ret2src
@ret2src
Breaker of Stuff | Injector of 0x41 | Discoverer of Dumb Things | Creator of Glitches. Dropping shells since 0x7DC.
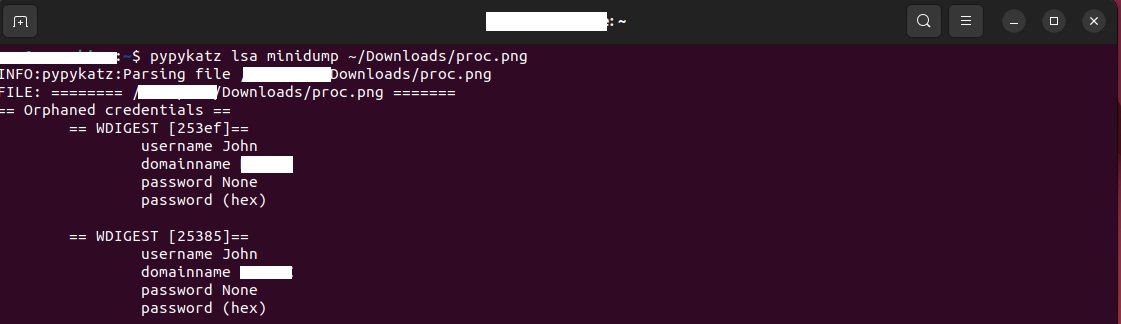
Another way is to look for snapshots of a target VM and get the memory .vmem file. After converting the memory dump it should open in WinDbg and extract some secrets with Mimikatz extension.
Welcome to the EU, where the lunatics in Brussels take everything from us. While it was narrowly prevented this time, the next act of pure fascism disguised as safety will come. 1984 in all its glory.
EU's Chat Control proposal is to effectively ban end to end encryption since it demands that governments can read all msgs. I find this to be not only insane, but feasibly impossible. Breaking the whole internet. Yet it got voted on last week, and just narrowly stopped. Whew!

My colleague Mathias and I just finished our talk about "Relaying Unprivileged Users to RCE" at @MCTTP_Con. You can find our slides at github.com/svaredteam/tal…

Active Directory Pentest Mindmap v2025.03 Full view and updated map : orange-cyberdefense.github.io/ocd-mindmaps/i…

I've been researching the Microsoft cloud for almost 7 years now. A few months ago that research resulted in the most impactful vulnerability I will probably ever find: a token validation flaw allowing me to get Global Admin in any Entra ID tenant. Blog: dirkjanm.io/obtaining-glob…
Better watch out for the TCP, I’ve seen it being abused by those pesky hackers over and over again!
Hackers reportedly used something called "TruffleHog" during their attack. They also used "child_process", and something called HTTP, something called TLS, and something called TCP. Please be on the lookout for any of these hacking tools being used in your environment.
no matter how hard you cyber, there will ~ALWAYS~ be another registry persistence you've never heard of.

FortiGuard Labs highlights an SEO-poisoning campaign that targets Chinese-speaking users. Attackers manipulate search rankings with SEO plugins and lookalike domains, delivering malware families such as Hiddengh0st and Winos. fortinet.com/blog/threat-re…

Here's an initial release of a LDAP browser written in python with a nice GUI and some integrations with #BloodHound github.com/ZephrFish/pyLD…
Made a thing, mucking about with python and a LDAP browser concept to ingest straight into BloodHound, simple LDAP browser using PyQt as a GUI and neo4j-driver to ingest into BH. Coming Soon #itstimetobrowse


#redteam Now, you can dump the #Windows password from the LSASS process with help from the past: WerFaultSecure.exe Github: 2x7EQ13/WSASS Experimental version: Windows 11 24H2 #Blueteam


the jump scare of the morning award goes to @J0R1AN (it even adapts to different native calculators using UA-based OS detection :))
Best Citrix Breakout ever. You can only download .ica files that provide access to certain local applications but breakout out of these applications is not possible? Just modify the .ica file before starting it and remove The InitialProgram= value -> Full Citrix Session! 🤓

The second book in my “being a professional red teamer requires more than just having kick ass technical tradecraft” series is: “Never Split the Difference” by Chris Voss. The reason I picked this book is because red teams rarely control the environments they are operating in.…

The first book in my “being a professional red teamer requires more than just having kick ass technical tradecraft” series is: “Thanks for the Feedback” by Douglas Stone & Sheila Heen. The reason I recommend this book is simple: red teamers spend _a lot_ of time delivering…

I stopped reporting Internet-exposed Citrix Netscaler instances as a vulnerability because dozens of customers argued with me that “it is intended to be exposed directly to the Internet”. I was right all along and will start reporting it again starting today.
“Once you start a Windows machine, it will first attempt to obtain network configuration via DHCPv6 […] due to Windows’ preference for IPv6. […] even if your network does not actively use IPv6.” This makes poisoning using mitm6 especially dangerous: resecurity.com/blog/article/m…
This will be fun
We’ve developed Claude for Chrome, where Claude works directly in your browser and takes actions on your behalf. We’re releasing it at first as a research preview to 1,000 users, so we can gather real-world insights on how it’s used.
Feeling too familiar with using Sysmon? You can use it for #redteam purposes by having it overwrite the #antimalware executable. Just like I did with #windowsdefender



every programmer must listen to this 👏🏼
United States Trends
- 1. Grammy 360K posts
- 2. #FliffCashFriday N/A
- 3. Dizzy 9,921 posts
- 4. Clipse 21.3K posts
- 5. #NXXT 1,090 posts
- 6. Kendrick 62.7K posts
- 7. #GOPHealthCareShutdown 8,278 posts
- 8. James Watson 5,103 posts
- 9. Orban 42K posts
- 10. #FursuitFriday 12.2K posts
- 11. addison rae 24.8K posts
- 12. Darryl Strawberry N/A
- 13. Leon Thomas 20.9K posts
- 14. Thune 71K posts
- 15. Carmen 47.7K posts
- 16. olivia dean 15.9K posts
- 17. Katseye 120K posts
- 18. Chase 87.6K posts
- 19. Alfredo 2 1,065 posts
- 20. AOTY 22.3K posts
Something went wrong.
Something went wrong.