#computerforensics نتائج البحث
Kudos to the trainers of the Mac Forensics course! This course is organised by CEPOL with the support of EUROPOL and ECTEG. #macforensics #computerforensics


12-27-24 DEW injuries today + Continuous barbarism waking to cut shaved hair•brows more My daughter enduring V2K/BCI Military technology TORTURE Treason betrayal in largest money laundering scandal scheme operation in history #ISeeYou #OSINT #ComputerForensics #Cybertorture 🫵

Exploring the Essentials of Computer Forensics 💻 | Uncover the foundational principles behind digital investigations, data recovery, and cybercrime analysis. Stay ahead in the evolving world of cybersecurity! #ComputerForensics #CyberSecurity #DigitalInvestigation

9-16-2024 • Network Packet Capture is a CRITICAL SOURCE OF EVIDENCE Fast effective response to cybersecurity threats network performance issues visibility into whats happening in your network Couple hour run today #ComputerForensics #Evidence #Cybertorture #Cybertrafficking 🔎

The Mac Forensics course has started at the CEPOL Cybercrime Academy. This course is organised by @EU_CEPOL with the support of @Europol and @ecteg. #macforensics #computerforensics #CEPOL #EUROPOL #ECTEG

🚀We’re heading to Paris to join MSAB at #Milipol 2025! In 2 weeks, we’ll be showcasing how Detego Suite Pro, our powerful #ComputerForensics & analytics platform, seamlessly augments MSAB’s #MobileForensics tools to create a unified #DigitalForensics ecosystem. See you there!
Woman shares genius hack using old Parmesan shaker lids: 'This is wonderful' ift.tt/KFpB1GE #computerforensics
Digital evidence can't hide from us! Our computer forensics team uncovers the facts securely and thoroughly, leaving no digital-stone unturned. See how we support your investigations: kldiscovery.com/solutions/comp… #ComputerForensics #DigitalEvidence #LegalTech

🚨 Join "Demystifying Data" workshop and master data conversion between binary, hexadecimal, decimal, & ASCII. Learn manual and tool-based methods, ensuring you can interpret digital evidence with ease. Register ➡️ buff.ly/3WVCrMR #DFIR #ComputerForensics

𝐖𝐚𝐧𝐭 𝐭𝐨 𝐫𝐞𝐝𝐮𝐜𝐞 𝐟𝐨𝐫𝐞𝐧𝐬𝐢𝐜 𝐰𝐨𝐫𝐤𝐥𝐨𝐚𝐝 𝐛𝐲 𝟑𝟎%? 𝐉𝐨𝐢𝐧 𝐮𝐬 𝐨𝐧 𝟐𝟕𝐭𝐡 𝐌𝐚𝐫𝐜𝐡 𝐭𝐨 𝐥𝐞𝐚𝐫𝐧 𝐡𝐨𝐰: eu1.hubs.ly/H0hFqF90 #DFIR #digitalforensics #computerforensics #mobileforensics #incidentresponse #cybersecurity

Turn pixels into evidence! Our guide to photo forensics with Belkasoft X shows you how to uncover the truth hidden in images. Read it here: eu1.hubs.ly/H0plPYB0 #DFIR #digitalforensics #computerforensics #incidentresponse

What is the different between Cyber Securityss & Computer Forensics? How about Forensic Science? 🧬🔍 Get the answer at @msumalaysia , come and see us or whatsapp us now 💻🧑💻 #cybersecurity #computerforensics #forensicscience #msumalaysia #MSUengage #go2msu

Don't miss ADF at the Law Enforcement Summit THIS FRIDAY, March 7th! Learn about the latest advancements in #digitalforensics, #mobileforensics, and #computerforensics. We can't wait to connect! #lawenforcement

🚨 Don't miss our hands-on workshop, "Demystifying Data," with @4enzikat0r! Learn to convert binary, hexadecimal, decimal, and ASCII. Gain actionable skills through interactive exercises and real-world examples. Register ➡️ buff.ly/3WVCrMR #DFIR #ComputerForensics

🚨Do you know everything about your files? Think again! Join TOMORROW’S workshop "Beyond File Names" with @4enzikat0r! and uncover hidden details using file signatures and metadata. ➡️ sans.org/u/1wp4 #ComputerForensics #DFIR

Excited to be at the Florida ICAC Conference at the Hyatt Regency Orlando. Stop by booth #6 to learn more about our cutting-edge digital forensic solutions! #digitalforensics #mobileforensics #computerforensics #CSAM #ICAC

🚨 File extensions don't tell the whole story... In this workshop @4enzikat0r! will dive into file signatures and metadata analysis. You'll uncover hidden details about a file’s origin, author, with hands-on exercises. ➡️ sans.org/u/1wp4 #DFIR #ComputerForensics

Join us at the Florida ICAC Conference! Our team is ready to discuss your digital investigation needs and showcase the latest advancements in forensic technology. Find us at booth #6. #digitalforensics #mobileforensics #computerforensics #CSAM #ICAC

Woman shares genius hack using old Parmesan shaker lids: 'This is wonderful' ift.tt/KFpB1GE #computerforensics
"RAM Forensics: Tools, Techniques, and Best Practices" Some of the most valuable evidence in digital forensics and cyber incident response investigations never touches the disk. It exists only in Random Access Memory (RAM), the computer's high-speed wor… ift.tt/GzWEZrd
Decode the Clue. Drop Your Answer. Digital evidence never lies—only experts can decode it. Think you know which Windows artifact reveals file deletion time? Comment your answer and test your forensic intelligence. #UPSIFS #ForensicScience #DigitalForensics

(Free by the author) Forensic Discovery: freecomputerbooks.com/Forensic-Disco… Look for "Read and Download Links" section to download. Follow me if you like this post. #ForensicDiscovery #ForensicScience #DigitalForensics #ComputerForensics #MultimediaForensics

The blow no one expected: a new hack shakes the market and drags Bitcoin down more than 5%. ift.tt/6hXfxb2 #computerforensics
Asahi Hackers Stole Personal Data Of 2 Million People - Silicon UK ift.tt/ahZUWBs #computerforensics
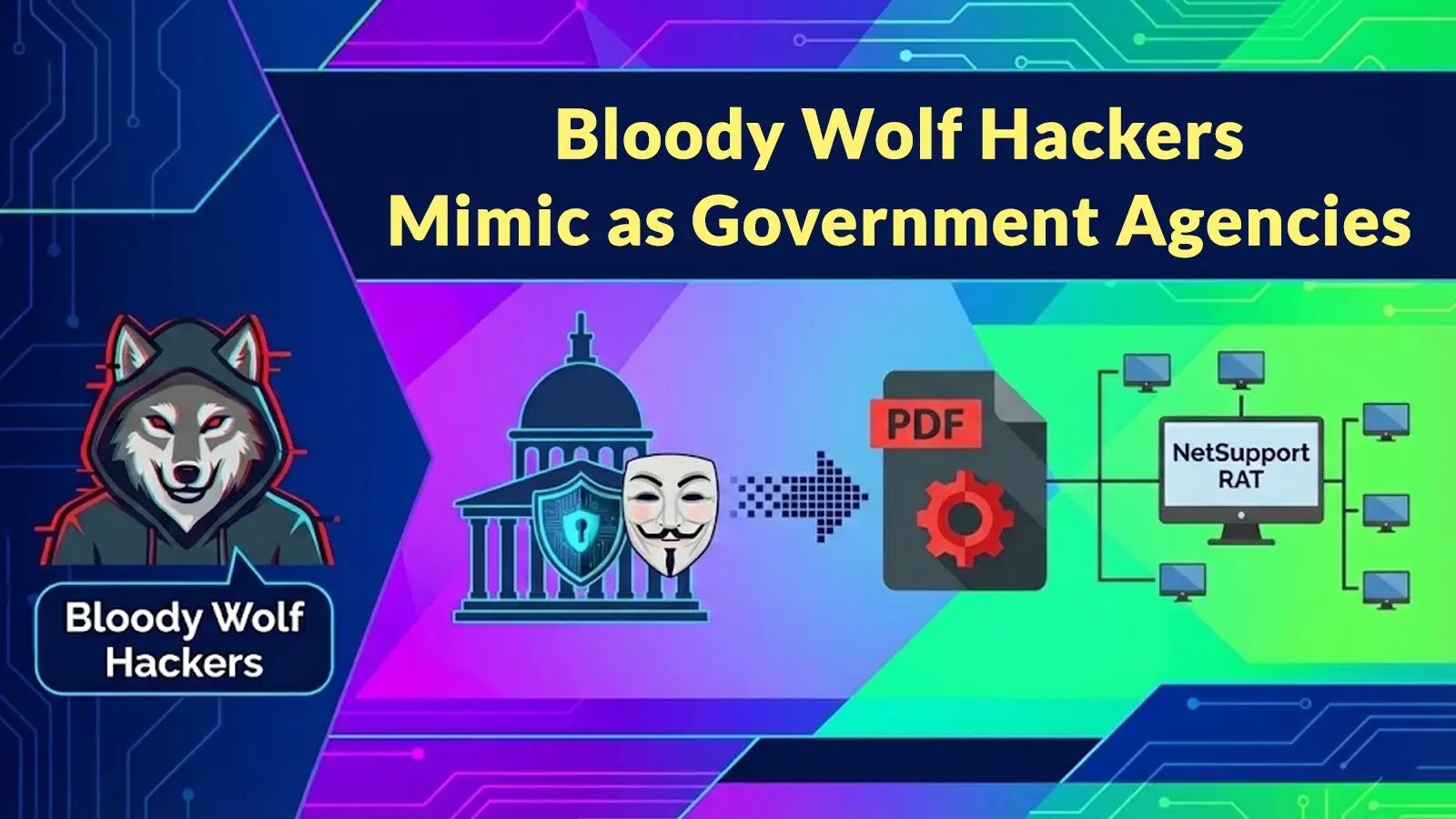
Bloody Wolf Hackers Mimic as Government Agencies to Deploy NetSupport RAT via ... ift.tt/vAXrBQf #computerforensics
Bloody Wolf Hackers Use Fake Government PDFs to Deliver NetSupport RAT - GBHackers ift.tt/oEgiWPI #computerforensics
Buy Is Digital Forensics Right for You? Take This Mini Course Before You Invest in Training or Degrees on @Gumroad waldrep.gumroad.com/l/DigitalForen… #digitalforensics #computerforensics #forensics #police #lawenforcement #cybercrime
Former fed prosecutor Saritha Komatireddy to run against embattled NY AG Letitia James ift.tt/mCjcR5k #computerforensics
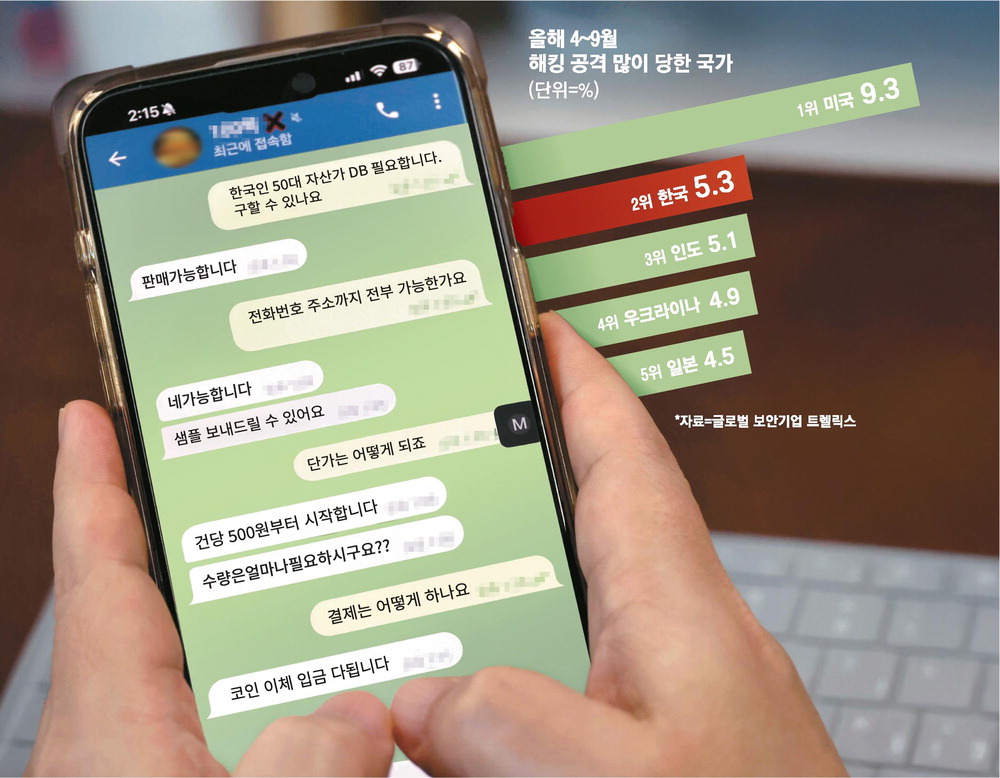
I have the contact information for the executives of Korea's top 100 companies. We'll give you a fu.. ift.tt/v8Eshp2 #computerforensics
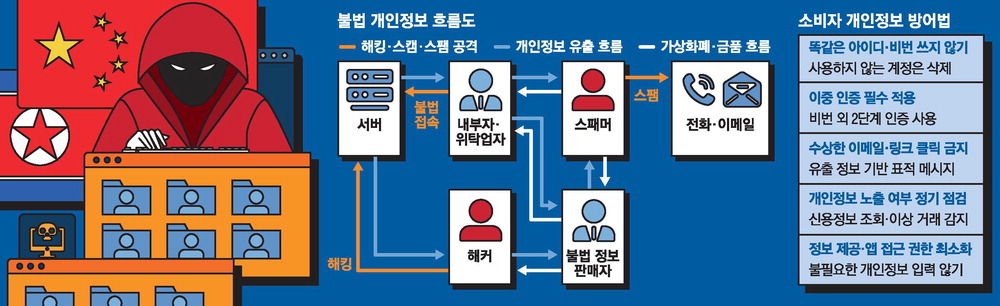
As it is said that "my personal information is already a public good," various information on Korean.. ift.tt/vy5wdeW #computerforensics
Asahi Hackers Stole Personal Data Of 2 Million People - Silicon UK ift.tt/Z4uwN6t #computerforensics
Lazarus, Kimsuky Conduct 58 Attacks Targeting South Korea ift.tt/tq1dEJr #computerforensics
No se evalúan anti-forensic traces: aplicaciones de limpieza, borrado seguro, sobrescritura o manipulación previa. Sin detectar estas señales, no puede afirmarse autenticidad de los datos.
Exclusive: KT's 134 Billion Won Bonuses Contrast Subsidiaries' Minimal Pay ift.tt/sm0gpvC #computerforensics
#digitalforensics #computerforensics #cyberforensics #Thailand #Bangkok public training available contact us [email protected] หลักสูตร Digital Forensics & Digital Evidence – Unlocking the Secrets Course

Decentralized Governance: What We Can Learn from the Balancer Hack - OneSafe Blog ift.tt/iTzI13j #computerforensics
Forensics: After a major incident, the SOC team conducts digital forensics to legally and technically trace the source, scope, and method of the attack, supporting legal action and improving future defenses.
Digital Forensics pros: Dive into investigating Conti ransomware using Splunk! hackers-arise.com/digital-forens… @three_cube @_aircorridor

(Open Access) Digital Forensics: freecomputerbooks.com/Digital-Forens… Look for "Read and Download Links" section to download. Follow me if you like this post. #DigitalForensics #ComputerForensics #ForensicScience #Nmap #Forensics #CyberSecurity

Kudos to the trainers of the Mac Forensics course! This course is organised by CEPOL with the support of EUROPOL and ECTEG. #macforensics #computerforensics


Digital evidence can't hide from us! Our computer forensics team uncovers the facts securely and thoroughly, leaving no digital-stone unturned. See how we support your investigations: kldiscovery.com/solutions/comp… #ComputerForensics #DigitalEvidence #LegalTech

12-27-24 DEW injuries today + Continuous barbarism waking to cut shaved hair•brows more My daughter enduring V2K/BCI Military technology TORTURE Treason betrayal in largest money laundering scandal scheme operation in history #ISeeYou #OSINT #ComputerForensics #Cybertorture 🫵

𝐖𝐚𝐧𝐭 𝐭𝐨 𝐫𝐞𝐝𝐮𝐜𝐞 𝐟𝐨𝐫𝐞𝐧𝐬𝐢𝐜 𝐰𝐨𝐫𝐤𝐥𝐨𝐚𝐝 𝐛𝐲 𝟑𝟎%? 𝐉𝐨𝐢𝐧 𝐮𝐬 𝐨𝐧 𝟐𝟕𝐭𝐡 𝐌𝐚𝐫𝐜𝐡 𝐭𝐨 𝐥𝐞𝐚𝐫𝐧 𝐡𝐨𝐰: eu1.hubs.ly/H0hFqF90 #DFIR #digitalforensics #computerforensics #mobileforensics #incidentresponse #cybersecurity

9-16-2024 • Network Packet Capture is a CRITICAL SOURCE OF EVIDENCE Fast effective response to cybersecurity threats network performance issues visibility into whats happening in your network Couple hour run today #ComputerForensics #Evidence #Cybertorture #Cybertrafficking 🔎

Exploring the Essentials of Computer Forensics 💻 | Uncover the foundational principles behind digital investigations, data recovery, and cybercrime analysis. Stay ahead in the evolving world of cybersecurity! #ComputerForensics #CyberSecurity #DigitalInvestigation

🚨 File extensions don't tell the whole story... In this workshop @4enzikat0r! will dive into file signatures and metadata analysis. You'll uncover hidden details about a file’s origin, author, with hands-on exercises. ➡️ sans.org/u/1wp4 #DFIR #ComputerForensics

What is the different between Cyber Securityss & Computer Forensics? How about Forensic Science? 🧬🔍 Get the answer at @msumalaysia , come and see us or whatsapp us now 💻🧑💻 #cybersecurity #computerforensics #forensicscience #msumalaysia #MSUengage #go2msu

🚨 Join "Demystifying Data" workshop and master data conversion between binary, hexadecimal, decimal, & ASCII. Learn manual and tool-based methods, ensuring you can interpret digital evidence with ease. Register ➡️ buff.ly/3WVCrMR #DFIR #ComputerForensics

THE FOUNDERS BELIEVED THAT NATURAL RIGHTS ARE INHERENT IN ALL PEOPLE BY VIRTUE OF THEIR BEING HUMAN THAT CERTAIN OF THESE RIGHTS ARE UNALIENABLE MEANING THEY CANNOT BE SURRENDERED TO GOVERNMENT UNDER ANY CIRCUMSTANCES #ComputerForensics #Government #HumanRights @Weaponization ⚖️

🚨Do you know everything about your files? Think again! Join TOMORROW’S workshop "Beyond File Names" with @4enzikat0r! and uncover hidden details using file signatures and metadata. ➡️ sans.org/u/1wp4 #ComputerForensics #DFIR

🚨 Don't miss our hands-on workshop, "Demystifying Data," with @4enzikat0r! Learn to convert binary, hexadecimal, decimal, and ASCII. Gain actionable skills through interactive exercises and real-world examples. Register ➡️ buff.ly/3WVCrMR #DFIR #ComputerForensics

Join us this week at the National Digital Investigators Conference 2024 from November 12-14! #digitalforensics #computerforensics #mobileforensics #NDIC

Want to decode binary data like a pro? 💻 Join @4enzikat0r! for "Demystifying Data" workshop! Learn to convert binary, hexadecimal, decimal, & ASCII. Enhance your skills with interactive exercises and real-world examples. ➡️ buff.ly/3WVCrMR #ComputerForensics

Don't miss ADF at the Law Enforcement Summit THIS FRIDAY, March 7th! Learn about the latest advancements in #digitalforensics, #mobileforensics, and #computerforensics. We can't wait to connect! #lawenforcement

Check out ADF this week at the 2024 Annual Provincial ICE Strategy Multidisciplinary Training Workshop in Ontario! #digitalforensics #mobileforensics #computerforensics #forensicstraining

Digital #evidence plays a crucial role in modern investigations. Our skilled professionals will work to uncover vital information from #digital devices. Learn More: AlphaGP.com #computerforensics #DigitalEvidence

Something went wrong.
Something went wrong.
United States Trends
- 1. #GivingTuesday 12.4K posts
- 2. #ALLOCATION 265K posts
- 3. The BIGGЕST 460K posts
- 4. #JUPITER 265K posts
- 5. Good Tuesday 35.2K posts
- 6. #GMMTVxTPDA2025 822K posts
- 7. Susan Dell N/A
- 8. Lucario 7,043 posts
- 9. Michael Dell 1,573 posts
- 10. rUSD N/A
- 11. Costco 34.4K posts
- 12. Michael and Susan N/A
- 13. Taco Tuesday 12.1K posts
- 14. Kanata 27.6K posts
- 15. #AreYouSure2 64K posts
- 16. Dart 41.4K posts
- 17. Trump Accounts 5,096 posts
- 18. JOSSGAWIN AT TPDA2025 124K posts
- 19. JIMMYSEA TPDA AWARD 2025 81.9K posts
- 20. King Von N/A