#confidentialcomputing результаты поиска
⏰ Final reminder: the FOSDEM 2026 Confidential Computing devroom closes its Call for Proposals on December 1. Submit here: hubs.la/Q03Sx6QW0 #FOSDEM2026 #CCC #ConfidentialComputing

💬 Are you working in Confidential Computing? The community devroom at FOSDEM 2026 is accepting talk proposals until Dec 1. Share your research, demos, or lessons learned: hubs.la/Q03Sx3-j0 #ConfidentialComputing #FOSDEM2026

🔒 Your data, truly yours! With Arcium, encryption isn't just some privacy; it's a foundational layer of security, keeping your sensitive information safe even during processing. That's #ConfidentialComputing in action! #Arcium @Arcium

The #ConfidentialComputing community will be gathering at FOSDEM 2026 in Brussels! A community-organized devroom will take place on Sunday, February 1, 2026. 🗓 Call for Proposals closes December 1, 2025 👉 Submit your proposal here: hubs.la/Q03Sx1DN0

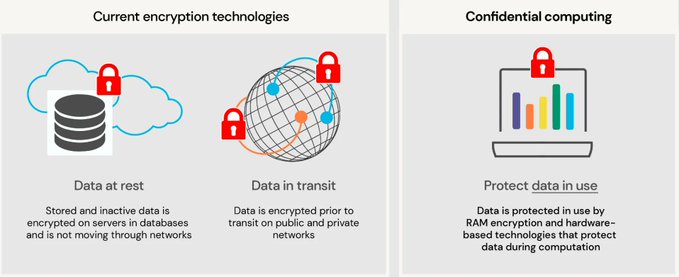
Confidential computing significantly improves the security and privacy of cloud computing by ensuring that data is inaccessible and encrypted while in use. Source Ledidi AS - Link bit.ly/3tcMMV1 rt @antgrasso #ConfidentialComputing #DataProtection #CloudComputing
Last week, CCC hosted a hands-on workshop where participants from Google, NVIDIA, TikTok, Meta, Duality, and more shared real-world deployments, bold experiments, and fresh perspectives on privacy-preserving computing. 👉 Recap: hubs.la/Q03Qhzf30 #ConfidentialComputing

🔵 L'ANSSI partage son positionnement vis-à-vis du #ConfidentialComputing. 📝 L'Agence rappelle notamment les modèles d'attaque que le Confidential Computing prétend traiter, ainsi que des lignes directrices. 🔗 cyber.gouv.fr/en/publication…

Acurast secured $11M to develop a confidential computing platform utilizing consumer smartphones as tamper-resistant nodes for secure workload processing. @Blockchain #ConfidentialComputing By Dynamic Nexus © #DynamicNexus #DynamicNexusCrypto

How Confidential Computing Protects Data in the Age of Cloud AI #cloudAI #confidentialcomputing #securecomputing #espincorp e-spincorp.com/how-confidenti…

Pharma’s biggest barrier isn’t data scarcity - it’s data access. See how #ConfidentialComputing enables secure, blinded collaboration on encrypted data - with IP protection and compliance built in. 📅 Oct 28 | 8AM PST / 11AM EST 🔗 Register: resources.fortanix.com/the-data-youll…

☂️Everything onchain is public — but @Arcium changes that. Compute in private ⚡ prove in public ✅ settle onchain 💎 That’s privacy without trust — the new era of Web3. <encrypt> #Arcium #ConfidentialComputing
🔐 Arcium is building a decentralized encrypted supercomputer. Compute on private data, verifiably — without ever revealing it. Powered by MPC, made for DeFi, AI, gaming & more. #ConfidentialComputing #Web3Privacy #Solana #Arcium
🔥 Cocos AI has powered Prism AI from day one. Secure multi-party AI inside TEEs — no raw data shared. Prism AI (launching soon): collaborative AI + SMPC + attested compute. Cocos: github.com/ultravioletrs/… Prism: prism.ultraviolet.rs #AI #SMPC #ConfidentialComputing #PrismAI
💡 Privacy-Enhancing Technologies (PETs): The New Frontier in Data Collaboration Read more at tinyurl.com/auvzky69 #PETs #PrivacyEnhancingTechnologies #ConfidentialComputing #DataSecurity #FutureofAI #ITStrategy #Cybersecurity #GDPR #HIPAA

🔐 Building the ultra-private future of blockchain. With Full Homomorphic Encryption (FHE), @zama_fhe lets you compute on encrypted data—no peeking, no leaking, full onchain confidentiality. From DeFi to identity to AI: privacy is the feature. 🧠 #FHE #ConfidentialComputing…

Join the Super Hackathon: migrate open-source dApps to opBNB, connect oracle feeds on Super Protocol’s confidential Web3 AI cloud, and stress-test at scale. $20K prize pool! hackathon.superprotocol.com #SuperHackathon #Web3 #ConfidentialComputing #opBNB #SuperProtocol
特に機密性の高いデータを クラウドで安全に処理する方法を一新🛡️ → goo.gle/4jPZtwB Google 広告でもプライバシー強化技術に #ConfidentialComputing が導入されました。今ならプレビュー版 #GeminiCloudAssist で、Confidential Computing を簡単に使用できます。
🔒 Confidentiality guaranteed: All user data and AI requests are processed in secure, isolated compute nodes. No central provider, no leaks. #Privacy #ConfidentialComputing #Security
🌐 Cocoon for developers: Submit AI tasks without exposing data Access GPU power globally Build applications with guaranteed confidentiality #DecentralizedAI #ConfidentialComputing #Privacy
🔥 Cocos AI has powered Prism AI from day one. Secure multi-party AI inside TEEs — no raw data shared. Prism AI (launching soon): collaborative AI + SMPC + attested compute. Cocos: github.com/ultravioletrs/… Prism: prism.ultraviolet.rs #AI #SMPC #ConfidentialComputing #PrismAI
⏰ Final reminder: the FOSDEM 2026 Confidential Computing devroom closes its Call for Proposals on December 1. Submit here: hubs.la/Q03Sx6QW0 #FOSDEM2026 #CCC #ConfidentialComputing

Confidential computing significantly improves the security and privacy of cloud computing by ensuring that data is inaccessible and encrypted while in use. Source Ledidi AS - Link bit.ly/3tcMMV1 rt @antgrasso #ConfidentialComputing #DataProtection #CloudComputing

Zama is building a full-stack encrypted computing layer that secures every step of Web3 and AI workflows. #ConfidentialComputing #Web3Security
Countdown to Barcelona! Only one week until Fortanix joins #NVIDIA at #HPEDiscover 2025. Ready to see live demos of Armet AI for confidential AI and secure enterprise workloads? Don't miss it! hubs.li/Q03TXt4n0 #ConfidentialComputing #AIsecurity #SecureAI

#Confidential #AI: Digitale Souveränität beginnt da, wo Daten technisch – und nicht nur regulatorisch, vertraglich oder per Serverstandort abgesichert sind, schreibt unser Gastautor. #ConfidentialComputing, bietet hier die Lösung. ➡️egovernment.de/sicher-in-der-…
⏰ Final reminder: the FOSDEM 2026 Confidential Computing devroom closes its Call for Proposals on December 1. Submit here: hubs.la/Q03Sx6QW0 #FOSDEM2026 #CCC #ConfidentialComputing

🧬 Empowering Science, Protecting Data Breakthroughs shouldn’t come at the cost of privacy. With Ethernity Cloud, researchers can run advanced computations on sensitive datasets — securely, privately, and collaboratively. 🔐 #Web3 #ConfidentialComputing #Research #DataPrivacy

Confidential Computing is a new paradigm essential for safeguarding data during processing. It utilizes advanced technologies to ensure secure data handling without unauthorized access. Microblog @antgrasso #ConfidentialComputing #infosec #DataProtection

💬 Are you working in Confidential Computing? The community devroom at FOSDEM 2026 is accepting talk proposals until Dec 1. Share your research, demos, or lessons learned: hubs.la/Q03Sx3-j0 #ConfidentialComputing #FOSDEM2026

💡 Did you know? With Ethernity Cloud, healthcare data is processed inside encrypted enclaves — so researchers get insights without ever seeing the raw data. 🏥🔐 Privacy and progress can coexist. 🛡️ #HealthTech #DataPrivacy #ConfidentialComputing #Web3

We are excited to welcome Phala Network as the newest General Member of the CCC! Phala is a secure cloud platform enabling developers to run AI workloads inside hardware-protected #TEEs. Welcome to the #ConfidentialComputing community! Announcement: hubs.la/Q03M0J1b0

The #ConfidentialComputing community will be gathering at FOSDEM 2026 in Brussels! A community-organized devroom will take place on Sunday, February 1, 2026. 🗓 Call for Proposals closes December 1, 2025 👉 Submit your proposal here: hubs.la/Q03Sx1DN0

#DeCC @SecretNetwork @partisiampc @lisaisloud @COTInetwork @ArciumHQ 'it is inevitable Mr Anderson!' #confidentialcomputing

🔵 L'ANSSI partage son positionnement vis-à-vis du #ConfidentialComputing. 📝 L'Agence rappelle notamment les modèles d'attaque que le Confidential Computing prétend traiter, ainsi que des lignes directrices. 🔗 cyber.gouv.fr/en/publication…

Join us at the #ConfidentialComputing Summit 2025 as Mike Bursell, Executive Director of the #CCC, takes the stage to explore two of the most pressing topics in secure AI and infrastructure. Learn more & register: hubs.la/Q03p7FBk0

Just wrapped up a talk on the main stage at @ETHSofiaBG! It was a bit stressful but super exciting to share about #DeCC , #confidentialcomputing and #Depin !

Tomorrow, join us at the #CCSummit. Discover how #ConfidentialComputing is revolutionizing #DataPrivacy, enabling cutting-edge AI solutions in business. Engage with pioneers shaping the future of #TrustworthyAI. Your innovation begins here. See you on June 5th & 6th #iExec $RLC

CCC September newsletter just dropped! 📢 Get highlights from the AI Infra Summit, details on the upcoming AI-Ready Data Safeguards Workshop (Oct 20, SF), OSFF New York, plus new resources and member news! Read now: hubs.la/Q03LNbrN0 #CCC #ConfidentialComputing

Last week, CCC hosted a hands-on workshop where participants from Google, NVIDIA, TikTok, Meta, Duality, and more shared real-world deployments, bold experiments, and fresh perspectives on privacy-preserving computing. 👉 Recap: hubs.la/Q03Qhzf30 #ConfidentialComputing

The growth of #ConfidentialComputing - buff.ly/3LGMT4a #IT #computing #security #cybersecurity #infosec

openEuler #AI #confidentialcomputing solutions have been officially launched!🥳Leveraging hardware-software collaboration and multi-arch support, #openEuler is setting new standards for #datasecurity with enhanced #compatibility and #performance. #opensource #openEulerSummit

GM FAM! 💛 Transparency or privacy? Why not both? Zama’s FHE lets you verify transactions while keeping data encrypted. @zama_fhe #Blockchain #FHE #ConfidentialComputing #ZamaCreatorProgram

Thrilled to be part of this initiative with @jilliangodsil and @blockleaders blockleaders.io/privacy/confid… #confidentialcomputing #decc #web3 #privacy

🚀 Big news in TrustedAI. Fortanix + @NVIDIA are redefining secure, on-prem AI. Run AI on sensitive data - securely, verifiably, at scale. 🔒 Trusted AI ⚡ Performance ✅ Compliance #AIsecurity #EnterpriseAI #ConfidentialComputing 👉 Learn more: hubs.li/Q03QBssp0

Something went wrong.
Something went wrong.
United States Trends
- 1. #WWERaw 26.3K posts
- 2. Giants 47.8K posts
- 3. Jaxson Dart 9,042 posts
- 4. Patriots 73.3K posts
- 5. Marcus Jones 4,716 posts
- 6. Abdul Carter 4,560 posts
- 7. LA Knight 7,481 posts
- 8. Pats 10.4K posts
- 9. #NYGvsNE 1,033 posts
- 10. Drake Maye 8,266 posts
- 11. Nattie 1,408 posts
- 12. Kalani 8,958 posts
- 13. Theo Johnson 1,154 posts
- 14. #RawOnNetflix N/A
- 15. Jey Uso 7,462 posts
- 16. Stein 17.6K posts
- 17. Boutte 1,639 posts
- 18. #MondayNightFootball N/A
- 19. Christian Elliss N/A
- 20. Sidney Crosby 1,029 posts