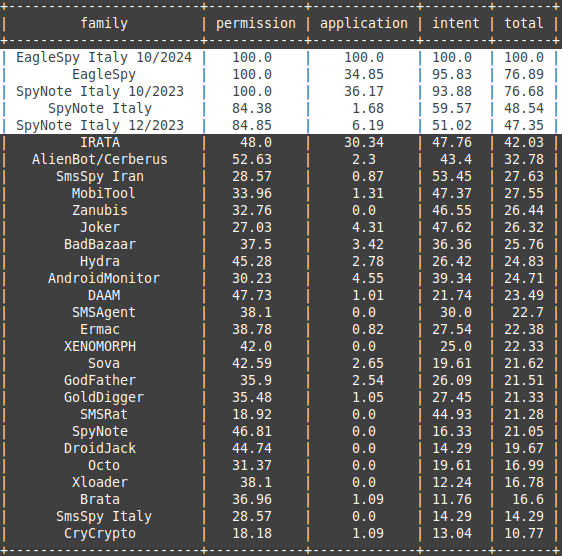
#spynote search results
#spynote found ->hxxps://www.virustotal.com/gui/file/a1de866d5f75b3f31becb07f4660e2a3cc29d242888be38fadb5a54657156745 #opendir
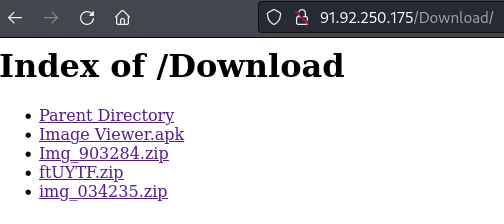
This is a type of craxs rat(#spynote) malware. Since A101 is a Turkish🇹🇷 market chain, the target is Turkish citizens.
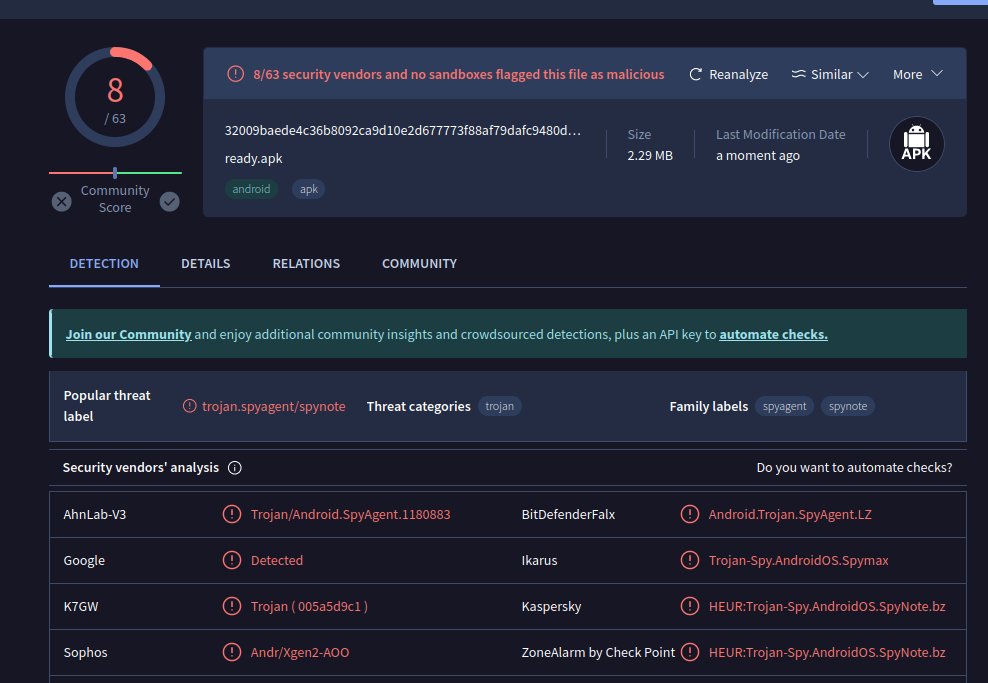
who can help? these apks are 0 detections on VT although i am almost 100% sure they are malicious.
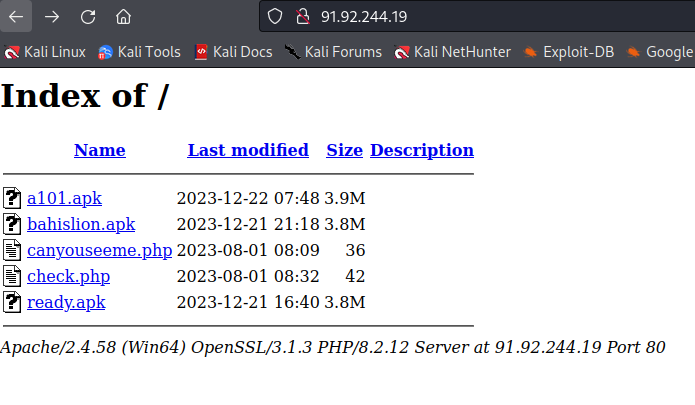
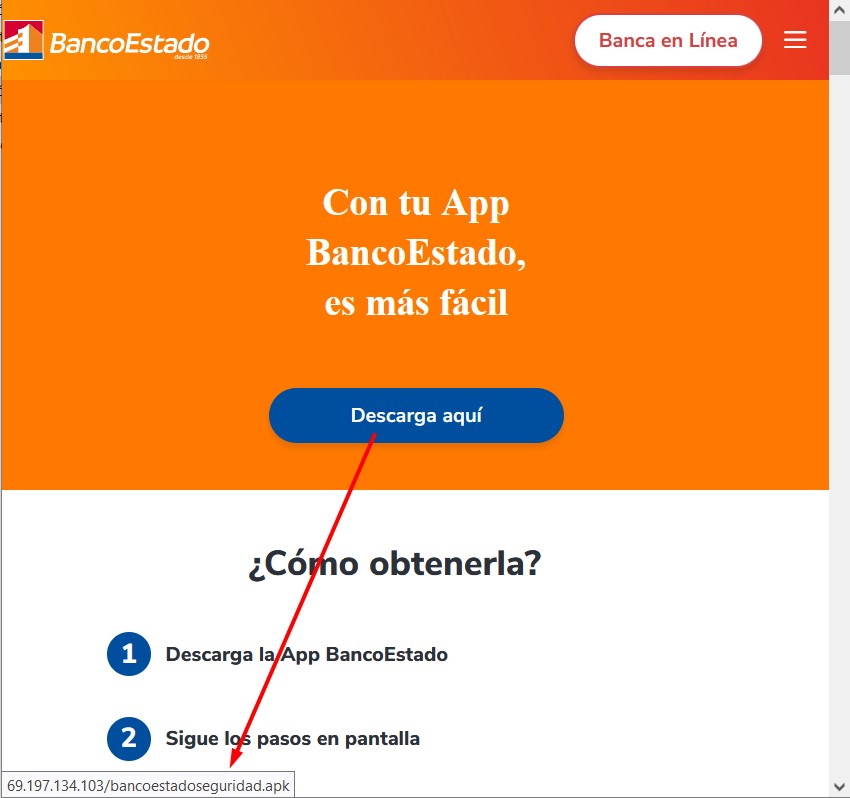
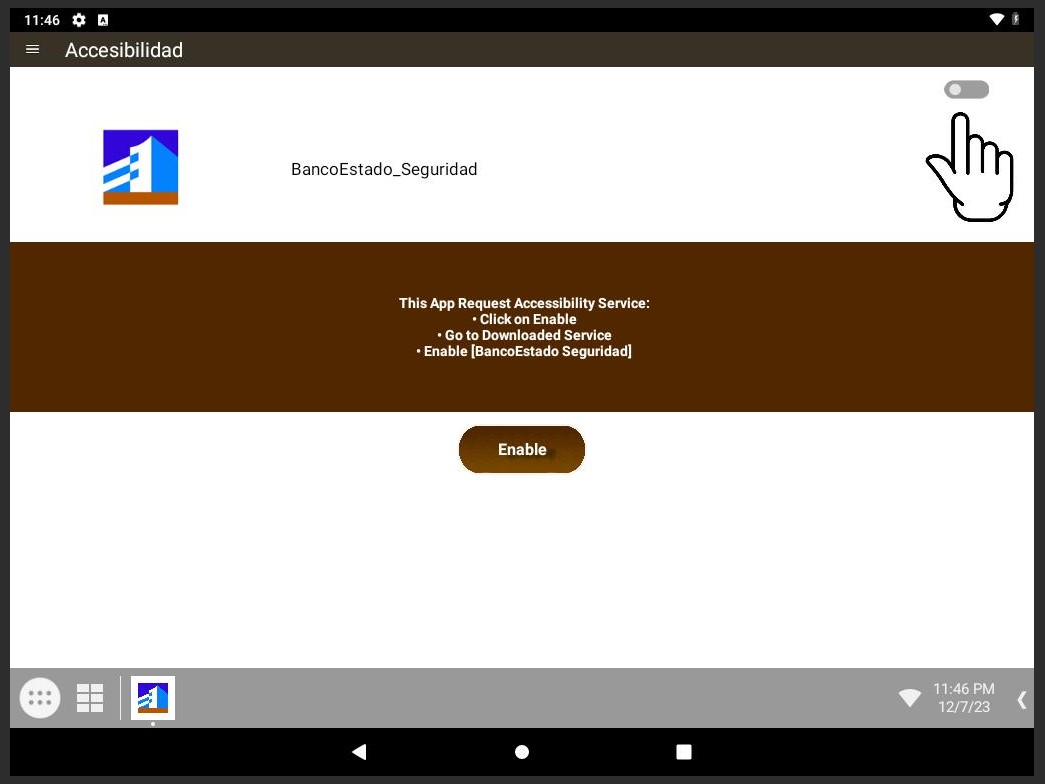
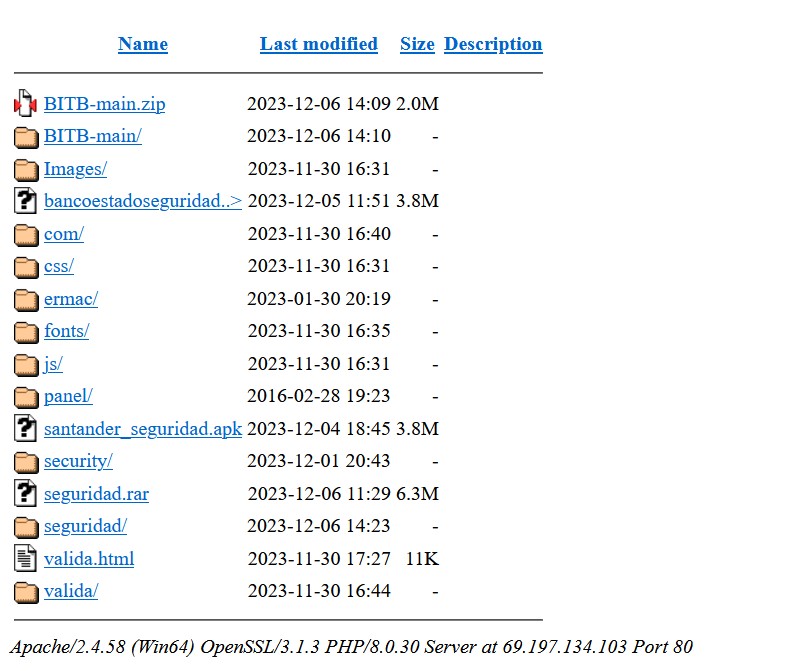
⚠️ #SpyNote Android RAT dirigido a Chile 🇨🇱 y suplantando a Banco Estado y Banco Santander. Para infectar a sus víctimas, el atacante realiza campañas de #phishing a través de la técnica conocida como BITB (Browser In The Browser). Ref: mrd0x.com/browser-in-the… 69.197.134.103…

#Fofabot Query for #SpyNote #Malware Query: title=="SpyNote Encryptor" IOCs: https://panel.spynote[.]us 109.248.59[.]212 45.130.151[.]211
![Cyberteam008's tweet image. #Fofabot Query for #SpyNote #Malware
Query: title=="SpyNote Encryptor"
IOCs:
https://panel.spynote[.]us
109.248.59[.]212
45.130.151[.]211](https://pbs.twimg.com/media/GH_sgPCWQAAzTtQ.jpg)
+ haorizi888[.]top #SpyNote
![skocherhan's tweet image. + haorizi888[.]top
#SpyNote](https://pbs.twimg.com/media/GoxD_TxWEAARm4B.png)
🚨 Newly Registered Domains Distributing SpyNote Malware The latest DomainTools Investigations (DTI) analysis reveals that deceptive websites hosted on newly registered domains are being used to deliver the potent AndroidOS SpyNote malware. dti.domaintools.com/newly-register…

#Spynote AS 20473 🇸🇬 http[:]//66.42.55.13/ready[.]apk AS 210538 🇹🇷 https[:]//45.87.173.219/ready[.]apk Undetected #IOC #Android cc @banthisguy9349 @bofheaded
![prashant_92's tweet image. #Spynote
AS 20473 🇸🇬
http[:]//66.42.55.13/ready[.]apk
AS 210538 🇹🇷
https[:]//45.87.173.219/ready[.]apk
Undetected
#IOC #Android
cc @banthisguy9349 @bofheaded](https://pbs.twimg.com/media/GbAk0RnWEAAulDs.jpg)
![prashant_92's tweet image. #Spynote
AS 20473 🇸🇬
http[:]//66.42.55.13/ready[.]apk
AS 210538 🇹🇷
https[:]//45.87.173.219/ready[.]apk
Undetected
#IOC #Android
cc @banthisguy9349 @bofheaded](https://pbs.twimg.com/media/GbAk0RnXYAIpgrr.jpg)
#AsyncRAT server distributing #SpyNote a.k.a. #CypherRat hxxp://31.172.83.170/apks/ [+]more info: bleepingcomputer.com/news/security/…
![V3n0mStrike's tweet image. #AsyncRAT server distributing #SpyNote a.k.a. #CypherRat
hxxp://31.172.83.170/apks/
[+]more info: bleepingcomputer.com/news/security/…](https://pbs.twimg.com/media/GCU0TbyWoAArnml.jpg)
![V3n0mStrike's tweet image. #AsyncRAT server distributing #SpyNote a.k.a. #CypherRat
hxxp://31.172.83.170/apks/
[+]more info: bleepingcomputer.com/news/security/…](https://pbs.twimg.com/media/GCU0To5W4AAZ8L3.jpg)
![V3n0mStrike's tweet image. #AsyncRAT server distributing #SpyNote a.k.a. #CypherRat
hxxp://31.172.83.170/apks/
[+]more info: bleepingcomputer.com/news/security/…](https://pbs.twimg.com/media/GCU0T6lXsAI6V5q.jpg)
http[:]45.138.16.250 hosting #SPYNOTE #apk #malware AS 210558( 1337 Services GmbH ) md5: 915e7b50d3cb50243c66ce069032e2cf
![raghav127001's tweet image. http[:]45.138.16.250 hosting #SPYNOTE #apk #malware
AS 210558( 1337 Services GmbH )
md5: 915e7b50d3cb50243c66ce069032e2cf](https://pbs.twimg.com/media/GOUwxMdXUAA2QtL.jpg)
![raghav127001's tweet image. http[:]45.138.16.250 hosting #SPYNOTE #apk #malware
AS 210558( 1337 Services GmbH )
md5: 915e7b50d3cb50243c66ce069032e2cf](https://pbs.twimg.com/media/GOUxF86W0AAIfyz.jpg)
![raghav127001's tweet image. http[:]45.138.16.250 hosting #SPYNOTE #apk #malware
AS 210558( 1337 Services GmbH )
md5: 915e7b50d3cb50243c66ce069032e2cf](https://pbs.twimg.com/media/GOUx5TZWIAEeDKY.jpg)
⚠️Watch out fake AV websites sharing malware #Spynote (for android) /avast-securedownload.com @Avast #Lumma Stealer /bitdefender-app.com @Bitdefender #StealC (via Buer Loader?) /malwarebytes.pro @Malwarebytes samples and detonations below 👀
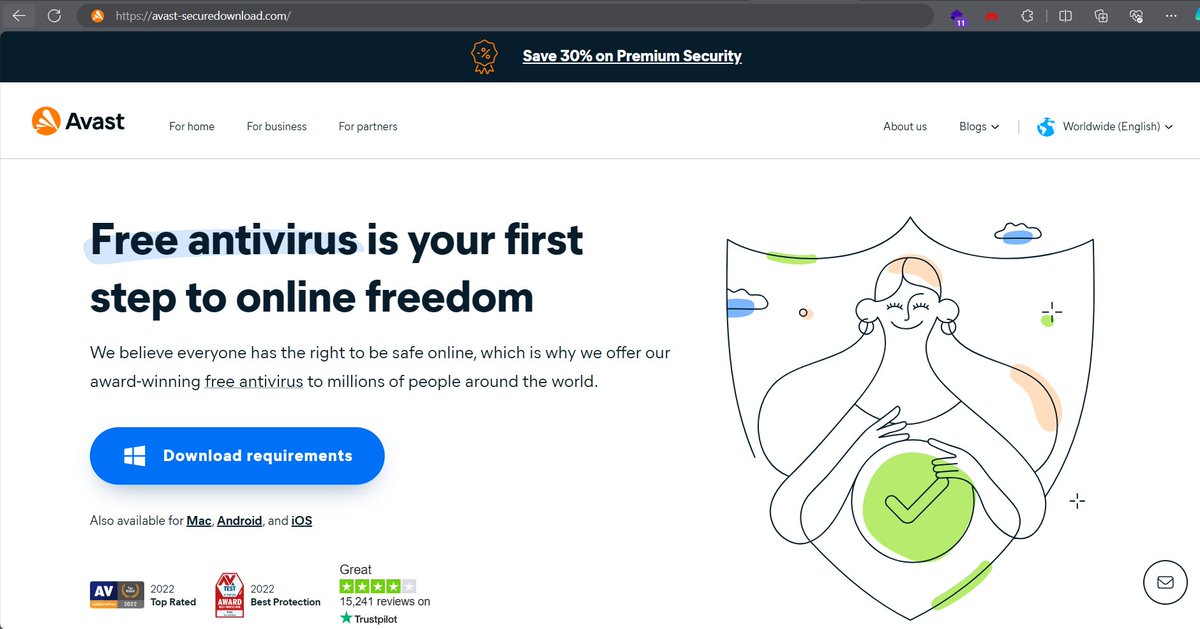
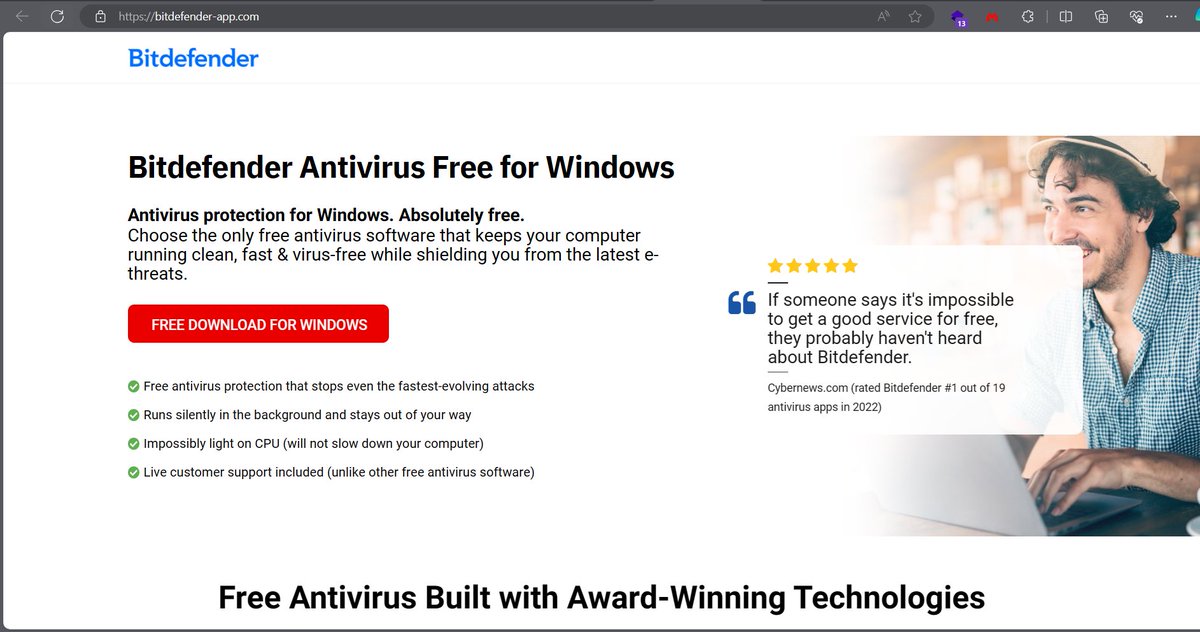
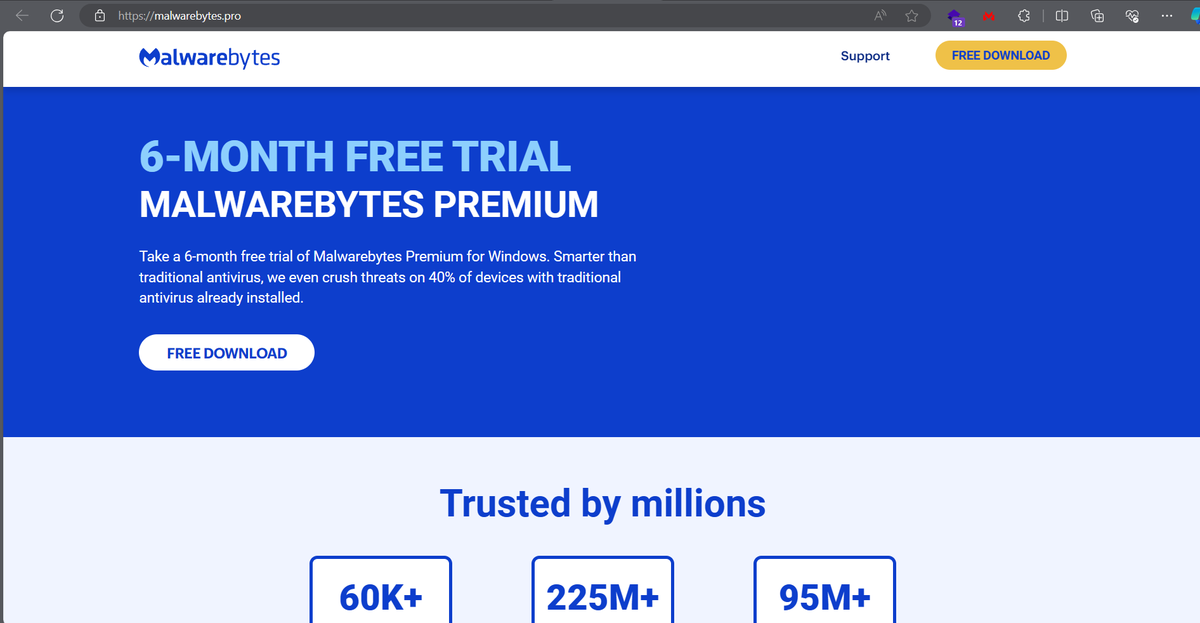
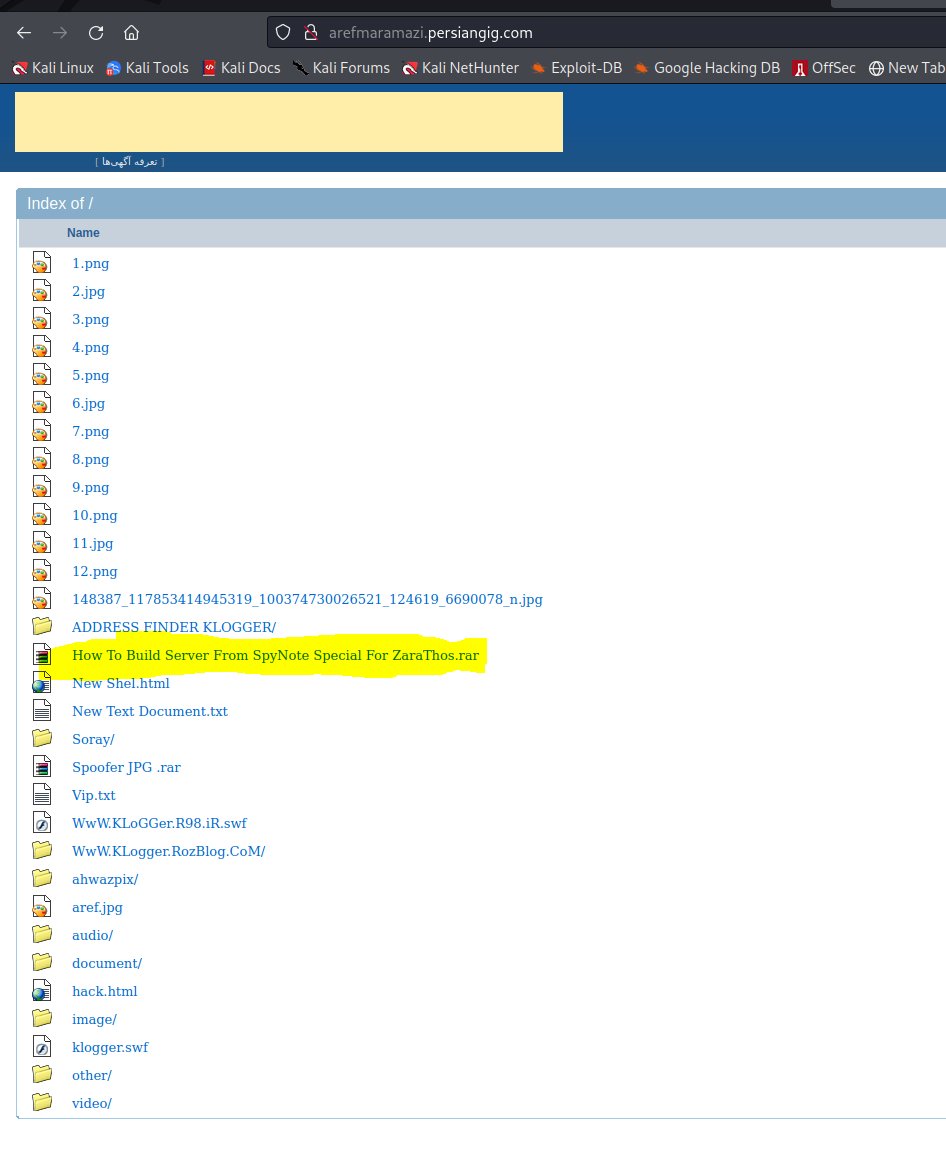
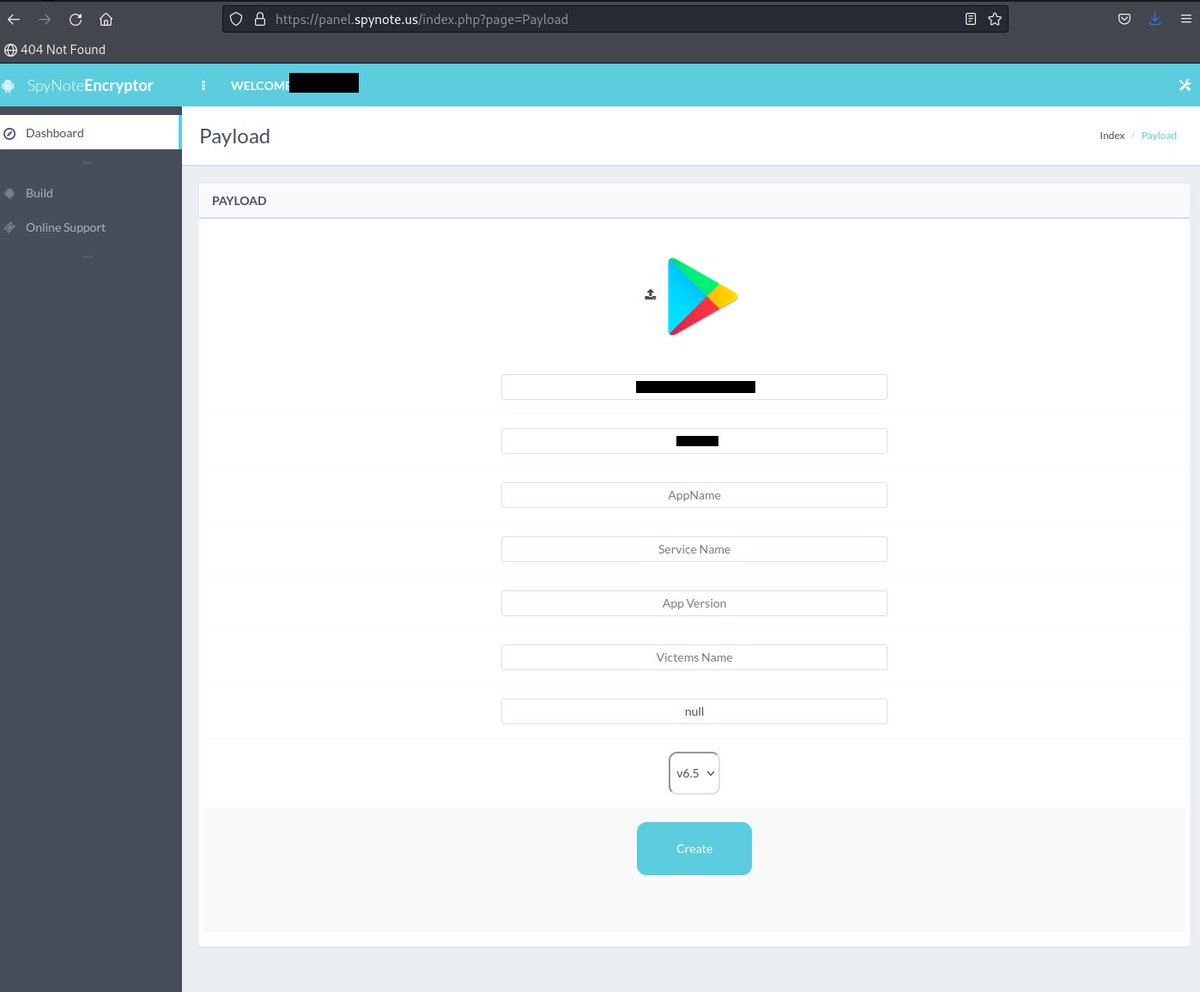
#spynote #spyware owner dor47 whoever wondered how Cybercriminals setup the malicious spynote apk's check Picture 2. we are sending roughly 40 samples now to @ReversingLabs
http://54.253.82.23:8080/ #opendir #spyware #spynote hxxp://47.57.184.164 /ready.apk hxxp://103.148.125.8 /ready.apk hxxp://47.57.7.44 /ready.apk hxxp://103.148.125.26 /ready.apk hxxp://164.155.241.15 /ready.apk hxxp://103.142.244.32 /ready.apk
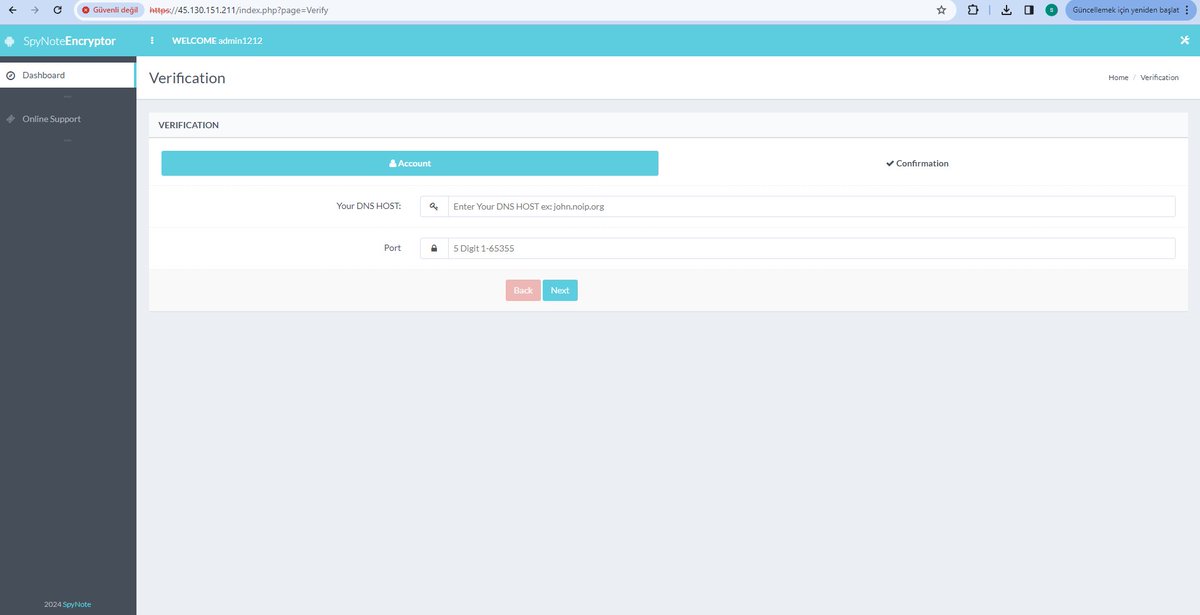
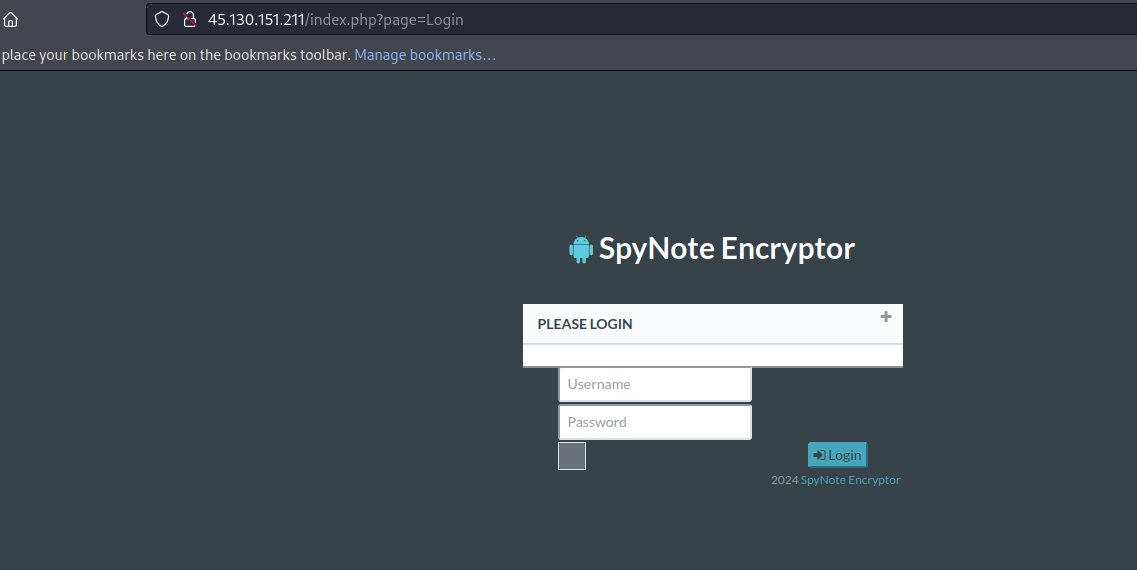
#spynote #android #encryptor panel hxxp://45.130.151.211/index.php?page=Login cc: @Gi7w0rm @500mk500 @abuse_ch @ViriBack
⚠️fake Android App [Rapport ラポート] #SpyNote #trojan IP: 194.124.216[.]154 (AS3214 xTom) Abused Brand: Bank of Japan 日本銀行 IoC: otx.alienvault.com/pulse/6440223b… 🦠/skin/client/signed10317c.apk bazaar.abuse.ch/sample/7c4fdf5… bazaar.abuse.ch/sample/841271e… @NaomiSuzuki_ @58_158_177_102 @bunnymaid
![ozuma5119's tweet image. ⚠️fake Android App [Rapport ラポート] #SpyNote #trojan
IP: 194.124.216[.]154 (AS3214 xTom)
Abused Brand: Bank of Japan 日本銀行
IoC: otx.alienvault.com/pulse/6440223b…
🦠/skin/client/signed10317c.apk
bazaar.abuse.ch/sample/7c4fdf5…
bazaar.abuse.ch/sample/841271e…
@NaomiSuzuki_ @58_158_177_102 @bunnymaid](https://pbs.twimg.com/media/FuGAx8paYAIX6fg.jpg)
![ozuma5119's tweet image. ⚠️fake Android App [Rapport ラポート] #SpyNote #trojan
IP: 194.124.216[.]154 (AS3214 xTom)
Abused Brand: Bank of Japan 日本銀行
IoC: otx.alienvault.com/pulse/6440223b…
🦠/skin/client/signed10317c.apk
bazaar.abuse.ch/sample/7c4fdf5…
bazaar.abuse.ch/sample/841271e…
@NaomiSuzuki_ @58_158_177_102 @bunnymaid](https://pbs.twimg.com/media/FuGAyVKaAAEBL0e.jpg)
![ozuma5119's tweet image. ⚠️fake Android App [Rapport ラポート] #SpyNote #trojan
IP: 194.124.216[.]154 (AS3214 xTom)
Abused Brand: Bank of Japan 日本銀行
IoC: otx.alienvault.com/pulse/6440223b…
🦠/skin/client/signed10317c.apk
bazaar.abuse.ch/sample/7c4fdf5…
bazaar.abuse.ch/sample/841271e…
@NaomiSuzuki_ @58_158_177_102 @bunnymaid](https://pbs.twimg.com/media/FuGBJNNaQAAEyOh.jpg)
🚩 Nuevo dominio .CL registrado para distribuir el Troyano para dispositivos Android #SpyNote. El sitio web se encuentra en scotiapass[.]cl y suplanta a Scotiabank Chile 🇨🇱 Los actores de amenaza también crearon un canal de YouTube (ScotiaPass) con una guía de instalación 😏…
![1ZRR4H's tweet image. 🚩 Nuevo dominio .CL registrado para distribuir el Troyano para dispositivos Android #SpyNote.
El sitio web se encuentra en scotiapass[.]cl y suplanta a Scotiabank Chile 🇨🇱
Los actores de amenaza también crearon un canal de YouTube (ScotiaPass) con una guía de instalación 😏…](https://pbs.twimg.com/media/GU9h9RbWsAEzG37.jpg)
![1ZRR4H's tweet image. 🚩 Nuevo dominio .CL registrado para distribuir el Troyano para dispositivos Android #SpyNote.
El sitio web se encuentra en scotiapass[.]cl y suplanta a Scotiabank Chile 🇨🇱
Los actores de amenaza también crearon un canal de YouTube (ScotiaPass) con una guía de instalación 😏…](https://pbs.twimg.com/media/GU9h9RpWYAAsWQ0.jpg)
![1ZRR4H's tweet image. 🚩 Nuevo dominio .CL registrado para distribuir el Troyano para dispositivos Android #SpyNote.
El sitio web se encuentra en scotiapass[.]cl y suplanta a Scotiabank Chile 🇨🇱
Los actores de amenaza también crearon un canal de YouTube (ScotiaPass) con una guía de instalación 😏…](https://pbs.twimg.com/media/GU9h9RlX0AA__QU.jpg)
![1ZRR4H's tweet image. 🚩 Nuevo dominio .CL registrado para distribuir el Troyano para dispositivos Android #SpyNote.
El sitio web se encuentra en scotiapass[.]cl y suplanta a Scotiabank Chile 🇨🇱
Los actores de amenaza también crearon un canal de YouTube (ScotiaPass) con una guía de instalación 😏…](https://pbs.twimg.com/media/GU9hjpMXwAAY-Bb.png)
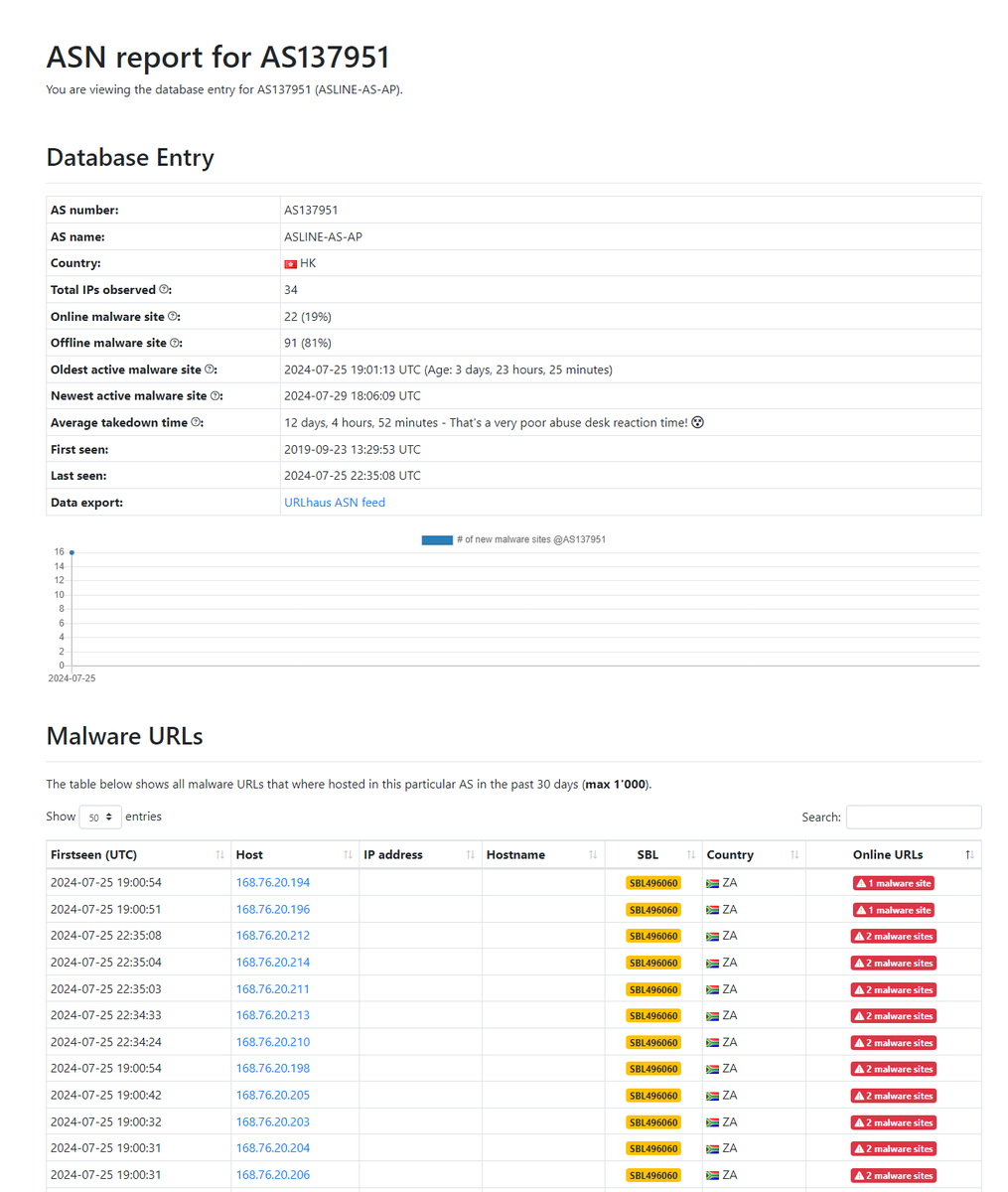
#spyware #spynote Alert ‼️ Coming from AS137951 ASLINE-AS-AP They have also left a nice cat picture for @vxunderground cc: @spamhaus thanks @NDA0E for reporting them.


#Phishing #Avast #Spynote 📌hxxps://avastsf.]com/📌 Windows - Downloads Anydesk (Revoked Cert) - Anydesk.exe (virustotal.com/gui/file/ec33d…) Mac - Downloads Anydesk - anydesk.dmg (virustotal.com/gui/file/9960c…) Android - Downloads Spynote Trojan - Avastavv.apk (virustotal.com/gui/file/94a3b…)
![RacWatchin8872's tweet image. #Phishing #Avast #Spynote
📌hxxps://avastsf.]com/📌
Windows - Downloads Anydesk (Revoked Cert) - Anydesk.exe (virustotal.com/gui/file/ec33d…)
Mac - Downloads Anydesk - anydesk.dmg (virustotal.com/gui/file/9960c…)
Android - Downloads Spynote Trojan - Avastavv.apk (virustotal.com/gui/file/94a3b…)](https://pbs.twimg.com/media/GP4H25kWYAA0Ti0.jpg)
![RacWatchin8872's tweet image. #Phishing #Avast #Spynote
📌hxxps://avastsf.]com/📌
Windows - Downloads Anydesk (Revoked Cert) - Anydesk.exe (virustotal.com/gui/file/ec33d…)
Mac - Downloads Anydesk - anydesk.dmg (virustotal.com/gui/file/9960c…)
Android - Downloads Spynote Trojan - Avastavv.apk (virustotal.com/gui/file/94a3b…)](https://pbs.twimg.com/media/GP4H6FkWAAEJWFG.jpg)
![RacWatchin8872's tweet image. #Phishing #Avast #Spynote
📌hxxps://avastsf.]com/📌
Windows - Downloads Anydesk (Revoked Cert) - Anydesk.exe (virustotal.com/gui/file/ec33d…)
Mac - Downloads Anydesk - anydesk.dmg (virustotal.com/gui/file/9960c…)
Android - Downloads Spynote Trojan - Avastavv.apk (virustotal.com/gui/file/94a3b…)](https://pbs.twimg.com/media/GP4H6FnXkAAXyOf.jpg)
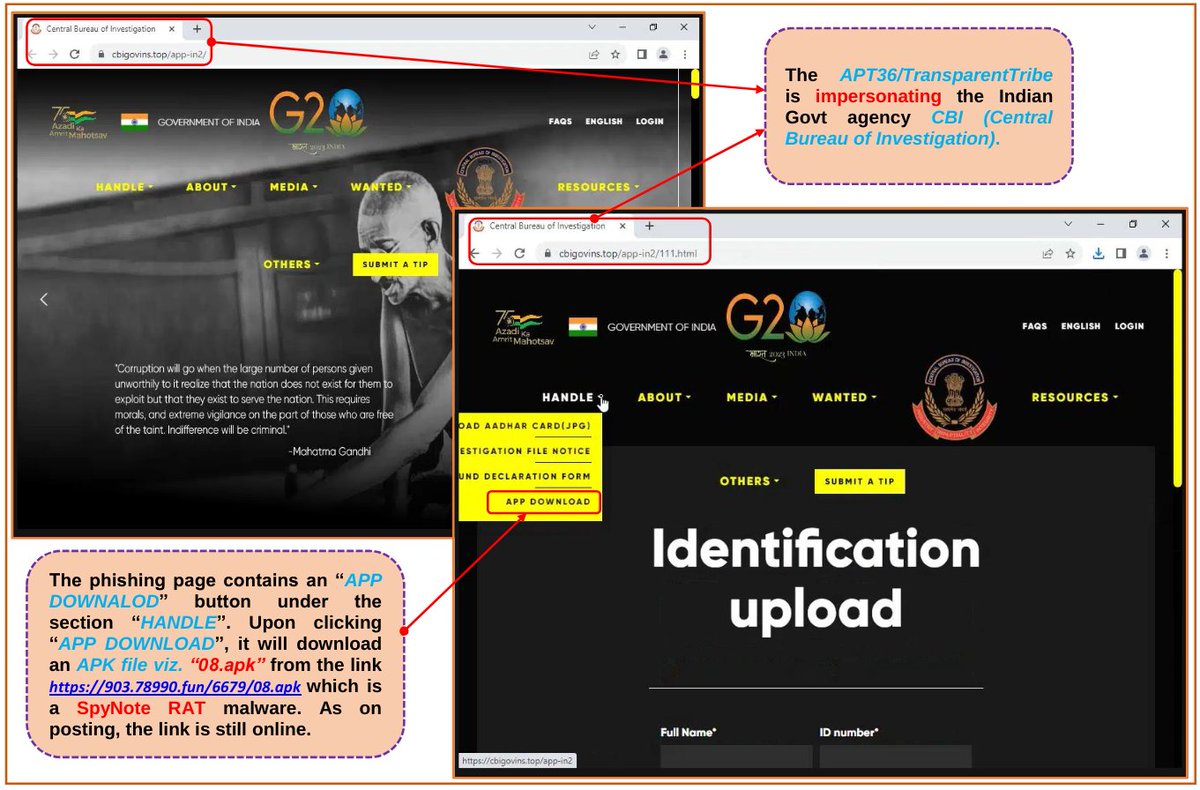
Pakistan's #APT36 / #TransparentTribe is Targeting Indian Govt agency Central Bureau of Investigation (CBI) to deliver #SpyNote #RAT malware. Details are explained in the attached snapshot. Infra: pastebin.com/w0F6pVa7 @500mk500 #Malware #ioc
Something went wrong.
Something went wrong.
United States Trends
- 1. #doordashfairy 1,069 posts
- 2. Vanity Fair 61.6K posts
- 3. Susie Wiles 124K posts
- 4. Mick Foley 33K posts
- 5. Mustapha Kharbouch 21.3K posts
- 6. Olive Garden 1,129 posts
- 7. Larian 10.9K posts
- 8. Brookline 9,235 posts
- 9. $TSLA 48.7K posts
- 10. Michelea Ponce 32.6K posts
- 11. Christensen 3,699 posts
- 12. Cardiff 25.6K posts
- 13. Mary and Joseph 1,326 posts
- 14. Snowslingers N/A
- 15. Kay Flock 1,061 posts
- 16. Carville 3,275 posts
- 17. Gittens 7,318 posts
- 18. Spielberg 28.8K posts
- 19. Garnacho 18.1K posts
- 20. Tosin 8,896 posts