내가 좋아할 만한 콘텐츠
The blog.mantrainfosec.com/blog/18/prepar… post by @xoreipeip shows how prepared statements can be exploited in NodeJS using mysql and mysql2 packages leading to SQLi! 🪄 So use of prepared statement might not be the ultimate solution here 🥵 as a side note, @xoreipeip later found this…
A penetration tester got root access to our Kubernetes cluster in 15 minutes. Here's what they exploited. The attack chain: - Found exposed Kubernetes dashboard (our bad) - Dashboard had view-only service account (we thought this was safe) - Service account could list secrets…
The security vulnerability we found in Perplexity’s Comet browser this summer is not an isolated issue. Indirect prompt injections are a systemic problem facing Comet and other AI-powered browsers. Today we’re publishing details on more security vulnerabilities we uncovered.
OMG.. whatsapp 0c in pwn2own
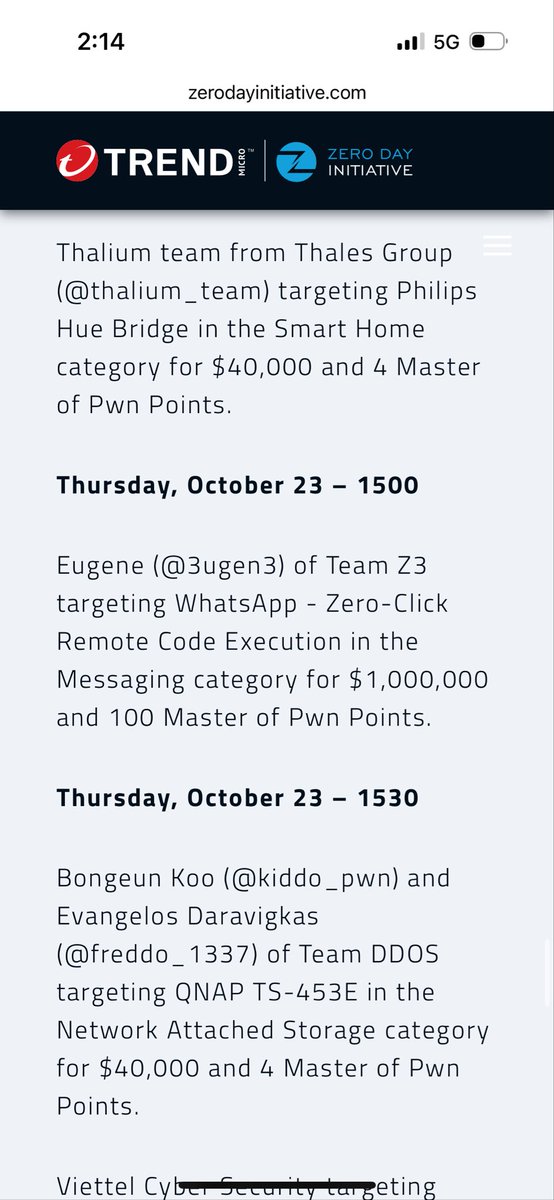
We just launched a $4.5m bug bounty live hacking event competition targeting the most popular cloud & ai open source software 🧵

The watchTowr Labs team is back, providing our full analysis of the Oracle E-Business Suite Pre-Auth RCE exploit chain (CVE-2025-61882). Enjoy with us (or cry, your choice..) labs.watchtowr.com/well-well-well…
The team at @OpenAI just fixed a critical account takeover vulnerability I reported few hours ago affecting #ChatGPT. It was possible to takeover someone's account, view their chat history, and access their billing information without them ever realizing it. Breakdown below 👇
I've been researching the Microsoft cloud for almost 7 years now. A few months ago that research resulted in the most impactful vulnerability I will probably ever find: a token validation flaw allowing me to get Global Admin in any Entra ID tenant. Blog: dirkjanm.io/obtaining-glob…
The @ReconVillage at @DEFCON 33 explored the digital terrain with Live Recon, GE(O)SINT, CTFs & labs. 🗺️ 🔍 Shoutout to @NahamSec @Jhaddix @DanielMiessler @InfosecVandana @niksthehacker @jeff_foley @anantshri & others! All #DEFCON33 villages 👇🏽 infosecmap.com/event/def-con-… #InfoSec

Had an amazing time at my first #BSidesAhmedabad 🎉 Great discussions, diverse connections & of course the mandatory MSRC team pic + group selfies 📸




No doubt, the fieriest panel of all🔥🔥
I will be at @bsidesahmedabad this year to talk about bug bounty and security with John Deere CISO Carl Kubalsky on 12th and 13th in an open Panel. If you are around please come say high :)
When the hunters of threats join the battlefield, you know the game changes. ⚔️🛡️ We’re beyond thrilled to announce @CrowdStrike as the Cyber Security Partner at BSides Ahmedabad 0x06 — bringing the power of Falcon intelligence to the most awaited cyber security gathering of the…

Sept 12–13: BSides Ahmedabad 🇮🇳 — Positive Technologies Offensive Team from @ptswarm with talks, networking & fresh research. Sept 13: Standoff Hacks finale — top bug hunters, private bounty scope & party. @amoshkov has the secret code for the grand party, DM him to crash it 👀

🇮🇳 Independence = Incredible Savings! This Independence Day, BSides Ahmedabad is celebrating with you! Grab your passes now and enjoy a patriotic 15% discount because liberty deserves a great learning party!🎉 Use coupon code “FREEDOM” & get 15% Off on Delegate & Professional…

🟥🟦 CTF teams, take note — Standoff Cyberbattle 16, October 6–8, online. 💰 $17,500 prize pool. 30 hours of pure Attack–Defence. 1500+ real-world systems, PLC/SCADA included, 30 hours of epic battle. Apply by Sept 1 → 16.standoff365.com/en/

The @SLCyberSec research team is releasing our final research post for our Christmas in July efforts, two RCEs and one XXE (all pre-auth) in Adobe Experience Manager Forms. One of the RCEs and the XXE still do not have official patches: slcyber.io/assetnote-secu…
🚨 Only 45 Days to Go! 🚨 BSides Ahmedabad 0x06 is almost here! 🎟️ Grab your pass NOW to witness the finest in cybersecurity — where cyber brilliance meets real-world defense➡️🔗konfhub.com/security-bside… Don’t just hear about it — be there. #BSidesAhmedabad #CyberSecurity…

I have launched YSoNet (ysonet.net) and added #SharePoint CVE-2025-49704 payload generator to it as the first thing. Here is how this can work: Running command: ``` ysonet.exe -p sharepoint --cve=CVE-2025-49704 -var 1 -c "calc" ``` Running C# code: ``` ysonet.exe…
Blog for ToolShell Disclaimer: The content of this blog is provided for educational and informational purposes only. blog.viettelcybersecurity.com/sharepoint-too… #SharePoint #ToolShell

United States 트렌드
- 1. Texans N/A
- 2. #MissUniverse 63.6K posts
- 3. James Cook 4,257 posts
- 4. #TNFonPrime 1,435 posts
- 5. Will Anderson 2,831 posts
- 6. Davis Mills 1,677 posts
- 7. Sedition 229K posts
- 8. Shakir 3,288 posts
- 9. Nico Collins 1,109 posts
- 10. Prater N/A
- 11. Christian Kirk 2,313 posts
- 12. Treason 122K posts
- 13. Lamelo 9,259 posts
- 14. Cheney 105K posts
- 15. Seditious 129K posts
- 16. #BUFvsHOU 1,573 posts
- 17. #htownmade 1,240 posts
- 18. Paul George 2,082 posts
- 19. TMNT 6,370 posts
- 20. Commander in Chief 64.9K posts
내가 좋아할 만한 콘텐츠
-
 Frans Rosén
Frans Rosén
@fransrosen -
 Geekboy
Geekboy
@emgeekboy -
 mohammed eldeeb
mohammed eldeeb
@malcolmx0x -
 Yassine Aboukir 🐐
Yassine Aboukir 🐐
@Yassineaboukir -
 Tanner
Tanner
@itscachemoney -
 Th3g3nt3lman
Th3g3nt3lman
@Th3G3nt3lman -
 Rahul Maini
Rahul Maini
@iamnoooob -
 André Baptista
André Baptista
@0xacb -
 todayisnew
todayisnew
@codecancare -
 Joel Margolis (teknogeek)
Joel Margolis (teknogeek)
@0xteknogeek -
 Patrik Fehrenbach
Patrik Fehrenbach
@ITSecurityguard -
 pwnmachine 👾
pwnmachine 👾
@princechaddha -
 Parth Malhotra
Parth Malhotra
@Parth_Malhotra -
 Inti De Ceukelaire
Inti De Ceukelaire
@securinti -
 Bhavuk Jain
Bhavuk Jain
@bhavukjain1
Something went wrong.
Something went wrong.