#gdatatechblog ผลการค้นหา
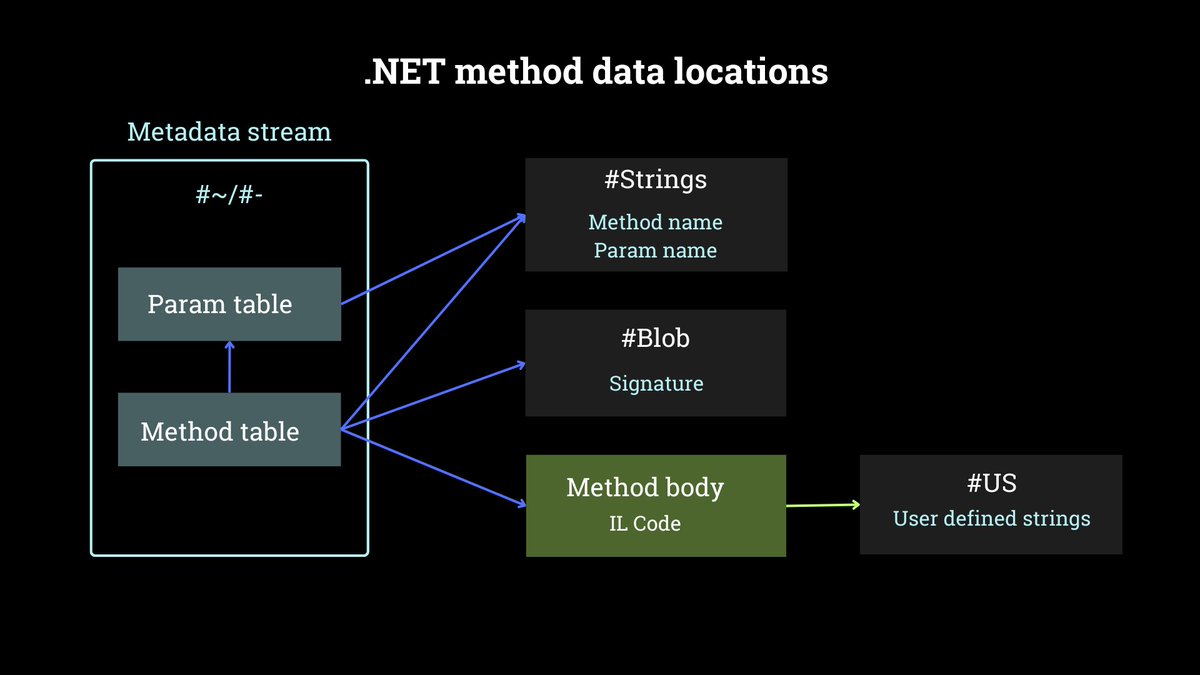
How to use knowledge about .NET structures and streams for writing better .NET Yara signatures. E.g. IL code patterns, method signature definitions, GUIDs, compressed length. #100DaysOfYara #GDATATechblog @GDATA #GDATA gdatasoftware.com/blog/2025/04/3…
🔍New Blog: JustAskJacky -- AI brings back classical trojan horse malware 🔗gdatasoftware.com/blog/2025/08/3… #GDATA @GDATA #GDATATechblog
Blog post: "PE trick explained: Telling 32 and 64 bit apart with naked eye" 👀 🦔 (based on question by @living_pirate) gdatasoftware.com/blog/pebitness… #GDATATechblog #GDATA @GDATA #PETrick #PEBitness
Some threat actors are bold enough to submit their malware as false positive to antivirus companies. This also happened with AppSuite PDF Editor. Our technical deep-dive is out 📝 gdatasoftware.com/blog/2025/08/3… #GDATA #GDATATechblog #AppSuite
Ever wanted to know how malware names are created and why they are such a mess? I wrote an article about it. #MalwareNames #GDATATechblog @GDATA gdatasoftware.com/blog/malware-f…
#RisePro stealer targets Github users in "gitgub" campaign #GDATATechblog gdatasoftware.com/blog/2024/03/3…
A colleague and me wrote an article about EvilConwi -- signed ConnectWise remote access software being abused as malware @GDATA #GDATATechblog gdatasoftware.com/blog/2025/06/3…
New blog article: Sandbox scores are not an antivirus replacement #GDATATechblog @GDATA gdatasoftware.com/blog/2024/09/3…
New article: "The real reason why malware detection is hard—and underestimated" If you think an AI with a 98% malware detection rate and 1% false positive rate is splendid, this might change your mind. #GDATATechblog @GDATA gdatasoftware.com/blog/2022/06/3…
New article: "Identifying system file manipulation" #GDATATechBlog #FileManipulation @GDATA gdatasoftware.com/blog/2022/09/3…
Blog: Printer company provided infected printer software for half a year. ➡️ XRed backdoor ➡️ SnipVex virus Initially reported by Youtuber of "Serial Hobbyism" #GDATATechblog #GDATA @GDATA gdatasoftware.com/blog/2025/05/3…
New article on BadSpace backdoor by @Loeweanva and me #GDATATechblog @GDATA #BadSpace gdatasoftware.com/blog/2024/06/3…
My colleagues at @GDataPH have written an article about Turla #GDATATechblog @GDATA #Turla gdatasoftware.com/blog/2024/07/3…
Dear companies. Please, make it easy for researchers to contact you about security and malware issues ☣️. React in time. Every hour counts.⌛️ #GDATA #GDATATechblog 📝 gdatasoftware.com/blog/2020/02/3…
#Ginzo stealer analysis #GDATA #GDATATechblog gdatasoftware.com/blog/2022/03/g…
New article: Analysis of JPHP (PHP for Java VM) malware named IceRat. ➡️ how to deobfuscate JPHP ➡️ IceRat IOCs #GDATATechblog @GDATA #JPHP gdatasoftware.com/blog/icerat-ev…
Steam game BlockBlasters downloads malware written by Arvin Tan #GDATATechblog @GDATA #GDATA gdatasoftware.com/blog/2025/09/3…
New Blog: Deobfuscating BBTok loader, ConfuserEx variant with dnlib, Python and PowerShell by @marius_benthin and me #GDATATechblog #GDATA @GDATA #BBTok gdatasoftware.com/blog/2024/09/3…
Opinion: More layers in malware campaigns are not a sign of sophistication #GDATATechblog @GDATA gdatasoftware.com/blog/2024/08/3…
I wrote an article about SectopRAT which was discovered by @malwrhunterteam #gdatatechblog #rat #SectopRAT gdatasoftware.com/blog/2019/11/3…
Steam game BlockBlasters downloads malware written by Arvin Tan #GDATATechblog @GDATA #GDATA gdatasoftware.com/blog/2025/09/3…
Some threat actors are bold enough to submit their malware as false positive to antivirus companies. This also happened with AppSuite PDF Editor. Our technical deep-dive is out 📝 gdatasoftware.com/blog/2025/08/3… #GDATA #GDATATechblog #AppSuite
🔍New Blog: JustAskJacky -- AI brings back classical trojan horse malware 🔗gdatasoftware.com/blog/2025/08/3… #GDATA @GDATA #GDATATechblog
A colleague and me wrote an article about EvilConwi -- signed ConnectWise remote access software being abused as malware @GDATA #GDATATechblog gdatasoftware.com/blog/2025/06/3…
Blog: Printer company provided infected printer software for half a year. ➡️ XRed backdoor ➡️ SnipVex virus Initially reported by Youtuber of "Serial Hobbyism" #GDATATechblog #GDATA @GDATA gdatasoftware.com/blog/2025/05/3…
How to use knowledge about .NET structures and streams for writing better .NET Yara signatures. E.g. IL code patterns, method signature definitions, GUIDs, compressed length. #100DaysOfYara #GDATATechblog @GDATA #GDATA gdatasoftware.com/blog/2025/04/3…

Karsten Hahn and I took a closer look at the latest #BBTok .NET loaders. In my first article on the #GDATATechblog we describe how to deobfuscate Trammy.dll and share new details about the BBTok infection chain. gdatasoftware.com/blog/2024/09/3… @struppigel @GDATA #GDATA
New Blog: Deobfuscating BBTok loader, ConfuserEx variant with dnlib, Python and PowerShell by @marius_benthin and me #GDATATechblog #GDATA @GDATA #BBTok gdatasoftware.com/blog/2024/09/3…
New blog article: Sandbox scores are not an antivirus replacement #GDATATechblog @GDATA gdatasoftware.com/blog/2024/09/3…
Opinion: More layers in malware campaigns are not a sign of sophistication #GDATATechblog @GDATA gdatasoftware.com/blog/2024/08/3…
My colleague wrote about #Ailurophile stealer. It puts stolen files and its own malicious PHP scripts into a virtual file system. #GDATATechblog @GDATA gdatasoftware.com/blog/2024/08/3…
My colleagues at @GDataPH have written an article about Turla #GDATATechblog @GDATA #Turla gdatasoftware.com/blog/2024/07/3…
New article on BadSpace backdoor by @Loeweanva and me #GDATATechblog @GDATA #BadSpace gdatasoftware.com/blog/2024/06/3…
#RisePro stealer targets Github users in "gitgub" campaign #GDATATechblog gdatasoftware.com/blog/2024/03/3…
RT MalwareTipscom: RT @struppigel: New article: "Identifying system file manipulation" #GDATATechBlog #FileManipulation @GDATA gdatasoftware.com/blog/2022/09/3…
New article: "Identifying system file manipulation" #GDATATechBlog #FileManipulation @GDATA gdatasoftware.com/blog/2022/09/3…
New article: "The real reason why malware detection is hard—and underestimated" If you think an AI with a 98% malware detection rate and 1% false positive rate is splendid, this might change your mind. #GDATATechblog @GDATA gdatasoftware.com/blog/2022/06/3…
#Ginzo stealer analysis #GDATA #GDATATechblog gdatasoftware.com/blog/2022/03/g…
New article: Allcome clipbanker analysis and config extraction ➡️first seen reported by @3xp0rtblog #Allcome #clipbanker #GDATATechblog @GDATA gdatasoftware.com/blog/2022/02/3…
New article: Hashing for (malware) samples. 🦔#⃣ Including icon hashes, call graph hashes, human readable hash, rich header hash, import hashes ... #GDATATechblog @GDATA #hashing #hash #malware gdatasoftware.com/blog/2021/09/a…
"Paliz, the PowerShell downloader in a ZIP and beyond" My first article for #GDataTechblog. Starting with something small. 😁 gdatasoftware.com/blog/2019/04/3…

Blog post: "PE trick explained: Telling 32 and 64 bit apart with naked eye" 👀 🦔 (based on question by @living_pirate) gdatasoftware.com/blog/pebitness… #GDATATechblog #GDATA @GDATA #PETrick #PEBitness

How to use knowledge about .NET structures and streams for writing better .NET Yara signatures. E.g. IL code patterns, method signature definitions, GUIDs, compressed length. #100DaysOfYara #GDATATechblog @GDATA #GDATA gdatasoftware.com/blog/2025/04/3…

Something went wrong.
Something went wrong.
United States Trends
- 1. Austin Reaves 43.3K posts
- 2. #LakeShow 2,863 posts
- 3. Trey Yesavage 36.2K posts
- 4. Jake LaRavia 5,153 posts
- 5. #LoveIsBlind 4,255 posts
- 6. Blue Jays 60.8K posts
- 7. jungwoo 98.6K posts
- 8. Rudy 8,971 posts
- 9. doyoung 76.2K posts
- 10. #AEWDynamite 22.5K posts
- 11. #Lakers 1,039 posts
- 12. Jeremy Lin N/A
- 13. Snell 13.5K posts
- 14. Pelicans 4,294 posts
- 15. Devin Booker 1,177 posts
- 16. Happy Birthday Kat N/A
- 17. #WorldSeries 65.8K posts
- 18. CALL 12 3,227 posts
- 19. Anthony Davis 4,142 posts
- 20. Wolves 63.1K posts



