SOCLabs
@DetectionLabs
We are building a SIEM learning and training platform for detection engineers.
How Detection Engineers Can Break Through Learning Barriers: SOCLabs Has the Answer by SOCLabs medium.com/p/how-detectio…
soclabs-detectionhub.medium.com
How Detection Engineers Can Break Through Learning Barriers: SOCLabs Has the Answer
You decide to learn SIEM detection rule writing. After finding a few online tutorials, it doesn’t seem that hard: understand log formats…
Practical Resources for Detection Engineers. || Starters 🕵🏻 and Pro || by @goodycyb medium.com/p/practical-re…
New challenge: Golden Ticket Detection 🎟 Think you can crack it? Give it a try! 🔗 soc-labs.top/en/detections/…
soc-labs.top
SOCLabs Detection Hub-Security Detection Challenge Platform
SOCLabs Detection Hub-Security Detection Challenge Platform
I did a great detection rule. soc-labs.top/en/detections/… via @DetectionLabs
soc-labs.top
SOCLabs Detection Hub-Security Detection Challenge Platform
SOCLabs Detection Hub-Security Detection Challenge Platform
Found an interesting detail during a DFIR case: On macOS, the last log does not record all SSH logins. When an attacker runs: ssh [email protected] "command" the login won’t show up in last. ⚠️ This means attackers can bypass the usual login traces.

😈 ChromeAlone - Transform Chromium browsers into a C2 Implant. A la Cobalt Strike or Meterpreter. @defcon talk and tool release by @praetorianlabs' Michael Weber. ChromeAlone contains a number of out of the box components, including: - A malicious Chrome extension that can…

A critical server’s login sources are usually limited to a few stable IPs ⚠️ When a new, unfamiliar IP suddenly shows up in the logs— it could be the first sign of an intrusion 🎯 New Challenge: 《IP Access Baseline Deviation Detection》 👀 Can you detect it right away?…

Two years ago I published a two part series on #MSGraph logs and how to use them for threat hunting. Now comes part 3 and the logs are finally available to the masses. #EntraID #KQL #Security cloudbrothers.info/en/detect-thre…
🎣 New Detection Challenge Live! We've just released our latest security detection challenge: "Double Extension Spoofing" Double extension spoofing is a classic phishing technique where attackers disguise executable files as regular documents. Can you spot this phishing trick?…

🚨 Just released: Browser Credential Theft Detection Challenge! 🕵️♂️🔐 It covers credential theft methods for multiple browsers 🛡️ Test if you can complete the challenge and validate your detection rules! 👇 Try it now:soc-labs.top/en/detections/… #ThreatDetection #BlueTeam #SIEM…
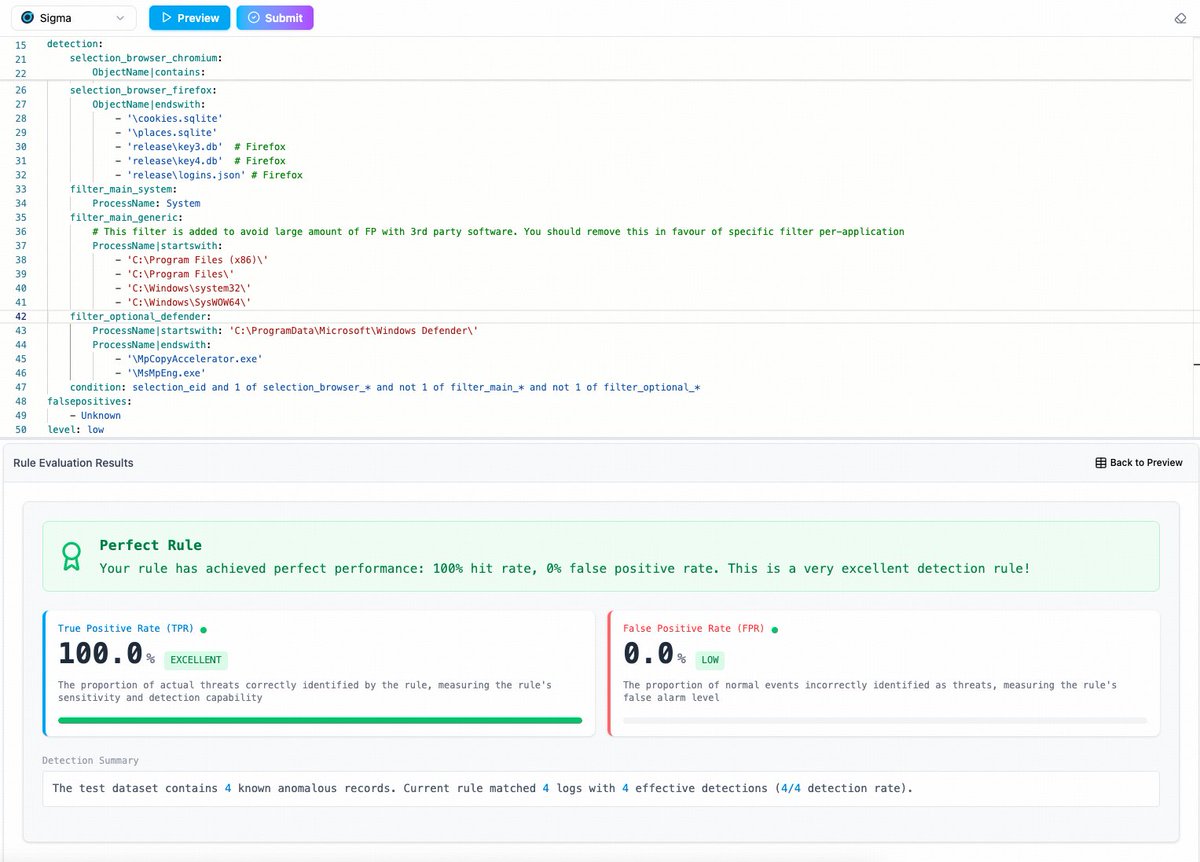
🚨 New Detection Challenge! 🚨 SOCLabs just launched a Password Spraying & Credential Access Detection challenge! Test your SIEM query skills and see if you can catch the attack. Ready to level up? Try it now on SOCLabs! 🔍💻 👉 soc-labs.top/en/detections/… #CyberSecurity #SIEM…
ClickFix variant targeting Mac users through X ads. Tries tricking users into "cleaning" their Macs by running a terminal command. Domain: hxxps://top-fixer[.]com/?p=141 Distributes install[.]sh file: virustotal.com/gui/file/525be…
![pcrisk's tweet image. ClickFix variant targeting Mac users through X ads. Tries tricking users into "cleaning" their Macs by running a terminal command. Domain: hxxps://top-fixer[.]com/?p=141 Distributes install[.]sh file: virustotal.com/gui/file/525be…](https://pbs.twimg.com/media/GvZYtBmWsAIzrer.jpg)
![pcrisk's tweet image. ClickFix variant targeting Mac users through X ads. Tries tricking users into "cleaning" their Macs by running a terminal command. Domain: hxxps://top-fixer[.]com/?p=141 Distributes install[.]sh file: virustotal.com/gui/file/525be…](https://pbs.twimg.com/media/GvZYuh8W4AAheWk.jpg)
Thanks for the shoutout to the Zen of Security Rules br0k3nlab.com/resources/zen-… Cool initiative to see this applied to threat hunting as well 🤙 Thanks for sharing @_w0rk3r
br0k3nlab.com
The Zen of Security Rules
Abstract The Zen of python does a perfect job succinctly capturing guiding principles for developing via 19 aphorisms. This is the zen of writing security rules, for fostering high-quality, high-ef...
THRUNTING isn’t just a buzzword. It’s a mindset. 🐑 Inspired by Tim Peters’ 19 aphorisms for Python, @THOR_Collective Dispatch introduces "The Zen of Thrunting." dispatch.thorcollective.com/p/the-zen-of-t… Stay curious. Happy thrunting.
An increased visibility into threads' call stacks helps with more reliable malware detection. The approach is based on ETW telemetry and module's Export Directory data for information enrichment. A post by John Uhlmann of @elasticseclabs. Great read! #redteam #blueteam #maldev…
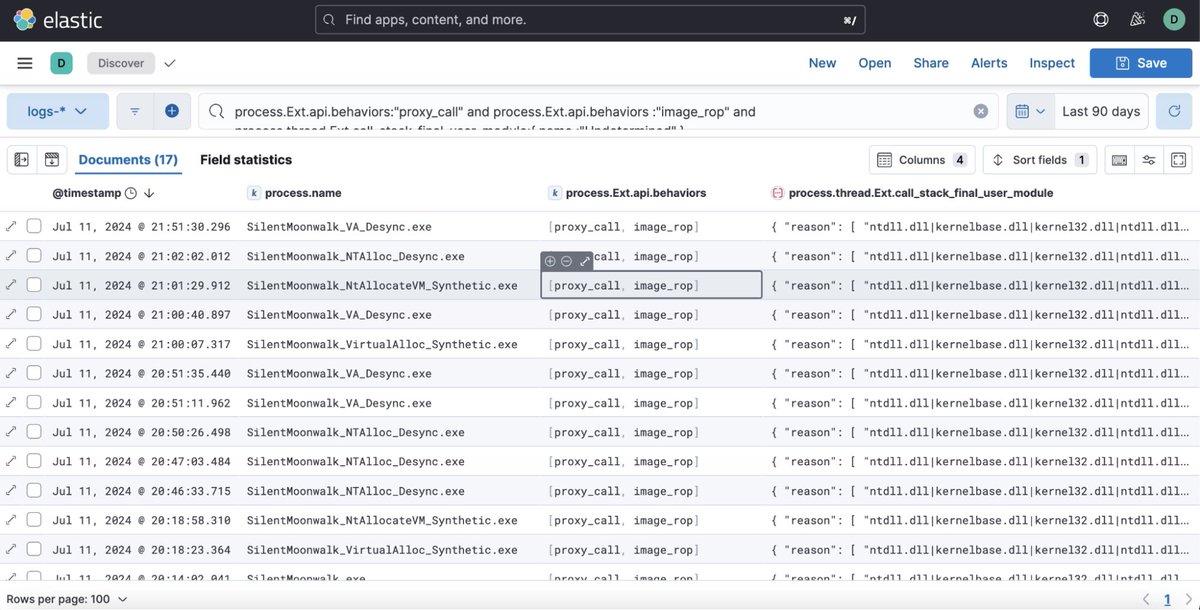
Used Claude to generate a Splunk query to hunt for browser exploits and potential @mrd0x #FileFix #clickfix like behaviors in Sysmon Process Create events. Ran it in a fortune 50 environment and for a 7 day period only had 200~ events out of 200 Million pastebin.com/PJGZuArj
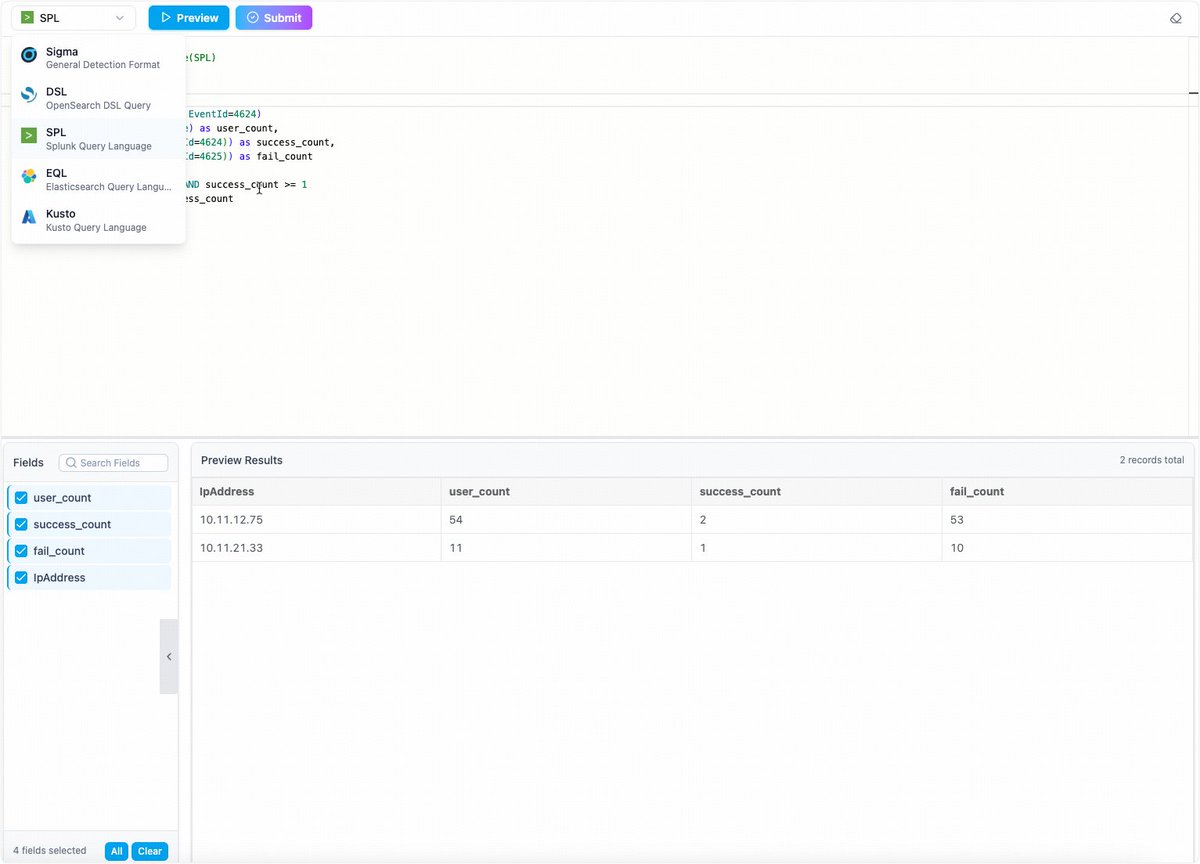
Inspired by this new FileFix technique from @mrd0x , we've launched a hands-on detection challenge! Write and test SIEM rules Splunk, Elastic, KQL, Sigma, OpenSearch in your browser. Try it now: 👉 https:soc-labs.top/en/detections/… #SIEM #DetectionEngineering #CyberSecurity #FileFix
soc-labs.top
SOCLabs Detection Hub-Security Detection Challenge Platform
SOCLabs Detection Hub-Security Detection Challenge Platform
And us
How to become a decent detection engineer: 1. Download Aurora 2. Run whatever your EDR misses through Aurora 3. Deploy the Sigma rules from Aurora to your SIEM
Did you know that you can kerberoast without any valid credentials? All you need is an account that is ASREProastable. This allows you to request service tickets for any account with a set SPN🔥 NetExec now has a native implementation of this technique, thanks to Azox

United States Trends
- 1. Blue Origin 8,155 posts
- 2. Megyn Kelly 30.5K posts
- 3. New Glenn 9,014 posts
- 4. Vine 34.1K posts
- 5. Senator Fetterman 18.7K posts
- 6. Brainiac 5,769 posts
- 7. CarPlay 4,399 posts
- 8. #NXXT_JPMorgan N/A
- 9. World Cup 102K posts
- 10. Portugal 63.2K posts
- 11. Matt Gaetz 14.4K posts
- 12. GeForce Season 1,072 posts
- 13. Padres 28.8K posts
- 14. Eric Swalwell 26.7K posts
- 15. Man of Tomorrow 6,256 posts
- 16. Black Mirror 5,260 posts
- 17. Katie Couric 9,844 posts
- 18. Grade 1 26.3K posts
- 19. Apple TV 8,546 posts
- 20. Judge 130K posts
Something went wrong.
Something went wrong.