#spynote resultados de búsqueda
http://54.253.82.23:8080/ #opendir #spyware #spynote hxxp://47.57.184.164 /ready.apk hxxp://103.148.125.8 /ready.apk hxxp://47.57.7.44 /ready.apk hxxp://103.148.125.26 /ready.apk hxxp://164.155.241.15 /ready.apk hxxp://103.142.244.32 /ready.apk
A new #SpyNote report is out! 🚨 Dive into the tactics of this Android RAT campaign, from dynamic payload decryption to new obfuscation methods. Learn how threat actors are using deceptive Google Play Store clones to target users dti.domaintools.com/spynote-malwar…
#Spynote #opendir | AttackCapture An opendir is tracked by @Huntio having 5 different spynote samples. 65cd191f13353ec1cc061ccc751cbfaa d610ced310444cfbab7daa91e3f79439 68a98e82d2abdec08d7cad18a0c3eb8b 32acc69b4c703de71d7a97632c805ede 16fd63efc57a726706ba9eb5b996af21

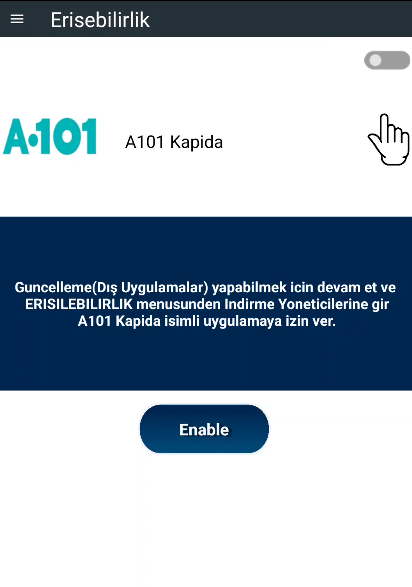
This is a type of craxs rat(#spynote) malware. Since A101 is a Turkish🇹🇷 market chain, the target is Turkish citizens.
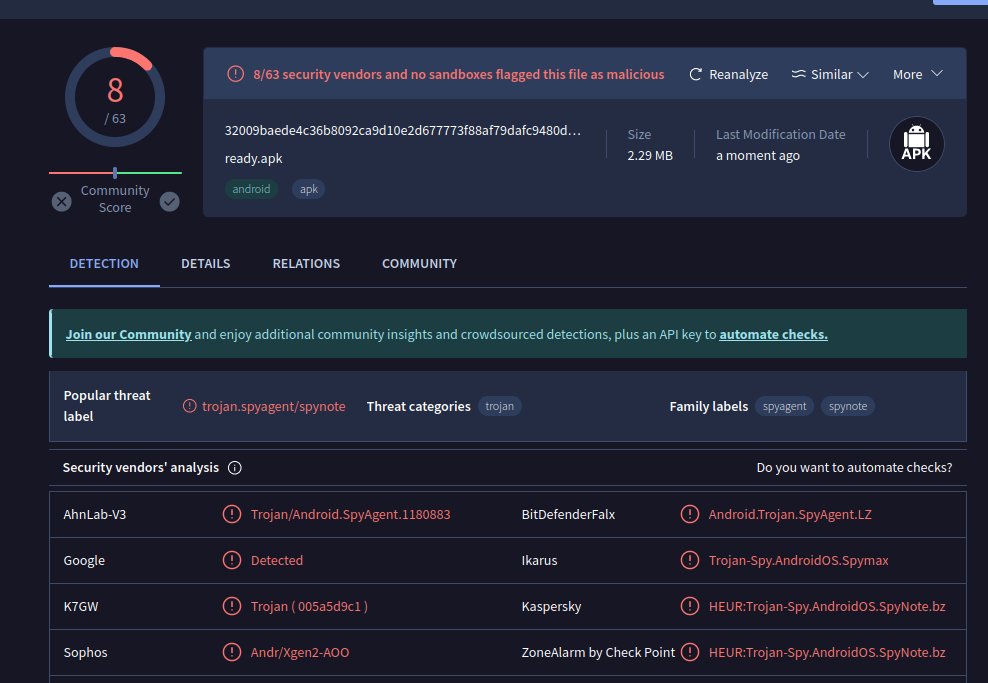
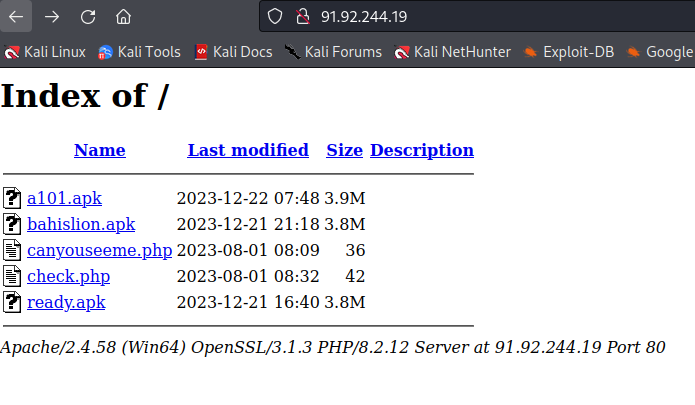
who can help? these apks are 0 detections on VT although i am almost 100% sure they are malicious.
🚩 Nuevo dominio .CL registrado para distribuir el Troyano para dispositivos Android #SpyNote. El sitio web se encuentra en scotiapass[.]cl y suplanta a Scotiabank Chile 🇨🇱 Los actores de amenaza también crearon un canal de YouTube (ScotiaPass) con una guía de instalación 😏…
![1ZRR4H's tweet image. 🚩 Nuevo dominio .CL registrado para distribuir el Troyano para dispositivos Android #SpyNote.
El sitio web se encuentra en scotiapass[.]cl y suplanta a Scotiabank Chile 🇨🇱
Los actores de amenaza también crearon un canal de YouTube (ScotiaPass) con una guía de instalación 😏…](https://pbs.twimg.com/media/GU9h9RbWsAEzG37.jpg)
![1ZRR4H's tweet image. 🚩 Nuevo dominio .CL registrado para distribuir el Troyano para dispositivos Android #SpyNote.
El sitio web se encuentra en scotiapass[.]cl y suplanta a Scotiabank Chile 🇨🇱
Los actores de amenaza también crearon un canal de YouTube (ScotiaPass) con una guía de instalación 😏…](https://pbs.twimg.com/media/GU9h9RpWYAAsWQ0.jpg)
![1ZRR4H's tweet image. 🚩 Nuevo dominio .CL registrado para distribuir el Troyano para dispositivos Android #SpyNote.
El sitio web se encuentra en scotiapass[.]cl y suplanta a Scotiabank Chile 🇨🇱
Los actores de amenaza también crearon un canal de YouTube (ScotiaPass) con una guía de instalación 😏…](https://pbs.twimg.com/media/GU9h9RlX0AA__QU.jpg)
![1ZRR4H's tweet image. 🚩 Nuevo dominio .CL registrado para distribuir el Troyano para dispositivos Android #SpyNote.
El sitio web se encuentra en scotiapass[.]cl y suplanta a Scotiabank Chile 🇨🇱
Los actores de amenaza también crearon un canal de YouTube (ScotiaPass) con una guía de instalación 😏…](https://pbs.twimg.com/media/GU9hjpMXwAAY-Bb.png)
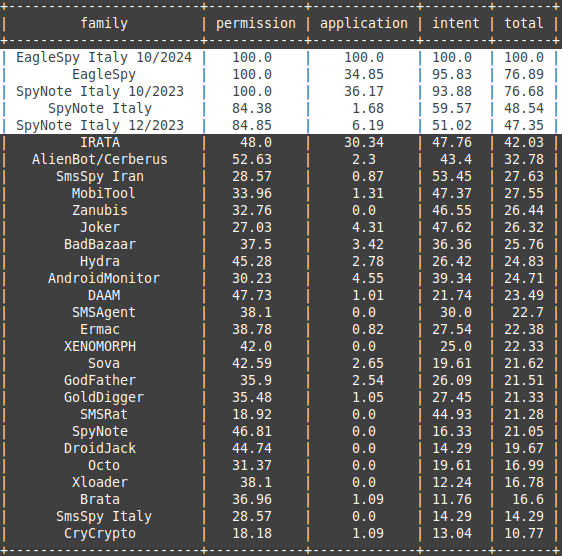
🎉 4 new rules added and 238 rules updated for the #SpyNote malware family. We're moving toward practical, powerful tools — thanks for your continued support! 🙏 Thanks to @zorro_wang ! 🔗 Report: reurl.cc/QaqnQZ

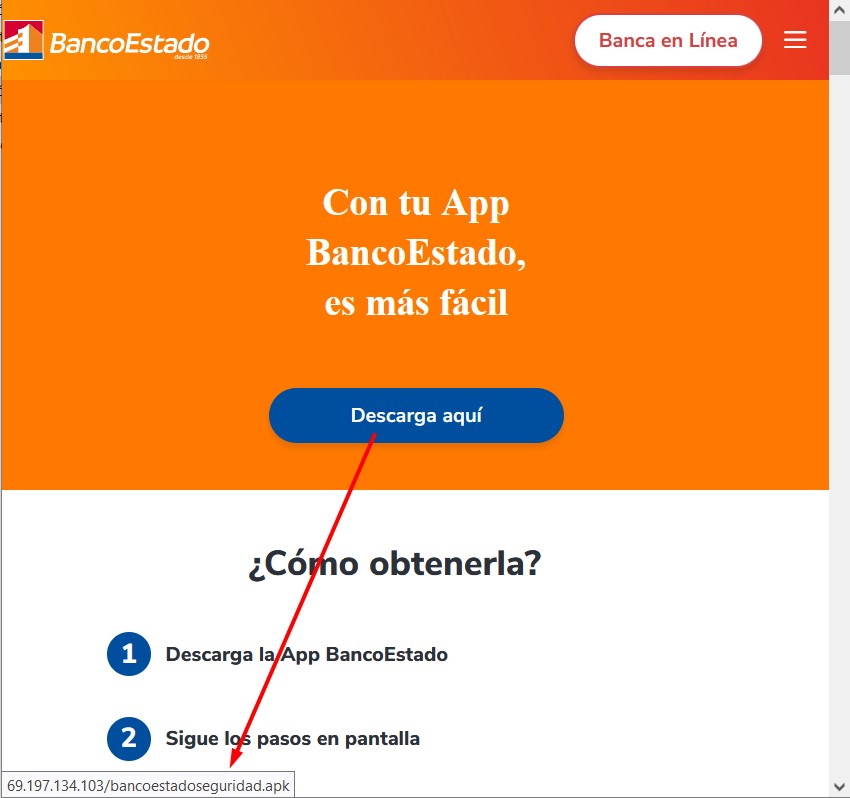
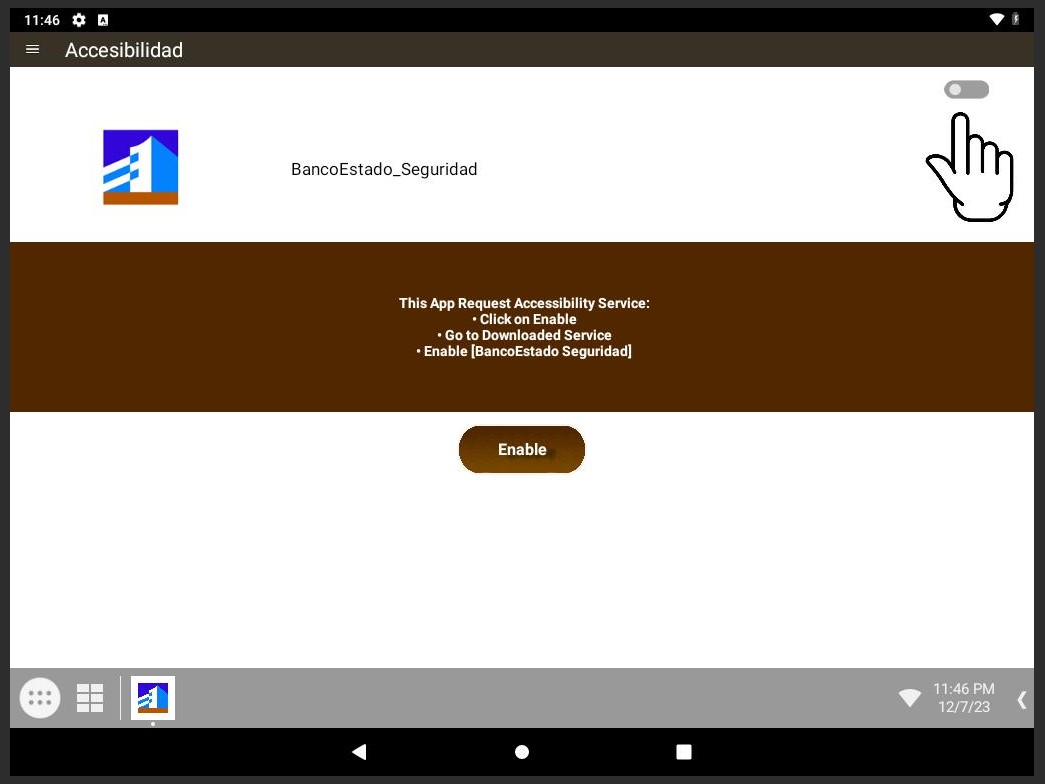
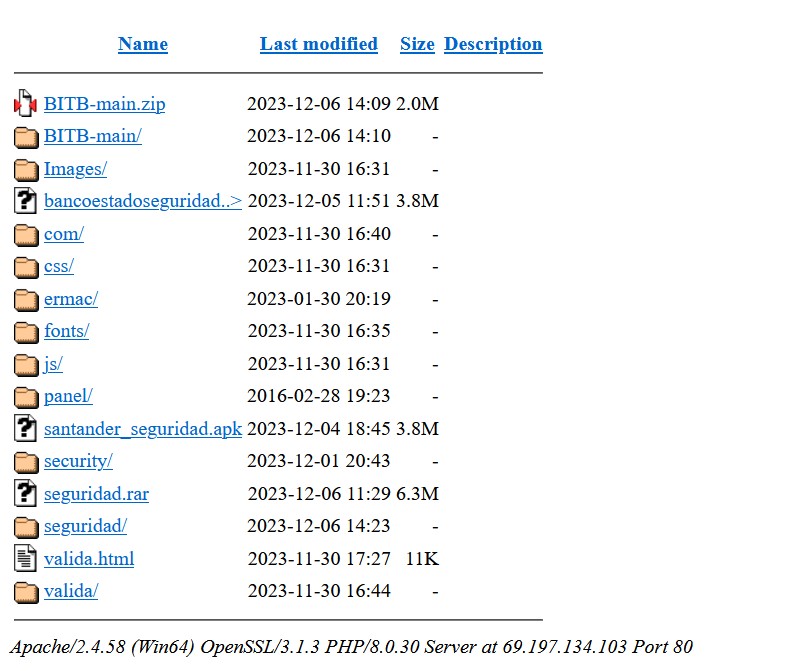
⚠️ #SpyNote Android RAT dirigido a Chile 🇨🇱 y suplantando a Banco Estado y Banco Santander. Para infectar a sus víctimas, el atacante realiza campañas de #phishing a través de la técnica conocida como BITB (Browser In The Browser). Ref: mrd0x.com/browser-in-the… 69.197.134.103…

#spynote #spyware owner dor47 whoever wondered how Cybercriminals setup the malicious spynote apk's check Picture 2. we are sending roughly 40 samples now to @ReversingLabs
+ haorizi888[.]top #SpyNote
![skocherhan's tweet image. + haorizi888[.]top
#SpyNote](https://pbs.twimg.com/media/GoxD_TxWEAARm4B.png)
🚨 Newly Registered Domains Distributing SpyNote Malware The latest DomainTools Investigations (DTI) analysis reveals that deceptive websites hosted on newly registered domains are being used to deliver the potent AndroidOS SpyNote malware. dti.domaintools.com/newly-register…

Per la prima volta abbiamo visto il malware Android #EagleSpy diffuso in Italia, esso risulta molto similare a ##SpyNote e CraxsRAT. Obiettivamente l'intento finale è sempre lo stesso, sottrarre informazioni bancarie. I#oC: d3lab.net/nuova-campagna…
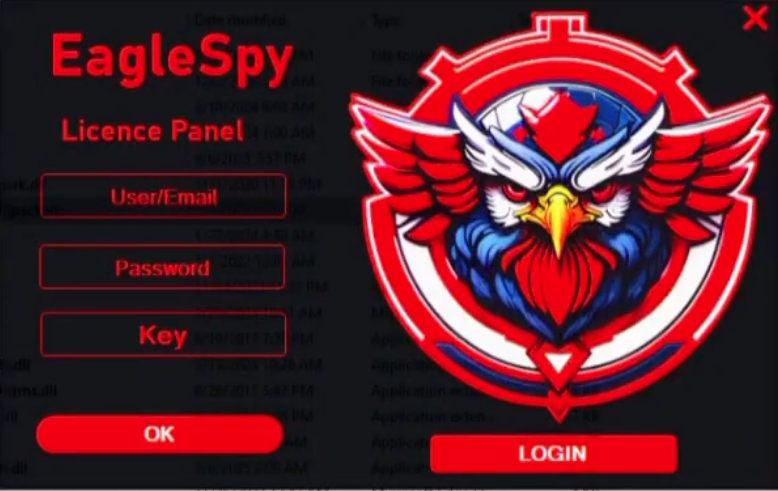
🚨 Nuova campagna di phishing bancario diffonde il #malware Android #EagleSpy! ℹ️ Questa applicazione malevola similare a #CraxsRAT e #SpyNote sottrare informazioni sensibili dallo smartphone #Android della vittima! 👉 d3lab.net/nuova-campagna… #cybersecurity #mwitaly #ioc
#Spynote campaign using fake VISA app Distribution: https://visasecurity[.]net/ C2: 172.86.93.104:7771 hash: 6b1179c23a7502b4dea7f9bde7dde3d4b5b97c64f634ff3471a1d3d27390f3b1 (The PC download button does nothing)
![alberto__segura's tweet image. #Spynote campaign using fake VISA app
Distribution: https://visasecurity[.]net/
C2: 172.86.93.104:7771
hash: 6b1179c23a7502b4dea7f9bde7dde3d4b5b97c64f634ff3471a1d3d27390f3b1
(The PC download button does nothing)](https://pbs.twimg.com/media/Gm9jKK-XUAAGx5X.jpg)
#Spynote campaign targeting Poland Distribution with a fake website looking like the Google Play: https://pltraf111.pages[.]dev/ hash: 71351a9013e7cfbe959d1ea78d1f7bf4bc2cb08a5716725c8434a911149099f3 C2: 45.88.79.231:7771
![alberto__segura's tweet image. #Spynote campaign targeting Poland
Distribution with a fake website looking like the Google Play: https://pltraf111.pages[.]dev/
hash: 71351a9013e7cfbe959d1ea78d1f7bf4bc2cb08a5716725c8434a911149099f3
C2: 45.88.79.231:7771](https://pbs.twimg.com/media/GnW99hFWUAAHrh1.jpg)
#Phishing #Avast #Spynote 📌hxxps://avastsf.]com/📌 Windows - Downloads Anydesk (Revoked Cert) - Anydesk.exe (virustotal.com/gui/file/ec33d…) Mac - Downloads Anydesk - anydesk.dmg (virustotal.com/gui/file/9960c…) Android - Downloads Spynote Trojan - Avastavv.apk (virustotal.com/gui/file/94a3b…)
![RacWatchin8872's tweet image. #Phishing #Avast #Spynote
📌hxxps://avastsf.]com/📌
Windows - Downloads Anydesk (Revoked Cert) - Anydesk.exe (virustotal.com/gui/file/ec33d…)
Mac - Downloads Anydesk - anydesk.dmg (virustotal.com/gui/file/9960c…)
Android - Downloads Spynote Trojan - Avastavv.apk (virustotal.com/gui/file/94a3b…)](https://pbs.twimg.com/media/GP4H25kWYAA0Ti0.jpg)
![RacWatchin8872's tweet image. #Phishing #Avast #Spynote
📌hxxps://avastsf.]com/📌
Windows - Downloads Anydesk (Revoked Cert) - Anydesk.exe (virustotal.com/gui/file/ec33d…)
Mac - Downloads Anydesk - anydesk.dmg (virustotal.com/gui/file/9960c…)
Android - Downloads Spynote Trojan - Avastavv.apk (virustotal.com/gui/file/94a3b…)](https://pbs.twimg.com/media/GP4H6FkWAAEJWFG.jpg)
![RacWatchin8872's tweet image. #Phishing #Avast #Spynote
📌hxxps://avastsf.]com/📌
Windows - Downloads Anydesk (Revoked Cert) - Anydesk.exe (virustotal.com/gui/file/ec33d…)
Mac - Downloads Anydesk - anydesk.dmg (virustotal.com/gui/file/9960c…)
Android - Downloads Spynote Trojan - Avastavv.apk (virustotal.com/gui/file/94a3b…)](https://pbs.twimg.com/media/GP4H6FnXkAAXyOf.jpg)
⚠️fake Android App [Rapport ラポート] #SpyNote #trojan IP: 194.124.216[.]154 (AS3214 xTom) Abused Brand: Bank of Japan 日本銀行 IoC: otx.alienvault.com/pulse/6440223b… 🦠/skin/client/signed10317c.apk bazaar.abuse.ch/sample/7c4fdf5… bazaar.abuse.ch/sample/841271e… @NaomiSuzuki_ @58_158_177_102 @bunnymaid
![ozuma5119's tweet image. ⚠️fake Android App [Rapport ラポート] #SpyNote #trojan
IP: 194.124.216[.]154 (AS3214 xTom)
Abused Brand: Bank of Japan 日本銀行
IoC: otx.alienvault.com/pulse/6440223b…
🦠/skin/client/signed10317c.apk
bazaar.abuse.ch/sample/7c4fdf5…
bazaar.abuse.ch/sample/841271e…
@NaomiSuzuki_ @58_158_177_102 @bunnymaid](https://pbs.twimg.com/media/FuGAx8paYAIX6fg.jpg)
![ozuma5119's tweet image. ⚠️fake Android App [Rapport ラポート] #SpyNote #trojan
IP: 194.124.216[.]154 (AS3214 xTom)
Abused Brand: Bank of Japan 日本銀行
IoC: otx.alienvault.com/pulse/6440223b…
🦠/skin/client/signed10317c.apk
bazaar.abuse.ch/sample/7c4fdf5…
bazaar.abuse.ch/sample/841271e…
@NaomiSuzuki_ @58_158_177_102 @bunnymaid](https://pbs.twimg.com/media/FuGAyVKaAAEBL0e.jpg)
![ozuma5119's tweet image. ⚠️fake Android App [Rapport ラポート] #SpyNote #trojan
IP: 194.124.216[.]154 (AS3214 xTom)
Abused Brand: Bank of Japan 日本銀行
IoC: otx.alienvault.com/pulse/6440223b…
🦠/skin/client/signed10317c.apk
bazaar.abuse.ch/sample/7c4fdf5…
bazaar.abuse.ch/sample/841271e…
@NaomiSuzuki_ @58_158_177_102 @bunnymaid](https://pbs.twimg.com/media/FuGBJNNaQAAEyOh.jpg)
#Spynote AS 20473 🇸🇬 http[:]//66.42.55.13/ready[.]apk AS 210538 🇹🇷 https[:]//45.87.173.219/ready[.]apk Undetected #IOC #Android cc @banthisguy9349 @bofheaded
![prashant_92's tweet image. #Spynote
AS 20473 🇸🇬
http[:]//66.42.55.13/ready[.]apk
AS 210538 🇹🇷
https[:]//45.87.173.219/ready[.]apk
Undetected
#IOC #Android
cc @banthisguy9349 @bofheaded](https://pbs.twimg.com/media/GbAk0RnWEAAulDs.jpg)
![prashant_92's tweet image. #Spynote
AS 20473 🇸🇬
http[:]//66.42.55.13/ready[.]apk
AS 210538 🇹🇷
https[:]//45.87.173.219/ready[.]apk
Undetected
#IOC #Android
cc @banthisguy9349 @bofheaded](https://pbs.twimg.com/media/GbAk0RnXYAIpgrr.jpg)
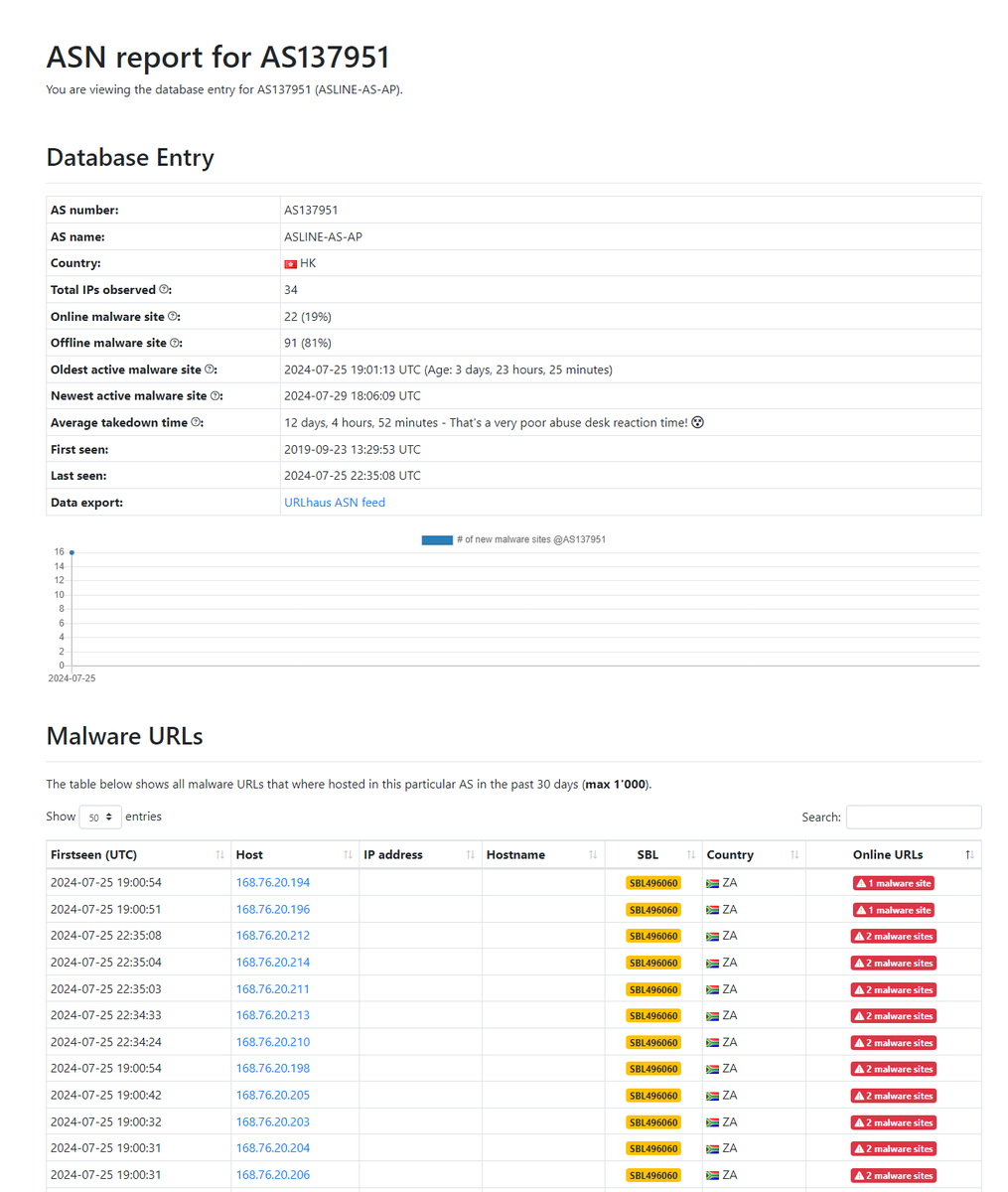
#spyware #spynote Alert ‼️ Coming from AS137951 ASLINE-AS-AP They have also left a nice cat picture for @vxunderground cc: @spamhaus thanks @NDA0E for reporting them.


#Spynote #opendir | AttackCapture An opendir is tracked by @Huntio having 5 different spynote samples. 65cd191f13353ec1cc061ccc751cbfaa d610ced310444cfbab7daa91e3f79439 68a98e82d2abdec08d7cad18a0c3eb8b 32acc69b4c703de71d7a97632c805ede 16fd63efc57a726706ba9eb5b996af21

🎉 4 new rules added and 238 rules updated for the #SpyNote malware family. We're moving toward practical, powerful tools — thanks for your continued support! 🙏 Thanks to @zorro_wang ! 🔗 Report: reurl.cc/QaqnQZ

Android RAT удаленно управляет любым устройством. #craxrat #eaglespy #spynote #шпионское ПО telegram @ venombrt

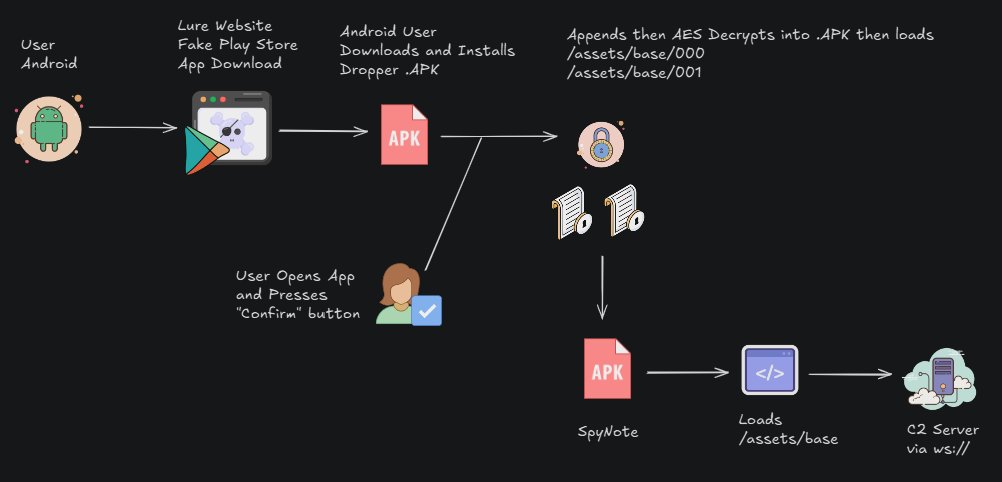
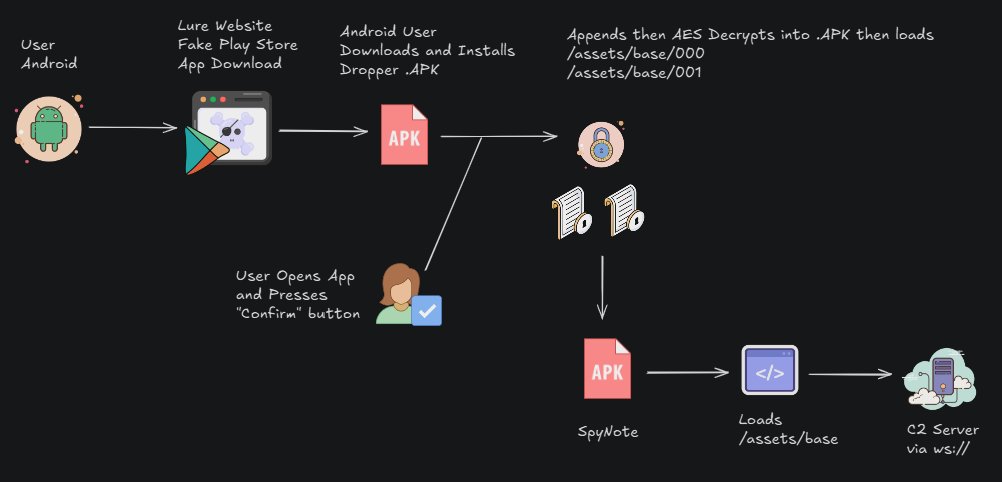
A new report reveals a SpyNote Android RAT campaign using fake Google Play Store clones to steal data, with the malware abusing Accessibility Services for control. #CyberSecurity #Android #SpyNote #Malware #Hacking securityonline.info/spynotes-new-l…
securityonline.info
SpyNote's New Lure: The Stealthy Campaign Using Fake App Stores
A new report reveals a SpyNote Android RAT campaign using fake Google Play Store clones to steal data, with the malware abusing Accessibility Services for control.
A new #SpyNote report is out! 🚨 Dive into the tactics of this Android RAT campaign, from dynamic payload decryption to new obfuscation methods. Learn how threat actors are using deceptive Google Play Store clones to target users dti.domaintools.com/spynote-malwar…

Fake Google Play Store sites deliver Android SpyNote RAT via APK droppers using dynamic decryption, DEX injection, and anti-analysis tactics. Targets include spoofed Chrome, CamSoda, and iHappy apps. #SpyNote #AndroidThreat #MalwareIndia ift.tt/xQlcgPK
A new #SpyNote report is out! 🚨 Dive into the tactics of this Android RAT campaign, from dynamic payload decryption to new obfuscation methods. Learn how threat actors are using deceptive Google Play Store clones to target users: dti.domaintools.com/spynote-malwar…
A new #SpyNote report is out! 🚨 Dive into the tactics of this Android RAT campaign, from dynamic payload decryption to new obfuscation methods. Learn how threat actors are using deceptive Google Play Store clones to target users dti.domaintools.com/spynote-malwar…

#ThreatProtection #SpyNote campaign abuses IBM Trusteer branding with a fake “Mobile” app. broadcom.com/support/securi…
SpyNote, BadBazaar, MOONSHINE Malware Target Android and iOS Users via Fake Apps buff.ly/EO4CWQ7 #Malware #SpyNote #Android #iOS #SecureComms #MobileComms

Android Malware Alert/PSA: mParivahan.apk #Spynote malware family. 2-stage IOCs: MD5: e4c7d672dec271226d5ff1a7da15e182 Payload: 9d0f2d607d48a8b5e3ce23315f86c004 tcp[:]//154[.]61[.]80[.]131[:]6666 tcp[:]//154[.]61[.]80[.]242[:]7771 Full report soon CC: @IndianCERT @MeityGov
![_mostwanted002_'s tweet image. Android Malware Alert/PSA:
mParivahan.apk
#Spynote malware family. 2-stage
IOCs:
MD5: e4c7d672dec271226d5ff1a7da15e182
Payload: 9d0f2d607d48a8b5e3ce23315f86c004
tcp[:]//154[.]61[.]80[.]131[:]6666
tcp[:]//154[.]61[.]80[.]242[:]7771
Full report soon
CC: @IndianCERT @MeityGov](https://pbs.twimg.com/media/GwICelKWsAA4U2t.jpg)
![_mostwanted002_'s tweet image. Android Malware Alert/PSA:
mParivahan.apk
#Spynote malware family. 2-stage
IOCs:
MD5: e4c7d672dec271226d5ff1a7da15e182
Payload: 9d0f2d607d48a8b5e3ce23315f86c004
tcp[:]//154[.]61[.]80[.]131[:]6666
tcp[:]//154[.]61[.]80[.]242[:]7771
Full report soon
CC: @IndianCERT @MeityGov](https://pbs.twimg.com/media/GwICRk4WYAA-bpR.jpg)
![_mostwanted002_'s tweet image. Android Malware Alert/PSA:
mParivahan.apk
#Spynote malware family. 2-stage
IOCs:
MD5: e4c7d672dec271226d5ff1a7da15e182
Payload: 9d0f2d607d48a8b5e3ce23315f86c004
tcp[:]//154[.]61[.]80[.]131[:]6666
tcp[:]//154[.]61[.]80[.]242[:]7771
Full report soon
CC: @IndianCERT @MeityGov](https://pbs.twimg.com/media/GwICU3WXMAEzAH1.jpg)
![_mostwanted002_'s tweet image. Android Malware Alert/PSA:
mParivahan.apk
#Spynote malware family. 2-stage
IOCs:
MD5: e4c7d672dec271226d5ff1a7da15e182
Payload: 9d0f2d607d48a8b5e3ce23315f86c004
tcp[:]//154[.]61[.]80[.]131[:]6666
tcp[:]//154[.]61[.]80[.]242[:]7771
Full report soon
CC: @IndianCERT @MeityGov](https://pbs.twimg.com/media/GwICXjvWQAE3L9z.jpg)
Researchers uncovered dozens of malicious Android apps disguised as popular programs on open servers, which are fronts for SpyNote spyware, harvesting sensitive user data. #AndroidSpyware #SpyNote #MobileSecurity #Cybersecurity #MalwareAlert securityonline.info/alert-hunt-io-…
🤖 Android devices can be a major cybersecurity hazard for businesses. See how #ANYRUN helps with early detection of malicious APKs to prevent costly incidents. Analysis of #SalvadorStealer and #SpyNote inside 👇 any.run/cybersecurity-…
#DomainTools webinar: How threat actors exploit newly-registered domain names 💻⌨️🛜 domaingang.com/domain-crime/d… #malware #spynote #domains 👊
domaingang.com
DomainTools webinar: How threat actors exploit newly-registered domain names
DomainTools is a cybersecurity company that specializes in providing domain name and DNS intelligence to help organizations detect, assess, and respond to threats. Its core role is to monitor domain...
SpyNote, BadBazaar, MOONSHINE Malware Target Android and iOS Users via Fake Apps buff.ly/EO4CWQ7 #Malware #SpyNote #Android #iOS #SecureComms #MobileComms

📱 Oh, you're still doing your own threat intel? Cute. Meanwhile, #SpyNote, #BadBazaar, and #MOONSHINE are redecorating your Android's insides. But hey, that "Update phone?" sticky note is probably doing wonders. 📅 Read the blog. Save a SOC manager. Maybe yourself. 👉…
SpyNote, BadBazaar, MOONSHINE Malware Target Android and iOS Users via Fake Apps buff.ly/EO4CWQ7 #Malware #SpyNote #Android #iOS #SecureComms #MobileComms

#spynote found ->hxxps://www.virustotal.com/gui/file/a1de866d5f75b3f31becb07f4660e2a3cc29d242888be38fadb5a54657156745 #opendir
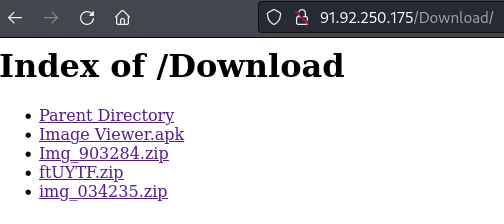

http://54.253.82.23:8080/ #opendir #spyware #spynote hxxp://47.57.184.164 /ready.apk hxxp://103.148.125.8 /ready.apk hxxp://47.57.7.44 /ready.apk hxxp://103.148.125.26 /ready.apk hxxp://164.155.241.15 /ready.apk hxxp://103.142.244.32 /ready.apk


🚩 Nuevo dominio .CL registrado para distribuir el Troyano para dispositivos Android #SpyNote. El sitio web se encuentra en scotiapass[.]cl y suplanta a Scotiabank Chile 🇨🇱 Los actores de amenaza también crearon un canal de YouTube (ScotiaPass) con una guía de instalación 😏…
![1ZRR4H's tweet image. 🚩 Nuevo dominio .CL registrado para distribuir el Troyano para dispositivos Android #SpyNote.
El sitio web se encuentra en scotiapass[.]cl y suplanta a Scotiabank Chile 🇨🇱
Los actores de amenaza también crearon un canal de YouTube (ScotiaPass) con una guía de instalación 😏…](https://pbs.twimg.com/media/GU9h9RbWsAEzG37.jpg)
![1ZRR4H's tweet image. 🚩 Nuevo dominio .CL registrado para distribuir el Troyano para dispositivos Android #SpyNote.
El sitio web se encuentra en scotiapass[.]cl y suplanta a Scotiabank Chile 🇨🇱
Los actores de amenaza también crearon un canal de YouTube (ScotiaPass) con una guía de instalación 😏…](https://pbs.twimg.com/media/GU9h9RpWYAAsWQ0.jpg)
![1ZRR4H's tweet image. 🚩 Nuevo dominio .CL registrado para distribuir el Troyano para dispositivos Android #SpyNote.
El sitio web se encuentra en scotiapass[.]cl y suplanta a Scotiabank Chile 🇨🇱
Los actores de amenaza también crearon un canal de YouTube (ScotiaPass) con una guía de instalación 😏…](https://pbs.twimg.com/media/GU9h9RlX0AA__QU.jpg)
![1ZRR4H's tweet image. 🚩 Nuevo dominio .CL registrado para distribuir el Troyano para dispositivos Android #SpyNote.
El sitio web se encuentra en scotiapass[.]cl y suplanta a Scotiabank Chile 🇨🇱
Los actores de amenaza también crearon un canal de YouTube (ScotiaPass) con una guía de instalación 😏…](https://pbs.twimg.com/media/GU9hjpMXwAAY-Bb.png)
⚠️ #SpyNote Android RAT dirigido a Chile 🇨🇱 y suplantando a Banco Estado y Banco Santander. Para infectar a sus víctimas, el atacante realiza campañas de #phishing a través de la técnica conocida como BITB (Browser In The Browser). Ref: mrd0x.com/browser-in-the… 69.197.134.103…




This is a type of craxs rat(#spynote) malware. Since A101 is a Turkish🇹🇷 market chain, the target is Turkish citizens.

who can help? these apks are 0 detections on VT although i am almost 100% sure they are malicious.

#spyware #spynote Alert ‼️ Coming from AS137951 ASLINE-AS-AP They have also left a nice cat picture for @vxunderground cc: @spamhaus thanks @NDA0E for reporting them.



http[:]45.138.16.250 hosting #SPYNOTE #apk #malware AS 210558( 1337 Services GmbH ) md5: 915e7b50d3cb50243c66ce069032e2cf
![raghav127001's tweet image. http[:]45.138.16.250 hosting #SPYNOTE #apk #malware
AS 210558( 1337 Services GmbH )
md5: 915e7b50d3cb50243c66ce069032e2cf](https://pbs.twimg.com/media/GOUwxMdXUAA2QtL.jpg)
![raghav127001's tweet image. http[:]45.138.16.250 hosting #SPYNOTE #apk #malware
AS 210558( 1337 Services GmbH )
md5: 915e7b50d3cb50243c66ce069032e2cf](https://pbs.twimg.com/media/GOUxF86W0AAIfyz.jpg)
![raghav127001's tweet image. http[:]45.138.16.250 hosting #SPYNOTE #apk #malware
AS 210558( 1337 Services GmbH )
md5: 915e7b50d3cb50243c66ce069032e2cf](https://pbs.twimg.com/media/GOUx5TZWIAEeDKY.jpg)
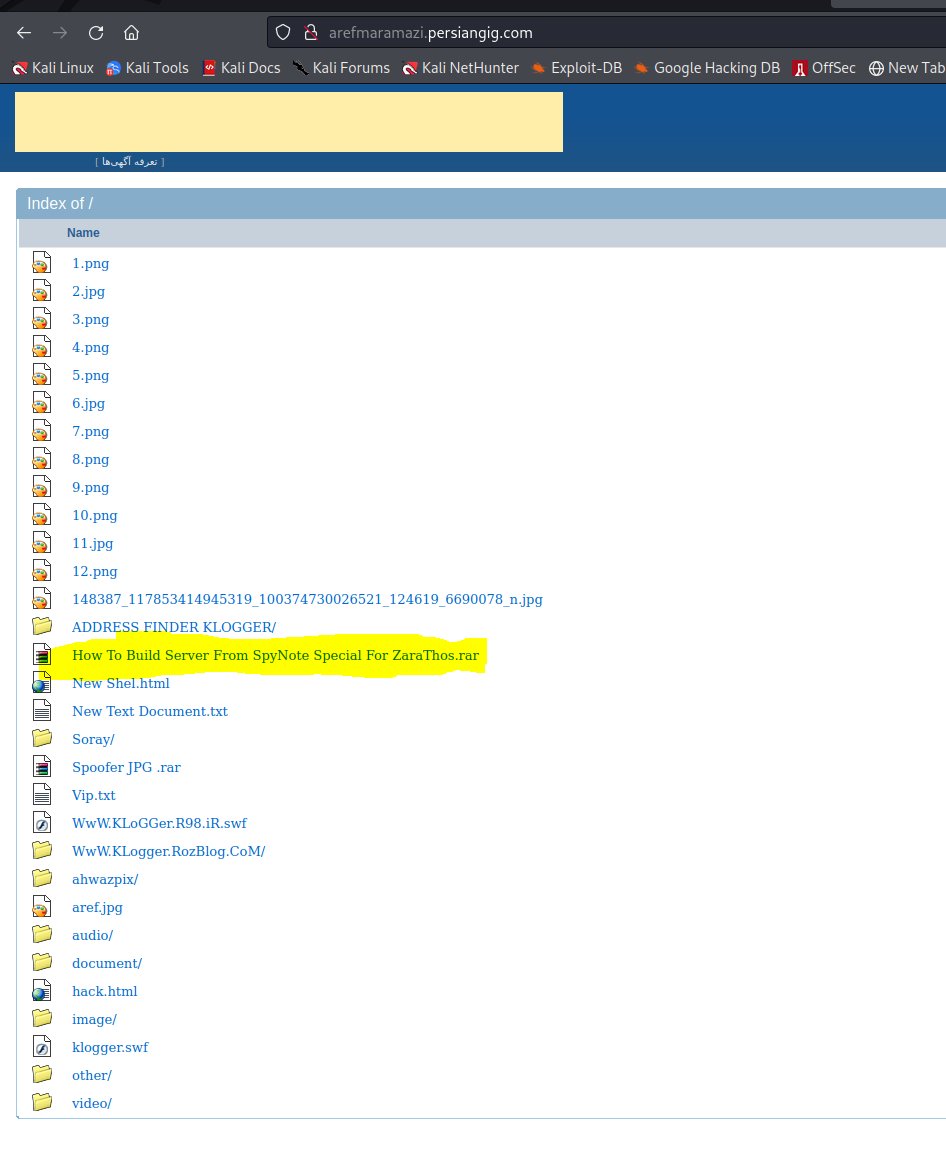
#spynote #spyware owner dor47 whoever wondered how Cybercriminals setup the malicious spynote apk's check Picture 2. we are sending roughly 40 samples now to @ReversingLabs


+ haorizi888[.]top #SpyNote
![skocherhan's tweet image. + haorizi888[.]top
#SpyNote](https://pbs.twimg.com/media/GoxD_TxWEAARm4B.png)
🚨 Newly Registered Domains Distributing SpyNote Malware The latest DomainTools Investigations (DTI) analysis reveals that deceptive websites hosted on newly registered domains are being used to deliver the potent AndroidOS SpyNote malware. dti.domaintools.com/newly-register…

Find 10 differences / Yet another #SpyNote 🤖 Today I read medium.com/s2wblog/detail… about DocSwap After research I found the old article about C2 communication SpyNote (#android #spyware) - bulldogjob.pl/articles/1200-… C2: 204.12.253[.]10:6834 - the network protocol is identical ⬇️
![naumovax's tweet image. Find 10 differences / Yet another #SpyNote 🤖
Today I read medium.com/s2wblog/detail… about DocSwap
After research I found the old article about C2 communication SpyNote (#android #spyware) - bulldogjob.pl/articles/1200-…
C2: 204.12.253[.]10:6834 - the network protocol is identical ⬇️](https://pbs.twimg.com/media/GmQKClxWsAAxYTL.jpg)
#Spynote AS 20473 🇸🇬 http[:]//66.42.55.13/ready[.]apk AS 210538 🇹🇷 https[:]//45.87.173.219/ready[.]apk Undetected #IOC #Android cc @banthisguy9349 @bofheaded
![prashant_92's tweet image. #Spynote
AS 20473 🇸🇬
http[:]//66.42.55.13/ready[.]apk
AS 210538 🇹🇷
https[:]//45.87.173.219/ready[.]apk
Undetected
#IOC #Android
cc @banthisguy9349 @bofheaded](https://pbs.twimg.com/media/GbAk0RnWEAAulDs.jpg)
![prashant_92's tweet image. #Spynote
AS 20473 🇸🇬
http[:]//66.42.55.13/ready[.]apk
AS 210538 🇹🇷
https[:]//45.87.173.219/ready[.]apk
Undetected
#IOC #Android
cc @banthisguy9349 @bofheaded](https://pbs.twimg.com/media/GbAk0RnXYAIpgrr.jpg)
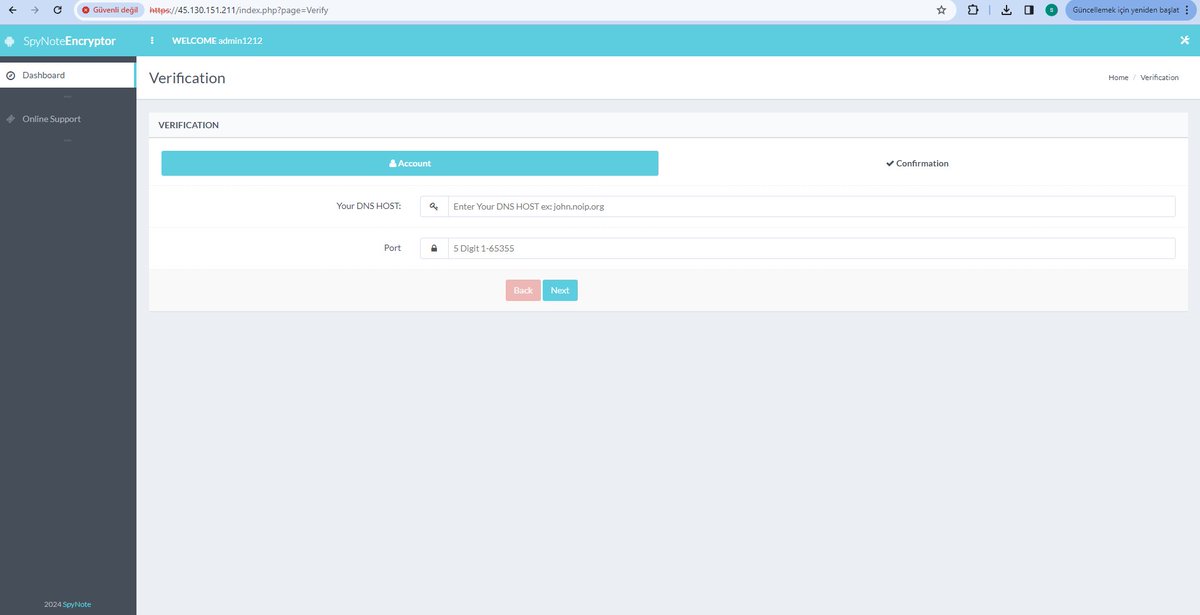
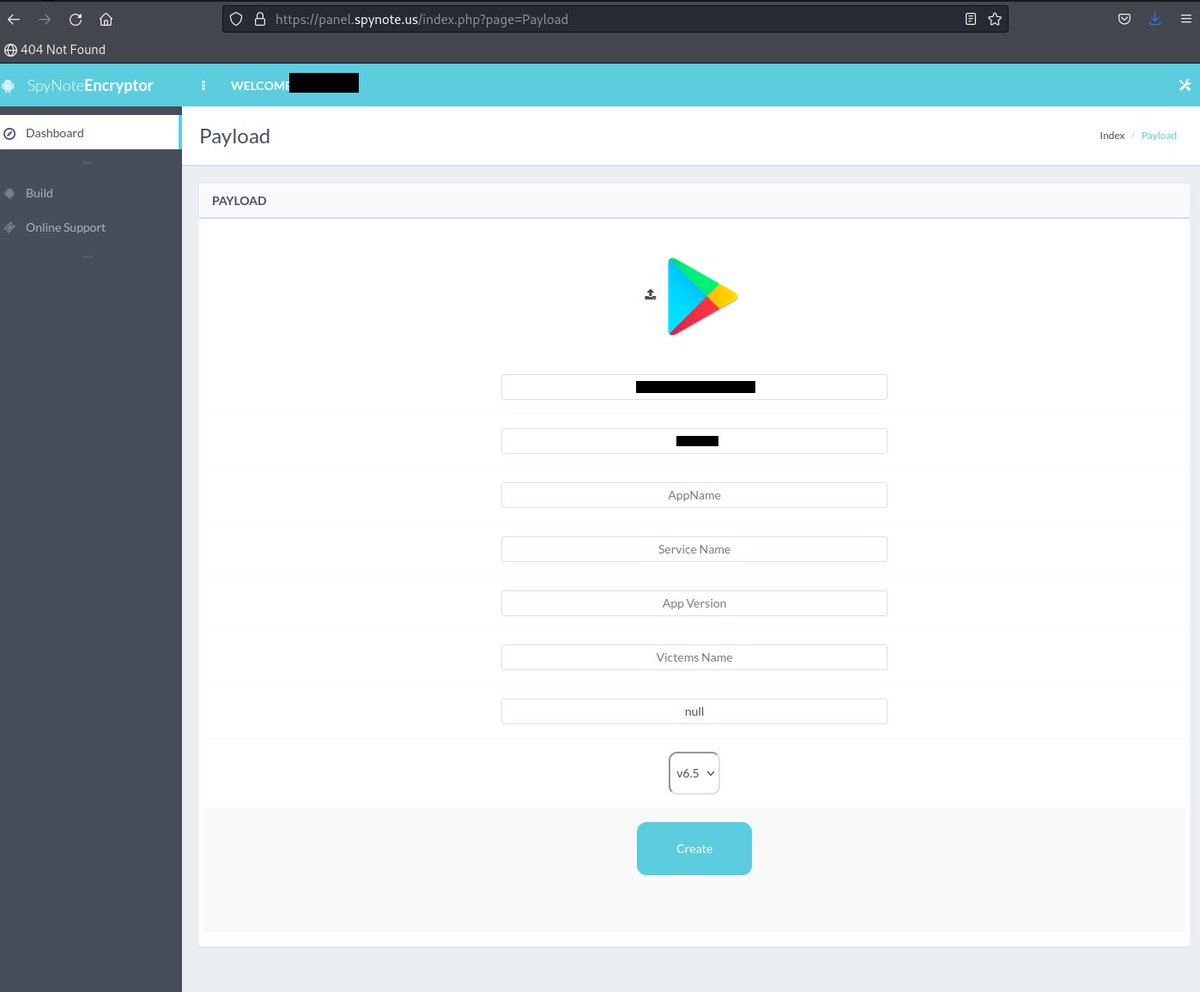
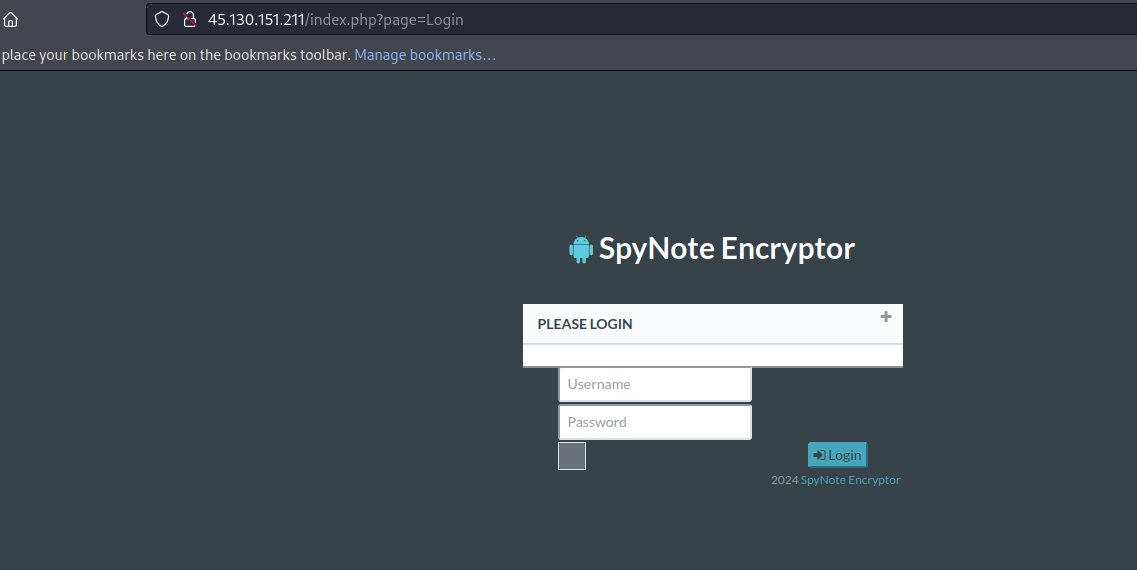
#spynote #android #encryptor panel hxxp://45.130.151.211/index.php?page=Login cc: @Gi7w0rm @500mk500 @abuse_ch @ViriBack
#Phishing #Avast #Spynote 📌hxxps://avastsf.]com/📌 Windows - Downloads Anydesk (Revoked Cert) - Anydesk.exe (virustotal.com/gui/file/ec33d…) Mac - Downloads Anydesk - anydesk.dmg (virustotal.com/gui/file/9960c…) Android - Downloads Spynote Trojan - Avastavv.apk (virustotal.com/gui/file/94a3b…)
![RacWatchin8872's tweet image. #Phishing #Avast #Spynote
📌hxxps://avastsf.]com/📌
Windows - Downloads Anydesk (Revoked Cert) - Anydesk.exe (virustotal.com/gui/file/ec33d…)
Mac - Downloads Anydesk - anydesk.dmg (virustotal.com/gui/file/9960c…)
Android - Downloads Spynote Trojan - Avastavv.apk (virustotal.com/gui/file/94a3b…)](https://pbs.twimg.com/media/GP4H25kWYAA0Ti0.jpg)
![RacWatchin8872's tweet image. #Phishing #Avast #Spynote
📌hxxps://avastsf.]com/📌
Windows - Downloads Anydesk (Revoked Cert) - Anydesk.exe (virustotal.com/gui/file/ec33d…)
Mac - Downloads Anydesk - anydesk.dmg (virustotal.com/gui/file/9960c…)
Android - Downloads Spynote Trojan - Avastavv.apk (virustotal.com/gui/file/94a3b…)](https://pbs.twimg.com/media/GP4H6FkWAAEJWFG.jpg)
![RacWatchin8872's tweet image. #Phishing #Avast #Spynote
📌hxxps://avastsf.]com/📌
Windows - Downloads Anydesk (Revoked Cert) - Anydesk.exe (virustotal.com/gui/file/ec33d…)
Mac - Downloads Anydesk - anydesk.dmg (virustotal.com/gui/file/9960c…)
Android - Downloads Spynote Trojan - Avastavv.apk (virustotal.com/gui/file/94a3b…)](https://pbs.twimg.com/media/GP4H6FnXkAAXyOf.jpg)
#Fofabot Query for #SpyNote #Malware Query: title=="SpyNote Encryptor" IOCs: https://panel.spynote[.]us 109.248.59[.]212 45.130.151[.]211
![Cyberteam008's tweet image. #Fofabot Query for #SpyNote #Malware
Query: title=="SpyNote Encryptor"
IOCs:
https://panel.spynote[.]us
109.248.59[.]212
45.130.151[.]211](https://pbs.twimg.com/media/GH_sgPCWQAAzTtQ.jpg)
#Spynote #opendir | AttackCapture An opendir is tracked by @Huntio having 5 different spynote samples. 65cd191f13353ec1cc061ccc751cbfaa d610ced310444cfbab7daa91e3f79439 68a98e82d2abdec08d7cad18a0c3eb8b 32acc69b4c703de71d7a97632c805ede 16fd63efc57a726706ba9eb5b996af21

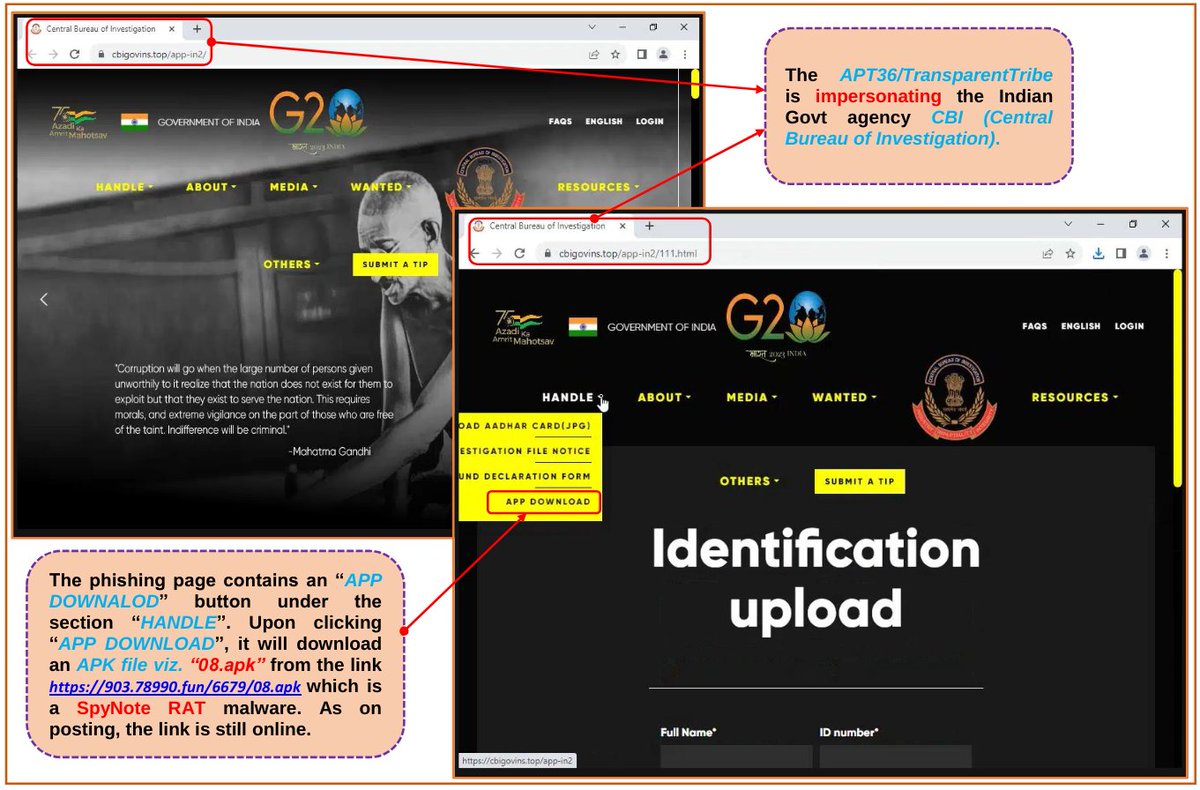
Pakistan's #APT36 / #TransparentTribe is Targeting Indian Govt agency Central Bureau of Investigation (CBI) to deliver #SpyNote #RAT malware. Details are explained in the attached snapshot. Infra: pastebin.com/w0F6pVa7 @500mk500 #Malware #ioc
Per la prima volta abbiamo visto il malware Android #EagleSpy diffuso in Italia, esso risulta molto similare a ##SpyNote e CraxsRAT. Obiettivamente l'intento finale è sempre lo stesso, sottrarre informazioni bancarie. I#oC: d3lab.net/nuova-campagna…

🚨 Nuova campagna di phishing bancario diffonde il #malware Android #EagleSpy! ℹ️ Questa applicazione malevola similare a #CraxsRAT e #SpyNote sottrare informazioni sensibili dallo smartphone #Android della vittima! 👉 d3lab.net/nuova-campagna… #cybersecurity #mwitaly #ioc
Something went wrong.
Something went wrong.
United States Trends
- 1. #GrandEgyptianMuseum 26K posts
- 2. #GEM𓅓 7,142 posts
- 3. #Talus_Labs 1,018 posts
- 4. #capcutlovers N/A
- 5. Game 7 1,490 posts
- 6. jungkook 833K posts
- 7. Happy New Month 172K posts
- 8. Kawhi 8,233 posts
- 9. vmin 4,504 posts
- 10. Ja Morant 5,765 posts
- 11. Barger 6,111 posts
- 12. Glasnow 6,822 posts
- 13. Halloween 2025 200K posts
- 14. Bulls 32.2K posts
- 15. Justin Dean 2,639 posts
- 16. Tinubu 46.7K posts
- 17. #RipCity N/A
- 18. Roki 7,796 posts
- 19. Luka Doncic 19.7K posts
- 20. Grizzlies 7,403 posts