
VCSLab
@vcslab
This is the Twitter channel of VCSLab - the research team of Viettel Cyber Security
You might like
We have another collision. Team Viettel used two bugs to exploit the Lexmark CX532adwe. While their heap based buffer over was unique, the other bug has been seen earlier in the contest. They still earn $7,500 and 1.5 Master of Pwn points. #Pwn2Own


Confirmed! namnp of Viettel Cyber Security used a crypto bypass and a heap overflow to exploit the Phillips Hue Bridge. They earn $20,000 and 4 Master of Pwn points, which catapults them in the Top 5. It also puts us over $1,000,000 for the contest! #Pwn2Own


Another confirmation! Dinh Ho Anh Khoa (@_l0gg) and Phan Vinh Khang (@pivik_) of Viettel Cyber Security used a unique command injection and two bugs that collided with previous bugs to exploit the Home Automation Green. They earn $12,500 and 2.75 Master of Pwn points. #Pwn2Own

🏠Boom! @ViettelCyberSec kicks off Day 2 of #Pwn2Own Ireland as they slip past the @home_assistant Green’s defenses! Smart home, smarter hack. They head off for the first disclosure of the day. #P2OIreland
Our researcher Khoa Dinh just published his findings for ToolShell Check it here
Blog for ToolShell Disclaimer: The content of this blog is provided for educational and informational purposes only. blog.viettelcybersecurity.com/sharepoint-too… #SharePoint #ToolShell

🚨 VCS warns of active attacks on a critical SharePoint vuln we first discovered & reported. Hackers can bypass auth & take over on-prem servers. 📌 Read our guidance: prevention, detection, hunting & more. viettelsecurity.com/microsoft-shar…

🌟 Huge shoutout to our brilliant researcher @_l0gg for discovering the critical SharePoint vulnerability at Pwn2Own Berlin! 🔍 His in-depth analysis of the widely exploited ToolShell flaw is a must-read for the cybersecurity community.
Blog for ToolShell Disclaimer: The content of this blog is provided for educational and informational purposes only. blog.viettelcybersecurity.com/sharepoint-too… #SharePoint #ToolShell

🚨 Shocking impact from the SharePoint vulnerability we found at Pwn2Own! 😱 Despite our efforts to patch it 🤝, many systems are still at risk ⚠️. Secure yours now! 🔒 Details: blog.viettelcybersecurity.com/toolshell-a-cr…
Viettel Cyber Security Press Release for Customer alert, Latest research and Recommendations. Blog is comming viettelsecurity.com/microsoft-shar… #SharePoint #ToolShell

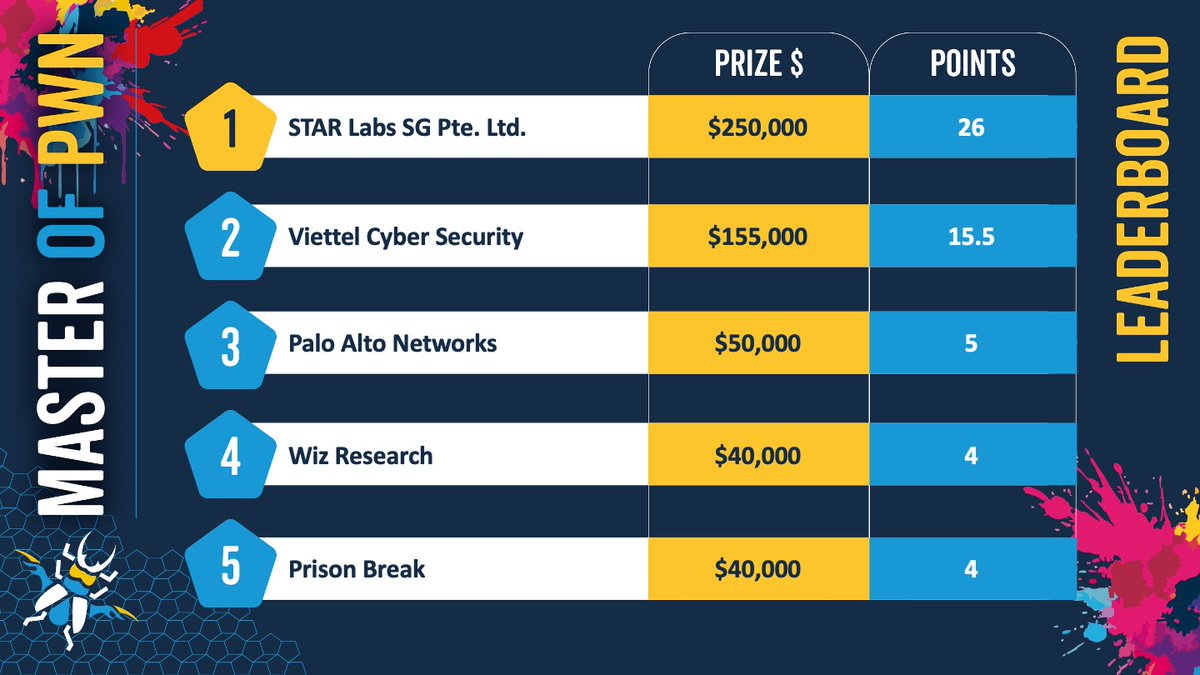
That brings Day Two of #Pwn2Own Berlin. So far, we have awarded $695,000 for 20 unique 0-days. STAR Labs has a commanding lead in Master of Pwn points and seem untouchable. Tune in tomorrow for the final day to see how it ends!
Confirmed! Viettel Cyber Security (@vcslab) used an OOB Write for their Guest-to-Host escape on #Oracle VirtualBox. The earn themselves $40,000 and 4 Master of Pwn points.


Blockbuster from @_l0gg Congratulation 🥳🥳🥳
Confirmed!! Dinh Ho Anh Khoa (@_l0gg) of Viettel Cyber Security combined an auth bypass and an insecure deserialization bug to exploit #Microsoft SharePoint. He earns $100,000 and 10 Master of Pwn points. #Pwn2Own #P2OBerlin


First successful entry for the Pwn2Own Berlin 2025 from our team 🍾🍾🍾
Boom! Viettel Cyber Security @vcslab was successful in demonstrating their attempt against NVIDIA Triton Inference Server - they are headed off to the disclosure room now. #Pwn2Own #P2OBerlin

🚨 Pwn2Own Automotive 2025 is a wrap! 🚗💥 🎉 We proudly made it to the Top 5 teams in our debut in the Automotive category! With 4 entries, 8.75 points, and $53,750 awarded, we’re just getting started in this exciting new field. 💪 Here's to more breakthroughs ahead! 🌍🔥
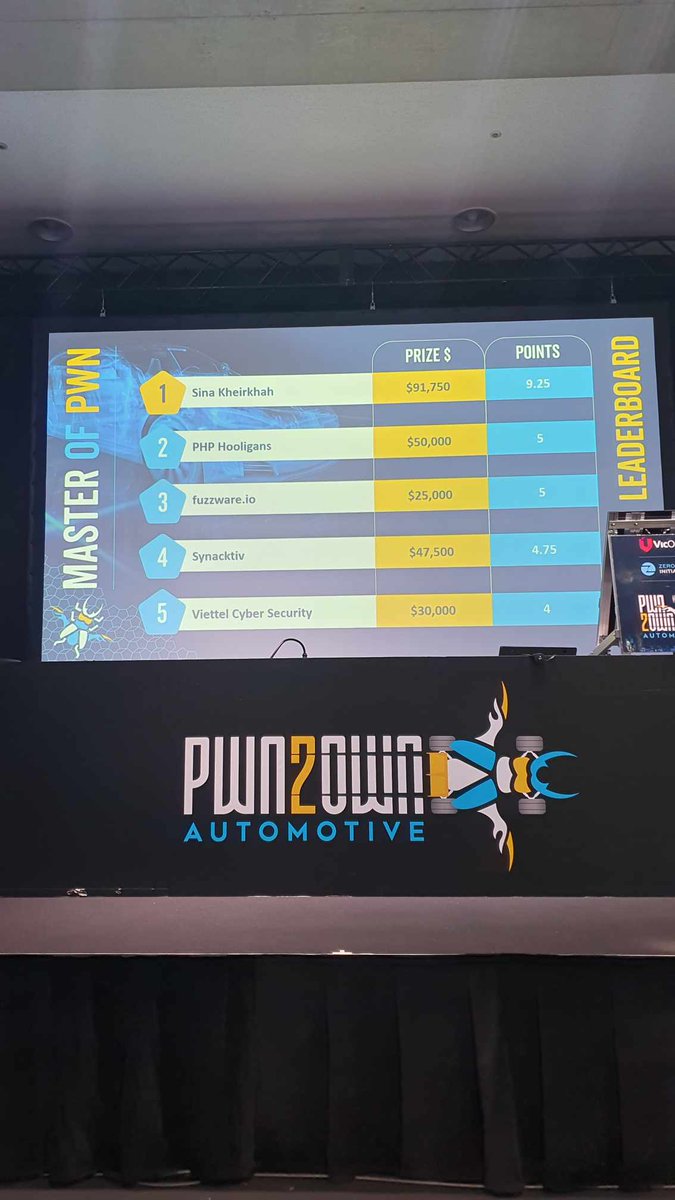
And that’s a wrap! #Pwn2Own Automotive 2025 is complete. In total, we awarded $886,250 for 49 0-days over the three day competition. With 30.5 points and $222,250 awarded, Sina Kheirkhah (@SinSinology) of Summoning Team (@SummoningTeam) is our Master of Pwn. #P2OAuto

After 2 thrilling days, our journey has come to an end, and guess what? Our white-hat hacker team is proudly in the Top 5 of the world’s greatest! 📷📷 Now it’s time to pack those trophies, head back to Vietnam, and celebrate Tet! 📷📷 Welcome home, our champions @vcslab…
Day 2 of #Pwn2Own Automotive comes to a close. We awarded $335,500, which brings the event total to $718,250. So far, 39 unique 0-days have been disclosed, & we've seen research never before demonstrated. @SinSinology has a commanding lead for Master of Pwn. Stay tuned for Day 3.

In an #Pwn2Own After Dark entry, the team from @vcslab exploited the Sony XAV-AX8500, but the bug they used was previously know. They earn $5,000 and 1 Master of Pwn point. #P2OAuto #Pwn2Own

初日が無事に終了しました。ご支援いただき、本当にありがとうございます。明日もさらに多くの勝利が待っています!#アルパイン #Kenwood Our first day has come to an end with two successful exploitations 😊 and we got into Top 5 Thank you for your support. More victories await us…
Confirmed! @vcslab used an OS command injection bug to exploit the #Kenwood IVI for code execution. They win $20,000 and 2 Master of Pwn points.


🚨Proud to join Pwn2Own Tokyo 2025! 🌏💥 💪 Ready to take on the challenge and own it! 🔥 #CyberSecurity #Pwn2Own #vcslab #Viettel
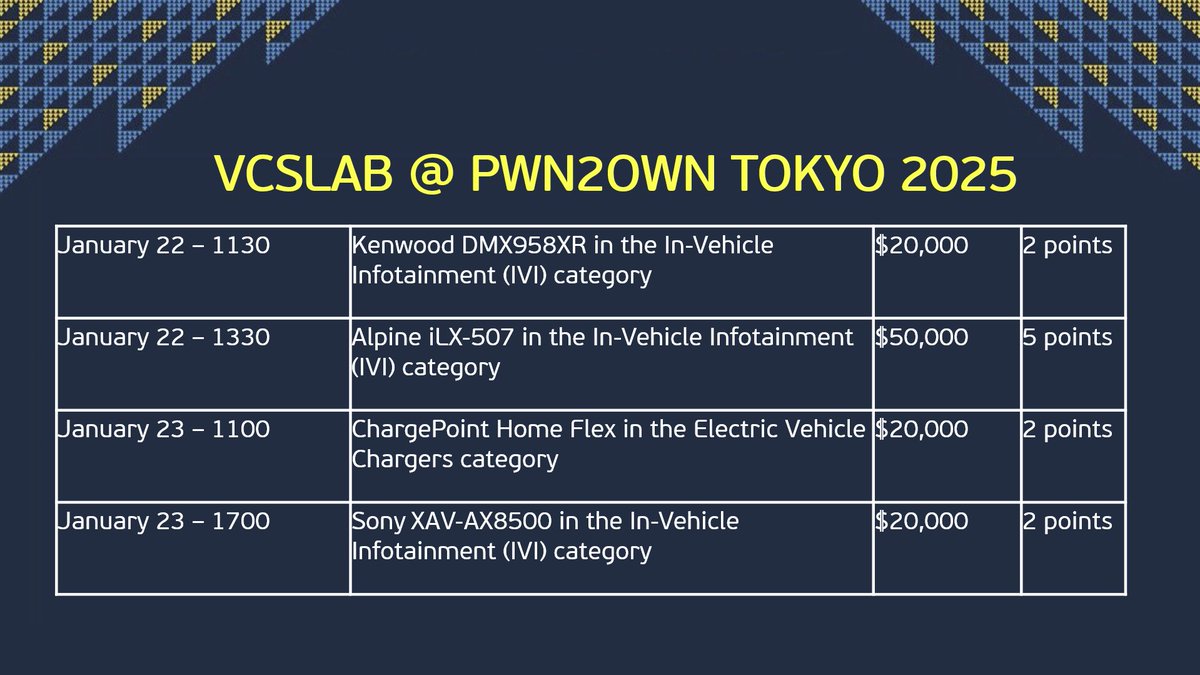
The schedule for #Pwn2Own Automotive is live! We have 50 entries from 21 teams across three categories. EV Chargers and IVI systems turned out to be popular choices. See the full schedule at zerodayinitiative.com/blog/2025/1/21… #P2OAuto
Rock on🤘🤘🤘 It is interesting to hear the legendary stories surrounding the rocks here. #Pwn2Own #Ireland #MasterOfPwn
United States Trends
- 1. #BUNCHITA 1,903 posts
- 2. #SmackDown 41.4K posts
- 3. Aaron Gordon 1,659 posts
- 4. Giulia 13.6K posts
- 5. Tulane 3,298 posts
- 6. Supreme Court 176K posts
- 7. #OPLive 2,182 posts
- 8. Connor Bedard 1,812 posts
- 9. Caleb Wilson 5,261 posts
- 10. #BostonBlue 4,156 posts
- 11. #Blackhawks 1,486 posts
- 12. Northwestern 4,669 posts
- 13. Rockets 19.8K posts
- 14. Podz 2,232 posts
- 15. Scott Frost N/A
- 16. Westbrook 4,637 posts
- 17. Lash Legend 5,857 posts
- 18. Chelsea Green 5,871 posts
- 19. Frankenstein 70.3K posts
- 20. Zach Lavine N/A
You might like
-
 TheZDIBugs
TheZDIBugs
@TheZDIBugs -
 starlabs
starlabs
@starlabs_sg -
 Bien 🇻🇳
Bien 🇻🇳
@bienpnn -
 Janggggg
Janggggg
@testanull -
 Qrious Secure
Qrious Secure
@qriousec -
 Thach Nguyen Hoang 🇻🇳
Thach Nguyen Hoang 🇻🇳
@hi_im_d4rkn3ss -
 Lan Vu
Lan Vu
@lanleft_ -
 Đào Trọng Nghĩa
Đào Trọng Nghĩa
@nghiadt1098 -
 SinSinology
SinSinology
@SinSinology -
 Lê Hữu Quang Linh 🇻🇳
Lê Hữu Quang Linh 🇻🇳
@linhlhq -
 Tuan Anh Nguyen⚡️ 🇻🇳
Tuan Anh Nguyen⚡️ 🇻🇳
@haxor31337 -
 frycos
frycos
@frycos -
 Công Thành Nguyễn
Công Thành Nguyễn
@ExLuck99 -
 Dohyun Lee
Dohyun Lee
@l33d0hyun -
 Piotr Bazydło
Piotr Bazydło
@chudyPB
Something went wrong.
Something went wrong.






























































































