#defensivecoding arama sonuçları
You might be wondering, what security measures is @idOS_network implementing to make their one-fits-all KYC concept safe ? Let me explain to you like the 5-yr old you are 👇 Data Encryption on a personal level So idOS has a bunch of data of you and imagine some hacker breaks…

Even the most advanced systems have #vulnerabilities, & complacency is often the biggest #cybersecurity risk. Stay ahead of #threats with a proactive defense strategy. CDA helps organizations strengthen their digital armor before the next attack hits. 🔗 criticaldesign.net

building apps is easy; securing them is the hard part. > this is the field guide for devs who want to defend against real-world attacks. > a must-read if you ship code to the web

Security in crypto is an ongoing process. A developer's mind -> no single flaw. An attacker's mind -> just one flaw. Developers must be perfect to be safe from attacks. But perfection doesn't exist, just constant patching, testing and finding flaws before the attacker.
I'm planning a Defensive CSS workshop, focused on practical CSS and design tips that help build future proof user interfaces. Would your team be interested if it's offered live or as a short recorded course? More about Defensive CSS: defensivecss.dev

Another day of the Defense Challenge Explored DOM Manipulation in JavaScript #JavaScript #WebDevelopment #DefenseChallenge #CoderArmy

When you're writing code, sometimes you may not even know it's broken or vulnerable until something bad happens. So Manish wrote this guide to help you identify common issues that'll make your code less safe. He talks about missing input validation, poor error handling, no rate…

🚨 The Human Firewall: Why Your People Are Your Biggest Cybersecurity Vulnerability (And How to Fortify Them) undercodetesting.com/the-human-fire… Educational Purposes!
This software engineer was nearly hacked by a coding interview. I've never seen this attack channel before. Be careful out there, especially vibe coders.

#AI models rely on quality data. This week’s episode: #DataPoisoning – Securing AI Models & Outputs 🔎 How compromised data skews AI results 🧩 Real-world examples + prevention tips 🛡️ Developer strategies to protect model integrity 🎥 Full video: youtu.be/7umLKZij6ow
New video: frequently seen Defender Antivirus/Defender for Endpoint mistakes There are probably 100 pointers for what to avoid or think about. Here's 5 to start. Is there interest in longer form content on well architected MDAV/MDE? Watch: youtu.be/_zjANEdgcpo
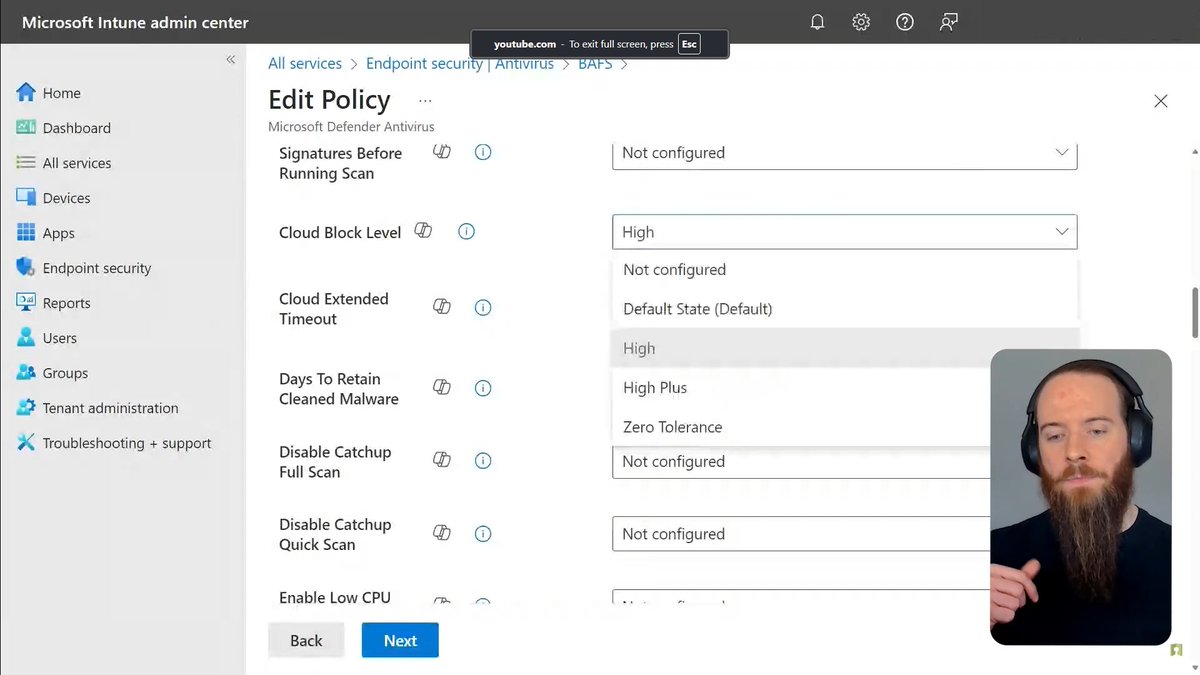
Key points: • Improve code predictability • Trust but verify • Fail fast techniques • Design by Contract • Best practices for naming, if statements, switch statements, enums, nesting, try catches • "Pokemon Exception handling" #defensiveCoding #pluralsight

📌 Google DeepMind launches CodeMender Google DeepMind has unveiled CodeMender, an AI agent that can autonomously detect, patch, and rewrite vulnerable software code. CodeMender represents a significant advancement in automated cybersecurity. By automating the time-consuming…
✍️ New Article: Defensive CSS I compiled a list of defensive CSS techniques to avoid possible issues. This is usually a checklist I use when I'm working on a new web project. Hope you find it useful. 🔗 ishadeed.com/article/defens…

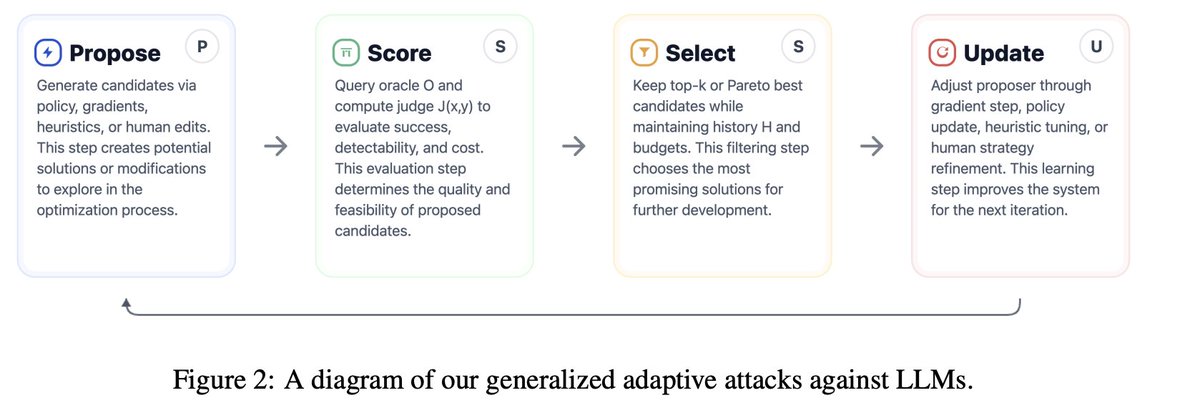
Stronger Adaptive Attacks Bypass Defenses Against Llm Jailbreaks and Prompt Injections - arxiv.org/abs/2510.09023 How should we evaluate the robustness of language model defenses? Current defenses against jailbreaks and prompt injections (which aim to prevent an attacker from…
Building resilient software is like designing a castle with multiple defense layers, ensuring that if one wall falls, others stand strong to protect the core. Balance robustness and performance for a stout fortress. #DefensiveCoding
Boost your software security with defensive coding! Learn key practices like input validation, secure authentication, and proper error handling. Protect your code from vulnerabilities. Read more: neklo.com/blog/software-… #DefensiveCoding #SoftwareSecurity #SecureDevelopment

𝐂# 𝐍𝐮𝐥𝐥 𝐂𝐨𝐧𝐝𝐢𝐭𝐢𝐨𝐧𝐚𝐥 𝐎𝐩𝐞𝐫𝐚𝐭𝐨𝐫 (?.) The null conditional operator (?.) is a powerful tool in C# that provides concise and safe null checking, especially when working with complex object hierarchies. Here are some advanced uses 🧵👇 #csharp #defensivecoding
2️⃣ Defensive programming: Anticipating potential issues and handling them appropriately enhances your application's robustness. Prepare for the unexpected. #DefensiveCoding

Finally… a new Zen of Defensive Programming blog post! This time I am diving into the use of constants and their impact on code safety. #programming #ProgrammingParadigms #DefensiveCoding guidohenkel.com/2023/04/zen-of…

Code defensively to handle unexpected inputs or errors. Don't assume everything will work perfectly. #programming #code #defensivecoding
I think it is time to remind people of this cool blog series called "Zen of Defensive Programming" #programming #ProgrammingParadigms #DefensiveCoding guidohenkel.com/2022/04/zen-of…

I know, I should publish a new installment in my "Zen of Defensive Programming" series, but who has the time? I'll get to it eventually, though… Meanwhile, if you haven't checked it out yet, here is what I've got so far. guidohenkel.com/2022/04/zen-of… #programming #DefensiveCoding
You can grab my Defensive Coding Bootcamp slidedeck for #NDCMelbourne here #defensivecoding #security slideshare.net/quorralyne/def…

slideshare.net
Defensive Coding Bootcamp
"Zen of Defensive Programming" continues. This week with a rule: One operation per line! Read the post to see, why it makes code better and safer. #programming #ProgrammingParadigms #DefensiveCoding guidohenkel.com/2022/06/zen-of…

"Zen of Defensive Programming" continues. This week with a rule: One operation per line! Read the post to see, why it makes code better and safer. #programming #ProgrammingParadigms #DefensiveCoding guidohenkel.com/2022/05/zen-of…

"Zen of Defensive Programming" continues with a closer look at "Ternary Operators" #programming #ProgrammingParadigms #DefensiveCoding guidohenkel.com/2022/05/zen-of…

A new week, a new blog post as Zen of Defensive Programming continues. This week's subject: Clear intentions! #programming #ProgrammingParadigms #DefensiveCoding guidohenkel.com/2022/05/zen-of…

Today we dive into specific examples to illustrate what defensive programming habits you can build to improve your code. More importantly, I’ll also explain, why they are a good choice. #programming #ProgrammingParadigms #DefensiveCoding guidohenkel.com/2022/05/zen-of…

I just posted another entry in my "Zen of Defensive Programming" series, this time discussing code safety, assertions, guard clauses, and the like! #programming #ProgrammingParadigms #DefensiveCoding guidohenkel.com/2022/04/zen-of…

Why you should not turn off compiler warnings and actually elevate your warning level. This and more in my new blog post "Zen of Defensive Programming" #programming #programmingparadigms #defensivecoding guidohenkel.com/2022/04/zen-of…

Here's the latest installment in my "Zen of Defensive Programming" series. Let's talk about compilers, warnings, compatibility and debugging for a moment… #programming #programmingparadigms #DefensiveCoding guidohenkel.com/2022/04/zen-of…

Don't let anyone tell you unit tests are for testing public interfaces only. Remind them to tell that to the bug that is lurking in the private implementation, untested and undiscovered! #programming #ProgrammingParadigms #DefensiveCoding
The next installment in my "Zen of Defensive Coding" blog series is here! This time, I'm covering code readability and maintenance. #programming #ProgrammingParadigms #DefensiveCoding guidohenkel.com/2022/04/zen-of…

This article explores how graceful degradation, #defensivecoding, observability, and a healthy attitude towards failures better equips us before, during, and after an error occurs. @smashingmag @_callumhart smashingmagazine.com/2021/08/build-…
Key points: • Improve code predictability • Trust but verify • Fail fast techniques • Design by Contract • Best practices for naming, if statements, switch statements, enums, nesting, try catches • "Pokemon Exception handling" #defensiveCoding #pluralsight

2️⃣ Defensive programming: Anticipating potential issues and handling them appropriately enhances your application's robustness. Prepare for the unexpected. #DefensiveCoding

"Zen of Defensive Programming" continues with a closer look at "Ternary Operators" #programming #ProgrammingParadigms #DefensiveCoding guidohenkel.com/2022/05/zen-of…

"Zen of Defensive Programming" continues. This week with a rule: One operation per line! Read the post to see, why it makes code better and safer. #programming #ProgrammingParadigms #DefensiveCoding guidohenkel.com/2022/05/zen-of…

The next installment in my "Zen of Defensive Coding" blog series is here! This time, I'm covering code readability and maintenance. #programming #ProgrammingParadigms #DefensiveCoding guidohenkel.com/2022/04/zen-of…

Why you should not turn off compiler warnings and actually elevate your warning level. This and more in my new blog post "Zen of Defensive Programming" #programming #programmingparadigms #defensivecoding guidohenkel.com/2022/04/zen-of…

Finally… a new Zen of Defensive Programming blog post! This time I am diving into the use of constants and their impact on code safety. #programming #ProgrammingParadigms #DefensiveCoding guidohenkel.com/2023/04/zen-of…

I think it is time to remind people of this cool blog series called "Zen of Defensive Programming" #programming #ProgrammingParadigms #DefensiveCoding guidohenkel.com/2022/04/zen-of…

I just posted another entry in my "Zen of Defensive Programming" series, this time discussing code safety, assertions, guard clauses, and the like! #programming #ProgrammingParadigms #DefensiveCoding guidohenkel.com/2022/04/zen-of…

A new week, a new blog post as Zen of Defensive Programming continues. This week's subject: Clear intentions! #programming #ProgrammingParadigms #DefensiveCoding guidohenkel.com/2022/05/zen-of…

Here's the latest installment in my "Zen of Defensive Programming" series. Let's talk about compilers, warnings, compatibility and debugging for a moment… #programming #programmingparadigms #DefensiveCoding guidohenkel.com/2022/04/zen-of…

Today we dive into specific examples to illustrate what defensive programming habits you can build to improve your code. More importantly, I’ll also explain, why they are a good choice. #programming #ProgrammingParadigms #DefensiveCoding guidohenkel.com/2022/05/zen-of…

Boost your software security with defensive coding! Learn key practices like input validation, secure authentication, and proper error handling. Protect your code from vulnerabilities. Read more: neklo.com/blog/software-… #DefensiveCoding #SoftwareSecurity #SecureDevelopment

Something went wrong.
Something went wrong.
United States Trends
- 1. Rickey 2,301 posts
- 2. Waddle 3,430 posts
- 3. Big Balls 22.6K posts
- 4. Argentina 497K posts
- 5. #BeyondTheGates 5,507 posts
- 6. Kings 157K posts
- 7. $HIMS 3,920 posts
- 8. Olave 2,965 posts
- 9. Russell Westbrook 13.6K posts
- 10. Voting Rights Act 25.8K posts
- 11. Maybe in California N/A
- 12. Justice Jackson 18.2K posts
- 13. #ClockTower1Year N/A
- 14. Hayley 5,180 posts
- 15. #TrumpsShutdownDragsOn 5,997 posts
- 16. Aphrodite 4,384 posts
- 17. Veo 3.1 5,739 posts
- 18. Meyers 2,357 posts
- 19. annabeth 2,371 posts
- 20. Capitol Police 26.3K posts