#trustedhardware search results
Batterij om de 8 jaar vervangen, niet dat de stand-by tijd lager was dan die van de iPhone #trustedhardware

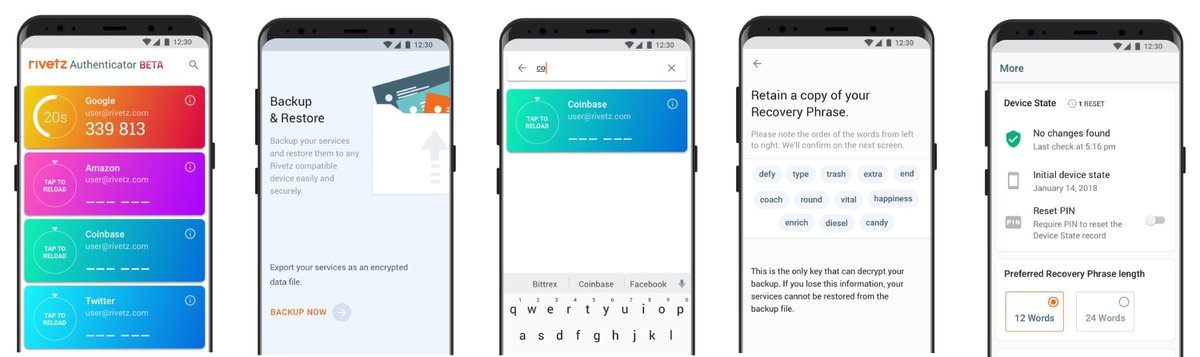
The #Rivetz #Authenticator is a two-step authentication app that uses #trustedhardware already implemented in your mobile device. This hardware is isolated from the rest of your device, resulting in a secure enclave - the perfect place to store secrets.
We're excited to exhibit alongside some industry leaders at #MWC19 next week. Visit us at booth 6i40 with @trustonic @Lookout @dejamobile . #TEE #trustedhardware

I'm excited to start experimenting with @Globaleaks and @torproject on the beautiful and secure #USBArmory #MkII board by @FSecure Thank you @AndreaBarisani for sponsoring this opportunity! #trustedhardware #trustedcomputing #trustedwhistleblowing

.@CMU_ECE Prof builds trust after counterfeit chips found in devices #trustedhardware. bit.ly/1GsXBGT

How safe is your favourite website? The safest sites on the internet have been revealed by #cybersecurity experts. One major criteria was two-factor authentication. What if we took it to the next level and implemented #trustedhardware 2fa? #secure dailym.ai/2DbL91v

The #ABItechSummit is 🔜 Register: abi.link/3iksBz1, then join @ABI_Menting and these industry powerhouses to discuss the major themes and industry trends for #trustedhardware and #confidentialcomputing in the #IoT. #digitalsecurity #iotsecurity #security

#cmuece prof builds trust after counterfeit chips found in everyday devices #trustedhardware bit.ly/1GsXBGT

Register: abi.link/3iksBz1, then join this #ABItechSummit panel to discuss the major themes and industry trends for #trustedhardware and #confidentialcomputing in the #IoT. #digitalsecurity #iotsecurity

RT Lookout "RT RivetzCorp: We're excited to exhibit alongside some industry leaders at #MWC19 next week. Visit us at booth 6i40 with trustonic Lookout dejamobile . #TEE #trustedhardware https://t.co/RsKCa0Yul2"

INFOGRAPHIC: How to protect against compromised smartphone cameras and microphones bit.ly/2IZopDk #rethinkmobilesecurity #mobilesecurity #trustedhardware

"Security-first hardware that closes the gaps in protection represents a promising paradigm shift" Read the full @ForbesTechCncl article from Mike Fong, founder and CEO of @Privoro bit.ly/2oHmDzI #trustedhardware #mobilesecurity

Couldn't help, but notice that #TrustedHardware #mobilesecurity solution on @JohnTChambers iPhone. Full story from @ZDNet and @tomforemski on the RSA Conference and #cybersecurity zd.net/2XUz9bK

Welcome to @Utimaco, the sponsor of this #ABItechSummit panel discussion. Register now: abi.link/3iksBz1, then join this amazing panel to discuss the major themes and industry trends for #trustedhardware & #confidentialcomputing in the #IoT. #digitalsecurity #iotsecurity

The Privoro Solution: Mobile protection through stand-alone, high-security hardware. bit.ly/2B76Ih9 #trustedhardware #mobilesecurity #rethinkmobilesecurity

You know the job. You know what works. And you know when a lock just feels right. 🛠️ That’s Caveo. #LocksmithsChoice #TrustedHardware #CaveoLocks

Revisit @Privoro founder and CEO Mike Fong's article in @SecurToday on external hardware becoming the next sidekick for smartphone security isolation bit.ly/2MPiEJd #rethinkmobilesecurity #trustedhardware #mobilesecurity

Operators on @MagicNewton can run services inside Intel TDX enclaves or operate zk-circuited ML model agents, ensuring trusted computation. #TrustedHardware #zkML
You know the job. You know what works. And you know when a lock just feels right. 🛠️ That’s Caveo. #LocksmithsChoice #TrustedHardware #CaveoLocks

Welcome to @Utimaco, the sponsor of this #ABItechSummit panel discussion. Register now: abi.link/3iksBz1, then join this amazing panel to discuss the major themes and industry trends for #trustedhardware & #confidentialcomputing in the #IoT. #digitalsecurity #iotsecurity

The #ABItechSummit is 🔜 Register: abi.link/3iksBz1, then join @ABI_Menting and these industry powerhouses to discuss the major themes and industry trends for #trustedhardware and #confidentialcomputing in the #IoT. #digitalsecurity #iotsecurity #security

Register: abi.link/3iksBz1, then join this #ABItechSummit panel to discuss the major themes and industry trends for #trustedhardware and #confidentialcomputing in the #IoT. #digitalsecurity #iotsecurity

I'm excited to start experimenting with @Globaleaks and @torproject on the beautiful and secure #USBArmory #MkII board by @FSecure Thank you @AndreaBarisani for sponsoring this opportunity! #trustedhardware #trustedcomputing #trustedwhistleblowing

WHITE PAPER: Examine the current approaches used by smartphone makers to ensure trust, the limitations of these methods and the alternatives for building certainty in a mobile-first world. bit.ly/2OTCdCT #rethinkmobilesecurity #mobilesecurity #trustedhardware

INFOGRAPHIC: How to protect against compromised smartphone cameras and microphones bit.ly/2IZopDk #rethinkmobilesecurity #mobilesecurity #trustedhardware

Revisit @Privoro founder and CEO Mike Fong's article in @SecurToday on external hardware becoming the next sidekick for smartphone security isolation bit.ly/2MPiEJd #rethinkmobilesecurity #trustedhardware #mobilesecurity

"Supply chain attacks – like the one reported to have affected Supermicro – bring much-needed attention to the fact that implicitly trusting the underlying hardware found in most commercial devices may be unwise." bit.ly/2MDIhNa #trustedhardware #mobilesecurity
"In recent years, the federal government has directed significant attention toward protecting the supply chain through policies focused on hardware" Full article from @GCNtech bit.ly/35BgHZu #trustedhardware #mobilesecurity #GovSec

We're excited to exhibit alongside some industry leaders at #MWC19 next week. Visit us at booth 6i40 with @trustonic @Lookout @dejamobile . #TEE #trustedhardware

Batterij om de 8 jaar vervangen, niet dat de stand-by tijd lager was dan die van de iPhone #trustedhardware

.@CMU_ECE Prof builds trust after counterfeit chips found in devices #trustedhardware. bit.ly/1GsXBGT

I'm excited to start experimenting with @Globaleaks and @torproject on the beautiful and secure #USBArmory #MkII board by @FSecure Thank you @AndreaBarisani for sponsoring this opportunity! #trustedhardware #trustedcomputing #trustedwhistleblowing

The #Rivetz #Authenticator is a two-step authentication app that uses #trustedhardware already implemented in your mobile device. This hardware is isolated from the rest of your device, resulting in a secure enclave - the perfect place to store secrets.

The #ABItechSummit is 🔜 Register: abi.link/3iksBz1, then join @ABI_Menting and these industry powerhouses to discuss the major themes and industry trends for #trustedhardware and #confidentialcomputing in the #IoT. #digitalsecurity #iotsecurity #security

Couldn't help, but notice that #TrustedHardware #mobilesecurity solution on @JohnTChambers iPhone. Full story from @ZDNet and @tomforemski on the RSA Conference and #cybersecurity zd.net/2XUz9bK

Revisit @Privoro founder and CEO Mike Fong's article in @SecurToday on external hardware becoming the next sidekick for smartphone security isolation bit.ly/2MPiEJd #rethinkmobilesecurity #trustedhardware #mobilesecurity

#cmuece prof builds trust after counterfeit chips found in everyday devices #trustedhardware bit.ly/1GsXBGT

How safe is your favourite website? The safest sites on the internet have been revealed by #cybersecurity experts. One major criteria was two-factor authentication. What if we took it to the next level and implemented #trustedhardware 2fa? #secure dailym.ai/2DbL91v

INFOGRAPHIC: How to protect against compromised smartphone cameras and microphones bit.ly/2IZopDk #rethinkmobilesecurity #mobilesecurity #trustedhardware

The Privoro Solution: Mobile protection through stand-alone, high-security hardware. bit.ly/2B76Ih9 #trustedhardware #mobilesecurity #rethinkmobilesecurity

"Security-first hardware that closes the gaps in protection represents a promising paradigm shift" Read the full @ForbesTechCncl article from Mike Fong, founder and CEO of @Privoro bit.ly/2oHmDzI #trustedhardware #mobilesecurity

RT Lookout "RT RivetzCorp: We're excited to exhibit alongside some industry leaders at #MWC19 next week. Visit us at booth 6i40 with trustonic Lookout dejamobile . #TEE #trustedhardware https://t.co/RsKCa0Yul2"

"In recent years, the federal government has directed significant attention toward protecting the supply chain through policies focused on hardware" Full article from @GCNtech bit.ly/35BgHZu #trustedhardware #mobilesecurity #GovSec

Register: abi.link/3iksBz1, then join this #ABItechSummit panel to discuss the major themes and industry trends for #trustedhardware and #confidentialcomputing in the #IoT. #digitalsecurity #iotsecurity

Welcome to @Utimaco, the sponsor of this #ABItechSummit panel discussion. Register now: abi.link/3iksBz1, then join this amazing panel to discuss the major themes and industry trends for #trustedhardware & #confidentialcomputing in the #IoT. #digitalsecurity #iotsecurity

WHITE PAPER: Examine the current approaches used by smartphone makers to ensure trust, the limitations of these methods and the alternatives for building certainty in a mobile-first world. bit.ly/2OTCdCT #rethinkmobilesecurity #mobilesecurity #trustedhardware

Something went wrong.
Something went wrong.
United States Trends
- 1. Good Monday 35.7K posts
- 2. Jimmy Cliff 6,632 posts
- 3. #MondayMotivation 9,229 posts
- 4. TOP CALL 3,879 posts
- 5. Victory Monday 1,792 posts
- 6. AI Alert 1,729 posts
- 7. Market Focus 2,788 posts
- 8. Check Analyze N/A
- 9. Token Signal 2,257 posts
- 10. #MondayVibes 2,410 posts
- 11. #centralwOrldXmasXFreenBecky 689K posts
- 12. SAROCHA REBECCA DISNEY AT CTW 705K posts
- 13. DOGE 194K posts
- 14. Happy Thanksgiving 10.5K posts
- 15. NAMJOON 67.6K posts
- 16. Chip Kelly 9,933 posts
- 17. Monad 128K posts
- 18. #BaddiesUSA 69.1K posts
- 19. #LingOrmDiorAmbassador 344K posts
- 20. Stefanski 10.7K posts













