Mickey Jin
@patch1t
Exploring the world with my sword of debugger : )
You might like
As promised, I just dropped a dozen new sandbox escape vulnerabilities at #POC2024 If you missed the talk, here is the blog post: jhftss.github.io/A-New-Era-of-m… Slides: github.com/jhftss/jhftss.… Enjoy and find your own bugs 😎
Actually, 15+ new sandbox escape vulnerabilities discovered. All of them are simple logic issues. You may find your own sandbox 0-days by yourself after listening to this talk!🔥🔥🔥
Excited to share our research on ChillyHell, a modular macOS backdoor targeting officials in Ukraine. Check out our write-up for more details. jamf.com/blog/chillyhel…
For those missing the talk, Blog: jhftss.github.io/Exploiting-the… Slides: github.com/jhftss/jhftss.…
A tiny timing flaw in Apple’s core file-copy APIs can put millions of devices at risk 📂🍏 Despite warnings, Apple thought it was “too hard to exploit”—until Mickey Jin developed an exploit that steals secrets in privileged services 👉nullcon.net/berlin-2025/sp… #NullconBerlin2025

Thank you @helpnetsecurity to mention us 👍 awesome research by @tsunek0h #macOS #applesecurity #NullconBerlin2025 helpnetsecurity.com/2025/09/04/mac…
🚨 New blog post: ELEGANTBOUNCER - Catch iOS 0-click exploits without having the samples. Features iOS backup forensics & messaging app scanning for iMessage, WhatsApp, Signal, Telegram & Viber attachments. 🔗 Link -> msuiche.com/posts/elegantb…
🍏 #AppleDevelopers use NSFileManager thinking it’s safe — but @patch1t found a race condition once thought “impossible to exploit.” At #NullconBerlin2025, he’ll show how it works, why CVE-2024-54566 failed, and Apple’s final fix. 👉 nullcon.net/berlin-2025/sp… #iOS #applesecurity

Brief info and POC for this week's Apple 0click iOS 18.6.1 RCE bug CVE-2025-43300 github.com/b1n4r1b01/n-da…

We released our Fuzzilli-based V8 Sandbox fuzzer: github.com/googleprojectz… It explores the heap to find interesting objects and corrupts them in a deterministic way using V8's memory corruption API. Happy fuzzing!
Launch constraints are annoying as a security researcher. What if you didn't have to worry about them? wts.dev/posts/bypassin…
So CVE-2025-43268 was indeed my vuln in cryptexctl, but @0x3C3E found it first, kudos to him. Here's the "exploit", which makes sudo try and load an unsigned dylib from the current directory: /S*/L*/S*/u*/b*/c*.r* exec $PWD/ sudo ls
📢 Just dropped: the full #OBTS v8 talk lineup! objectivebythesea.org/v8/talks.html And for the first time we'll have 3 full days of presentations! 🤩 Congrats to the selected speakers and mahalo to all who submitted. With ~100 submissions, selecting the final talks was a daunting task! 😫
I lightly mentioned CVE-2025-31235, a double-free I found in coreaudiod/CoreAudio, during my OffensiveCon presentation last month. It's been derestricted now, so enjoy my writeup which includes a PoC and dtrace script to help understand the vulnerability! project-zero.issues.chromium.org/issues/4062711…
My "Finding Vulnerabilities in Apple Packages at Scale" talk is up on YT 🎉
All talks from #SecurityFest are now published on YouTube for your enjoyment. Grab some popcorn and binge watch! youtube.com/@securityfest
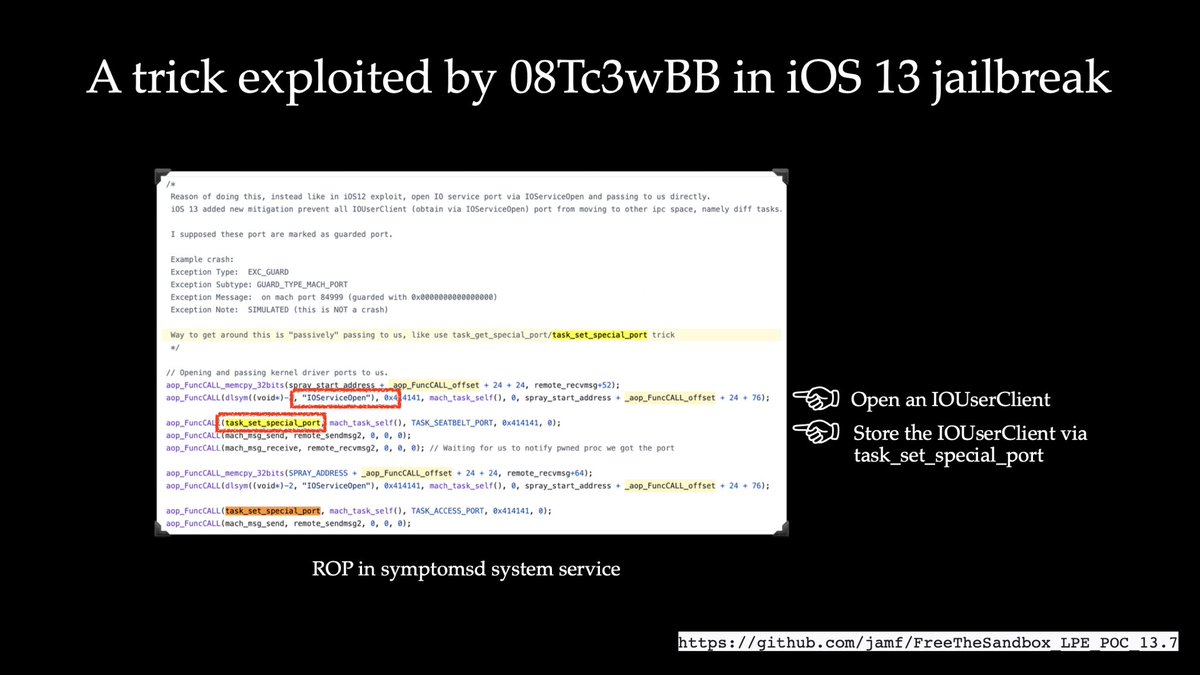
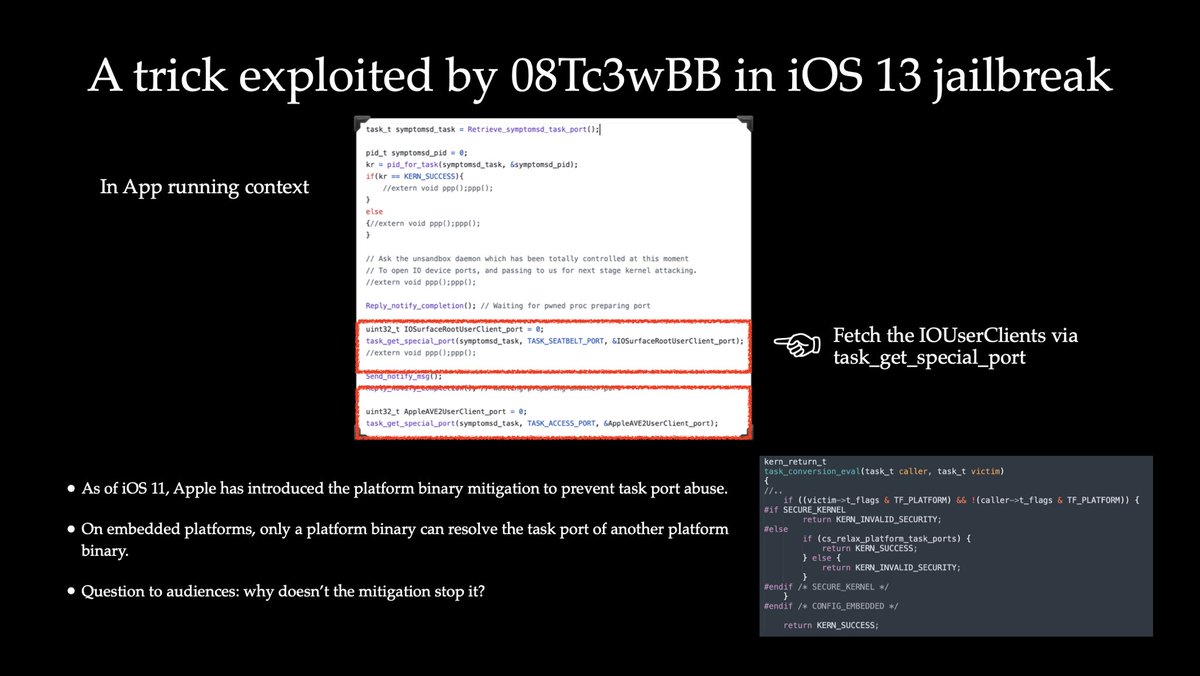
Woah, @WangTielei talk “Sending Me Your IOUserClients: A Bypass to Immovable Ports” at @deepsec_cc was insanely good! I enjoyed it! Super clever new discovery. feels awesome to see other researchers referencing my past work.
Stoked for Jaron Bradley's soon to be released 2nd-book: "Threat Hunting macOS" 😍📚 (And was honored to write its forward). Jaron is an outstanding researcher, speaker, trainer, & friend, and this book will become an essential macOS security resource. linkedin.com/feed/update/ur…
The slides for my OffensiveCon talk "Finding and Exploiting 20-year-old bugs in Web Browsers" docs.google.com/presentation/d…
Thrilled to announce my new Project Zero blog post is LIVE! 🎉 I detail my knowledge-driven fuzzing process to find sandbox escape vulnerabilities in CoreAudio on MacOS. I'll talk about this and the exploitation process next week @offensive_con! googleprojectzero.blogspot.com/2025/05/breaki…
United States Trends
- 1. Baker 38.9K posts
- 2. 49ers 36.7K posts
- 3. Packers 33.7K posts
- 4. Bucs 12.3K posts
- 5. #BNBdip N/A
- 6. Flacco 12.7K posts
- 7. Fred Warner 13.1K posts
- 8. Cowboys 75.4K posts
- 9. Niners 5,898 posts
- 10. #TNABoundForGlory 9,657 posts
- 11. Cam Ward 3,091 posts
- 12. Zac Taylor 3,342 posts
- 13. #FTTB 4,562 posts
- 14. #GoPackGo 4,237 posts
- 15. Panthers 77K posts
- 16. Titans 24.9K posts
- 17. Egbuka 6,720 posts
- 18. Browns 67.9K posts
- 19. Mac Jones 6,109 posts
- 20. #Bengals 3,350 posts
You might like
-
 starlabs
starlabs
@starlabs_sg -
 RET2 Systems
RET2 Systems
@ret2systems -
 Bien 🇻🇳
Bien 🇻🇳
@bienpnn -
 Csaba Fitzl
Csaba Fitzl
@theevilbit -
 Jordy Zomer
Jordy Zomer
@pwningsystems -
 Dohyun Lee
Dohyun Lee
@l33d0hyun -
 kylebot
kylebot
@ky1ebot -
 sakura
sakura
@eternalsakura13 -
 acez
acez
@amatcama -
 Samuel Groß
Samuel Groß
@5aelo -
 Axel Souchet
Axel Souchet
@0vercl0k -
 Dataflow Security
Dataflow Security
@dfsec_com -
 Synacktiv
Synacktiv
@Synacktiv -
 Leonid Bezvershenko
Leonid Bezvershenko
@bzvr_ -
 KevinLu
KevinLu
@K3vinLuSec
Something went wrong.
Something went wrong.