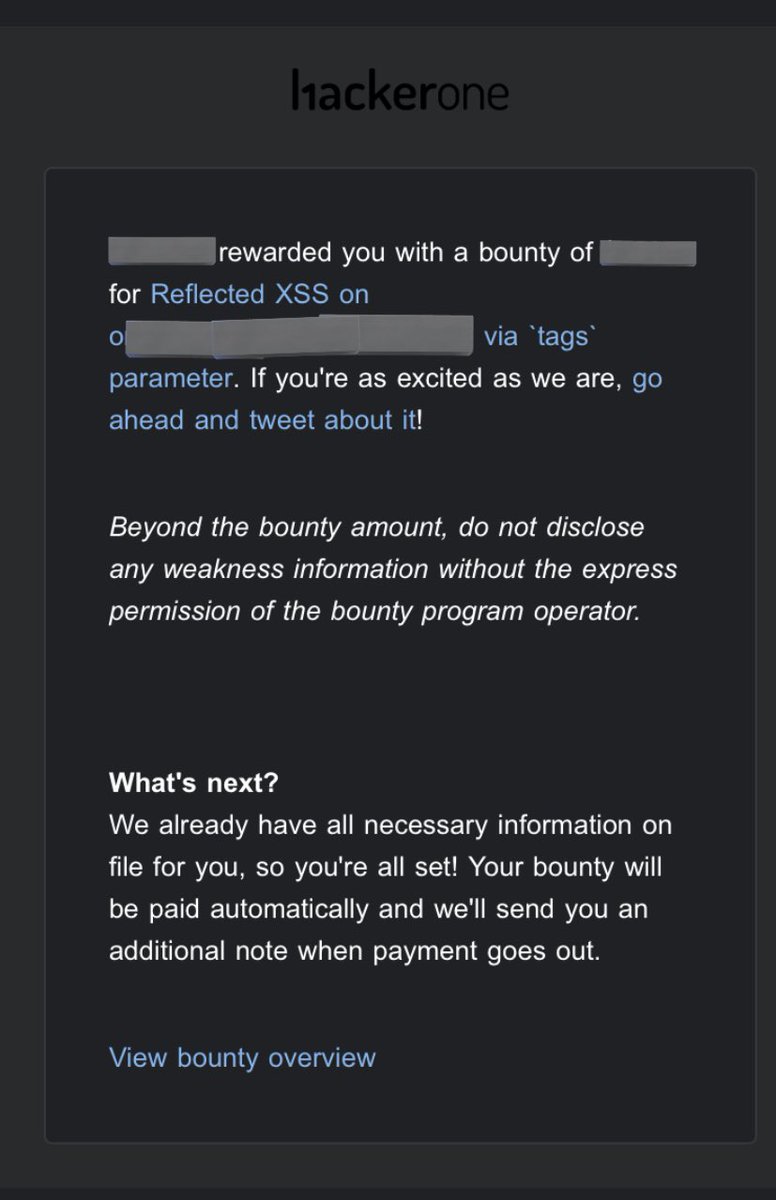
Here is the write-up for the vulnerability I found a few days ago medium.com/@Ibrahimsec/ho…
I was awarded a $3,000 bounty on @Hacker0x01! hackerone.com/nightm4re #TogetherWeHitHarder ATO i guess?
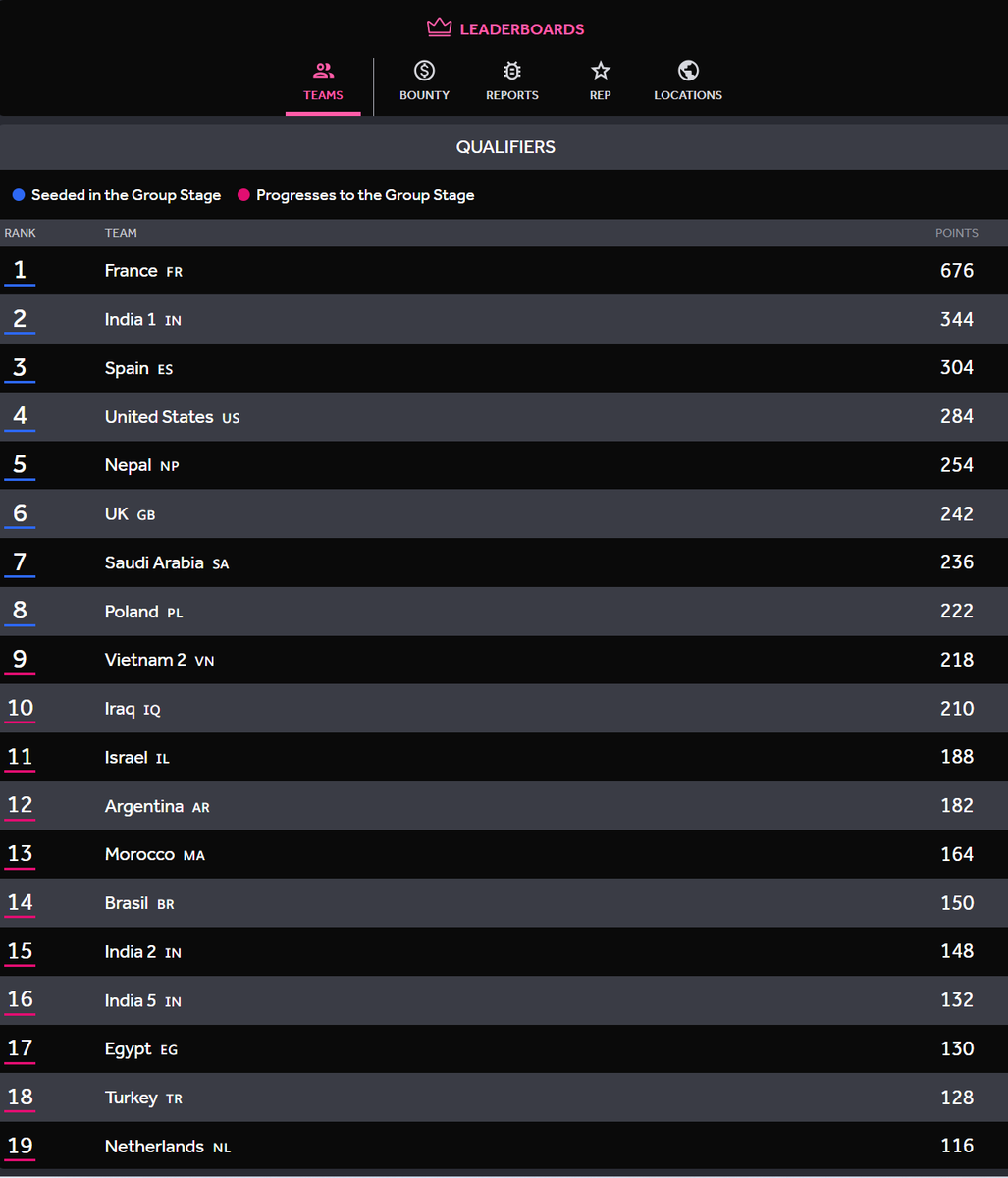
Saudi Arabia TEAM is on FIRE!! 🔥🔥 4 days remaining Leaderboard: leaderboards.hackerone.live/awc2024 #AmbassadorWorldCup @Hacker0x01
I was awarded a $3,000 bounty on @Hacker0x01! hackerone.com/nightm4re #TogetherWeHitHarder ATO i guess?
See you in the next round!
الحمدلله ممثلين لفريق السعودية 🇸🇦 تأهلنا الى دور الـ16 في كأس العالم هكر ون، شكراً @hacker0x01 على التنظيم الرهيب. فخورين بفريقنا ونكمل مشوارنا للقب بتوفيق الله! 🏆🚀 We made it! Team Saudi to the Sweet Sixteen in #AWC2024 🎉, Huge thanks to @Hacker0x01 for the amazing event
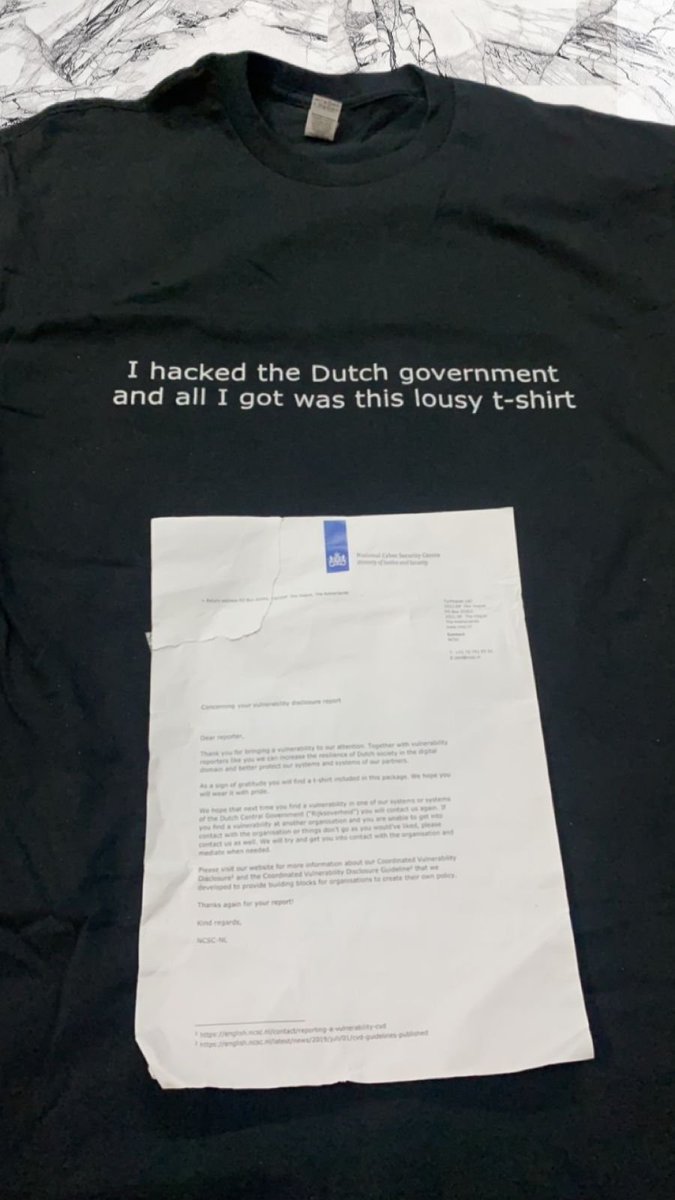
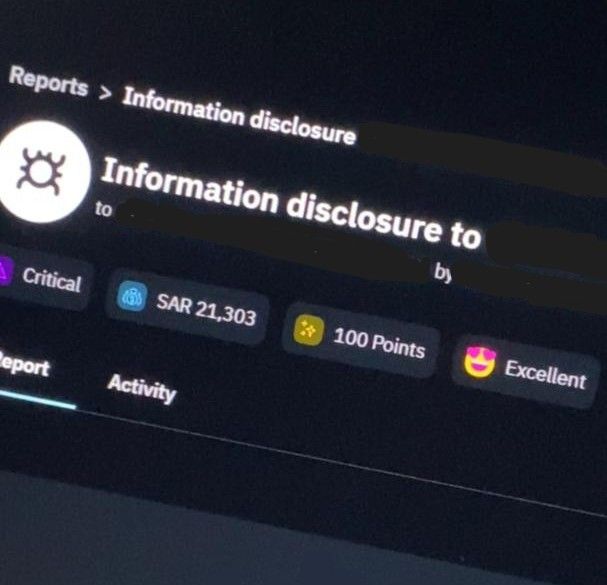
LY Corporation disclosed a bug submitted by @leetibrahim: hackerone.com/reports/2403554 #hackerone #bugbounty

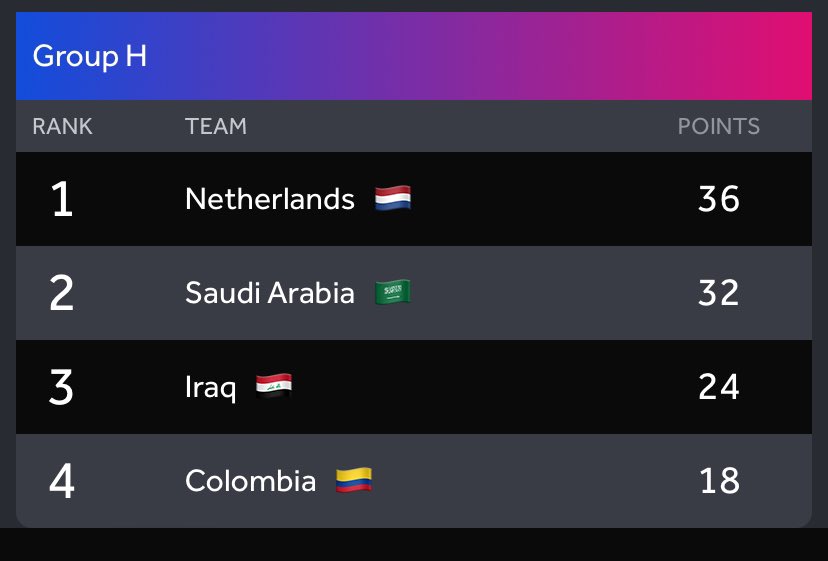
الحمدلله تأهلنا مع ال32 فريق الى دور المجموعات وضمن الفرق الاساسية (افضل 8 فرق) في مسابقة كأس العالم هكر ون 2024 🇸🇦💪 Saudi Arabia qualified to group stage with 32 teams and as one of the main teams for the next round (Top 8) 🇸🇦💪 #AWC2024
I was awarded a $2,400 bounty on @Hacker0x01! hackerone.com/nightm4re #TogetherWeHitHarder Broken Access Control
تم قبول ممثلي المملكة العربية السعودية 🇸🇦 لمسابقة AWC 2024 هكر ون @Hacker0x01 🏆 المشاركين: @AMakki1337 @0x_rood @eman_yazji @r00t_nasser @0xRaw @0xRAYAN7 @Ahmed0Makki @Ibrah1m_0x @leetibrahim @AlHomaidNoor @abdlah_md @stuipds @Liliexx2 @omarzzu @9yk @Dr_Ro0T

My tip on how I found a subdomain takeover: 1. Got a notification that a new domain had been added to the scope 2. Subdomain enum using ffuf, resolved them using dnsx 3. Checked the CNAME of valid subdomains 4. One of the subdomains was pointing to non-registered Azure service.
Don't discount dead subdomains in bug bounty! Try enumerating them against valid target IP addresses, who knows what you might find 😏 @leetibrahim has had some success with this tip, hopefully you will too! #bugbounty #bugbountytips 👇

United States 趨勢
- 1. Thanksgiving 740K posts
- 2. #StrangerThings5 300K posts
- 3. BYERS 70K posts
- 4. robin 106K posts
- 5. Afghan 334K posts
- 6. #DareYouToDeath 129K posts
- 7. Dustin 61.9K posts
- 8. Vecna 69.3K posts
- 9. Holly 70.8K posts
- 10. Reed Sheppard 7,112 posts
- 11. Jonathan 75.1K posts
- 12. noah schnapp 9,451 posts
- 13. mike wheeler 10.8K posts
- 14. Rahmanullah Lakanwal 131K posts
- 15. hopper 17.4K posts
- 16. Taliban 43K posts
- 17. derek 21.7K posts
- 18. Nancy 70.4K posts
- 19. Podz 5,313 posts
- 20. Lucas 86.3K posts
你可能會喜歡
-
 0xRAYAN 🇸🇦
0xRAYAN 🇸🇦
@0xRAYAN7 -
 Tur.js
Tur.js
@Tur24Tur -
 Abdelrhman Allam 🇵🇸
Abdelrhman Allam 🇵🇸
@sl4x0 -
 Fares
Fares
@_2os5 -
 /usr/bin/fares
/usr/bin/fares
@SirBagoza -
 Mohamed Elkhayat
Mohamed Elkhayat
@Mohamed87Khayat -
 🇸🇦 Murtada Bin Abdullah (Rood)
🇸🇦 Murtada Bin Abdullah (Rood)
@0x_rood -
 Unhandled0xD
Unhandled0xD
@trap_handler -
 Fahad
Fahad
@Pwn3dx -
 𝐱𝐫𝟎𝐨𝟎𝐭𝐱 🇸🇦
𝐱𝐫𝟎𝐨𝟎𝐭𝐱 🇸🇦
@xr0o0tx -
 0xRaw
0xRaw
@0xRaw -
 Hossam A. Mesbah 🇵🇸
Hossam A. Mesbah 🇵🇸
@m359ah -
 Abdalla Abdelrhman
Abdalla Abdelrhman
@0x2nac0nda -
 يعقوب الحربي
يعقوب الحربي
@az7rb -
 Al-hassan abbas | الحسن عباس
Al-hassan abbas | الحسن عباس
@exploit_msf
Something went wrong.
Something went wrong.