#proxyauthentication search results
What is px402? px402 (built by PRXVT) is a zero-knowledge privacy layer built on top of x402 x402 - HTTP 402 payment protocol by Coinbase/Cloudflare - Standard web micropayments (like paying for API calls, content access, etc.) - Transparent: Sender address visible…

Who proved what and when, which version was verified keep it traceable. Signed logs + timestamps end debates. Prove “I meet this threshold,” keep raw docs private. E.g., prove age > 18 without sharing the ID. Privacy lowers risk, UX raises trust @brevis_zk

Day 6 of improving my backend skills. Added login controller and validate the fields using joi. Learnt about Access and Refresh token, it's actually cool ngl. Successfully implement proxy on 2 different apis. Big W :)


⚠️ Proton warns 300 million credentials leaked on dark web @ProtonPrivacy reveals over 300 million login details exposed via its new Dark Web Monitoring platform, highlighting credential-theft scale and urging users and organisations to shutter reused passwords, enable #2FA and…

Red Tip #402: Need to proxy Linux tools? Proxychains4. Need to proxy Windows tools like ADExplorer or Remote Desktop? Try out Proxycap, Proxifier. #cyber #operations #redteam

ES2015 Proxies landed in Chrome. Very useful for interception, object virtualization and logging/profiling 🔥

hi oomfs i am seeing this person running around (and liking my shit?) and after looking thru their account they are not just pure nsfw but also int w/r4cepl4y + transvestigates a real person. not to mention being nasty to one of my oomfs. i'm just sharing info bc ew bro

CYBERSECURITY GIVEAWAY ALERT Think you're unhackable?Let's make sure. Want to level up your cyber defense skills We're giving away insert prize premium VPN Cybersecurity Course Security Toolkit Follow @priyakashyp2502 (So I Can Dm With you) Like+ Retweet Reply'Cyber'

Day 5 of improving my backend skill. Didn't do much today, touched grass :) Learnt about proxy, it basically allows you to send request and response through different API endpoints. We go again tomorrow 💪

🔐 Struggling with “Proxy Authentication Error 2606” in Microsoft OneDrive, Microsoft Outlook izoate.com/blog/how-to-fi… #Microsoft365 #Error2606 #ProxyAuthentication #OneDriveFix #OutlookFix #TeamsFix #NetworkTroubleshooting #Izoate
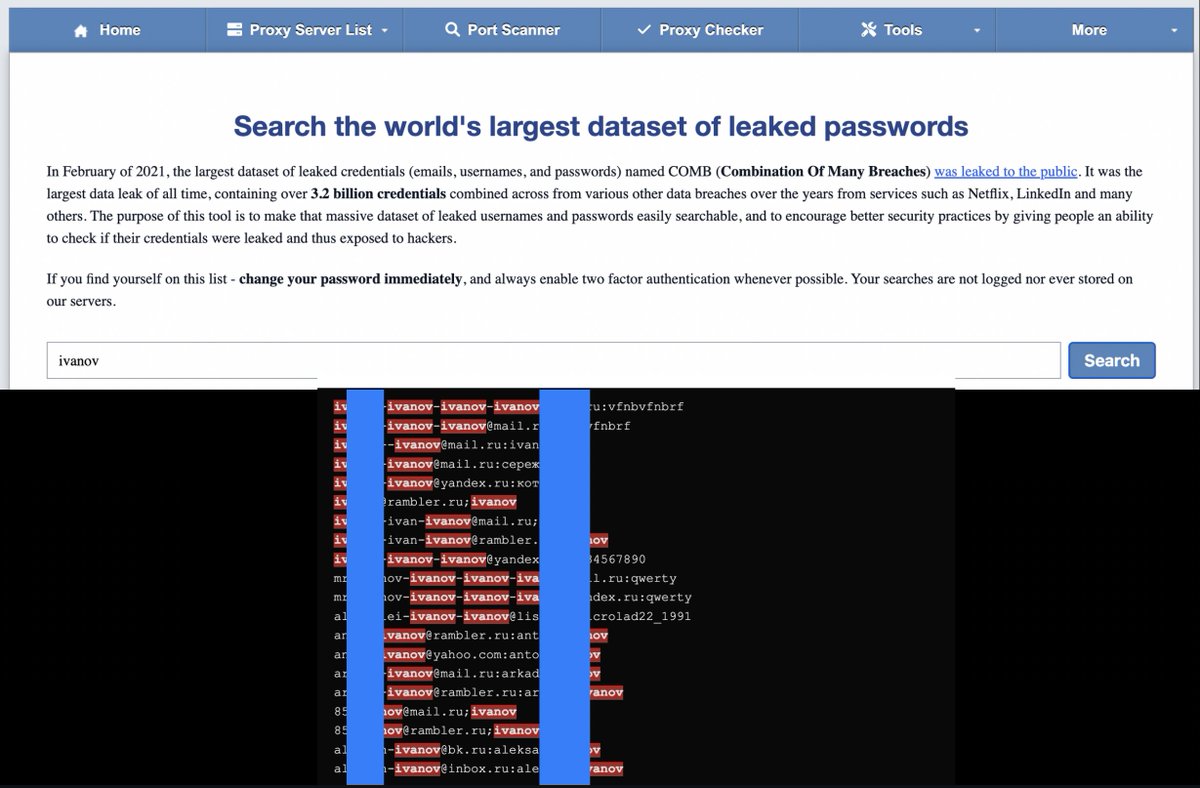
Leaked passwords database search tool Search by 3,2 billions leaked credentials by: - email - nickname - password (you can also try searching by mobile number, as some people use it as a password) proxynova.com/tools/comb/ Tip by @SaltinDeadsec
To understand authorization controls (Conditional Access), we need to understand the authentication tokens it evaluates When we log into a Hybrid or Entra joined device, we authenticate to Entra and get a Primary Refresh Token (PRT) with the time of the event in it The "issue":

May I have your attention for a moment, please?! go & verify your identity on @idOS_network website Verify cuz: > it’s safe & your data privacy is preserved > KYC once & works across the ecosystem > your gateway to stablecoin economy You welcome 😌
Closed identity stacks create lock-in, open ones create markets. 1⃣ Decentralize storage to prevent gatekeepers 2⃣Add privacy to prevent surveillance 3⃣ Enable compliant reusability to improve UX ...and you unlock the stablecoin economy. That's idOS.
Is your site stuck behind a digital gatekeeper?🚧 Don't worry; we know how to unlock the '407 Proxy Authentication Required' mystery! 🔓 Ready to set your website free? Explore the solution now: bit.ly/46aDSc1🌐✨ #WebDevelopment #HTTPError #ProxyAuthentication

🔒 Proxy servers are key to enhancing security, privacy, and performance online. But how do we ensure authorized access? 🤔🔑. Learn how these methods secure access to proxy servers and protect sensitive information. pyproxy.com/information/pr… #CyberSecurity #ProxyAuthentication

Was ist #CNTLM bitte für ein Ranz? Zum Glück px gefunden. Datt funktioniert einfach. #ProxyAuthentication
If you want to know how to activate the NTLM method for AnyDesk, please visit our Helpcenter: support.anydesk.com/Settings #AnyDesk #NTLM #ProxyAuthentication #RemoteDesktopSoftware #RemoteAccess #RemoteSupport #ITSupport #Windows
🔒 Proxy servers are key to enhancing security, privacy, and performance online. But how do we ensure authorized access? 🤔🔑. Learn how these methods secure access to proxy servers and protect sensitive information. pyproxy.com/information/pr… #CyberSecurity #ProxyAuthentication

Is your site stuck behind a digital gatekeeper?🚧 Don't worry; we know how to unlock the '407 Proxy Authentication Required' mystery! 🔓 Ready to set your website free? Explore the solution now: bit.ly/46aDSc1🌐✨ #WebDevelopment #HTTPError #ProxyAuthentication

Something went wrong.
Something went wrong.
United States Trends
- 1. Jonathan Taylor 15.4K posts
- 2. Falcons 27.7K posts
- 3. Colts 44.8K posts
- 4. Daniel Jones 9,399 posts
- 5. Penix 9,697 posts
- 6. Bijan 6,147 posts
- 7. Mooney 3,738 posts
- 8. #ForTheShoe 3,411 posts
- 9. Raheem Morris 3,459 posts
- 10. Liverpool 173K posts
- 11. Tyler Warren 2,004 posts
- 12. Drake London 4,049 posts
- 13. Max B 19.4K posts
- 14. Doku 51.4K posts
- 15. Konate 18.1K posts
- 16. Marlon Humphrey N/A
- 17. Zac Robinson 1,374 posts
- 18. Cole Bishop N/A
- 19. Go Bills 7,484 posts
- 20. Pitts 4,122 posts