#pcisecureslcstandard search results
Invest in ISO standards today to protect your information, safeguard privacy, and ensure your business remains resilient, trusted, and operational, no matter what the future brings. ccsrisk.com/iso-newsletter…
Strengthen Compliance & Customer Confidence Our penetration testing framework aligns with global standards, giving you a clear roadmap to remedy any shortfalls Learn more at csscloud.co.uk/cyber-security… #IT #cybersecurity

Your customers trust you with their data and you should trust the partner handling it. SureCall follows the strictest compliance and security standards in the industry: 🔐 PCI-DSS 🔐 PIPEDA 🔐 Full privacy + data protection protocols Every agent is trained, monitored, and…

Need clarity on the MPoC standard? 📱 #PCISSC’s new Guidance Document gives examples, clarifications & guidance for stronger, safer mobile payments. 🔗 brnw.ch/21wXLYQ

🔐 Protege los datos más sensibles de tu empresa usando #LinuxServer con las mejores prácticas de seguridad. #infosec #ciberseguridadparatodos

@NIST PQC standards are accelerating — state and local governments shouldn’t wait. Align teams and contracts now so switches, routers, VPNs and app access adopt quantum-resistant cryptography: bit.ly/3JXwWcC

・PCI DSS(Payment Caed Industry Data Security Standard) クレジットカード会員データを安全に取り扱うためのクレジットカード業界のセキュリティ基準。
CVE-2025-11935 With TLS 1.3 pre-shared key (PSK) a malicious or faulty server could ignore the request for PFS (perfect forward secrecy) and the client would continue on with the co… cve.org/CVERecord?id=C…
セキュリティ評価「Secure SketCH」にPCI DSSの自己問診票作成を支援するテンプレート | IT Leaders it.impress.co.jp/articles/-/286…
Payment card data remains one of the top targets for cybercriminals. PCI DSS helps keep it safe, but understanding when it applies can be tricky. Our guide makes it simple: who needs PCI, what’s new in v4.0.1, and four practical tips to maintain compliance year-round. Read the…
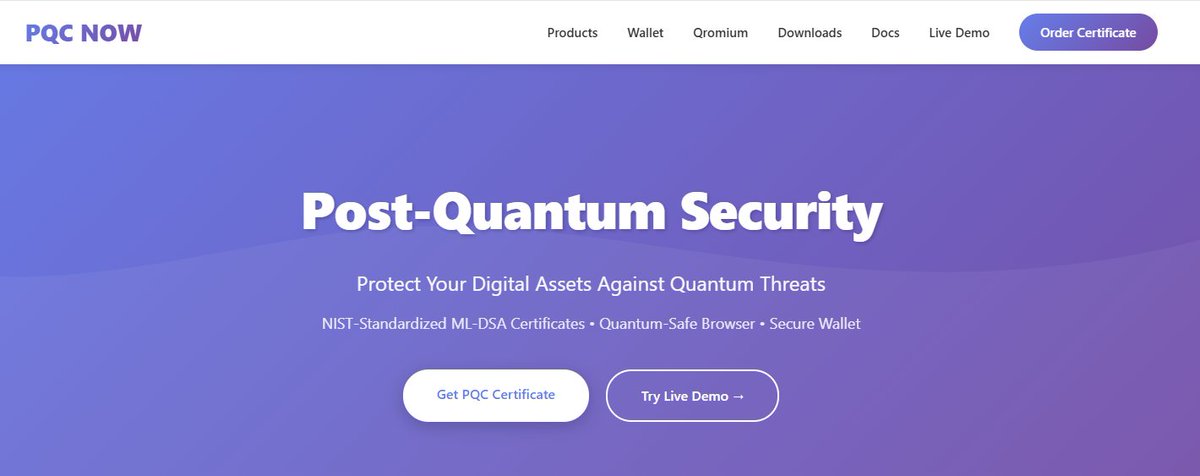
pqcnow.com PQC SSL Certificates Post-Quantum Cryptography for the Future of Web Security Quantum-Resistant SSL/TLS Certificates Protect your website against future quantum computer attacks with ML-DSA (NIST FIPS 204) post-quantum digital signatures.
pqcnow.com Protect Your Digital Assets Against #Quantum Threats NIST-Standardized ML-DSA Certificates • Quantum-Safe Browser • Secure Wallet
An #IT Security Health Check is your proactive defence against #cyber threats. By assessing networks, systems & applications from both external & internal perspectives, we uncover common & publicly known #vulnerabilities that criminals often exploit: csscloud.co.uk/cyber-security…

2️⃣ Standard: The HOW-TO. The specific technologies & configurations needed to meet the policy. Example: "Laptops must use BitLocker (Windows) or FileVault (macOS) with a minimum 256-bit key."
Here are the top 7 PCI DSS v4.0.1 Requirements to Prioritize in 2025: securitymetrics.com/blog/top-7-pci… #cybersecurity #PCIDSS #securitymetrics

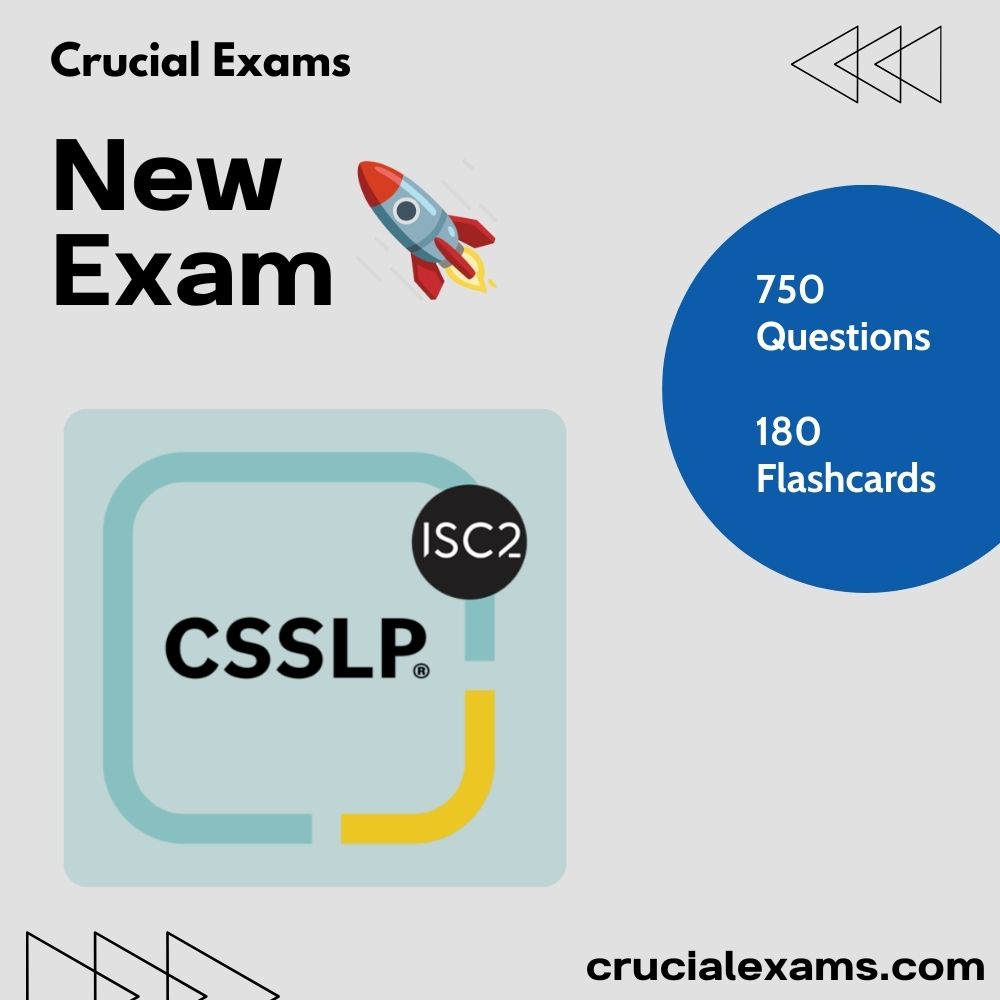
Day 3 of #ISC2 Launch Week 🚀 Today is the CSSLP - Certified Secure Software Lifecycle Professional, which is now available on Crucial with 750 practice questions and 180 flashcards! 👉 crucialexams.com/exams/isc2/cer…
As compliance expectations evolve, authenticated scanning offers deeper insight into system-level vulnerabilities across the CDE. Dive into this blog to learn how #PCIDSS Requirement 11.3.1.2 elevates internal security and improves validation → tevora.us/3XyCXQ2

The pressure for cybersecurity compliance in critical embedded systems is intensifying; but simply meeting standards like ISO 26262 or DO-178C isn't enough when lives or essential services are on the line. Traditional static analysis often leaves teams drowning in alerts,…

Industry-standards: PCI DSS v4.0 (A), NAIC Insurance Data Security Model Law (D), SOC 2 (B) EU: GDPR (S), NIS2 (A), DORA (S), PSD2 (A), AI Act (S), Cyber Resilience Act (A), Data Act (C), eIDAS 2.0 (C), EBA Guidelines on ICT and Security Risk Management (A) 3/5

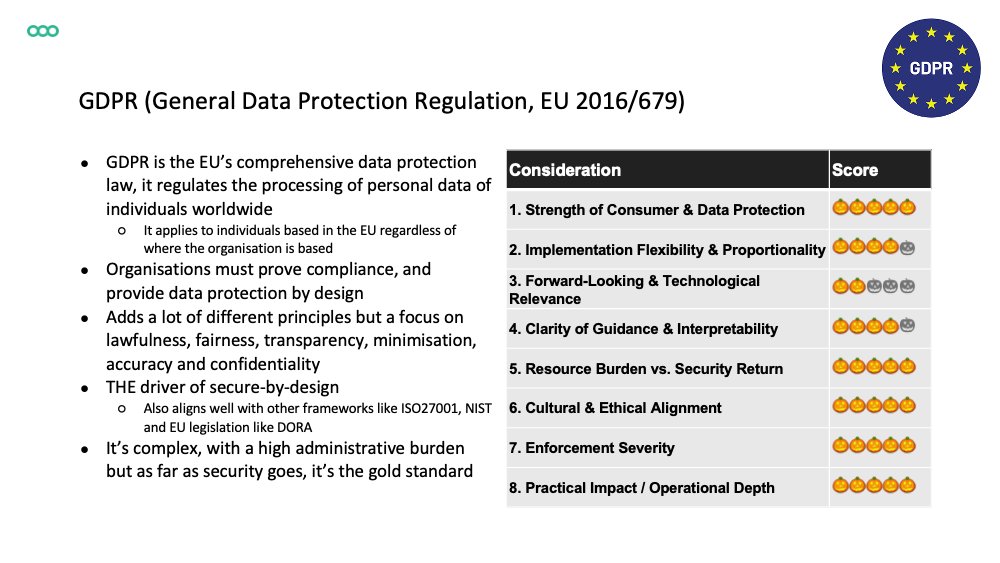
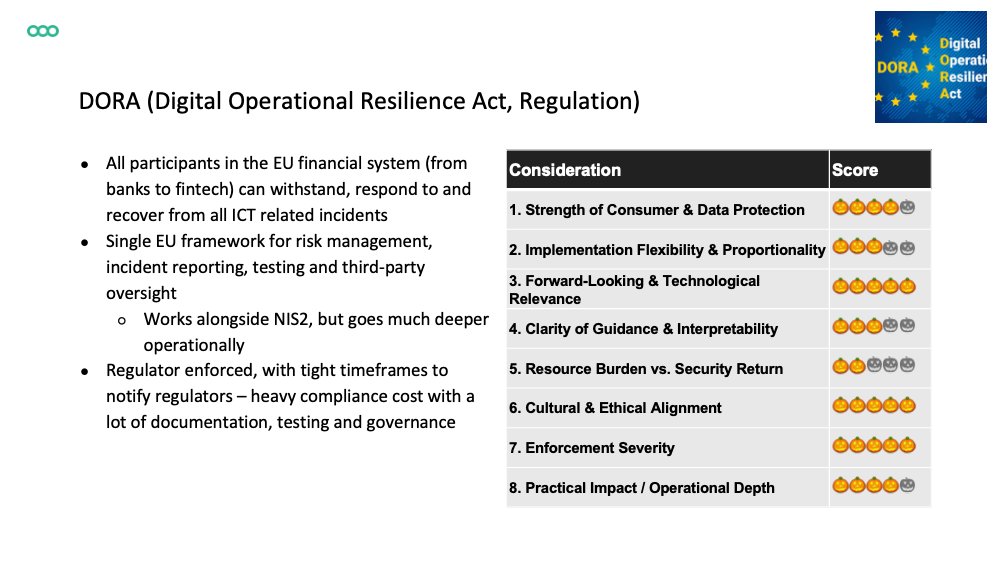
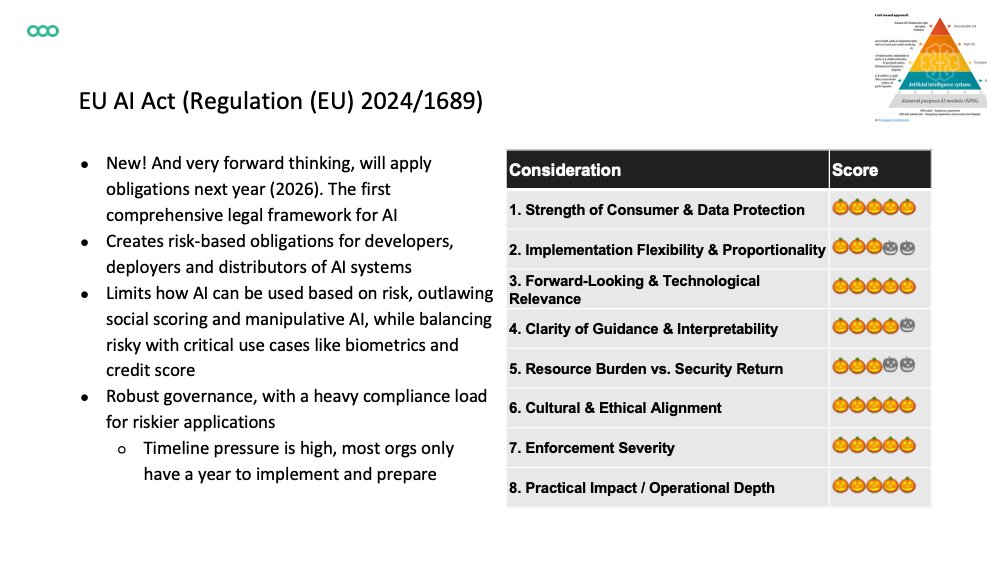
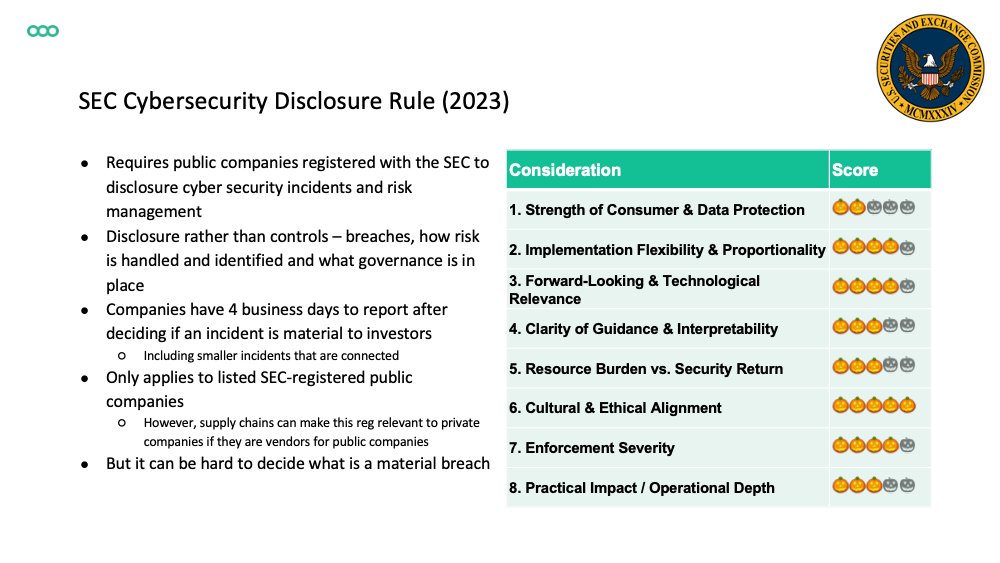
US: FTC Safeguards Rule (A), NYDFS 23 NYCRR 500 (D), SEC Cybersecurity Disclosure Rule (2023) (C), Computer-Security Incident Notification Rule (D), HIPAA Security Rule (D), CCPA/CPRA (C) Frameworks: NIST Cybersecurity Framework (S), Cyber Essentials (B), ISO/IEC 27001 (S) 2/5



Something went wrong.
Something went wrong.
United States Trends
- 1. #DWTS 12.9K posts
- 2. Elaine 30K posts
- 3. Jalen Johnson 2,877 posts
- 4. Alix 5,218 posts
- 5. Kingston Flemings N/A
- 6. Godzilla 28.5K posts
- 7. Hazel 9,913 posts
- 8. Wizards 7,221 posts
- 9. Bishop Boswell N/A
- 10. Araujo 193K posts
- 11. Joey Galloway 1,359 posts
- 12. Seton Hall 2,246 posts
- 13. #DancingWithTheStars N/A
- 14. House Party 7,420 posts
- 15. Chelsea 669K posts
- 16. Barca 268K posts
- 17. Daniella 2,219 posts
- 18. Carrie Ann N/A
- 19. Leftover 7,412 posts
- 20. BRUNO IS 70 N/A


















