おすすめツイート
Introductory Windows Stack Overflow Exploitation x.com/i/broadcasts/1…
CTRAPS: CTAP Impersonation and API Confusion Attacks on FIDO2 x.com/i/broadcasts/1…
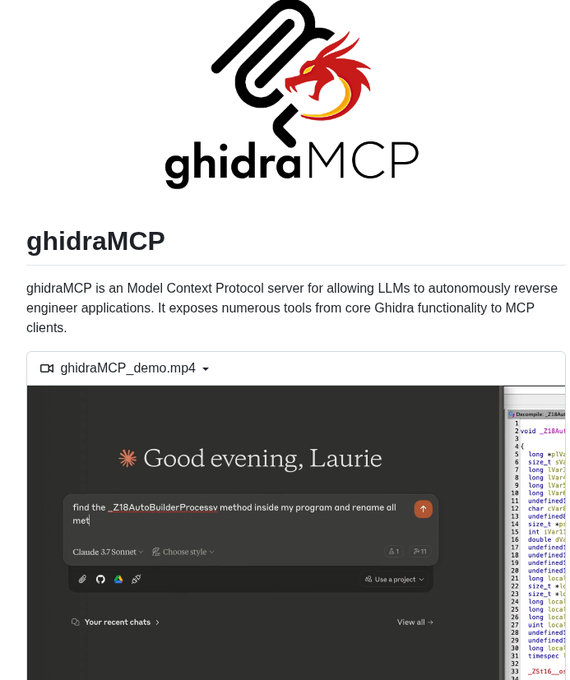
Let's LLMs automate reverse engineering in Ghidra : - github.com/LaurieWired/Gh… #infosec #cybersec #bugbountytips
A special shoutout to all the SMEs who helped us with specific parts of the @sansforensics FOR589 Cybercrime Intelligence course. Especially @SttyK @Jon__DiMaggio @ASG_Sc0rpi0n @DE7AULTsec and @afx_IDE. Thank you so much for all of your help 👏 FOR589: sans.org/cyber-security…

Cybercrime Squad detectives have charged a woman for a series of alleged cyber hacks on Western Sydney University under Strike Force Docker. MORE INFORMATION ➡ police.nsw.gov.au/news/article?i…
Breaking into a Cyber Security Career in 2025 x.com/i/broadcasts/1…
🚨 New on LABS: Malware-as-a-Smart-Contract – Part 1 🚨 Attackers abusing BSC smart contracts & compromised WordPress to serve payloads via ClickFix. Malware in the browser, C2 via blockchain - wild stuff. Full breakdown by @LiliLin41874723 👇 🔗labs.jumpsec.com/malware-as-a-s…
countdown to youtube.com/watch?v=8tGsKb… @Steph3nSims !
youtube.com
YouTube
An OpSec look at the DarkNet/Dark Web Marketplace DNM Bible Part 2
New blog: The Slow Collapse of Critical Thinking in OSINT due to AI "OSINT used to be a thinking game. Now it’s becoming a trusting game and that should terrify you." #OSINT #OSINT4good #AI Read the blog here: dutchosintguy.com/post/the-slow-…

Great new blog on LockBit 4.0 analysis! 👇
Reviving my blog with a complete analysis of the latest #LockBit #ransomware v4.0 Green! 🤠 chuongdong.com/reverse%20engi… h/t to @fwosar & @demonslay335 for all the crypto helps! Huge thanks to @BushidoToken & @CuratedIntel for the threat intelligence insight too! 🙏

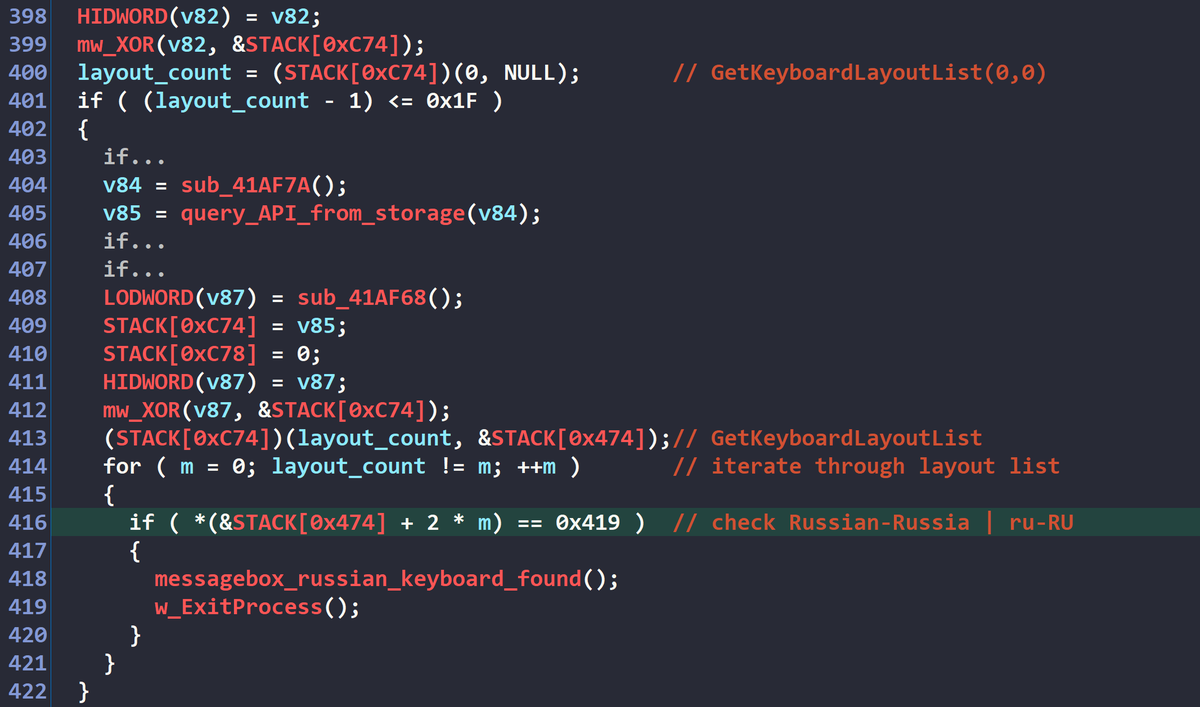

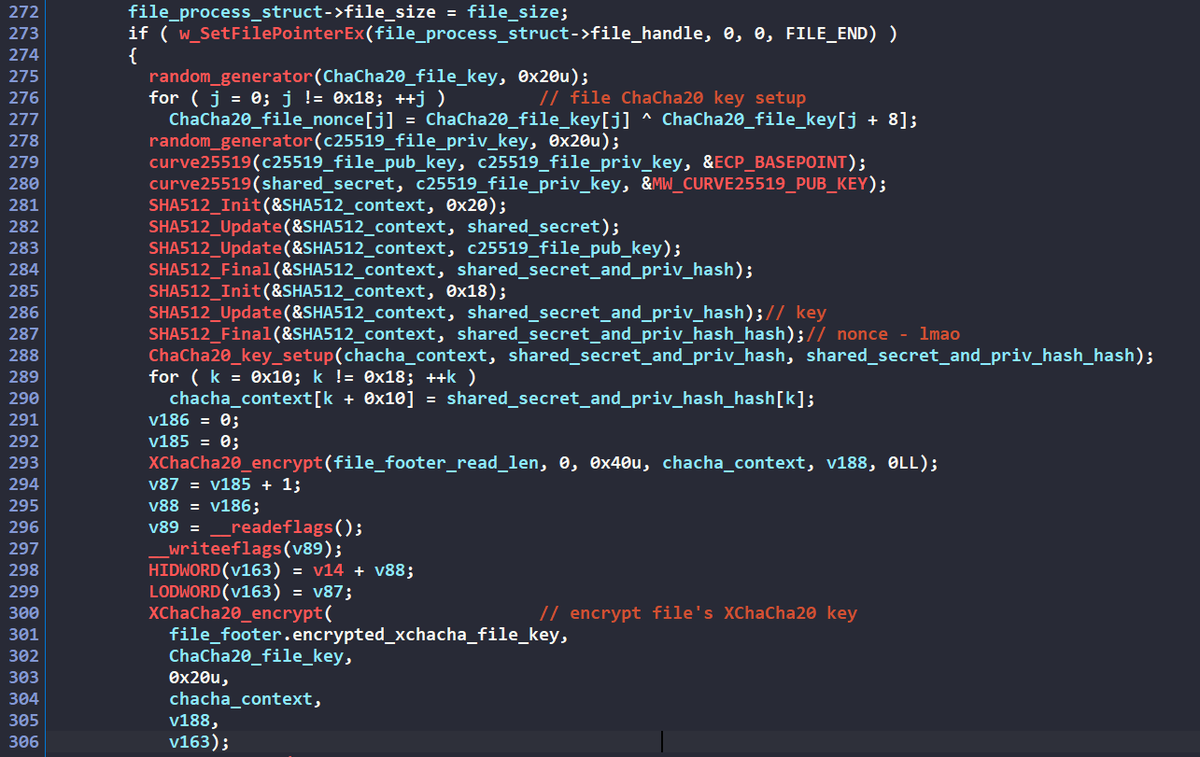
Anyone else realised that the Russian SVR appears to be simply going back through old @BHinfoSecurity blogs and testing to see if these known techniques still work 😅 First Rogue RDP and now Device Code Phishing 1. blackhillsinfosec.com/rogue-rdp-revi… 2. blackhillsinfosec.com/dynamic-device…
If you are watching the Off By One Security streams via X, please consider subscribing to the channel on YouTube where you can interact during the stream and watch the video post-stream. youtube.com/@OffByOneSecur…
Join me on Friday, February 14th on the @offby1security stream with the amazing @33y0re (Connor McGarr) for a look at Windows Kernel Mode Shadow Stacks and the Secure Kernel! youtube.com/watch?v=T7qxs-…

UpGuard , Using Exposed Ollama APIs To Find DeepSeek Models -- upguard.com/blog/deepseek-…
Using an AI Chatbot to Help Solve a CTF Binary Challenge! x.com/i/broadcasts/1…
Join me this Friday (7-Feb) at 11AM on the @offby1security stream for a session on using an AI Chatbot to help with a CTF challenge on binary exploitation. We will also be giving away 3 licenses to @mrgretzky's Evilginx Mastery course! youtube.com/watch?v=SMmvJo…

AI Cyber Threat Intelligence Roundup: January 2025 blogs.cisco.com/security/ai-cy… via @ciscosecure
Today, I'm releasing the first version of a small web 🚀: rosti.bin.re It provides IOCs and YARA rules collected semi-automatically from public blog posts and reports of almost 200 cybersecurity sites. I hope it proves useful to some of you ... 🙏✨ #ThreatIntel
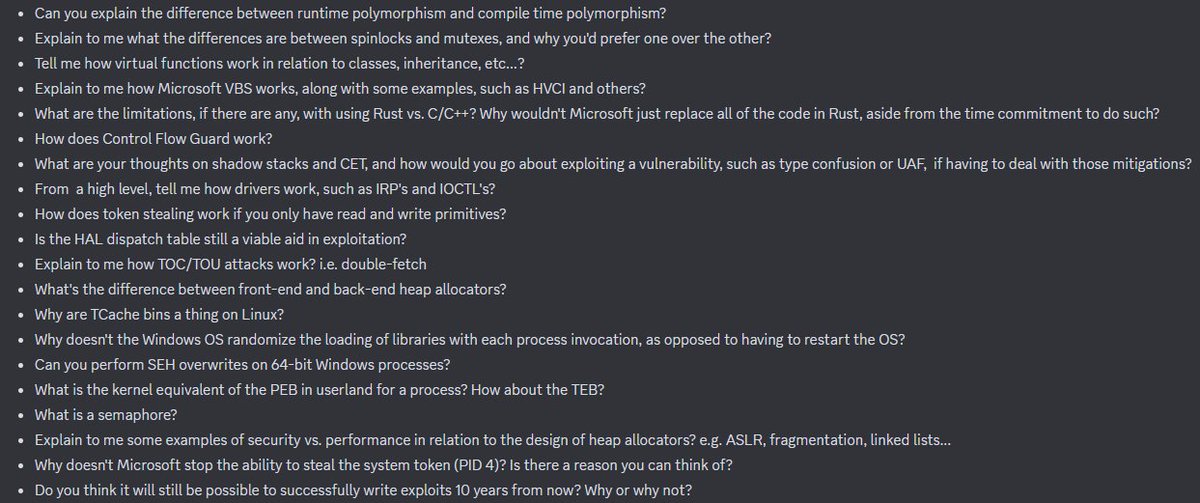
On the Off By One Security Discord server, I was asked to post some questions I'd ask a potential candidate applying for a vulnerability researcher position. I'm sure some will not agree with the questions, but they work for me! Feel free to use them. discord.gg/offbyonesecuri…
Mind-blown by this GitHub hack! 🤯 Simply change .com to .gg in any GitHub URL and instantly chat with the entire repo using AI. No more digging - just ask questions and get instant answers! Big thank you to @nisten who develops it and @thursdai_pod where it was mentioned. 👏
United States トレンド
- 1. Ravens 55.4K posts
- 2. Ravens 55.4K posts
- 3. Lamar 44.2K posts
- 4. Joe Burrow 19.2K posts
- 5. Zay Flowers 3,965 posts
- 6. #WhoDey 3,446 posts
- 7. Cowboys 90.4K posts
- 8. #heatedrivalry 6,866 posts
- 9. Derrick Henry 4,331 posts
- 10. Zac Taylor 2,579 posts
- 11. Perine 1,542 posts
- 12. Harbaugh 2,948 posts
- 13. AFC North 2,220 posts
- 14. ilya 10.1K posts
- 15. #CINvsBAL 2,626 posts
- 16. Sarah Beckstrom 199K posts
- 17. Mahomes 33.3K posts
- 18. Cam Boozer 2,109 posts
- 19. Jason Garrett N/A
- 20. Tanner Hudson 1,262 posts
おすすめツイート
-
 LetsDefend
LetsDefend
@LetsDefendIO -
 Google VRP (Google Bug Hunters)
Google VRP (Google Bug Hunters)
@GoogleVRP -
 Blue Team News
Blue Team News
@blueteamsec1 -
 PentesterLab
PentesterLab
@PentesterLab -
 inversecos
inversecos
@inversecos -
 Objective-See Foundation
Objective-See Foundation
@objective_see -
 Volexity
Volexity
@Volexity -
 Ali Hadi | B!n@ry
Ali Hadi | B!n@ry
@binaryz0ne -
 RedDrip Team
RedDrip Team
@RedDrip7 -
 🇷🇴 cristi
🇷🇴 cristi
@CristiVlad25 -
 Professor Messer
Professor Messer
@ProfessorMesser -
 Nuclei by ProjectDiscovery
Nuclei by ProjectDiscovery
@pdnuclei -
 Seongsu Park
Seongsu Park
@unpacker -
 AGID
AGID
@AgidGov -
 chompie
chompie
@chompie1337
Something went wrong.
Something went wrong.