#datasecuritycompliance 搜尋結果
Investment in #DataProtection regulations & #DataPrivacy policies have become very crucial as the cost of a data breach is much greater–in both tangible & intangible terms. Its very important for the organisation to have the required #DataSecurityCompliance & policies in place.

Prevent data disasters with DLP best practices- enforce access controls, monitor endpoints, encrypt everything, and automate backups. It’s not just protection—it’s precision. shorturl.at/Nytwd #DataLossPrevention #DataSecurityCompliance #DataProtection #DLPTools

What is the Need for Data Protection Compliance for Enterprise Security Requirements? Lets Checkout #DataProtectionCompliance #DataProtection #DataSecurityCompliance #CloudSecurity #CloudCodes bit.ly/2Ycq7sc

#DataSecurityCompliance #CybersecurityRegulations #PrivacyLaws #GDPR #HIPAA #CCPA #DataProtection #DataBreachResponse #InformationSecurity #RegulatoryCompliance #DataPrivacy #PII #RiskAssessment #ComplianceFramework #DataEncryption #CyberInsurance #DataRetention #DataHandling
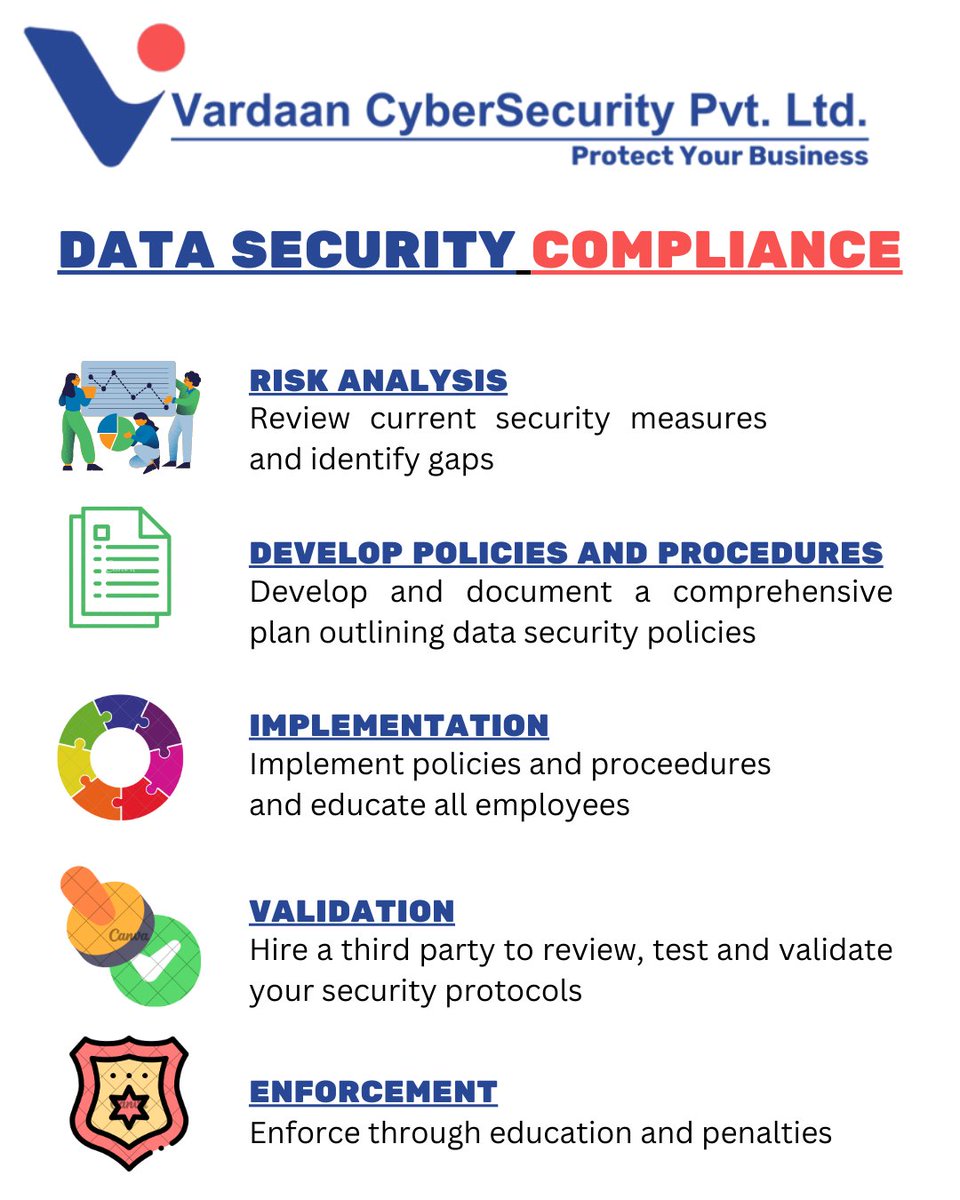
Mastering Data Management: The Key to Enhancing Data Security and Compliance Learn how mastering data management drives security and compliance: enfusesolution.wordpress.com/2025/09/08/mas… #DataManagementSolutions #DataSecurityCompliance #MasterDataManagement #DataCompliance #EnFuseSolutions
enfusesolution.wordpress.com
Mastering Data Management: The Key to Enhancing Data Security and Compliance
In today’s data-driven landscape, effective data management has become a crucial element for organizations striving to protect sensitive information, maintain regulatory compliance, and build trust…
What is New with PCI DSS 4.0? youtu.be/9_27kQrt7No?fe… via @YouTube #datasecurity #datasecuritycompliance #compliance #fortanixsolutions #pcidss #regulatorycompliance
youtube.com
YouTube
What is New with PCI DSS 4.0?
Product update! Nightfall’s new console includes a violations dashboard with an intuitive & elegant design that lets you view data security risk over time with robust filters. Here's your chance to see it in action: hubs.li/Q01hw1VV0 #saassecurity #datasecuritycompliance
Attending the Gartner Security & Risk Management Summit? Let’s meet and talk SaaS security! #GartnerSec #infosec #datasecuritycompliance hubs.li/Q01clPrb0
Data Security Matters: Ensuring Protection with Effective Management Solutions Protect your business by implementing best practices for data security and compliance; read more here: lite.evernote.com/note/a80307e5-… #DataSecuritySolutions #DataSecurityCompliance #EnFuseSolutions
Maintain comprehensive audit trails to track database activities and ensure accountability. Learn how to monitor changes, detect unauthorized access, and meet compliance requirements effectively. bit.ly/4njfmNy #AuditTrails #Compliance #DatabaseSecurity

Without full awareness, gaps in security multiply. True data privacy compliance means treating every device, file, and leftover asset as a possible vulnerability that must be managed.
6.Data Access and Usage control :データへの不正なアクセス、改ざん、利用等を防止するためのアクセス制限・利用制限が適切に運用する 7.Complience : 法令等に違反する行為をしない
Do you have a plan for fast data breach notifications? It's a key GDPR requirement. Stay ahead of Supervising Authorities (SAs) and their powerful investigative reach. Read about the consequences of non-compliance: ow.ly/hx0430sQNN1

2/4🌐 GDPR and global rules demand a mature approach to data handling, user protection and incident readiness. Clear processes, proactive governance and compliance-aligned operations help maintain trust and give companies the foundation to scale securely.
The key to GDPR? Encryption and constant testing. Your computing infrastructure must be built for compliance. We break down the technical requirements. See the checklist for data security: bit.ly/4kWf3s6

📑 Compliance Management Ensuring security processes align with regulations and standards—critical in an era shaped by privacy laws like the DPDP Act. In a fast-changing digital landscape, a strong SOC isn’t optional—it’s essential for trust, compliance, and business continuity.

These rules emphasize robust data security, with a Security Operations Centre (SOC) being a critical component for compliance, a topic of significant discussion at events like the Bengaluru Tech Summit. #BengaluruTechSummit #DPDPAct #DPDPrules #SecurityOperationCentre

LinkedIn Article on Key Compliance Challenges and Action Plan for Organizations under DPDPA linkedin.com/feed/update/ur… #DPDPA #DataProtection #riskpro #dataprotectionandprivacy

Navigating Cloud Compliance in the Digital Age Using the cloud without a compliance plan is like driving without brakes. Think: GDPR, HIPAA, PCI DSS, FedRAMP, ISO 27001. ✅ Audit regularly ✅ Encrypt data in transit + at rest ✅ Limit access & train your team Compliance is a…
Don't get caught off guard by data regulations! 🚨 Our latest guide helps your business navigate the complex world of data privacy, explaining key legal requirements and best practices. youtu.be/iGJJDm54RB0 #ComplianceTips #DataSecurity #espprojects

Compliance is more than just checking boxes, it's a strategic necessity that protects your revenue and reputation. But manual compliance efforts are slow, expensive, and a massive drain on your IT team's resources. We change the game by embedding security and compliance into…
Day 29 #100DaysOfCyberSecurity Today, I focused on the key steps to ensure compliance with the General Data Protection Regulation (GDPR). @ireteeh @_DeejustDee @elormkdaniel @TemitopeSobulo



Day 28 #100DaysOfCyberSecurity Today, I covered the areas an organization should focus on to prepare effectively for the GDPR. @ireteeh @_DeejustDee @TemitopeSobulo @elormkdaniel


Effective #DataCompliance starts with strategic #TechPlanning. Early integration of SSO and log bus systems reduces risks, cuts costs, and streamlines audits. Build a robust compliance framework for sustainable growth. See how this suits your business ⤵️ ow.ly/MY2z50Xp74U

Effective #DataCompliance starts with strategic #TechPlanning. Early integration of SSO and log bus systems reduces risks, cuts costs, and streamlines audits. Build a robust compliance framework for sustainable growth. See how this suits your business ⤵️ ow.ly/MY2z50Xp74U

DOJ Data Security Program compliance: Key considerations for organizations jdsupra.com/legalnews/doj-…
DOJ Data Security Program compliance: Key considerations for organizations jdsupra.com/legalnews/doj-…
DOJ Data Security Program compliance: Key considerations for organizations jdsupra.com/legalnews/doj-…
DOJ Data Security Program compliance: Key considerations for organizations jdsupra.com/legalnews/doj-… | by @DLA_Piper
DOJ Data Security Program compliance: Key considerations for organizations jdsupra.com/legalnews/doj-… | by @DLA_Piper
What is the Need for Data Protection Compliance for Enterprise Security Requirements? Lets Checkout #DataProtectionCompliance #DataProtection #DataSecurityCompliance #CloudSecurity #CloudCodes bit.ly/2Ycq7sc

Investment in #DataProtection regulations & #DataPrivacy policies have become very crucial as the cost of a data breach is much greater–in both tangible & intangible terms. Its very important for the organisation to have the required #DataSecurityCompliance & policies in place.

Prevent data disasters with DLP best practices- enforce access controls, monitor endpoints, encrypt everything, and automate backups. It’s not just protection—it’s precision. shorturl.at/Nytwd #DataLossPrevention #DataSecurityCompliance #DataProtection #DLPTools

Something went wrong.
Something went wrong.
United States Trends
- 1. Cloudflare 214K posts
- 2. Gemini 3 26.1K posts
- 3. #AcousticPianoCollection 1,212 posts
- 4. Olivia Dean 4,145 posts
- 5. Piggy 57.3K posts
- 6. Saudi 120K posts
- 7. La Chona 1,279 posts
- 8. Salman 32.8K posts
- 9. Taco Tuesday 14.8K posts
- 10. CAIR 24.3K posts
- 11. #LaSayoSeQuedóGuindando N/A
- 12. #tuesdayvibe 3,163 posts
- 13. #ONEPIECE1166 4,497 posts
- 14. Good Tuesday 35.8K posts
- 15. Sam Leavitt N/A
- 16. Anthropic 8,488 posts
- 17. Jamal Khashoggi 1,995 posts
- 18. Passan 1,030 posts
- 19. Garling 2,370 posts
- 20. Mark Epstein 26.5K posts

























