#hashing 搜索结果
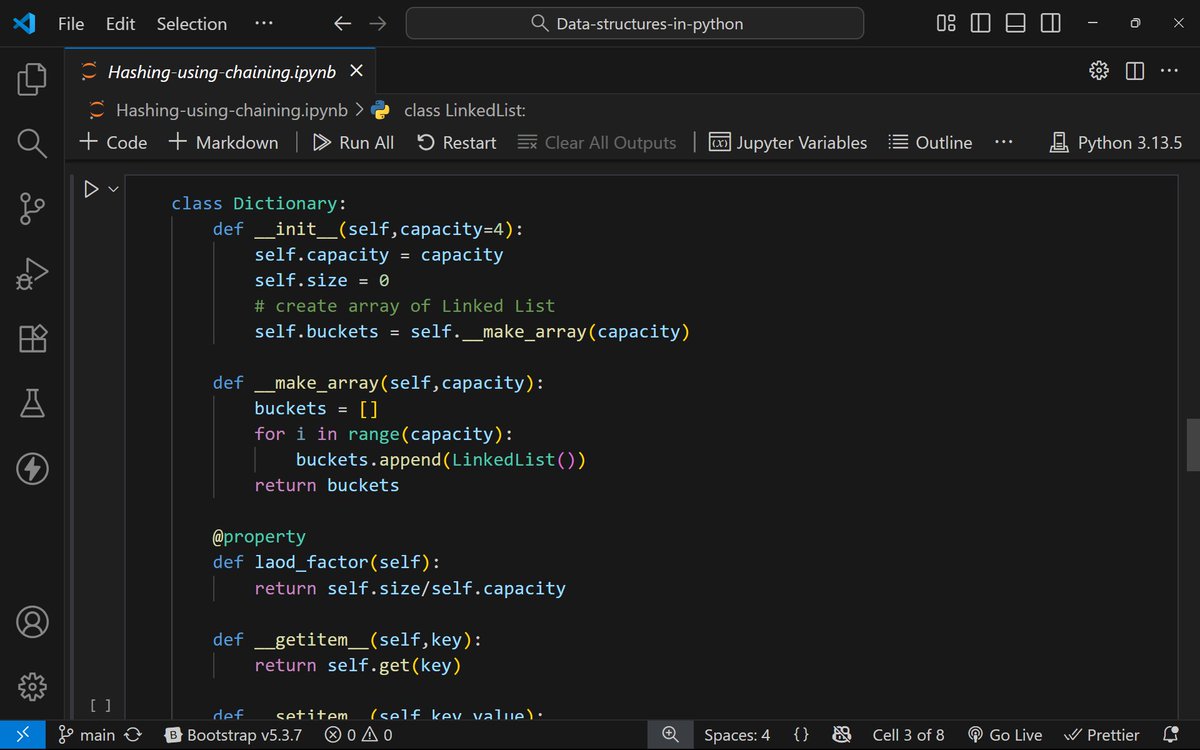
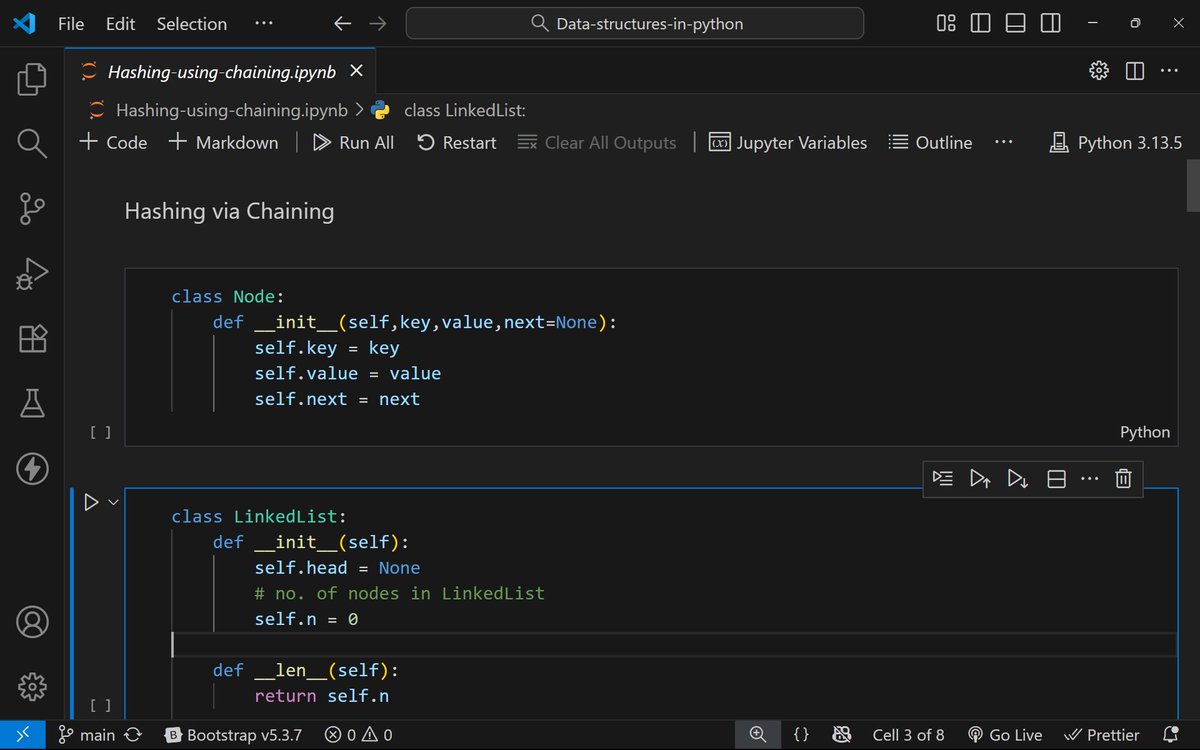
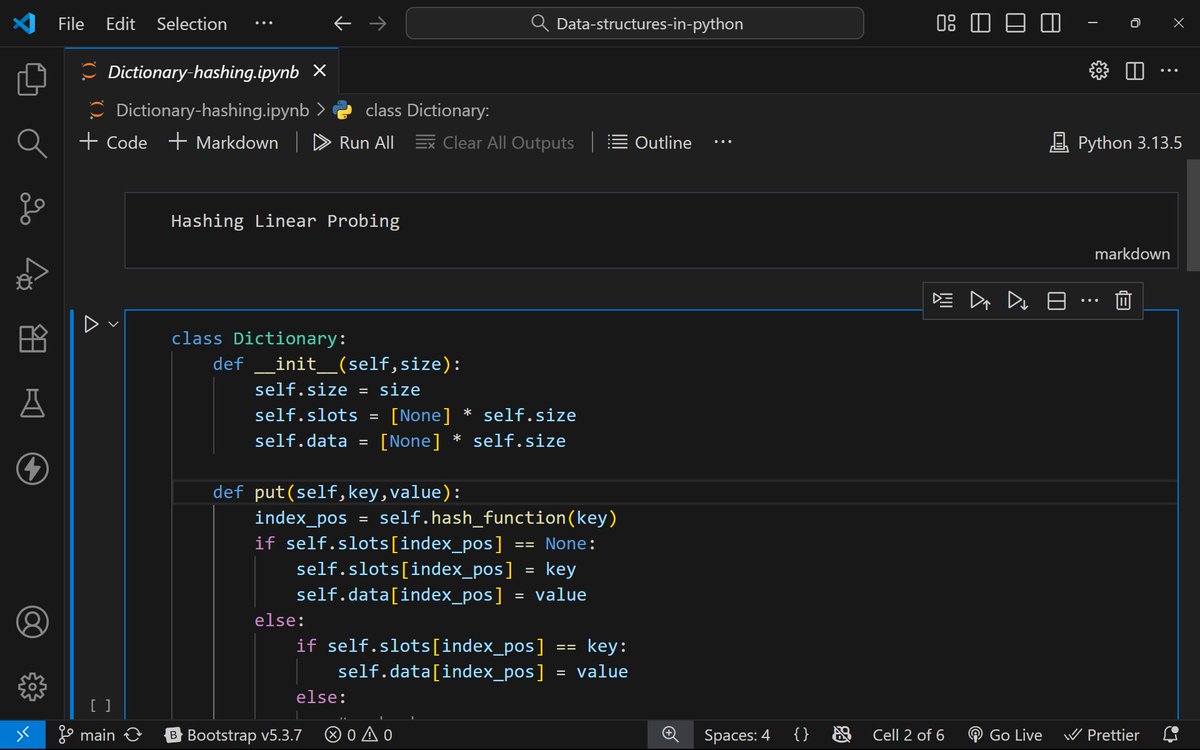
I finally understood hashing. Not just the theory — I built it. From collisions and chaining to linear & quadratic probing, rehashing, and load factors. I even coded my own Dictionary class in Python from scratch 🔥 Learning by building > reading. #DSA #Hashing #BuildInPublic
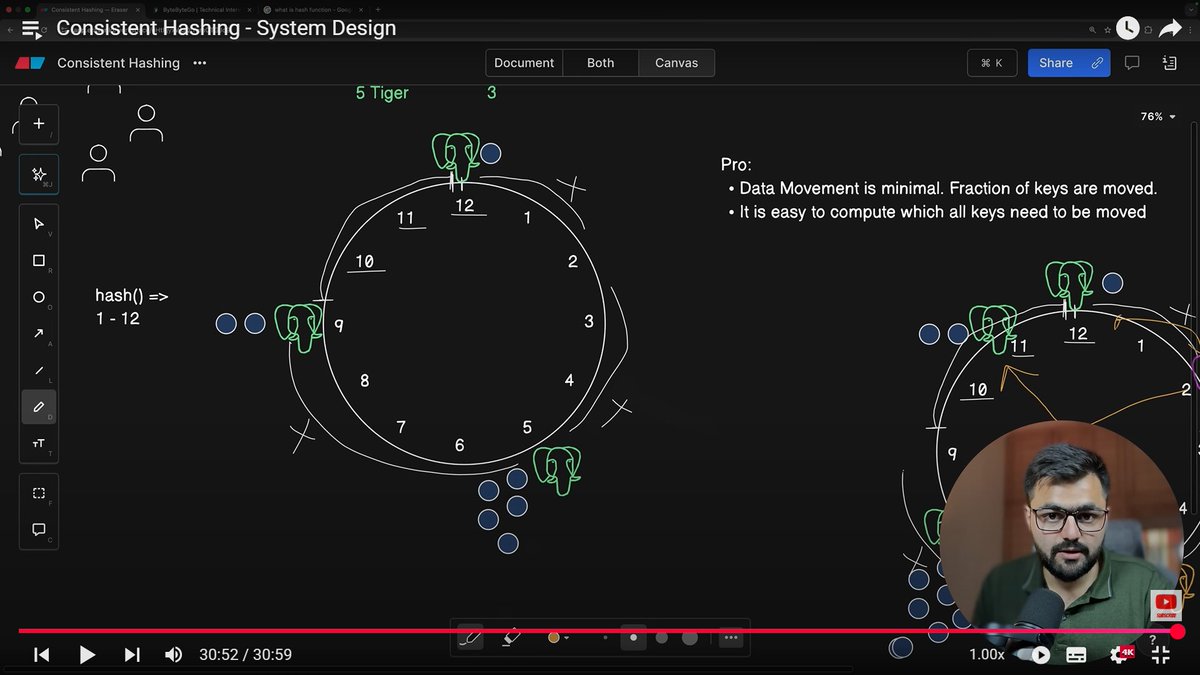
System Design - Part 7 (Consistent Hashing) by @piyushgarg_dev - What is Consistent Hashing? - Hash Space and Hash Ring #SystemDesign #Hashing
🔒 Don’t encrypt passwords — that’s bad practice. Encryption can be undone. Hashing can’t. Hashing is one-way, like 7 ÷ 3 = 2 R1. Could’ve been 13 ÷ 6 too — same result, different input. Hash passwords. Don’t encrypt them. #CyberSecurity #Infosec #Hashing #TechTips
ما هو ال Encoding وكيف يعمل free4arab.net/courses/web-ap… شرح بالعربي لــ Encryption free4arab.net/courses/cyber-… ما هو ال Hashing وكيف يعمل free4arab.net/courses/web-ap… #Encoding #Encryption #hashing
Cryptography for Hackers redteamrecipe.com/cryptography-f… from AES and RSA to Bcrypt and PGP. Dive into the technical details of how these methods secure your data. Tools: gchq.github.io dcode.fr/en #hashing #encryption #redteam #cryptography

Day 43 ✅ | #gfg160 Challenge @geeksforgeeks Solved → 🔢 Count Pairs with Given Sum 🧠 Method Used: Hash Map (Frequency Count) 📈 Time: O(n) | 📦 Space: O(n) 👉 More in ALT → #DSA #Hashing #PairsWithSum #Python #gfg160 #geekstreak2025 #codenameanastasia
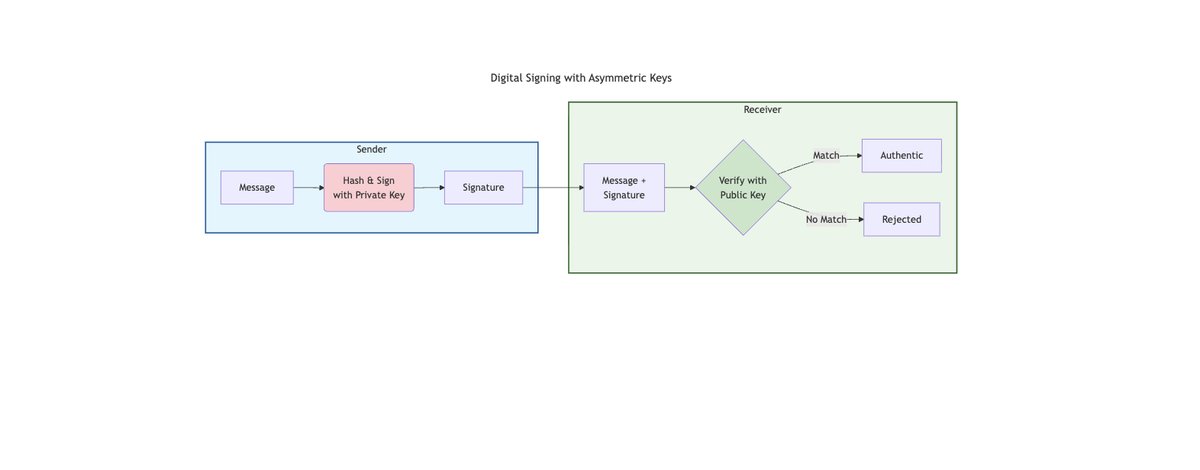
How hashing algorithms (e.g., SHA-256) and asymmetric keys can be used for message signing #DigitalTransformation #DTI #Hashing #Asymmetric #Encryption #AsymmetricEncryption #Asymmetric_Encryption #DigitalSignatures Message signing using asymmetric keys linkedin.com/pulse/message-…
🧵 Imagine you’re in a huge library. Thousands of books around you, but you can find the exact one you need in seconds. That’s the power of hash functions in data structures! 🚀 #Hashing #DataStructures

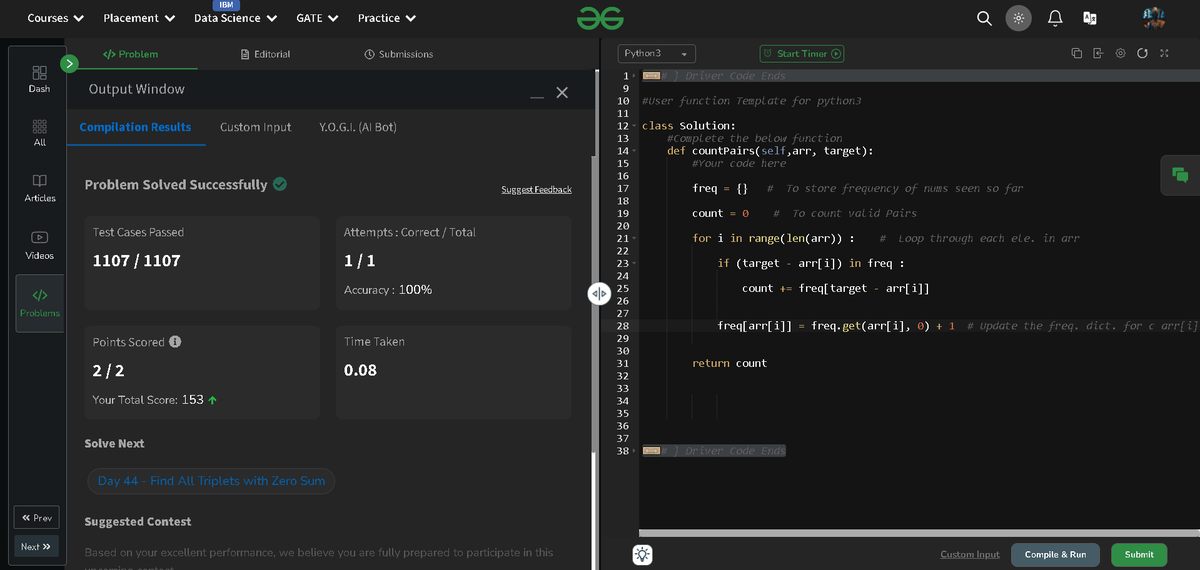
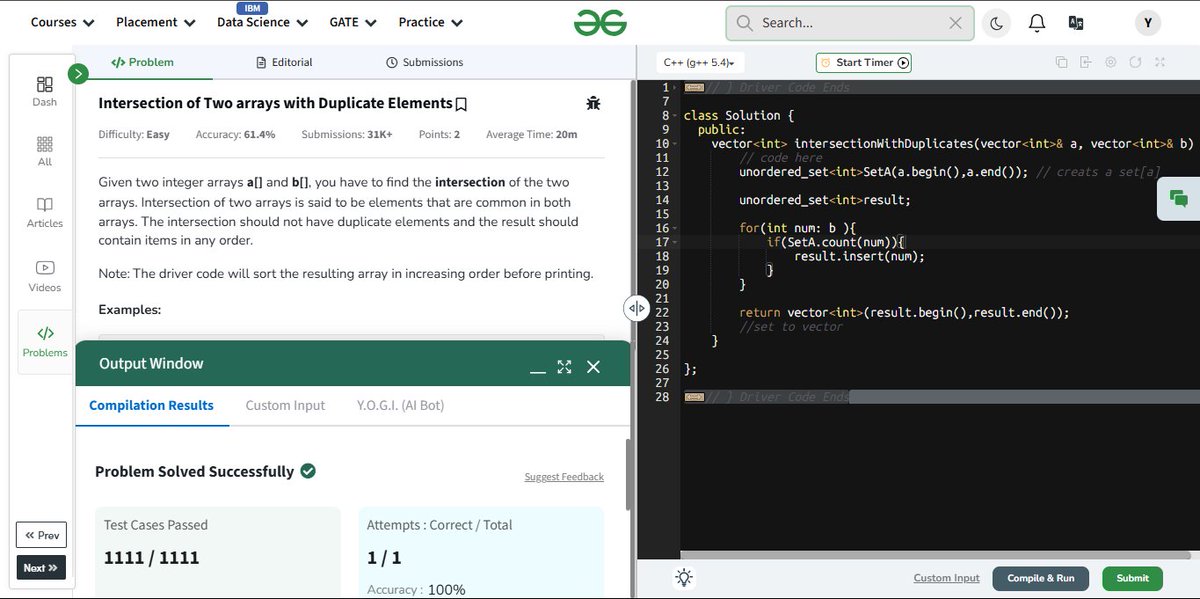
🚀 #GFG160 – Day 41: Intersection with Duplicates! 🔁➕ Solved the Intersection of Two Arrays with Duplicate Elements problem today ✔️ Intersection of Two Arrays with Duplicates #Hashing #ArrayProblems #GeeksforGeeks #100DaysOfCode #geekstreak2025 @geeksforgeeks
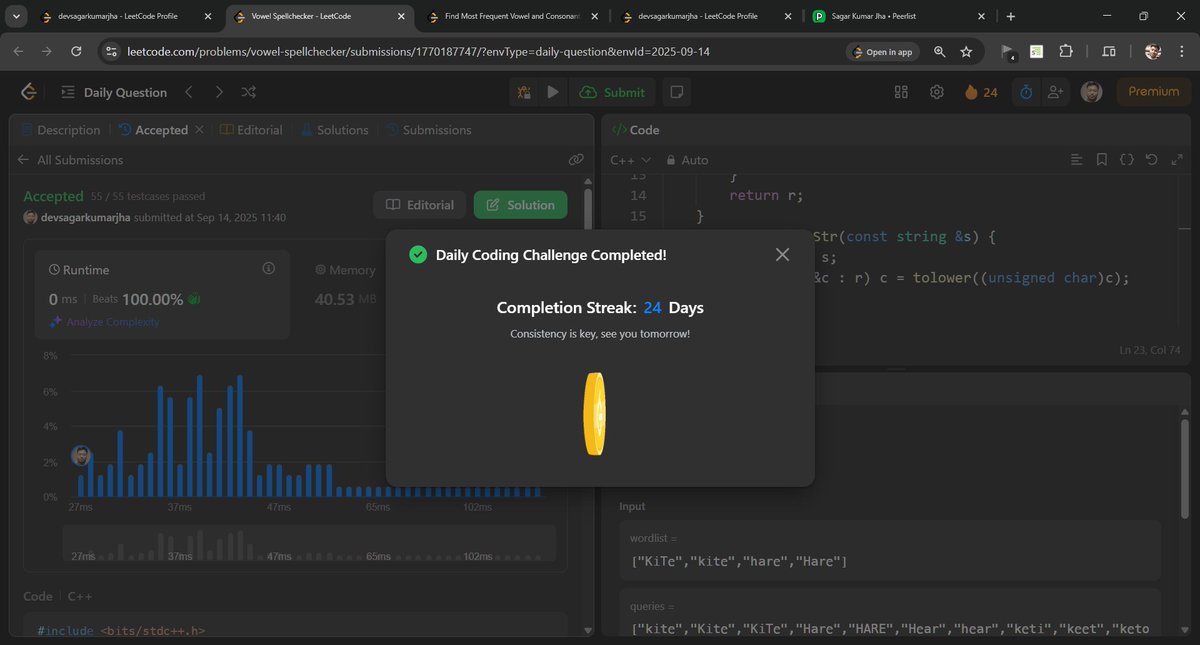
Day 24 Solved✅LC #POTD 966 (Medium) 👉 3-tier match: exact → lowercase → vowel-masked 👉 Use set for exact, maps for lowercase & vowel forms 👉 Query = check in order ⏱ O(L·(N+Q)), neat hashing trick! 🔗 leetcode.com/problems/vowel… #LeetCode #Hashing #Strings #DSA #100DaysOfCode
Just hashing passwords isn’t enough. Add salt to the mix! Salted hashing defends against rainbow table attacks by adding randomness to each password before hashing. Even if two users have the same password, their hashes will be different. #CyberSecurity #Hashing #WebSecurity

🌟 Day 63 of #geekstreak2024! Problem: Largest Subarray of 0's and 1's Hint: Replace all 0's with -1's. Use a hashmap to track prefix sums and their first occurrences. Update the result whenever the prefix sum is repeated. #gfg160 #Hashing #PrefixSum #DSA
Word of the Day: #Hashing Hashing turns any data into a unique digital fingerprint. This fingerprint: • can’t be reversed • doesn’t reveal the original data • changes entirely if you alter even 1 bit That’s why hashing powers blockchains, IPFS, security, and Web3. #Web3…
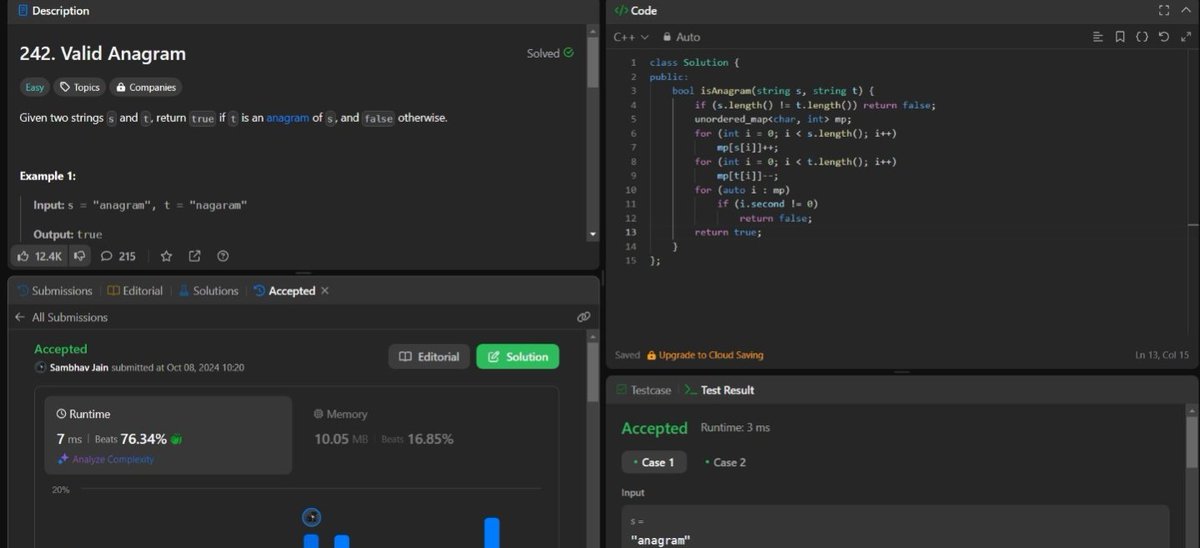
#Day421 of #500DaysOfDSA Topics and Learnings: #Hashing Problems Re-revised: 41. #LeetCode #242 : Valid Anagram Approach: Used Hashing to solve this Complexity Analysis: TC: O(N) SC: O(N)
#Şifreleme ve #Hashing: Dijital Güvenliğin İki Farklı Yüzü... Şifreleme gizlilik için çift yönlüdür, geri alınabilir. Hashing bütünlük için tek yönlüdür, verinin parmak izidir, geri alınamaz. #SiberTehdit #Güvenlik 👇👇👇 askweb.com.tr/sifreleme-ve-h…
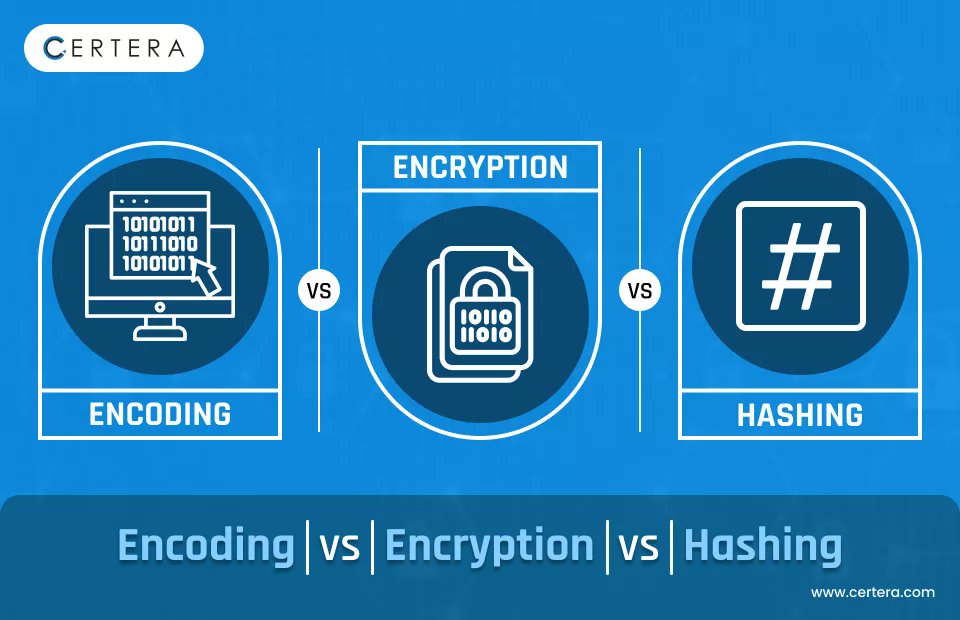
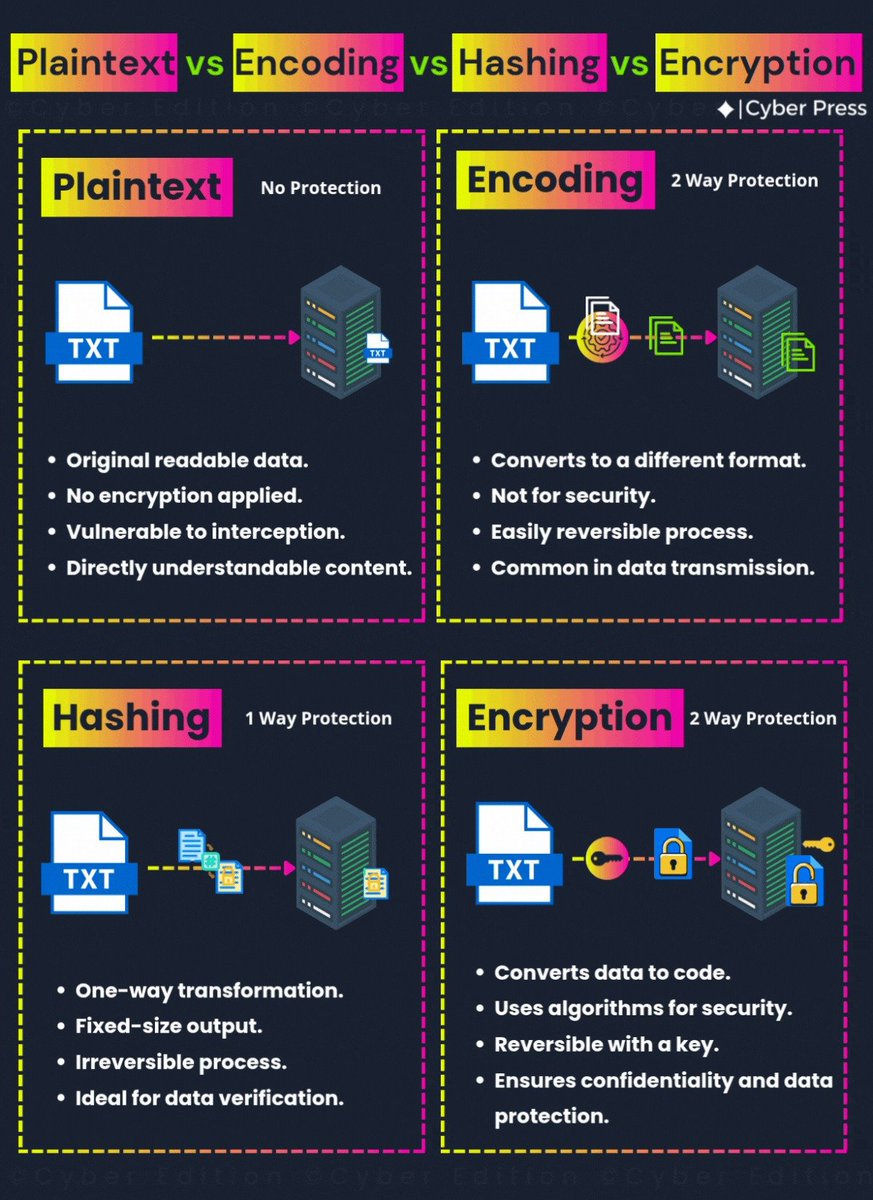
Encryption, encoding, and hashing all sound similar, but each has a unique function. Dive into this blog to understand how they protect your data! Full Article - tinyurl.com/encryption-enc… #encryption #Encoding #Hashing #CyberSecurity #DataProtection
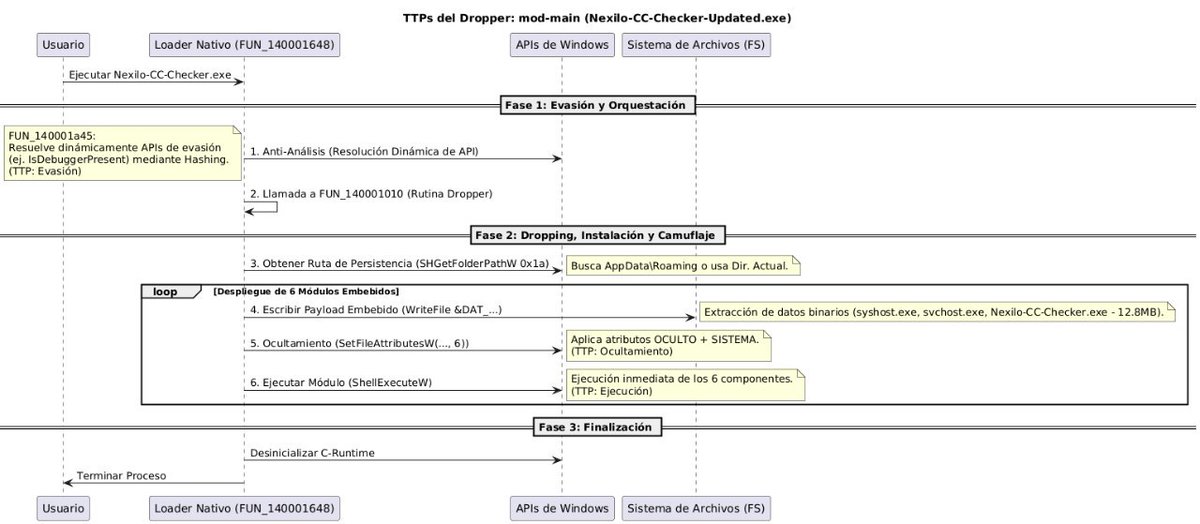
Un #dropper multi-etapa que descubrí en canales de programas #crackeados. Analicé cómo usa API #Hashing para evasión y despliega un #Clipper (roba cripto del portapapeles) y un #InfoStealer (roba info, screenshots, activa RDP). linkedin.com/posts/tty503_m… linkedin.com/posts/tty503_m…
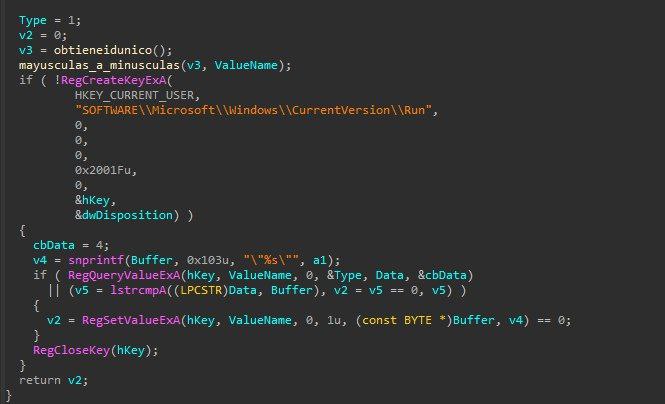
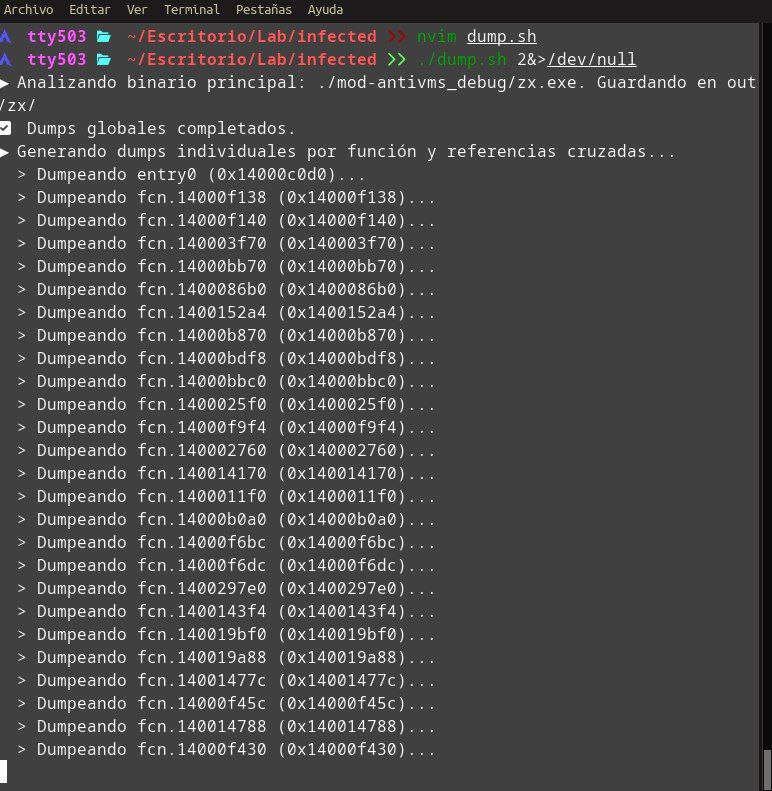
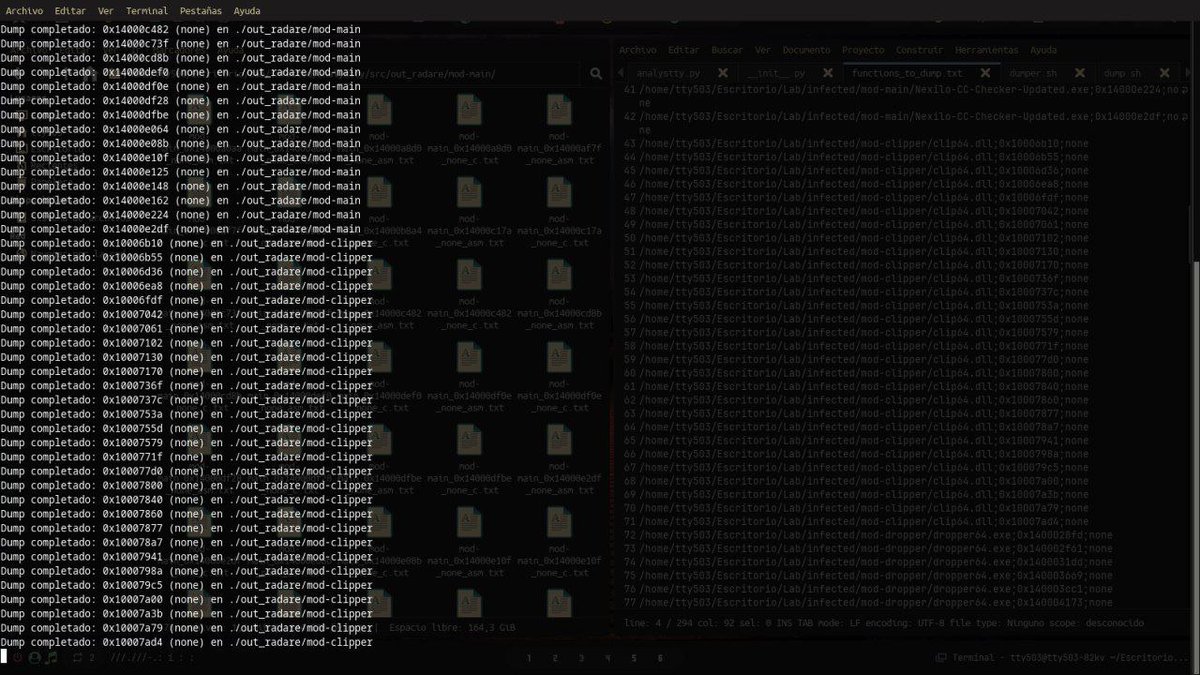
Los sistemas no guardan contraseñas: guardan su hash. Con técnicas como “salting” se añade un valor aleatorio que impide ataques por diccionario o tablas rainbow. Así, aunque roben la base de datos, tus credenciales siguen protegidas. #Seguridad #Hashing
Las contraseñas no se guardan en texto: se almacenan en forma de hash. Ni la empresa que te da acceso conoce tu contraseña real. Un atacante tampoco puede reconstruirla desde el hash. Es una defensa esencial en cualquier sistema moderno. #Seguridad #Hashing
Data turned to keys, Whispers of secrets secured, Fast paths to the truth. #Haiku #Hashing #CodePoetry #DevHaiku #CodingLife #TechHaiku #CodeArt #DeveloperWisdom #CodingPoetry #ProgrammersLife #HaikuOfCode
🌟 Day 227/∞ 🚀 Solved Longest Consecutive Sequence 🔗 💡 Used a HashSet to check starts of sequences and expand them efficiently. Time Complexity: O(n) | Space: O(n) ⚡ #LeetCode #DSA #Hashing #CodeEveryday #KeepCoding
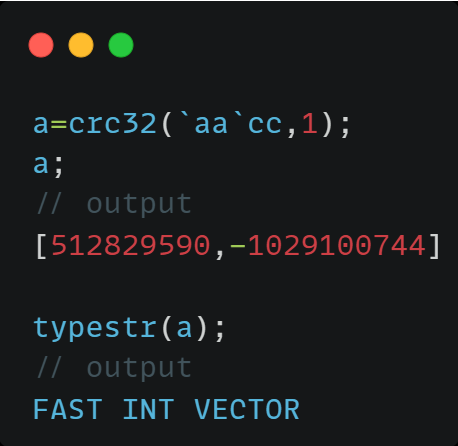
crc32(str) hashes strings via CRC32 algorithm, outputting an INT! 🔒 Optional initial checksum—useful for fast data integrity checks or string hashing. #DolphinDB #Hashing #DataIntegrity
youtube.com/shorts/DR7JBMl… #DSA #Hashing #DataStructures #Algorithms #CodingShorts #LearnToCode #ProgrammingBasics #TechShorts #AlgorithmTutorial #CodeNewbie #SoftwareEngineering
youtube.com
YouTube
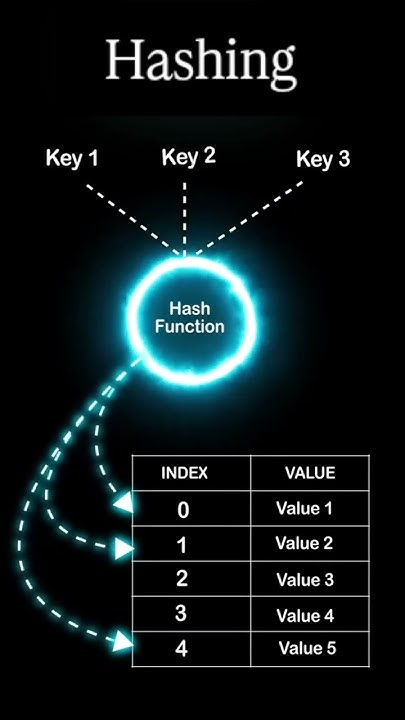
Hash function | DSA: How Hashing Works in Data Structures #Shorts...
Hashing hardware fuels the digital backbone. ⚡ Precision, power, and performance — all in every hash. #Tech #Hashing
🔒 Don’t encrypt passwords — that’s bad practice. Encryption can be undone. Hashing can’t. Hashing is one-way, like 7 ÷ 3 = 2 R1. Could’ve been 13 ÷ 6 too — same result, different input. Hash passwords. Don’t encrypt them. #CyberSecurity #Infosec #Hashing #TechTips
💻 Day 5 of my 10-Day DSA Challenge Learnt some hashing today — ◽ Mid-square ◽ Modulo division ◽ Folding hash Also tried a few two-pointer problems 🔁 Still more to cover, but getting there #DSA #Hashing #10DayChallenge
I finally understood hashing. Not just the theory — I built it. From collisions and chaining to linear & quadratic probing, rehashing, and load factors. I even coded my own Dictionary class in Python from scratch 🔥 Learning by building > reading. #DSA #Hashing #BuildInPublic



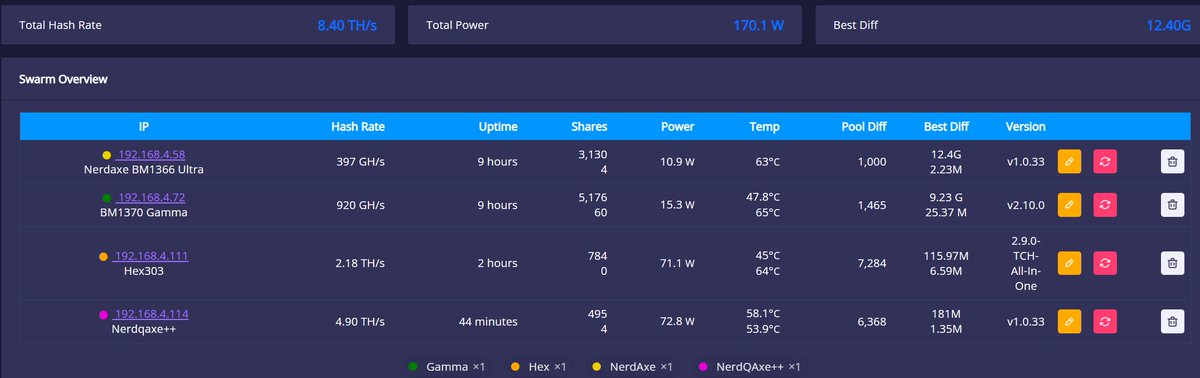
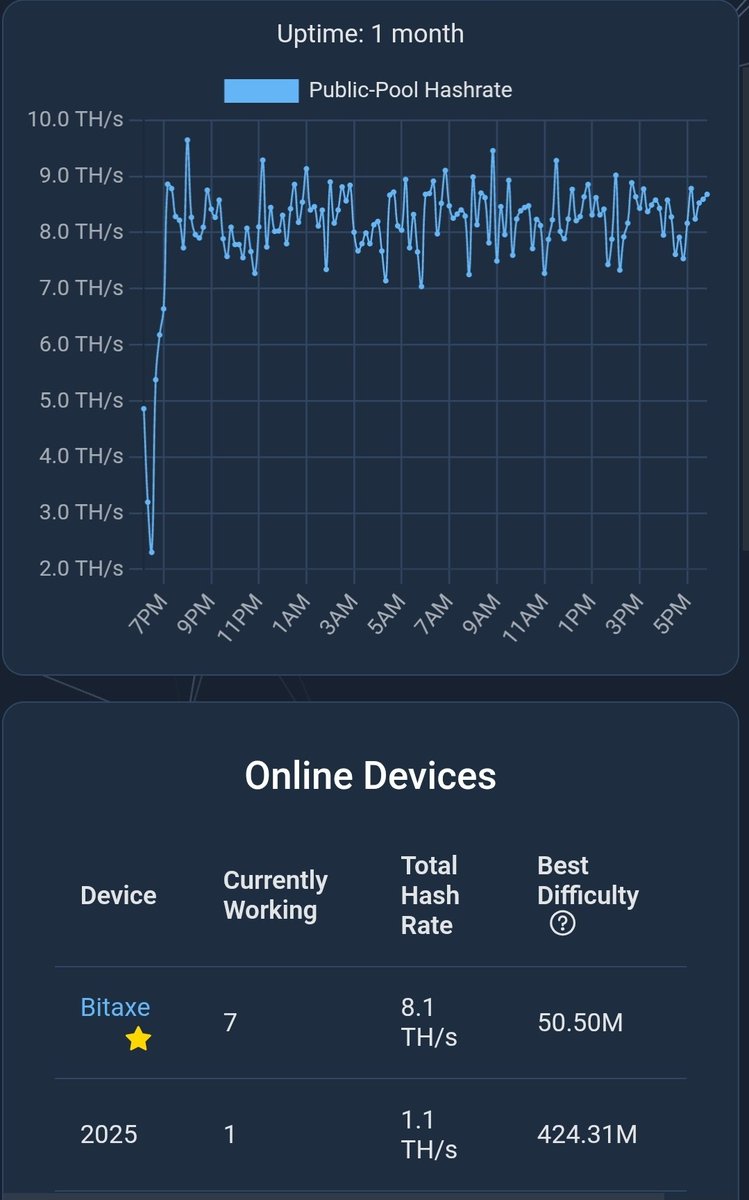
Well, well, well…. #nerdaxe from @BitronicsStore arrived today and already #hashing and waiting for my block ;D Gracias, chicos! Thank you guys!



ما هو ال Encoding وكيف يعمل free4arab.net/courses/web-ap… شرح بالعربي لــ Encryption free4arab.net/courses/cyber-… ما هو ال Hashing وكيف يعمل free4arab.net/courses/web-ap… #Encoding #Encryption #hashing

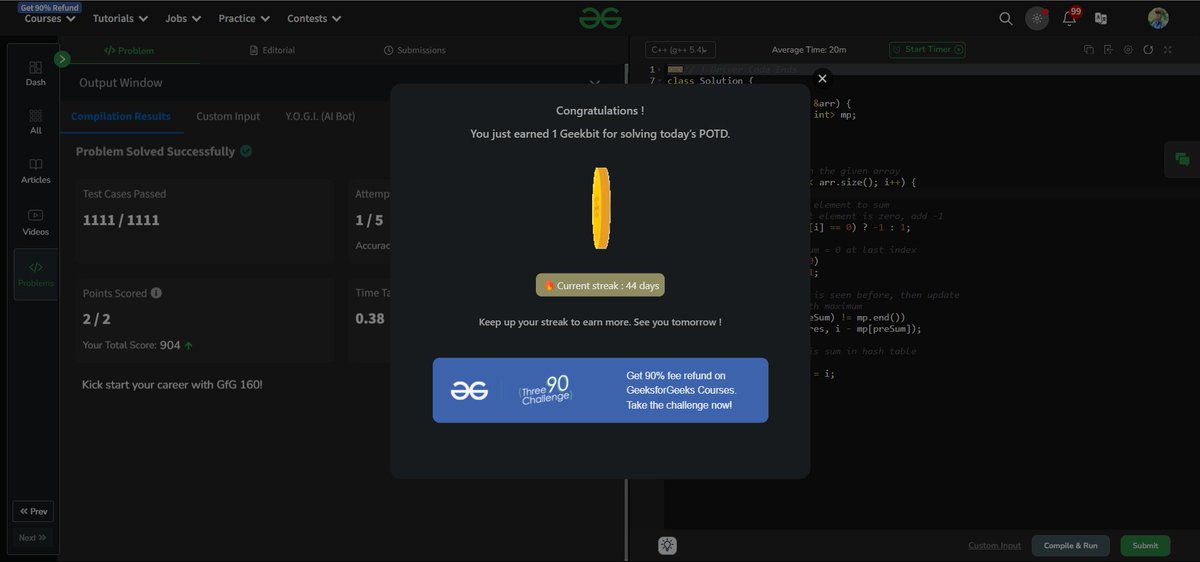
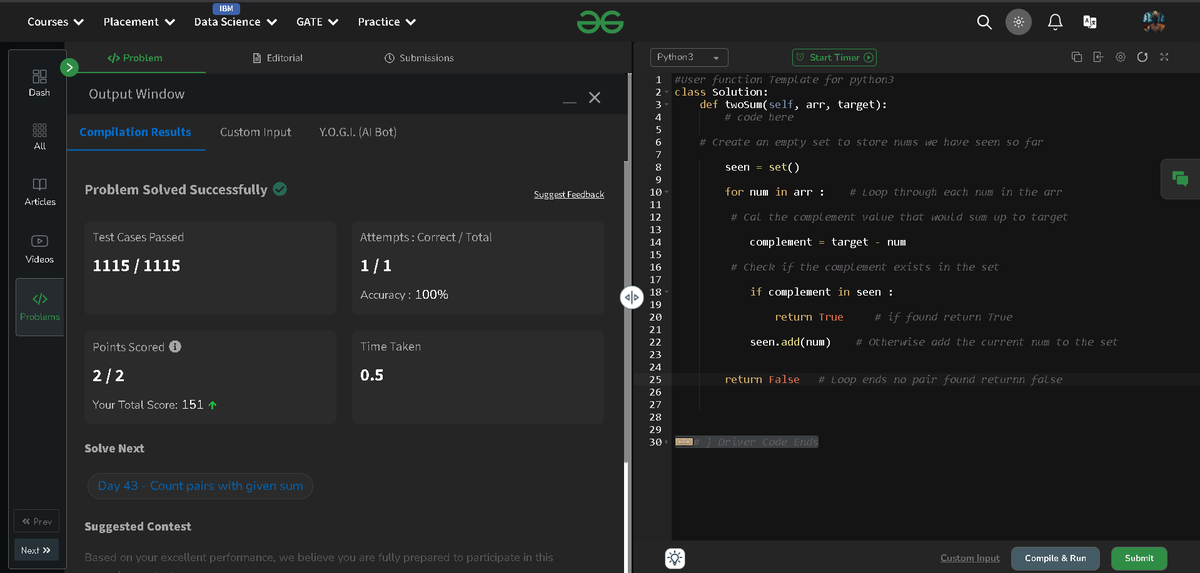
Day 43 ✅ | #gfg160 Challenge @geeksforgeeks Solved → 🔢 Count Pairs with Given Sum 🧠 Method Used: Hash Map (Frequency Count) 📈 Time: O(n) | 📦 Space: O(n) 👉 More in ALT → #DSA #Hashing #PairsWithSum #Python #gfg160 #geekstreak2025 #codenameanastasia

Day 42 ✅ | #gfg160 Challenge @geeksforgeeks Solved → 🧮 Two Sum – Pair with Given Sum 🧠Method Used:Hashing (Set) for efficient lookup 📈 Time: O(n) | 📦 Space: O(n) More in ALT → #DSA #Hashing #TwoSum #gfg160 #geekstreak2025 #LearnInPublic
How hashing algorithms (e.g., SHA-256) and asymmetric keys can be used for message signing #DigitalTransformation #DTI #Hashing #Asymmetric #Encryption #AsymmetricEncryption #Asymmetric_Encryption #DigitalSignatures Message signing using asymmetric keys linkedin.com/pulse/message-…

Day 24 of 30: Understanding #Hashing: 🔢 A cryptographic process that converts data into a fixed-size string of characters, used to secure data on the blockchain. It’s fundamental to blockchain security. #CryptoBasics #Blockchain
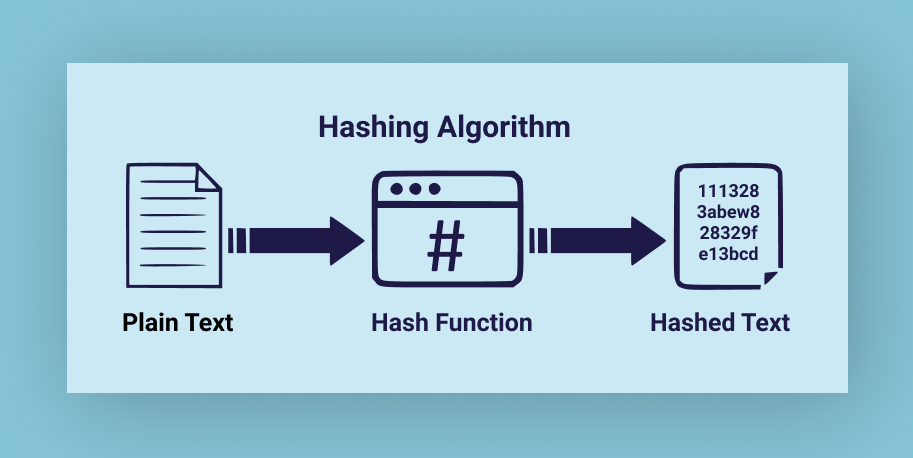
🧵 Imagine you’re in a huge library. Thousands of books around you, but you can find the exact one you need in seconds. That’s the power of hash functions in data structures! 🚀 #Hashing #DataStructures

🚀 #GFG160 – Day 41: Intersection with Duplicates! 🔁➕ Solved the Intersection of Two Arrays with Duplicate Elements problem today ✔️ Intersection of Two Arrays with Duplicates #Hashing #ArrayProblems #GeeksforGeeks #100DaysOfCode #geekstreak2025 @geeksforgeeks

System Design - Part 7 (Consistent Hashing) by @piyushgarg_dev - What is Consistent Hashing? - Hash Space and Hash Ring #SystemDesign #Hashing

Day 9 of #100DaysOfCode: 🗝️ Explored the world of Hashing today – diving into maps, collisions, and mastering the division rule. 🔍 Understanding the secrets of efficient data storage! 💻🔒 #Hashing #DataStructures #CodeLearning
Cryptography for Hackers redteamrecipe.com/cryptography-f… from AES and RSA to Bcrypt and PGP. Dive into the technical details of how these methods secure your data. Tools: gchq.github.io dcode.fr/en #hashing #encryption #redteam #cryptography

Something went wrong.
Something went wrong.
United States Trends
- 1. Thanksgiving 2.33M posts
- 2. Chiefs 64.4K posts
- 3. Mahomes 22.8K posts
- 4. George Pickens 9,296 posts
- 5. Post Malone 4,565 posts
- 6. Tony Romo 2,330 posts
- 7. Turpin 1,636 posts
- 8. Sarah Beckstrom 84K posts
- 9. #KCvsDAL 6,149 posts
- 10. McDuffie 4,345 posts
- 11. Lions 99.6K posts
- 12. Packers 73.1K posts
- 13. Rashee Rice 3,592 posts
- 14. Kelce 13.6K posts
- 15. Dan Campbell 8,273 posts
- 16. Clowney N/A
- 17. Hollywood Brown N/A
- 18. Andy Reid 1,454 posts
- 19. Dak Prescott 4,811 posts
- 20. Spags 1,239 posts