Roman
@securecodeninja
a web builder & defender 🕷️ proud to be pinoy 🇵🇭 appsec quarterback 🛡️
Talvez você curta
It's been fun writing @SemgrepRegistry rules for #AspNetCore and #csharp, you should try creating one too! Wanna learn how to fix these @semgrep findings? Check out my book! amazon.com/dp/180107156X
We just shipped automated security reviews in Claude Code. Catch vulnerabilities before they ship with two new features: - /security-review slash command for ad-hoc security reviews - GitHub Actions integration for automatic reviews on every PR
Wasting time fuzzing hardened code without hitting new vulnerabilities. Legacy black-box fuzzers stall at validation checks, missing deeper bugs. In Chapter 8 of my new book From Day Zero to Zero Day, you'll explore the advanced techniques behind coverage-guided fuzzing using…

McDonald's uses an AI bot called "Olivia" for hiring. A pair of hackers found they could access every conversation job applicants had with it—including all the personal info they shared—by exploiting security flaws as basic as using the password "123456". wired.com/story/mcdonald…
Oktajacking - Using Okta to keylog for initial access or as a sneaky form of SAMLjacking for lateral movement from a compromised SaaS app. Massive shoutout to @_xpn_ as I used his great research for this, I just applied it to different kill chain phases. pushsecurity.com/blog/oktajacki…
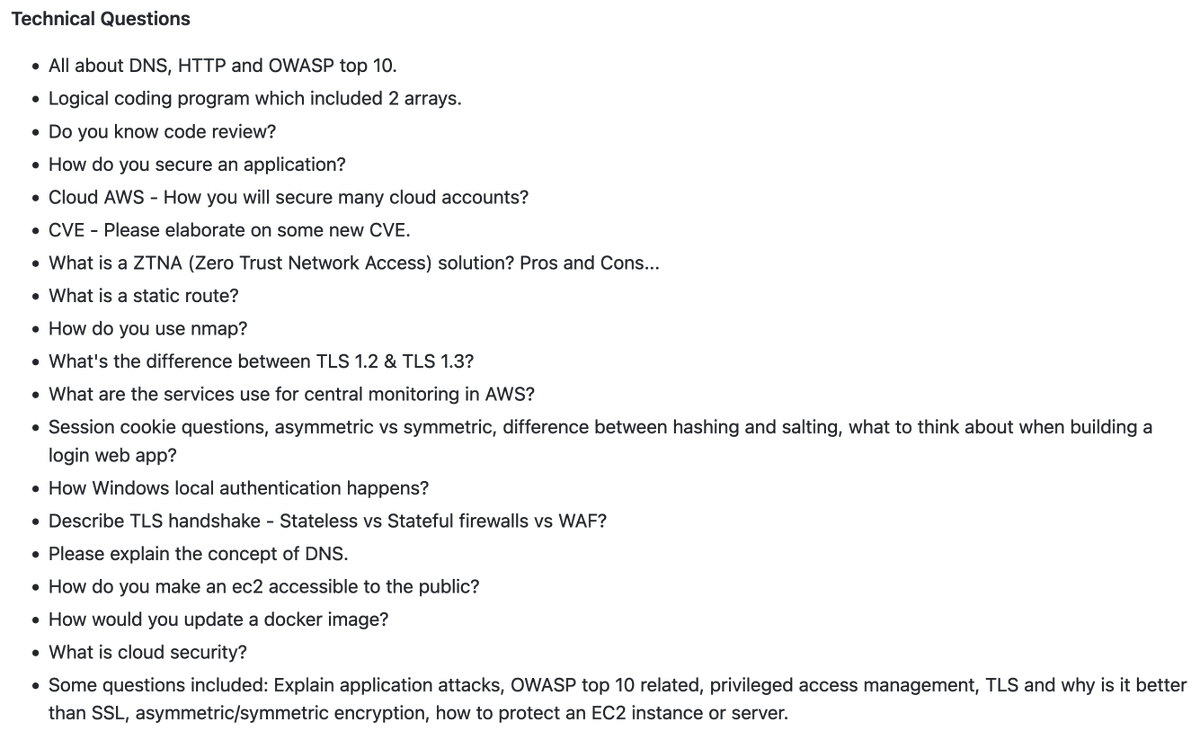
👔 Security Architect & Principal Security Engineer Interview Questions A consolidated list of questions pulled from Glassdoor From: Netflix, Morgan Stanley, Wiz, & more * Technical * Behavioral and Influential * Frameworks/Design/Threat Modeling github.com/tadwhitaker/Se…
Just because you're using Okta, doesn't mean you're using SSO. I wrote a blog post covering: • What is SWA and what are the risks? • Extracting SWA passwords • Bypassing password reveal restrictions • Detection and response for Okta account breaches pushsecurity.com/blog/okta-swa/…
🛠️ Building a free Burp Collaborator with Cloudflare Workers How to use Cloudflare Workers to receive out-of-band connections during your web app testing (e.g. track when blind XSS triggers) and pipe the results to Discord blog.gbrls.space/blog/building-…

After the success of our security research, we decided to invest a $120k bounty and share our story and tools with you. Now, we are releasing an Automated Scans feature on VIDOC, allowing you to easily automate your #bugbounty hunting on a large scale! blog.vidocsecurity.com/blog/2022-summ…
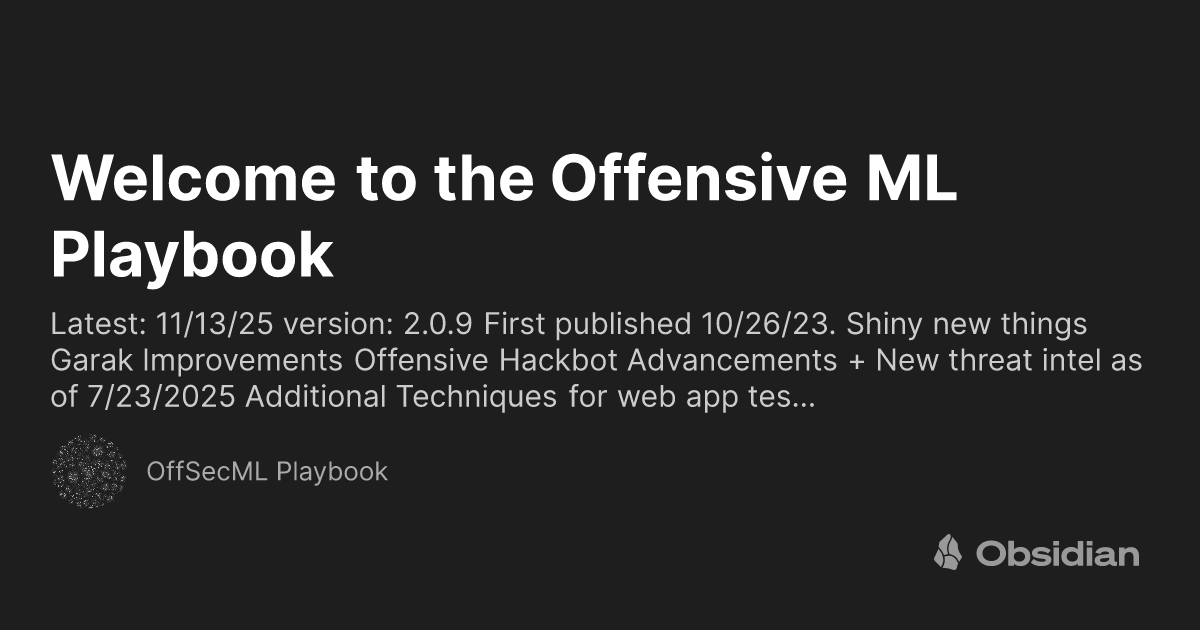
😈 The Offensive ML Playbook A database of offensive ML TTPs covering: * Supply chain attacks * Offensive ML techniques * Adversarial ML Examples: * Poisoning an LLM’s ground truths * How to put malware in a model and distribute it By @WHITEHACKSEC wiki.offsecml.com/Welcome+to+the…
Just discovered a full account takeover on Grammarly.com, Vidio.com and more using a new OAuth attack technique. This is the last part of the OAuth trilogy; in total, we could take over 1+ BILLION accounts! salt.security/blog/oh-auth-a… #OAuth #hacking
What are HAR files? A HAR file is a recording of your current session & includes all web traffic including secrets & tokens. Admins usually share these files with customer support when troubleshooting issues. Here's a thread on how you can handle .har files safely. 🧵⬇️
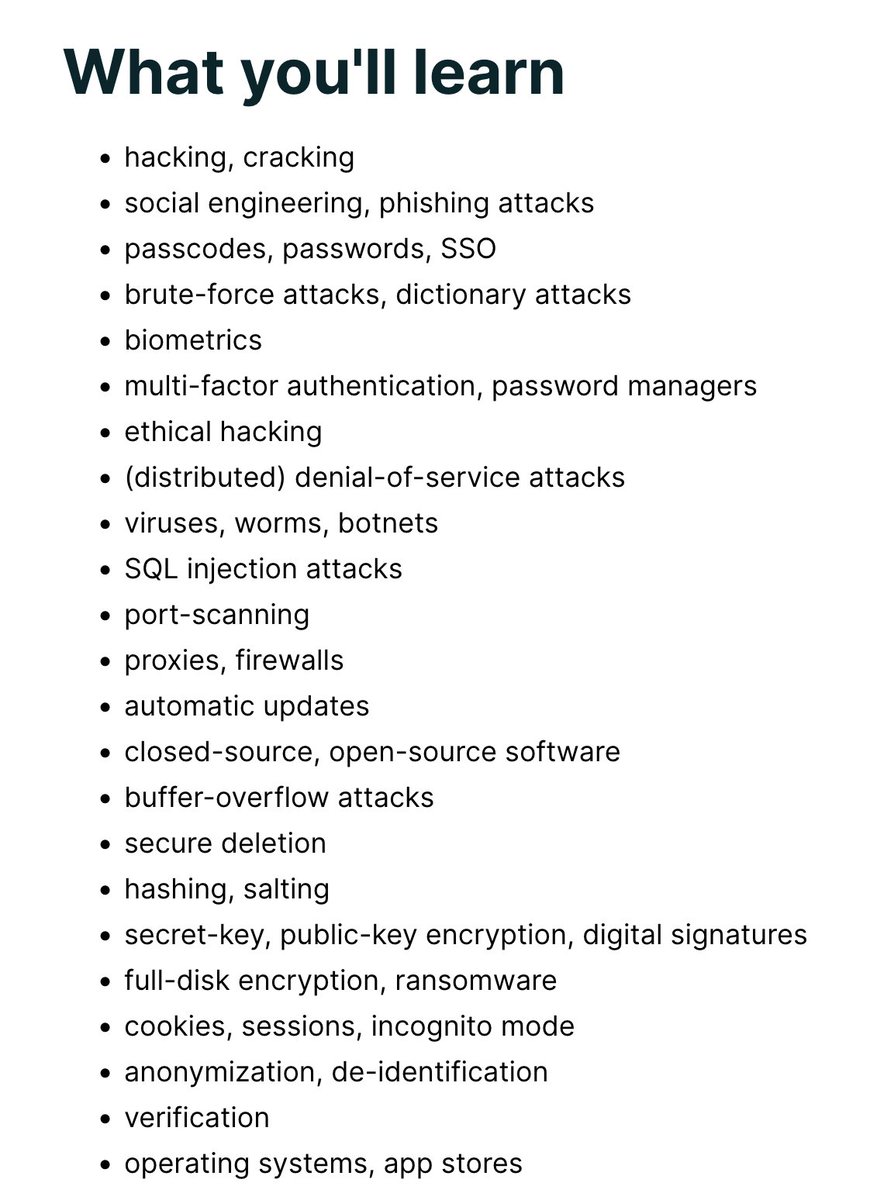
🎓 Free Cybersecurity Course from Harvard An introduction to #cybersecurity for technical and non-technical audiences Self-paced, 2-6 hours/week over 5 weeks edx.org/learn/cybersec…
Chalk is now officially open source. Total visibility of your software engineering lifecycle. Designed for platform and security teams. eu1.hubs.ly/H05xD2d0
𝗟𝗲𝗮𝗿𝗻 𝗝𝗪𝗧 𝗹𝗶𝗸𝗲 𝘆𝗼𝘂'𝗹𝗹 𝗻𝗲𝘃𝗲𝗿 𝗳𝗼𝗿𝗴𝗲𝘁. 🧵

Now Generally Available: GitHub Advanced Security for Azure DevOps is ready for you to use devblogs.microsoft.com/devops/now-gen…
🗒️ Source Code Management Platform Configuration Best Practices Guide by @OpenSSF for securing SCM platforms * Harden CI/CD pipelines against supply chain attacks * Branch protection policies and access controls/permissions * Server-level policies best.openssf.org/SCM-BestPracti…

🤖 promptfoo A tool for testing your prompts. Evaluate and compare LLM outputs, catch regressions, and improve prompt quality. github.com/promptfoo/prom…
Just stumbled upon some pretty dope talks by @naugtur ❤️ 📜 "Eval all the strings! Hardened JavaScript" youtube.com/watch?v=Qjeh7Q… and his free workshop he did @defcon on: 📜 "Defensive coding and hardened JavaScript" naugtur.pl/pres3/lava/wor… github.com/naugtur/js-tra…

youtube.com
YouTube
Eval all the strings! Hardened JavaScript - Zbyszek Tenerowicz |...
🧠 Web AppSec Interview Questions A tough set of questions by @0xTib3rius covering: * XSS * CSRF * SQL injection * Web cache deception and poisoning * Session fixation * HTTP request smuggling * DOM clobbering * HTTP parameter pollution + much more tib3rius.com/interview-ques…
🌐 Wapalyzer A community fork of the deleted Wappalyzer project Can detect & identify the technologies used to build any website Supports patterns, regular expressions and coding finterprints By @Lissy_Sykes #bugbountytips github.com/Lissy93/wapaly…
United States Tendências
- 1. #FanCashDropPromotion N/A
- 2. Good Friday 54.5K posts
- 3. LINGORM DIOR AT MACAU 482K posts
- 4. #FridayVibes 4,185 posts
- 5. Happy Friyay 1,144 posts
- 6. RED Friday 2,988 posts
- 7. #ElMundoConVenezuela 3,279 posts
- 8. #TheWorldWithVenezuela 3,286 posts
- 9. #FridayFeeling 2,260 posts
- 10. Josh Allen 45.7K posts
- 11. Ja Rule N/A
- 12. Sedition 347K posts
- 13. Kenyon N/A
- 14. Dubai Air Show 42.6K posts
- 15. Haier EST SUPHA 154K posts
- 16. Parisian 2,019 posts
- 17. Tejas 75.8K posts
- 18. Commander in Chief 89.4K posts
- 19. Niger 65.4K posts
- 20. Patriot Act 3,020 posts
Talvez você curta
Something went wrong.
Something went wrong.