hacker.house
@myhackerhouse
World-class ethical hacking services, training and software. Cutting-edge cybersecurity solutions, privacy and technical services.
คุณอาจชื่นชอบ
Hands-On Hacking training course from Hacker House - learn how attackers target and breach networks using real-world applied hacking techniques. Have you ever wanted to learn how to hack? Try our FREE sample module, crack a server & learn new skills hacker.house/training
Wi-Fi Attack Training Manual (Version: 1.0 (Internal Training – Military & Public Security Use)) - 0x0.st/Kpqv.pdf
The #KnownSec "RESTRICTED – Military/Public Security Use Only" contained image teasers from files. Using OCR, translation and AI, I was able to reconstruct the 15 pages of "Wi-Fi Attack Training". There is reference to a 2019 0day (at the time) WiFi exploit DRAGONBLOOD.

Technical analysis of AIX 5.3L libc locale environment variable handling vulnerability that enables local privilege escalation to root. overs the buffer overflow mechanism, PowerPC shellcode construction, and exploitation technique targeting /usr/bin/su. deepwiki.com/hackerhouse-op…


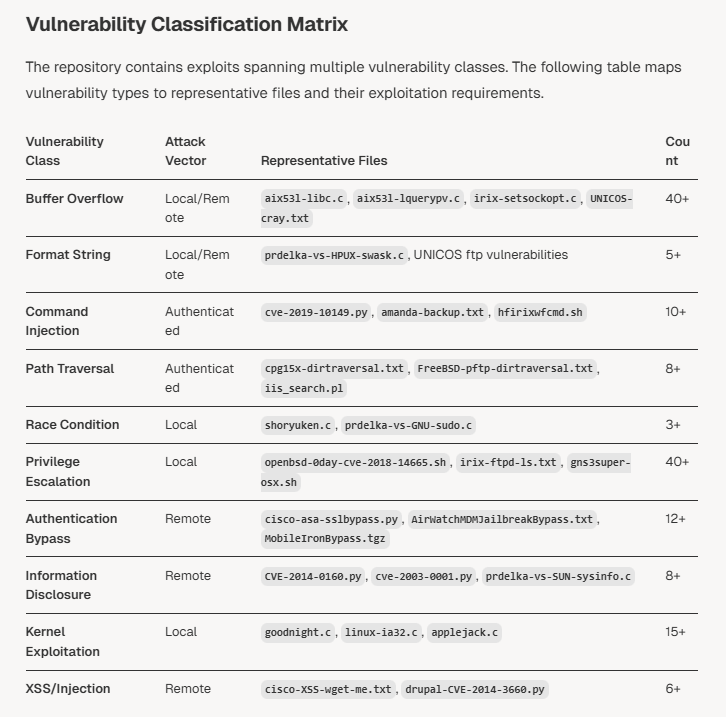
Exploits for Unix variants with significant historical value and may still exist in specialized environments such as scientific computing facilities, ICS, and legacy envs. Coverage includes Cray UNICOS, SGI IRIX, Solaris, HP-UX, and SCO Unix systems. deepwiki.com/hackerhouse-op…

SignToolEx, a code-signing tool that enables the use of expired certificates for executable signing operations. deepwiki.com/hackerhouse-op…

Exploiting Windows Installers with SetupHijack: Race Conditions, UAC Bypasses, and Privilege Escalation hacker.house/blog/exploitin…

High-Risk Vulnerabilities in Microsoft Telnet MS-TNAP Implementation hacker.house/blog/critical-…

Credential harvesting through the Microsoft Telnet NTLM Authentication Protocol (MS-TNAP). Implements a malicious Telnet server that exploits a protocol-level vulnerability in telnet.exe to capture NTLM authentication material via URIs. deepwiki.com/hackerhouse-op…

OffensiveLua is a collection of 20+ offensive security scripts written in Lua that perform red team operations through direct Windows API calls. The repo includes OffensiveLuaEmbedded.exe that embeds LuaJIT with advanced debugging capabilities. deepwiki.com/hackerhouse-op…

145+ documented vulnerabilities, covers vulnerabilities from the 1990s (Cray UNICOS, SGI IRIX) through modern systems (2025 IIS exploits), providing both educational value and historical context for security researchers and penetration testers. deepwiki.com/hackerhouse-op…
I was exploiting time extensions in TCP recently and observed a peculiar behavior that the Linux kernel doesn't actually randomize timestamps when you tell it to, see - timecrime.c raw.githubusercontent.com/hackerhouse-op…
SetupHijack is a security research tool that exploits race conditions and insecure file handling in Windows installer and update processes. github.com/hackerhouse-op…

Texas Instruments Code Composer Setup UAC Bypass. [0day]
![hackerfantastic's tweet image. Texas Instruments Code Composer Setup UAC Bypass. [0day]](https://pbs.twimg.com/media/G1t2p2cXMAA8IE2.jpg)
SetupHijack is a security research tool that exploits race conditions and insecure file handling in Windows installer and update processes to elevate privileges. github.com/hackerhouse-op…

"Make sure to keep your computer up to date" ;)

SetupHijack is a security research tool that exploits race conditions and insecure file handling in Windows installer and update processes to elevate privileges. github.com/hackerhouse-op…

United States เทรนด์
- 1. #BaddiesUSA 62K posts
- 2. Rams 29.6K posts
- 3. TOP CALL 3,433 posts
- 4. #LAShortnSweet 22.4K posts
- 5. Scotty 9,997 posts
- 6. #centralwOrldXmasXFreenBecky 306K posts
- 7. SAROCHA REBECCA DISNEY AT CTW 327K posts
- 8. Eagles 142K posts
- 9. Chip Kelly 8,811 posts
- 10. sabrina 63.4K posts
- 11. #ITWelcomeToDerry 15.9K posts
- 12. AI Alert 1,033 posts
- 13. Market Focus 2,300 posts
- 14. Raiders 68.2K posts
- 15. Vin Diesel 1,340 posts
- 16. #RHOP 12.4K posts
- 17. Ahna 7,421 posts
- 18. Stacey 24.7K posts
- 19. billie 19.9K posts
- 20. Stafford 15.3K posts
คุณอาจชื่นชอบ
-
 hacker.house
hacker.house
@hackerfantastic -
 Snow
Snow
@_sn0ww -
 MalwareHunterTeam
MalwareHunterTeam
@malwrhunterteam -
 SANS Offensive Operations
SANS Offensive Operations
@SANSOffensive -
 Will Schroeder
Will Schroeder
@harmj0y -
 Security BSides
Security BSides
@SecurityBSides -
 Rapid7
Rapid7
@rapid7 -
 SpecterOps
SpecterOps
@SpecterOps -
 Nextron Systems
Nextron Systems
@nextronsystems -
 Metasploit Project
Metasploit Project
@metasploit -
 hasherezade
hasherezade
@hasherezade -
 x0rz
x0rz
@x0rz -
 HackerOne
HackerOne
@Hacker0x01 -
 Florian Roth ⚡️
Florian Roth ⚡️
@cyb3rops -
 TrustedSec
TrustedSec
@TrustedSec
Something went wrong.
Something went wrong.