You might like
The ATF of cameras
Turns out cameras have distinct blur finger prints - you can identify which camera took a photo, like a smoking gun. blur-fields.github.io

I think a lot of organizations underestimate how many modern cybercriminals have become experts in business process on top of more traditional technical ability. This is reflected most commonly through social engineering, but it manifests in other ways too. Many cybercriminals…
Saw a guy hunting for threat actors in the network today. No SIEM. No IDS. No EDR. He just sat there. Watching traffic in wireshark. Like a psychopath.
New Government Power Unlocked: The FBI is now removing malware from personal computers. The US Taxpayer is paying the FBI $11 Billion dollars per year, and we only got one strain of malware removed? Is this a 4th Amendment issue? In this case the warrant was given only after…
FBI wipes Chinese PlugX malware from over 4,000 US computers - @serghei bleepingcomputer.com/news/security/…
This is true
PayPal is updating their ToS to let themselves give your data to merchants starting Nov & they're banking on people not knowing to opt out, SO to opt out before they start: go to Settings >Data & Privacy > Manage shared info >Personalized shopping, & toggle that shit off
‼️‼️‼️‼️
Detect and shut down token attacks as they happen. Check out token protection enforcement in Microsoft Entra. #TokenProtection youtu.be/gPcNlm0CyOw
Detect and shut down token attacks as they happen. Check out token protection enforcement in Microsoft Entra. #TokenProtection youtu.be/gPcNlm0CyOw
There are levels to detection engineering!
Dear @MicrosoftTeams, Enterprise Customers (the ones who pay the bill for Teams) do not want to see advertisements inside Teams to promote the use of personal accounts: 1) Exfiltration of Company Data 2) Teams Phishing. Links clicked in Personal Chat put the corporate PC and…

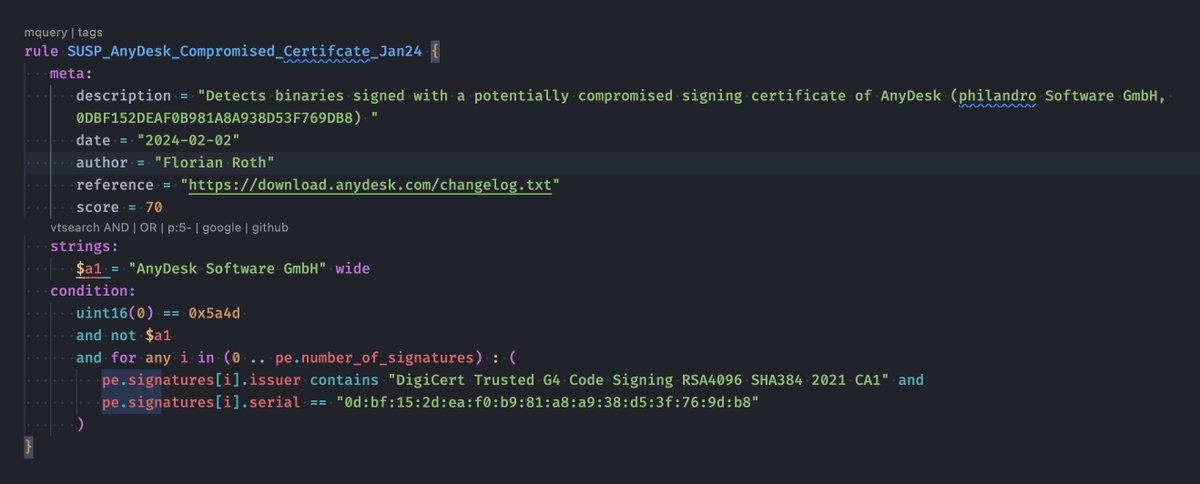
Just to be clear : this rule is for hunting purposes only. This doesn’t imply that the rule causes many false positives - on the contrary. We haven’t yet seen files signed with this certificate on VirusTotal. We expect developments regarding AnyDesk's current situation to…
I have created a YARA rule to detect binaries that are signed with a potentially compromised AnyDesk signing certificate (if the PE header info isn't AnyDesk -> other binaries signed with the compromised cert) #100DaysOfYARA #AnyDesk github.com/Neo23x0/signat…
Protect your organizations against QR code phishing with Defender for Office 365 techcommunity.microsoft.com/t5/microsoft-d… #MicrosoftDefender #Security #MicrosoftSecurity #Cybersecurity #DefenderXDR
If you are still rocking Exchange 2007, look, you got your ROI on that purchase - don’t be greedy. 😂
There are 30,635 machines on the public web with an unsupported version of Microsoft Exchange: •275 instances of Exchange Server 2007 •4,062 instances of Exchange Server 2010 •26,298 instances of Exchange Server 2013
Just released my latest analysis of Defender for Endpoint features by OS. Targeted at folks deploying MDE to understand what can be used and where; what capabilities you might have missed; or potential customers evaluating options. Blog + download: campbell.scot/mde-comparison…

Microsoft Defender has been updated to block 15 different methods of LSASS dumping @msftsecurity @AV_Comparatives microsoft.com/security/blog/…

Want to know more about MDE Advanced Features? In this video, I do a deep dive on what these features are and how they can help further secure your endpoints. #msftadvocate #mde #microsoftsecurity youtu.be/zigu9YbpsFE

youtube.com
YouTube
Getting Started with Microsoft Defender for Endpoint: Advanced...
Curious about Defender for Endpoint's Threat and Vulnerability Management capabilities? In this video, I dive into the TVM feature set. #msftadvocate #mde #tvm #defenderforendpoint youtu.be/0KY19q5ZgQ0

youtube.com
YouTube
Getting Started with Microsoft Defender for Endpoint: Threat and...
This…. Still this.
Have you just rolled out Defender for Endpoint and are wondering where to start configuring? In this video, I review how to configure the Automated Investigation feature of MDE. #defender #msftadvocate #mde youtu.be/1UJoH-p3Xik
youtube.com
YouTube
Getting Started with Microsoft Defender for Endpoint: Automated...
@zm_infosec shows how to deploy Microsoft Defender for Endpoint using Intune youtu.be/QmY0dc8rLyE

youtube.com
YouTube
Getting Started with Microsoft Defender for Endpoint: Onboarding via...
United States Trends
- 1. #FanCashDropPromotion 2,522 posts
- 2. #GRAMMYs 33.5K posts
- 3. ADDISON RAE 5,784 posts
- 4. Dizzy 7,275 posts
- 5. #FridayVibes 5,503 posts
- 6. Good Friday 62.6K posts
- 7. olivia dean 3,051 posts
- 8. #FursuitFriday 9,951 posts
- 9. #PETITCOUSSIN 22.9K posts
- 10. Munetaka Murakami 2,087 posts
- 11. Happy Friyay 1,633 posts
- 12. Publix 2,104 posts
- 13. Elise Stefanik 10.5K posts
- 14. Best New Artist 5,796 posts
- 15. Kehlani 21.5K posts
- 16. chappell 3,573 posts
- 17. Happy N7 2,778 posts
- 18. Laporta 9,213 posts
- 19. Tammy Faye 4,389 posts
- 20. Katseye 49.8K posts
Something went wrong.
Something went wrong.