Nwa_Mazzi🛜
@x_mitchh
GOD FIRST | OFU KA IRI | AI Enthusiast | Cybersecurity| Python| 💻🥷♍
You might like
I strongly believe that all that's meant for me will surely manifest in its due time. God never fails. I'll always put my whole trust in him forever.
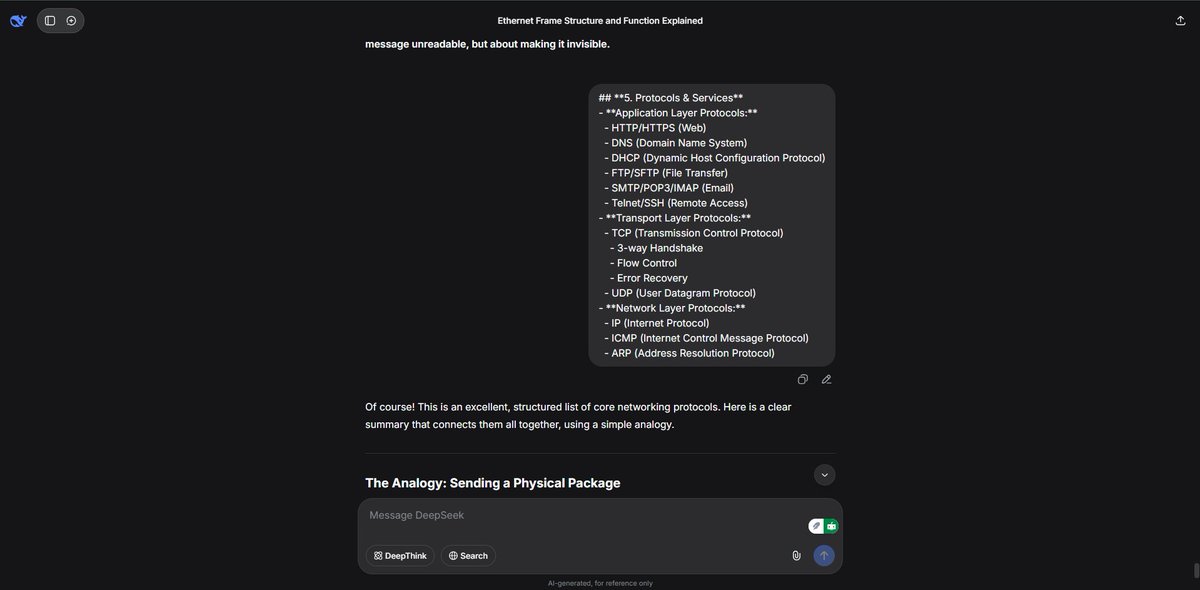
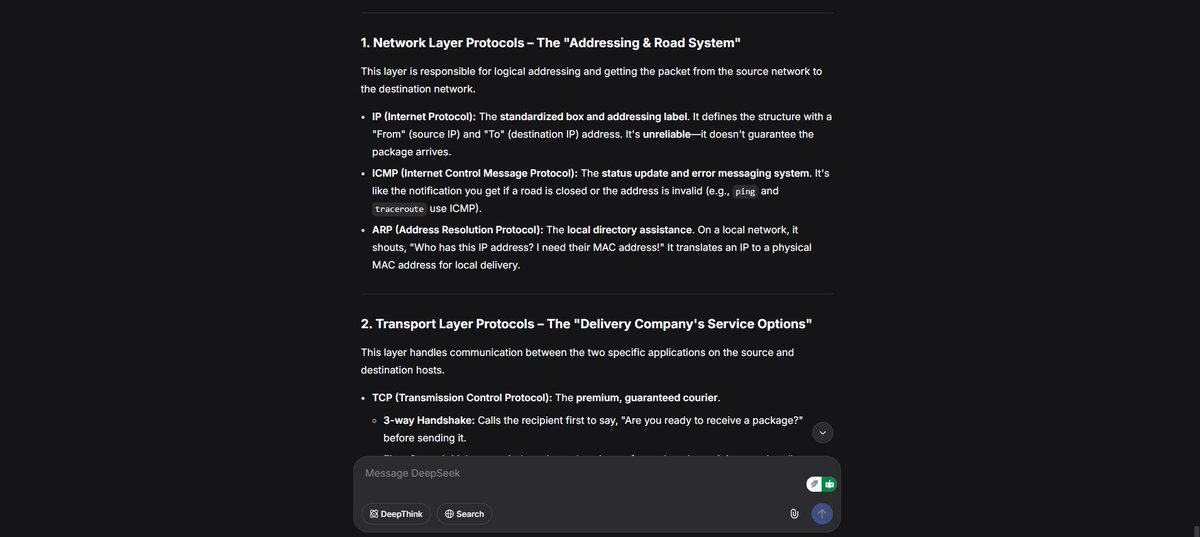
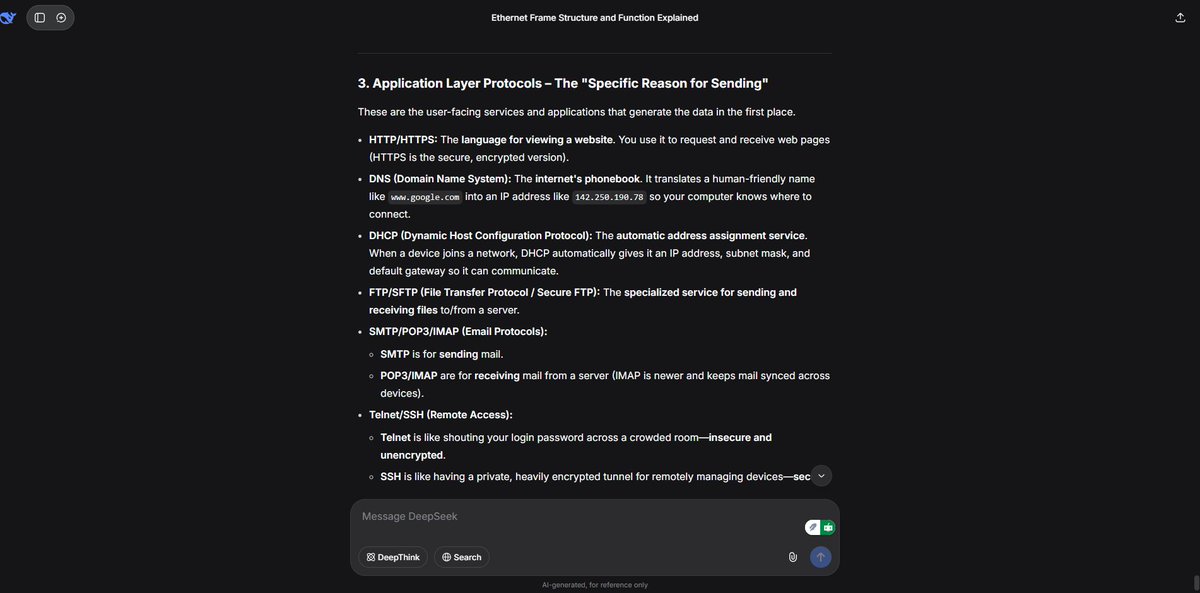
17% of #100DaysOfCybersecurity. I dive deeper into network protocols and services and also had an amazing class with my study group that was really productive and helpful. @ireteeh @segoslavia @Nnajikenechi @cyberjeremiah
16% of #100DaysOfCyberSecurity. Busy day. I did a light study on TCP and UDP and how they use port numbers. Getting ready for a productive week ahead! @ireteeh @segoslavia @Nnajikenechi
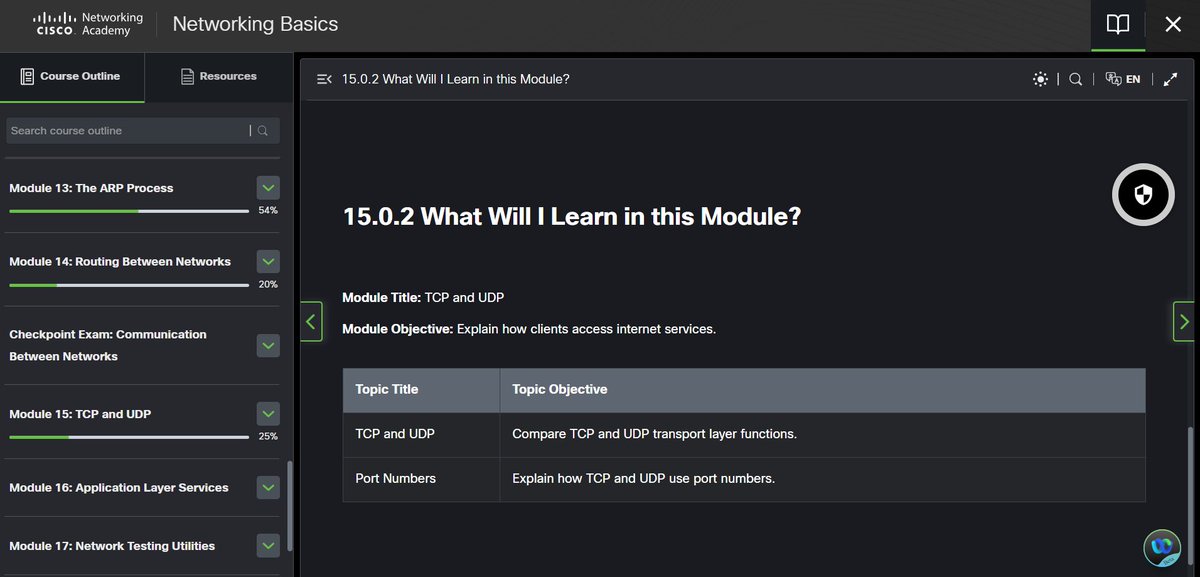
16% of #100DaysOfCyberSecurity. Busy day. I did a light study on TCP and UDP and how they use port numbers. Getting ready for a productive week ahead! @ireteeh @segoslavia @Nnajikenechi

15% of #100DaysOfCybersecurity. I took today off to relax, recharge, and review everything that I had already learned so far in networking. @ireteeh @segoslavia @Nnajikenechi @cyberjeremiah
15% of #100DaysOfCybersecurity. I took today off to relax, recharge, and review everything that I had already learned so far in networking. @ireteeh @segoslavia @Nnajikenechi @cyberjeremiah
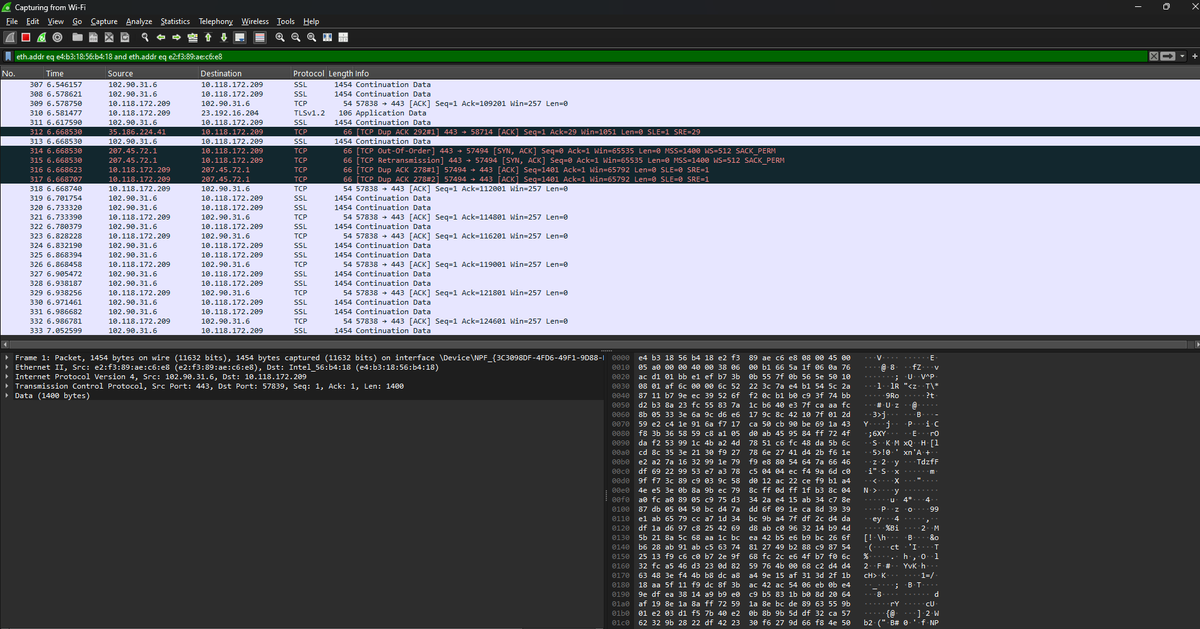
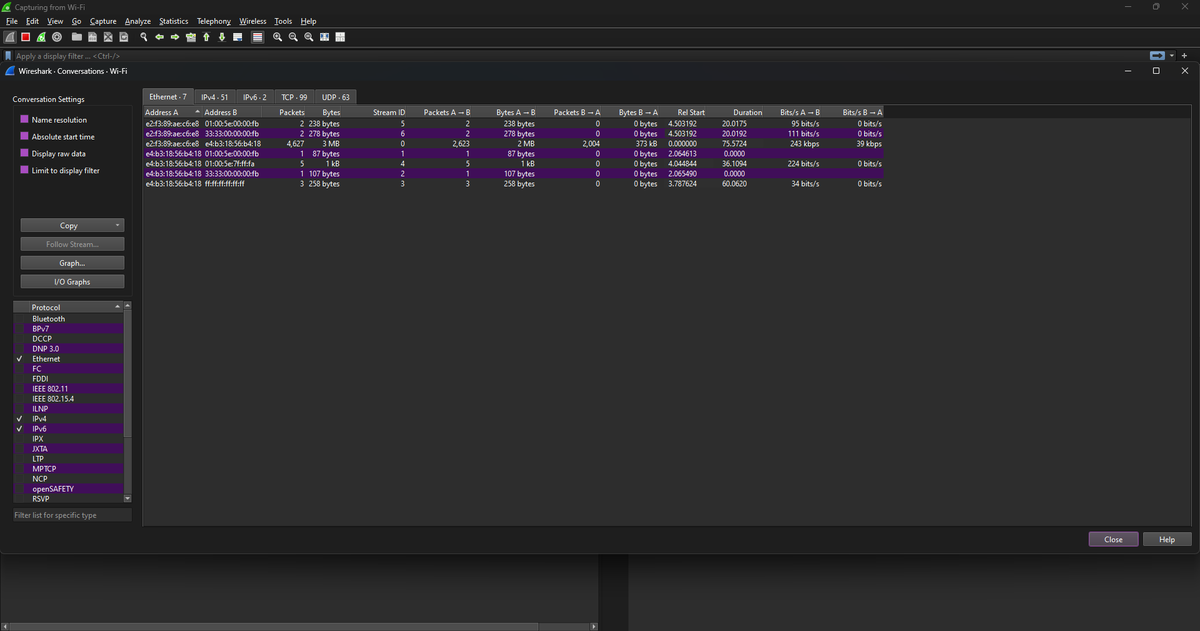
14% of #100DaysOfCyberSecurity. Busy day. I examined NAT (Network Address Translation), a protocol that translates private IPs to public IPs through a router table before going into a remote network. Still figuring out how to use Wireshark. @ireteeh @segoslavia @Nnajikenechi
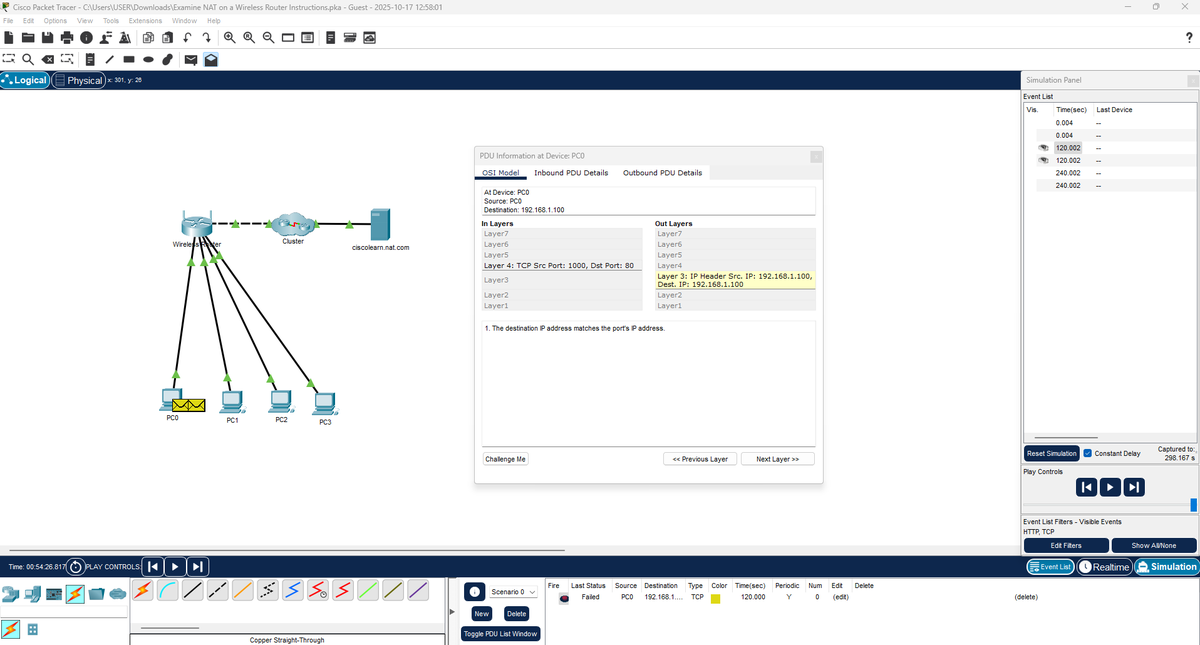
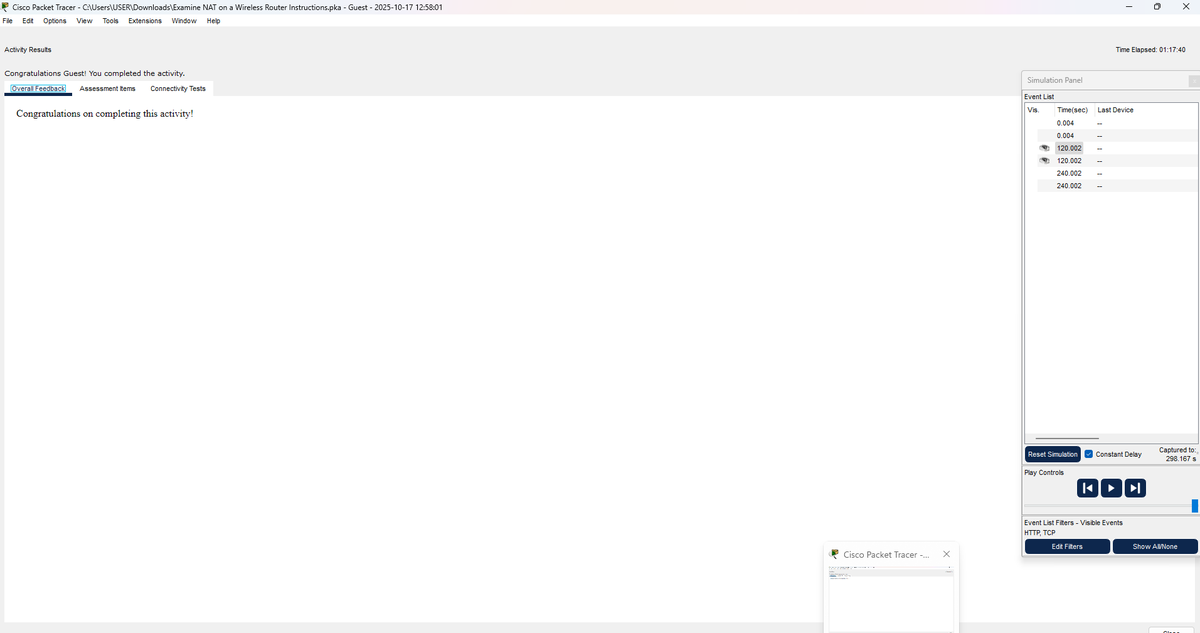
Omo I believe in myself die. I go make am
14% of #100DaysOfCyberSecurity. Busy day. I examined NAT (Network Address Translation), a protocol that translates private IPs to public IPs through a router table before going into a remote network. Still figuring out how to use Wireshark. @ireteeh @segoslavia @Nnajikenechi




13% of #100DaysOfCyberSecurity. Today was all about practice; I configured a DHCP server (used to obtain IP addresses) and installed Wireshark (a network protocol analyzer) used to analyze network traffic. Currently learning and understanding how it works. @ireteeh @segoslavia
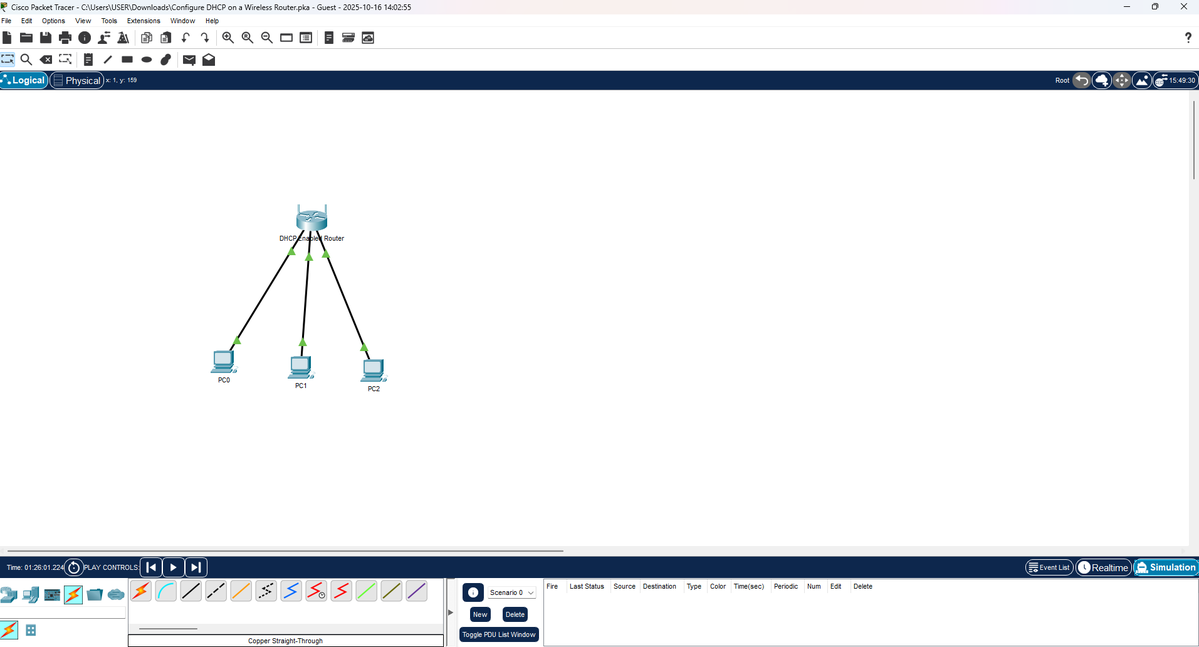
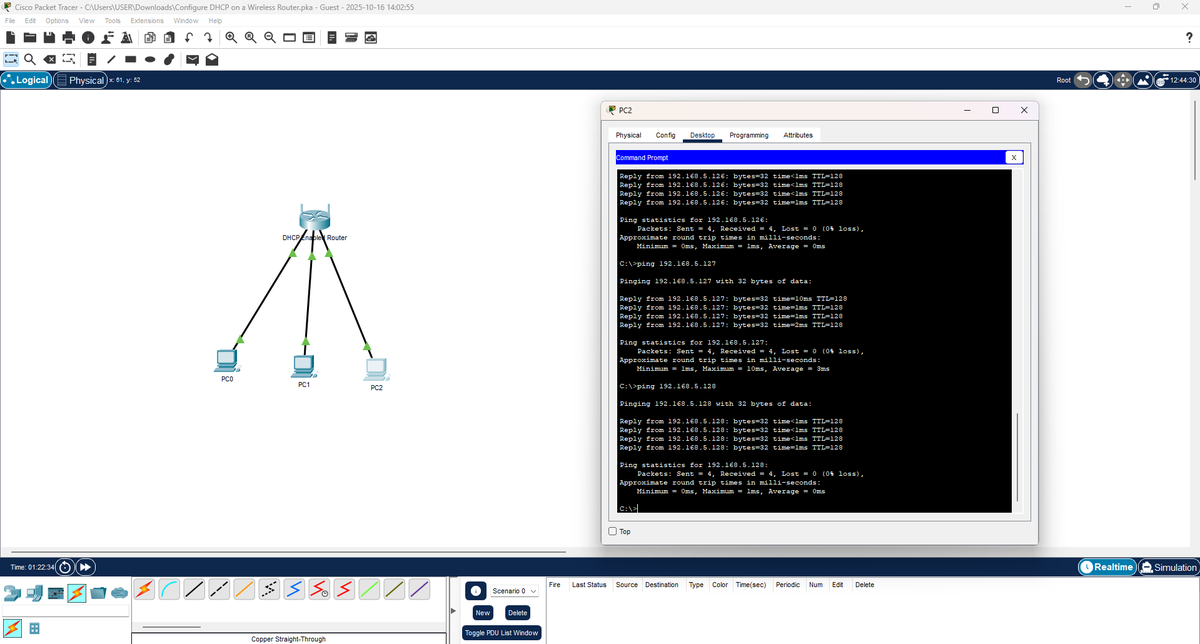
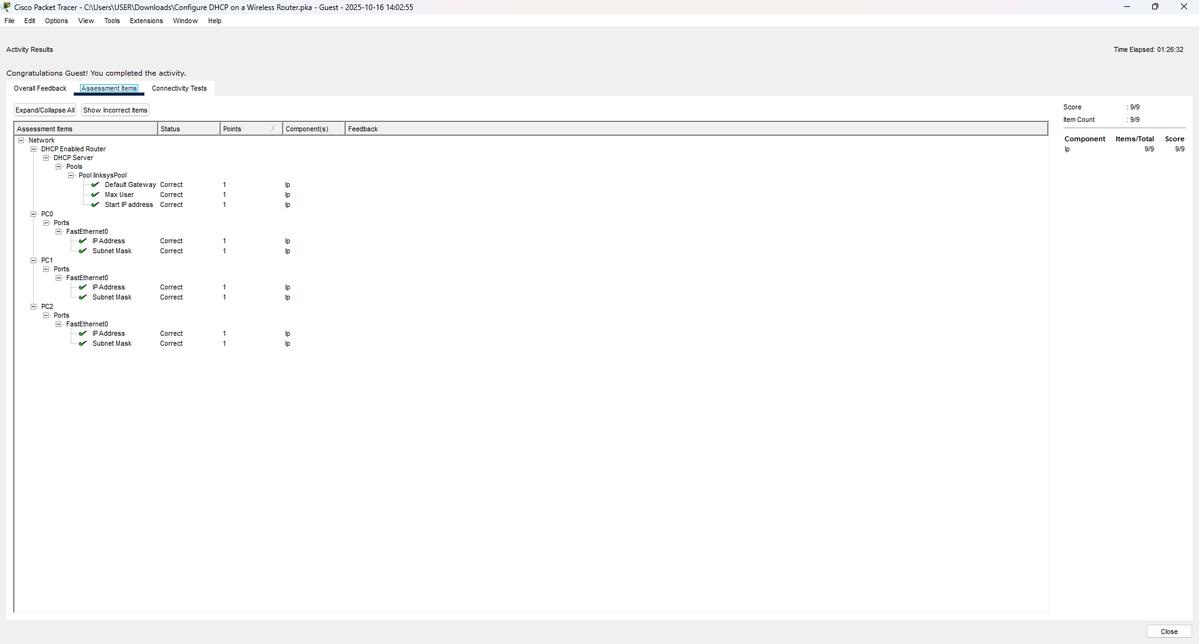
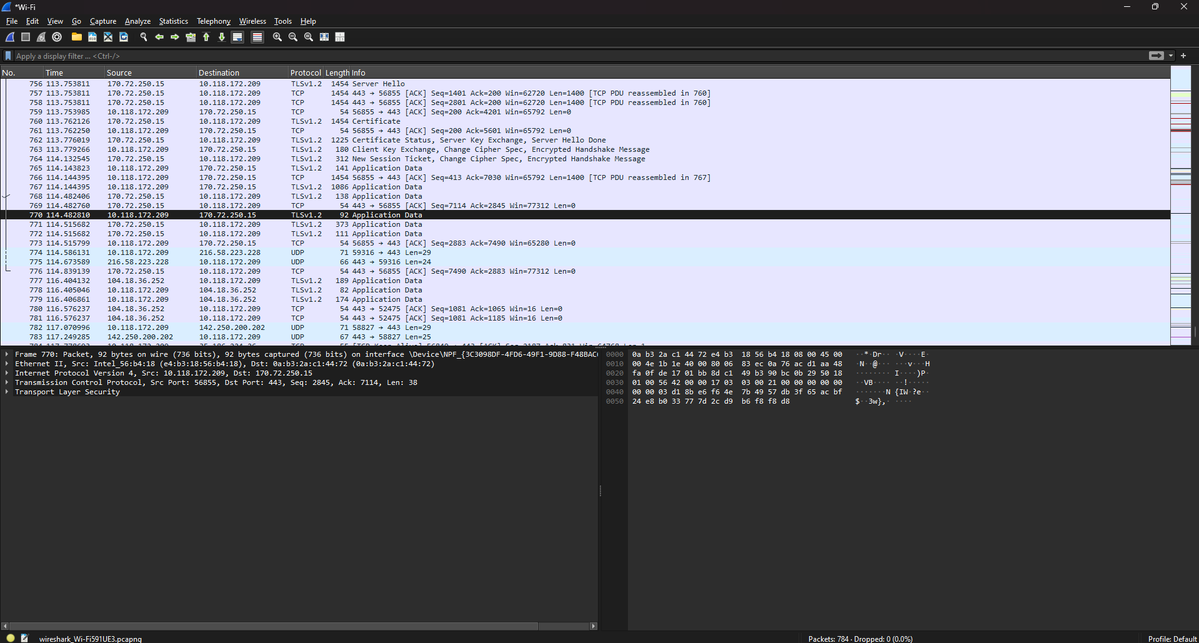
13% of #100DaysOfCyberSecurity. Today was all about practice; I configured a DHCP server (used to obtain IP addresses) and installed Wireshark (a network protocol analyzer) used to analyze network traffic. Currently learning and understanding how it works. @ireteeh @segoslavia




12% of #100DaysOfCyberSecurity. Module 14 (Routing Between Networks). @ireteeh @segoslavia
12% of #100DaysOfCyberSecurity. Module 14 (Routing Between Networks). @ireteeh @segoslavia

11% of #100DaysOfCyberSecurity. Module 13 (ARP Process). @ireteeh @segoslavia
10% of #100DaysOfCyberSecurity. Module 12 (Gateways to Other Networks). @ireteeh @segoslavia

All jokes aside, I think one of the best things that can happen to you as a young person is figuring out what you truly want to do with your life early on and being in an environment that doesn’t hinder it from happening
10% of #100DaysOfCyberSecurity. Module 12 (Gateways to Other Networks). @ireteeh @segoslavia

9% of #100DaysOfCyberSecurity. Module 11 (Dynamic Addressing with DHCP). @ireteeh @segoslavia

9% of #100DaysOfCyberSecurity. Module 11 (Dynamic Addressing with DHCP). @ireteeh @segoslavia

8% of #100DaysOfCyberSecurity. Module 10 (IPv6 Addressing Formats and Rules). @ireteeh @segoslavia

8% of #100DaysOfCyberSecurity. Module 10 (IPv6 Addressing Formats and Rules). @ireteeh @segoslavia

7% of #100DaysOfCyberSecurity. Module 9 (IPV4 and Network Segmentation). @ireteeh @segoslavia

7% of #100DaysOfCyberSecurity. Module 9 (IPV4 and Network Segmentation). @ireteeh @segoslavia

Busy day, but i still did my best to study. 6% of #100DaysOfCyberSecurity. Module 8 (Internet Protocol). @ireteeh @segoslavia @Nnajikenechi

Busy day, but i still did my best to study. 6% of #100DaysOfCyberSecurity. Module 8 (Internet Protocol). @ireteeh @segoslavia @Nnajikenechi

5% of #100DaysOfCyberSecurity. Module 6 & 7 (Network Media and the Access Layer). @ireteeh @segoslavia
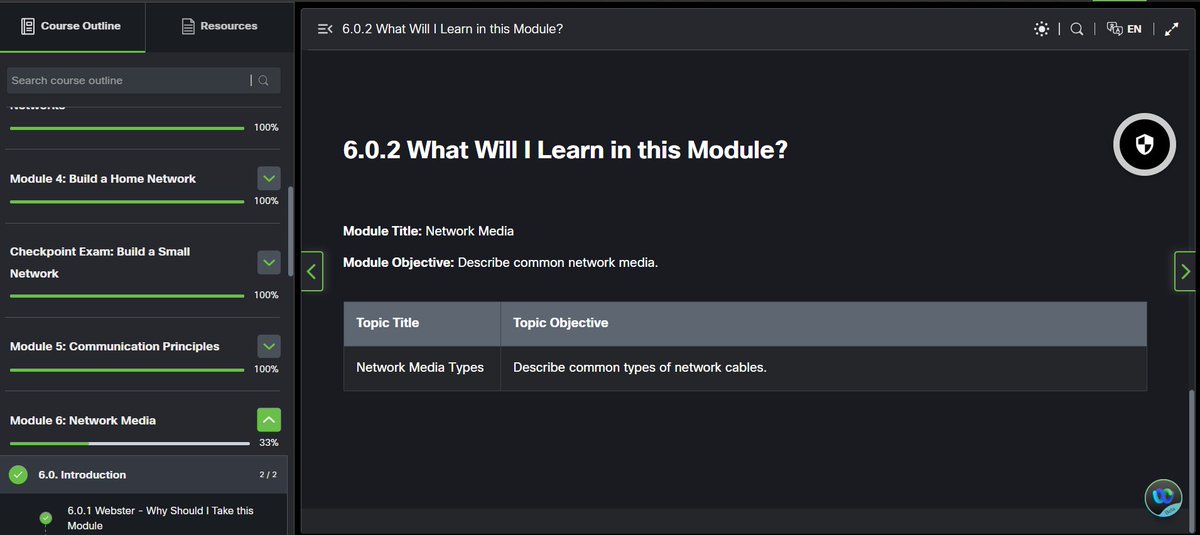
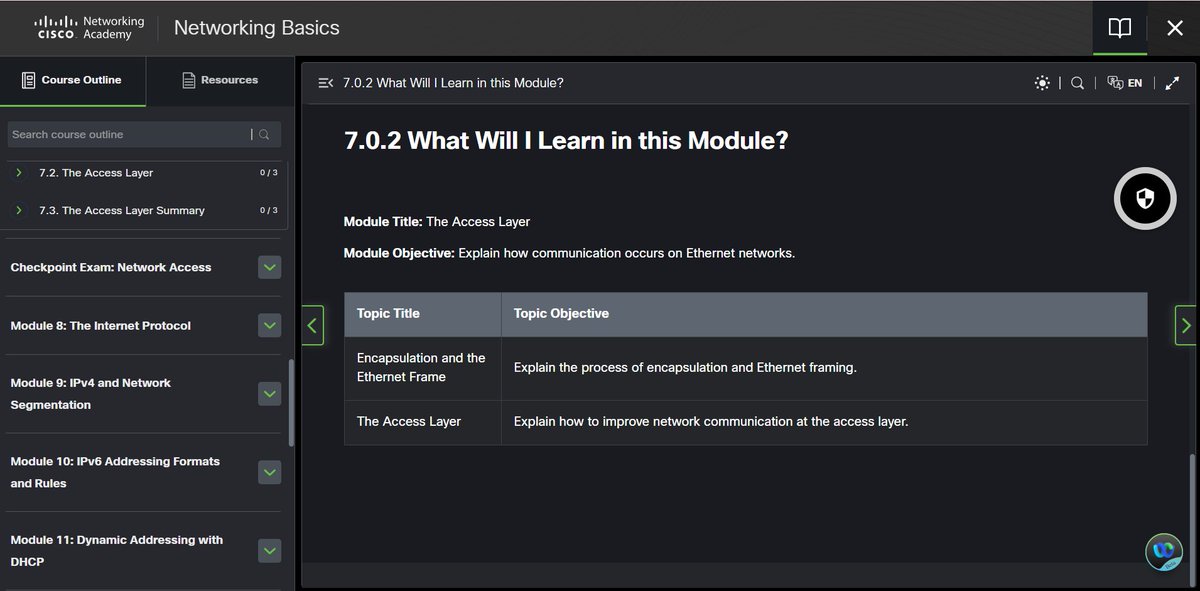
5% of #100DaysOfCyberSecurity. Module 6 & 7 (Network Media and the Access Layer). @ireteeh @segoslavia


4% of #100DaysOfCyberSecurity. Module 5 (Communications Standards & Protocols, TCP/IP and OSI models) @ireteeh @segoslavia
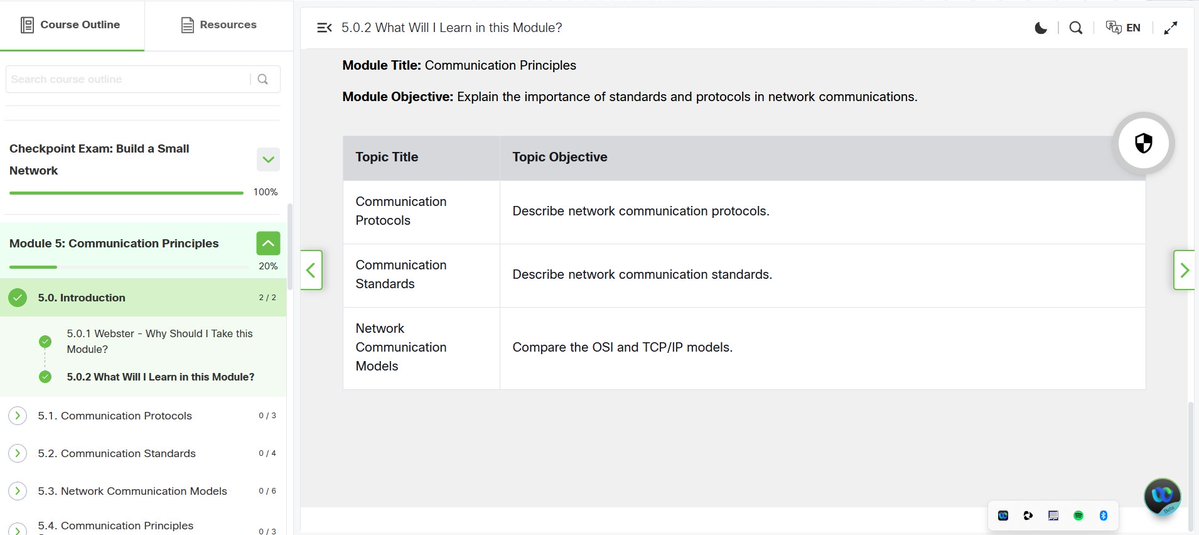
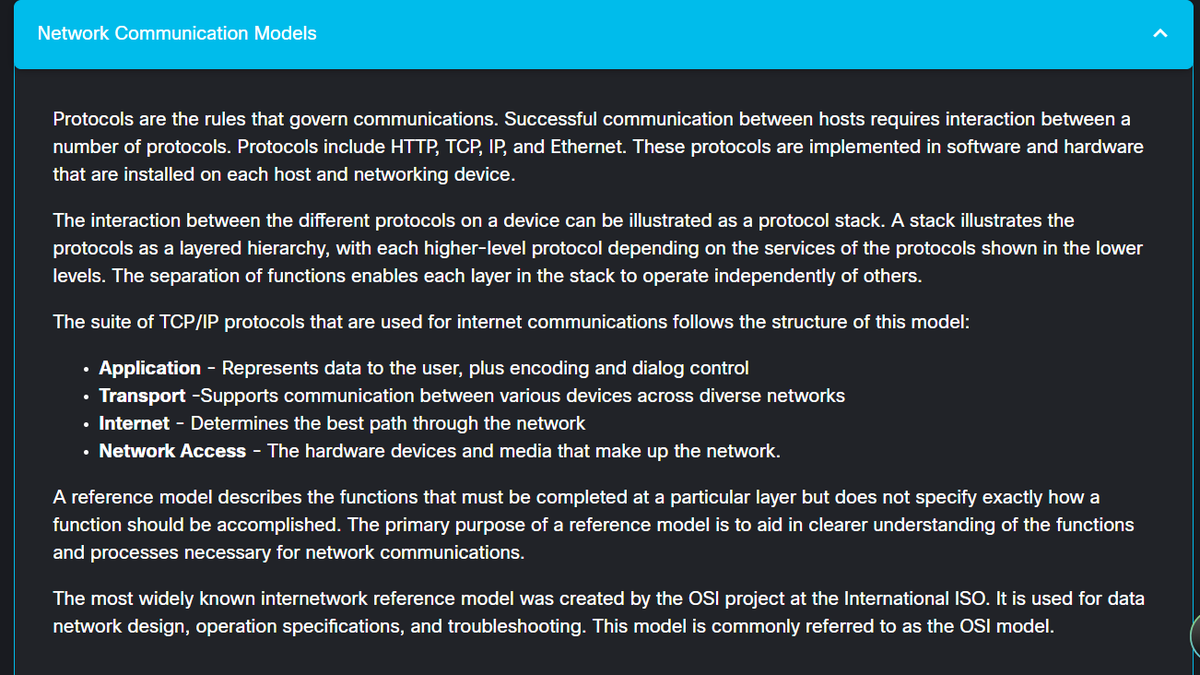

4% of #100DaysOfCyberSecurity. Module 5 (Communications Standards & Protocols, TCP/IP and OSI models) @ireteeh @segoslavia



3% of #100DaysOfCyberSecurity Module 3 & 4). @ireteeh @segoslavia
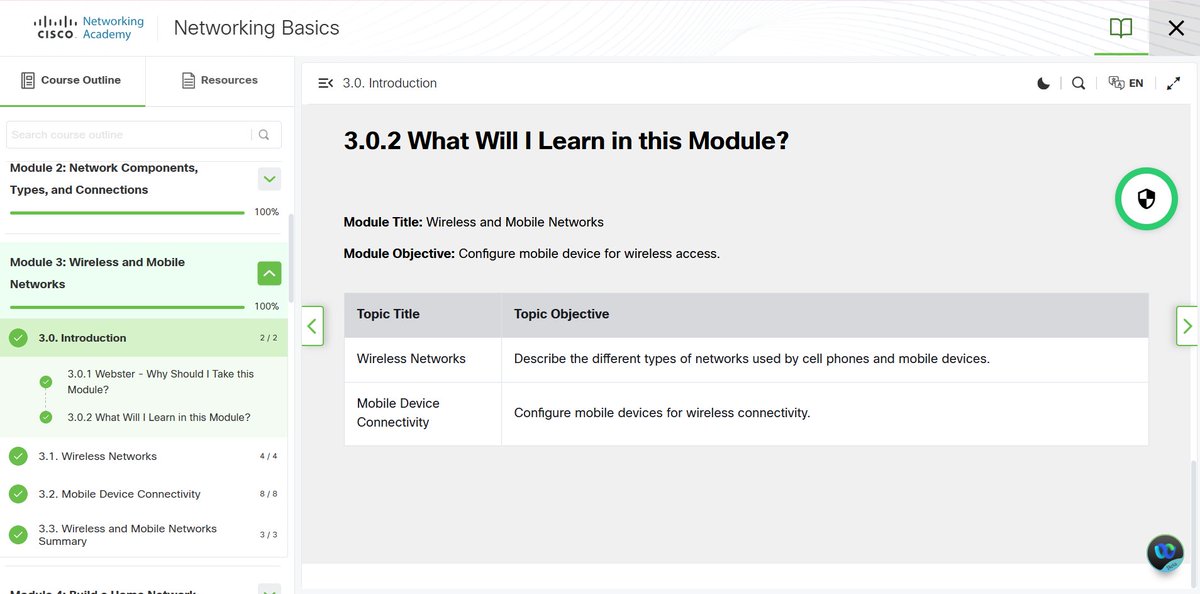

2% of #100DaysOfCyberSecurity. Module 2 (Clients and Servers, Network Components and ISP Connectivity Options). @ireteeh @segoslavia


2% of #100DaysOfCyberSecurity. Module 2 (Clients and Servers, Network Components and ISP Connectivity Options). @ireteeh @segoslavia


1% of #100DaysOfCyberSecurity. Module 1(Networks Types, Data Transmission, Bandwidth and Throughput). @ireteeh @segoslavia @Nnajikenechi

1% of #100DaysOfCyberSecurity. Module 1(Networks Types, Data Transmission, Bandwidth and Throughput). @ireteeh @segoslavia @Nnajikenechi

Excited to share that I’ve officially completed the Introduction to Cybersecurity course. Starting today, I’m launching my #100DaysOfCybersecurity challenge to deepen my knowledge, build hands-on experience, and inspire others entering the field. @ireteeh @segoslavia

Excited to share that I’ve officially completed the Introduction to Cybersecurity course. Starting today, I’m launching my #100DaysOfCybersecurity challenge to deepen my knowledge, build hands-on experience, and inspire others entering the field. @ireteeh @segoslavia

United States Trends
- 1. Good Tuesday 20.2K posts
- 2. White House 331K posts
- 3. Texans 38.8K posts
- 4. World Series 117K posts
- 5. Mariners 94.9K posts
- 6. Sanae Takaichi 56.5K posts
- 7. #Talus_Labs N/A
- 8. Blue Jays 100K posts
- 9. Cobie 32.6K posts
- 10. CJ Stroud 6,934 posts
- 11. StandX 4,848 posts
- 12. Seahawks 37.7K posts
- 13. Springer 70.1K posts
- 14. Nick Caley 2,734 posts
- 15. LA Knight 8,841 posts
- 16. East Wing 75.9K posts
- 17. Dodgers in 5 2,314 posts
- 18. Dan Wilson 4,346 posts
- 19. #LaCasaDeAlofoke2 16K posts
- 20. Financial 156K posts
You might like
Something went wrong.
Something went wrong.