내가 좋아할 만한 콘텐츠
Microsoft is Offering FREE Azure 2025 Certification Courses! No Fee, Completely Free These 20 Courses Includes Video Tutorials, Hand's on Labs and Notes. Don't miss these courses if you want to make your career in 2025:
Powerful technique to quickly improve how you speak
I got asked to put a quick demo together after a recent engagement to show how easy it is to abuse disconnected RDP sessions from local admin. Thought I’d share in case useful secureyourit.co.uk/wp/2024/11/07/…
Curious about Cobalt Strike's #UDRL capabilities? Get a walkthrough on how to easily develop custom loaders. cobaltstrike.com/blog/revisitin…
serviceui.exe - a useful lolbin I came across on a pentest a while back that I thought I'd share. secureyourit.co.uk/wp/2024/11/02/… @Oddvarmoe #lolbas #lolbin
DonPAPI users I have pushed quite a few things lately! Hopefully you'll like it and here is a recap (1/x)
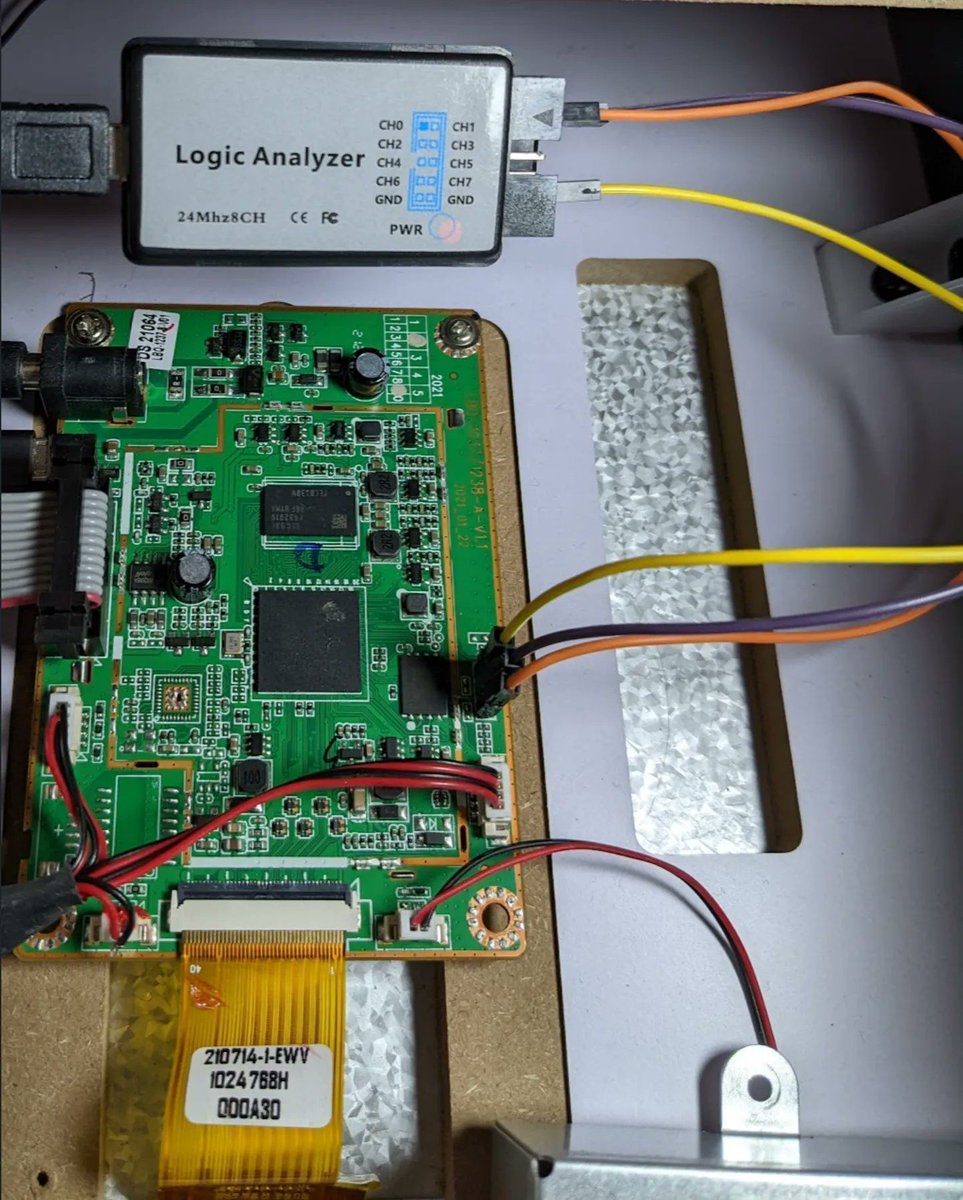
Intro for beginners to embedded devices reverse engineering Ghidra setup: voidstarsec.com/blog/ghidra-de… Tools: voidstarsec.com/blog/intro-to-… Firmware extraction: voidstarsec.com/blog/uart-uboo… Credits @voidstarsec #reverseengineering #infosec
Windows Internals Crash Course (62 minutes from the creator of x64dbg) - because you’ll find Windows in cars, robots, and manufacturing IoT. 😎💻🛠 Course: youtube.com/watch?v=I_nJlt… Slides: mrexodia.github.io/files/wicc-202… Materials: mrexodia.github.io/files/wicc-202…
Microsoft Copilot: From Prompt Injection to Exfiltration of Personal Information · Embrace The Red embracethered.com/blog/posts/202…
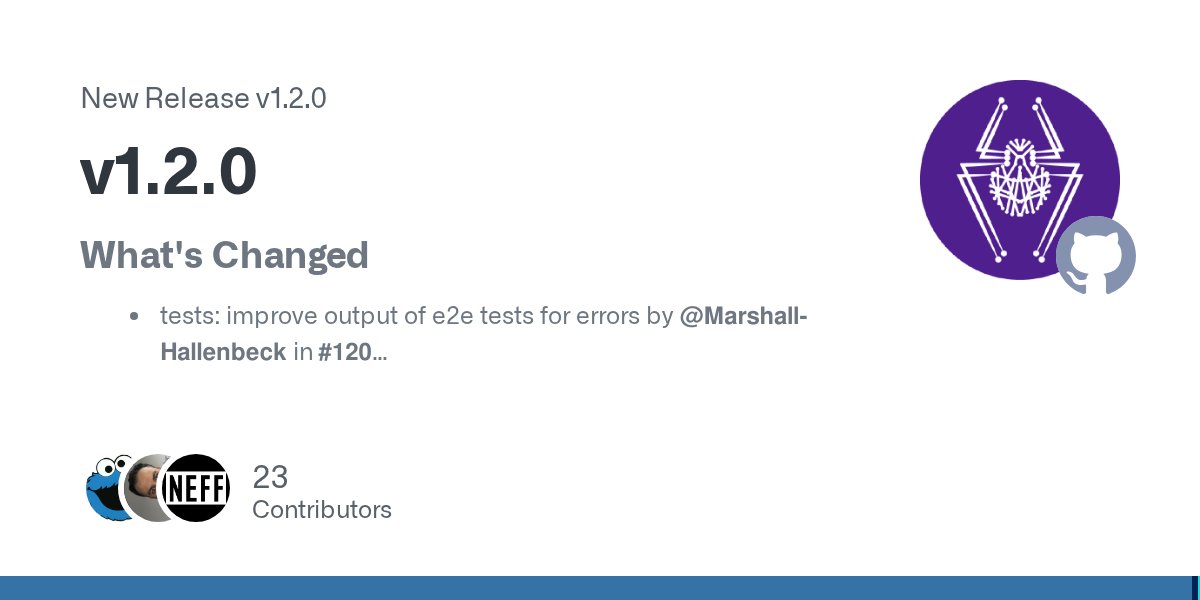
🚨 #NetExec v1.2.0 (codename "ItsAlwaysDNS") has been OFFICIALLY released. There are too many amazing features, modules, and bugfixes to talk about all of them (just look at the notes 🤯github.com/Pennyw0rth/Net…), but the codename is because you can now specify a DNS server!
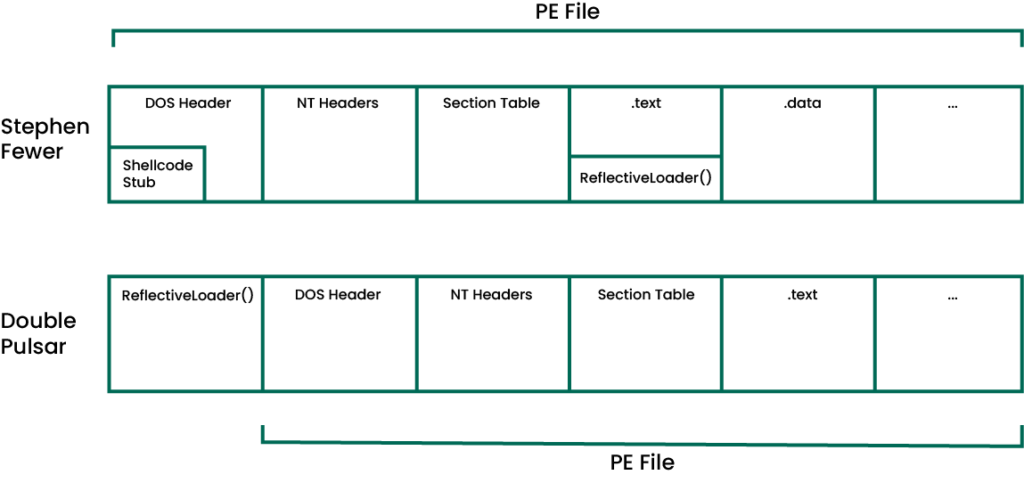
My new article revisits classic technique Reflective Loading, and explains my tool InflativeLoading. winslow1984.com/books/malware/… Thank @0xBoku @MalDevAcademy @stephenfewer @hasherezade and all other authors(and their articles/tools/projects) for the inspiration and help
This is a great blog by @Tw1sm Tldr; Compromise workstations by coercing machine account HTTP authentications and relaying them to LDAP to set shadow credentials on the computer object. Then extract the NT hash, create a silver ticket, move laterally 🔥 fortalicesolutions.com/posts/shadow-c…
Buffer Overflow in TP-Link Tapo C100 Home Security Camera reddit.com/r/netsec/comme…
Don’t rely on motivation.
I've used Evilginx plenty of times for engagements and unfortunatly have seen it abused in the wild. Decided to make a post on how to protect against modern phishing attacks using different methods - inspired by @merill bleekseeks.com/blog/how-to-pr…
Today, I have a question. A pressing question. For some Western feminists. How can you remain silent, when women and girls are raped, tortured, their bodies carried around naked and spat on by bearded men shouting Allah Akbar? Then you can never call yourself a feminist again.…
🚨 BBC forced to apologise for getting caught reporting shocking fake news Pass it on for the world to see
United States 트렌드
- 1. Lakers 83K posts
- 2. Luka 63.9K posts
- 3. Ayton 13.2K posts
- 4. Marcus Smart 7,763 posts
- 5. Warriors 90.4K posts
- 6. Curry 37.6K posts
- 7. Shai 32.4K posts
- 8. Rockets 57.7K posts
- 9. #DWTS 46.7K posts
- 10. Sengun 24.2K posts
- 11. Double OT 6,196 posts
- 12. Draymond 7,480 posts
- 13. Reaves 8,459 posts
- 14. #DubNation 12.3K posts
- 15. Jimmy Butler 7,486 posts
- 16. #LakeShow 6,383 posts
- 17. Reed Sheppard 6,276 posts
- 18. Kuminga 8,736 posts
- 19. Gabe Vincent 1,888 posts
- 20. Vando 2,597 posts
내가 좋아할 만한 콘텐츠
-
 Will Schroeder
Will Schroeder
@harmj0y -
 Matt Hand
Matt Hand
@matterpreter -
 kmkz
kmkz
@kmkz_security -
 Steven
Steven
@0xthirteen -
 Marcello
Marcello
@byt3bl33d3r -
 Tim MalcomVetter
Tim MalcomVetter
@malcomvetter -
 Andrea P
Andrea P
@decoder_it -
 Jason Lang
Jason Lang
@curi0usJack -
 @[email protected]
@[email protected]
@christruncer -
 Cn33liz
Cn33liz
@Cneelis -
 Dwight Hohnstein
Dwight Hohnstein
@djhohnstein -
 Dominic Chell 👻
Dominic Chell 👻
@domchell -
 bohops
bohops
@bohops -
 Spiros Fraganastasis
Spiros Fraganastasis
@m3g9tr0n -
 Oddvar Moe
Oddvar Moe
@Oddvarmoe
Something went wrong.
Something went wrong.